CPC Definition - Subclass H04L
This place covers:
Transmission of signals having been supplied in digital form, e.g. data transmission, telegraphic communication, or methods or arrangements for monitoring.
As the scope of H04L covers a diversity of subject matter, the user is referred to the definitions for the main groups of H04L. The following list is intended to assist the user.
Systems:
- characterised by the code used, e.g. Morse or Baudot; details, see definition for groups H04L 15/00, H04L 17/00, H04L 13/00;
- step by step systems, see definition for group H04L 19/00;
- mosaic printer telegraph systems, see definition for group H04L 21/00;
- baseband systems, see definition for group H04L 25/00;
- modulated carrier systems, see definition for group H04L 27/00;
- data switching networks, see definition for group H04L 12/00.
Arrangements of general application:
- network architectures or network communication protocols for network security, see definition for group H04L 63/00
- real time communication protocols in data switching networks, see definition for group H04L 65/00;
- network protocols for data switching network services, see definition for group H04L 67/00
This place does not cover:
Arrangements applicable to telegraphic or telephonic communication |
Attention is drawn to the following places, which may be of interest for search:
This place covers:
Codes for error detection or error correction, i.e. theoretical code construction and coding circuit architecture designs are classified in H04M 13/00; the application of such codes in transmission systems is covered by H04L 1/00 subgroups.
This place does not cover:
Correcting synchronisation |
Attention is drawn to the following places, which may be of interest for search:
Computer systems | |
Error correction or detection in electrical digital data processing | |
Coin-feed or like apparatus with coded identity card or credit card | |
Error correction in speech coding | |
Codes for error detection or error correction per se, i.e. theoretical code construction and coding circuit architecture designs | |
Transmission | |
Diversity Systems for radio transmission systems | |
Error detection and correction for transmission of compressed video (e.g. MPEG) |
Classification into the main group H04L 1/00 itself should be avoided and instead its relevant subgroups should be used by identifying the particular error technique used. If no other group can be assigned for error control applicable to transmission systems, then it may be assigned to this main group.
In addition an Indexing Code can be given under H04L 2001/0092 for network topology, which is of interest to H04L 1/00.
In patent documents, the following abbreviations are often used:
AM | Acknowledged Mode |
AMC | Adaptive Modulation and Coding |
AMR | Adaptive Multirate |
ARQ | Automatic Repeat reQuest |
BCCH | Broadcast Control Channel |
BCH | Broadcast Channel |
BER | Bit Error Rate |
BLER | Block Error Rate |
BPSK | Binary Phase Shift Keying |
BW | Bandwidth |
C-RNTI | Cell Radio Network Temporary Identity |
CDMA | Code Division Multiple Access |
CE | Cyclic Extension |
CP | Cyclic Prefix |
CQI | Channel Quality Indicator |
CRC | Cyclic Redundancy Check |
CSI | Channel State Information |
DCCH | Dedicated Control Channel |
DCI | Downlink Control Information |
DFT | Discrete Fourier Transform |
DL | Downlink |
DL-SCH | Downlink Shared Channel |
DRA | Dynamic Resource Allocation |
DRX | Discontinuous Reception |
DTCH | Dedicated Traffic Channel |
DTX | Discontinuous Transmission |
E-UTRA | Evolved UMTS Terrestrial Radio Access |
E-UTRAN | Evolved UMTS Terrestrial Radio Access Network |
EPC | Evolved Packet Core |
FDD | Frequency Division Duplex |
FDM | Frequency Division Multiplexing |
FDMA | Frequency Division Multiple Access |
FEC | Forward Error Correction |
H-ARQ | Hybrid ARQ |
HSDPA | High Speed Downlink Packet Access |
HSUPA | High Speed Uplink Packet Access |
IP | Internet Protocol |
IPSec | Internet Protocol Security |
LTE | Long Term Evolution |
MAC | Medium Access Control |
MAC | Message Authentication |
NACK | Negative ACK |
NAS | Non-Access Stratum |
OFDM | Orthogonal Frequency Division Multiplexing |
PAPR | Peak-to-Average Power Ratio |
PDCCH | Physical Dedicated Control Channel |
PDCP | Packet Data Convergence Protocol |
PHICH | Physical Hybrid ARQ Indicator Channel |
PUCCH | Physical Uplink Control Channel |
PUSCH | Physical Uplink Shared Channel |
QAM | Quadrature Amplitude Modulation |
QPSK | Quadrature Phase Shift Keying |
RRC | Radio Resource Control |
SDMA | Space (or Spatial) Division Multiple Access |
SIMO | Single Input Multiple Output |
SIP | Session Initiation Protocol |
SIR | Signal-to-Interference Ratio |
STC | Space Time Coding |
UEP | Unequal error protections |
UM | Unacknowledged Mode |
VoIP | Voice over Internet Protocol |
WCDMA | Wideband Code Division Multiple Access |
This place covers:
General link adaptation techniques, including power control for non-radio links, and handshaking procedures involving link adaptation.
This place does not cover:
Allocation of payload for multicarrier modulation system | |
Control of transmission power in radio systems |
Attention is drawn to the following places, which may be of interest for search:
Splitting-up the transmission path, e.g. time, frequency etc. | |
Allocating sub-channels of the transmission path | |
Negotiation of transmission parameters unrelated to channel quality | |
Adaptation of equalizers (attention: Indexing Code) | |
Transmit line pre-equalization, e.g. precoding, MIMO calibration | |
Multichannel equalizers (attention: Indexing Code) | |
Adaptation of timing of transmitters in a network | |
Mode change for facsimile transmission | |
Network traffic and resource management | |
Communication route selection based on channel quality | |
Wireless resource allocation |
Adaptive techniques are covered by specific subgroups under H04L 1/0001 unless they are other aspects, e.g. frequency hopping, adaptive slew rate, adaptive interleaving, DSL power back-off.
This place covers:
The end raw rate at which bits are transmitted through the channel, e.g. after encoding.
Attention is drawn to the following places, which may be of interest for search:
Allocation of payload | |
Management of data rate of a bus | |
Network nodes adapting their rate to physical link properties | |
Rate modification | |
Explicit feedback to the source | |
Negotiation of communication rate in wireless communication | |
Power control taking into account the transmission rate |
This place covers:
Also adaptive CDMA and direct sequence spread spectrum is covered by this subgroup.
This place does not cover:
Management of data rate of a bus | |
Network nodes adapting their rate to physical link properties | |
CDMA system aspects | |
Negotiation of communication rate in wireless communication systems; network traffic / resource management |
Adaptation of modulation is classified in H04L 1/0003 even if line bitrate remains constant, e.g. switch-over from 8-QAM to 8-PSK.
Adaptation of modulation and coding schemes (MCS/AMR) are classifed also under H04L 1/0009.
Particular ARQ physical mapping aspects should be classified mainly under the H04L 1/1893 or H04L 1/1861.
If the adaptation concerns both control and payload then only H04L 1/0003 is used.
If the adaptation concerns both control and payload then only H04L 1/0003 is used.
This place covers:
This group covers adaptive formatting aspects, e.g. adaptive slot allocation, or adaptive packet formats other than coding.
This place does not cover:
Adaptation of format of signaling | |
Channel / frequency assignment |
This place covers:
Frame or packet length adaptation at lower OSI layers.
This place does not cover:
Maximum packet size (MTU) for TCP/IP |
This place covers:
Also switching between uncoded and coded modes.
This place does not cover:
Adapting channel coding for congestion | |
Unequal or adaptive error correction protection |
ARQ redundancy schemes are classified under the subgroups of H04L 1/1812.
Repetition coding per se is classified also in H04L 1/08; other types of codes under the subgroups of H04L 1/004.
Adaptation of space-time coded transmissions, in particular modification of the space-time matrix is classified under the subgroups of H04L 1/0618.
Adaptation of modulation and coding schemes (MCS) are classified also under H04L 1/0003.
If the adaptation concerns both control and payload then only H04L 1/0009 is used.
If the adaptation concerns both control and payload then only H04L 1/0009 is used.
This place covers:
The coding rate must be adapted in rate matching operations for link adaptation.
Use of multiple puncturing patterns is covered by H04L 1/0068; general rate matching without regard to link quality is covered H04L 1/0067.
This place does not cover:
Adaptive speech coding per se, no transmission involved | |
Adaptive video coding per se, no transmission involved |
This place covers:
This class is used for special adaptation strategies for adopting a transmission mode, e.g. select an MCS mode, which do not fall within its subclasses. For example, use of special utility or cost functions is classified here.
This place covers:
This class is used for uncommon memory structures, e.g. switching tables, look-up tables and the like.
This place covers:
Guarantee of QoS and interaction of QoS parameters of higher layers and of the physical and data link layers. Adaptation takes into account types of data, e.g. real-time data.
This place does not cover:
Wireless network traffic management |
Latency aspects per se should be classified only here and not in any higher subgroups.
This place covers:
Special statistical approaches for mode-switching including future system or channel conditions mode-switching decision, e.g. calculation of confidence intervals or sequential testing for early decisions.
This place covers:
Algorithms explicitly using Markov chains.
This place covers:
Algorithms in which the adaptation thresholds themselves are adapted according to e.g. state of transmitter or receiver.
This place covers:
E.g. during the negotiation phase.
This place does not cover:
Re-negotiation phase of parameters unrelated to channel quality |
This place covers:
Signaling conveying adaptation commands or channel quality indicators, scheduling and formatting aspects thereof.
This place does not cover:
Signaling for administration of a divided path | |
MIMO systems with feedback | |
Antenna switching / beamforming based on receiver feedback | |
Monitoring or testing of receivers with feedback of measurements to the transmitter | |
Measuring or estimating channel quality parameters |
The appropriate sub-group should be assigned and the main sub-class be avoided.
Signal quality per se is classified in H04L 1/20.
This place covers:
Both for forward and reverse direction.
This place does not cover:
Monitoring or testing of receivers with feedback of measurements to the transmitter |
This place covers:
How the actual signaling is conveyed.
The appropriate sub-group should be assigned and the main sub-class be avoided. Mere error control coding of signaling is not assigned by this class.
This place does not cover:
Wireless Transmission Power Control |
Protection of CQI (channel quality indicator) or TFCI (or transport format combination indicator) with error control is classified in H04L 1/0072.
This place does not cover:
Details of the supervisory signal being transmitted together with payload signals; piggybacking | |
Systems acting by means of fluids in general; Fluid-pressure actuators, e.g. servo-motors; Details of fluid-pressure systems, not otherwise provided for |
The class should not be assigned if the commands include an acknowledgement indication.
Piggybacked acknowledgements or transmission of command with acknowledgement indication is classified in H04L 1/1664 , H04L 1/1671 .
Implicit signaling is not classified here either but in relevant subgroups under H04L 1/0033, H04L 1/0036.
This place covers:
Specific parameters of transmitter aspects, i.e. circuit or computer-based implementation, e.g. amplifying circuit, etc. according to channel quality.
The class should be assigned only if its subclass is not relevant.
This place covers:
Mode switching based on ACK/NACK indications (ACK/NACKs are used as derivative channel quality indicators).
This place covers:
Specific parameters of receiver aspects, i.e. circuit or computer-based implementation, e.g. demodulator, etc. according to channel quality.
The class should be assigned only if any subclass is not relevant.
This place does not cover:
Identification of modulation type | |
CDMA code identification |
This place does not cover:
Code rate detection or code type detection | |
Arrangements for detecting the data rate of an incoming signal | |
Arrangements for identifying the type of modulation |
Code rate detection of code type detection are classified in H04L 1/0046.
This place covers:
Application of FEC codes in transmission systems.
This place does not cover:
Space-time coding | |
Error correction in synchronization | |
Error correction or detection in electrical digital data processing | |
Error correction in speech coding | |
Error detection/correction (code construction per se, coding and decoding architectures) | |
Codes for error detection or error correction per se | |
Error correction for video transmission (e.g. MPEG) |
Adaptive FEC is classified in H04L 1/0009.
Space-time/frequency coding/decoding is classified in H04L 1/0618, H04L 1/0606
Repetition coding is classified in H04L 1/08.
Hybrid ARQ redundancy schemes (ARQ combined with FEC) are classified under the subgroups of H04L 1/1812.
This place covers:
Hardware circuit design or functional computer-implemented arrangements.
This place covers:
The FEC encoding operation is specifically designed by taking into account other signal generation operations (e.g. properties of the modulator or local oscillator).
This place does not cover:
Rate matching | |
For PSK signal shaping, e.g. trellis shaping, coset coding | |
QAM signal shaping, e.g. trellis shaping, coset coding |
Classes H04L 1/0058, H04L 1/006, H04L 1/0067 are considered first before giving the above subclass.
This place covers:
Hardware circuit design or functional computer-implemented arrangements.
This place does not cover:
Blind format detection | |
Packet format detection | |
Data rate detection |
Adaptive code rate or code type detection is classified in H04L 1/0038.
Packet format detection is classified in H04L 1/0091.
This place covers:
The FEC encoding operation is specifically designed by taking into account other signal generation operations (e.g. properties of the demodulator, sensitivity to errors of later signal processing stages).
This place does not cover:
Sequence estimation or equalization |
This place does not cover:
Synchronization based on error correcting/detecting codes | |
with channel-decoding circuitry | |
In conjunction with spatial equalization |
This place does not cover:
Turbo equalization | |
Turbo coding and decoding per se |
This place does not cover:
Sequence estimation, e.g. Viterbi decoding arrangements |
This place covers:
Block codes such as Reed-Solomon codes, LDPC codes, etc.
This place does not cover:
Error detection codes | |
Concatenated codes |
Classes H04L 1/0061 and H04L 1/0064 take precedence.
This place does not cover:
Coded modulation with block coding per se |
This place does not cover:
Coded modulation with trellis coding per se |
This place does not cover:
By repeating transmission, e.g. Verdan system |
Adaptive rate matching according to link quality is covered by H04L 1/0013.
Repetition coding is covered by H04L 1/08.
This place covers:
Puncturing patterns (adaptive and non-adaptive).
This place does not cover:
Avoidance of errors by organising the transmitted data in a format specifically designed to deal with errors | |
Unequal error protection |
Unequal error protection formatting arrangements is covered by H04L 1/0086.
General aspects of UEP is covered by old Indexing Code H04L 2001/0098.
This place covers:
Use of interleavers, which interchange data elements in the time domain in transmission systems.
Diversity arrangements, see H04L 1/02.
This place does not cover:
Assignment of physical channels and/or subcarriers | |
Interleaving per se and its memory designs | |
Spatial/frequency diversity for radio communication |
Turbo coding interleavers are not classified here since they are considered integral part of the turbo coder.
Non-adaptive formatting arrangements is covered by H04L 1/0086.
Adaptive FEC for control data is covered by H04L 1/001.
This place covers:
Details of FEC of feedback such as CQI, ACK.
ACK/NACK repetition coding is covered by H04L 1/1858.
This place covers:
Details concerning transmission of FEC related parameters related to signaling information.
Transmission of signaling for adaptation purposes is covered by H04L 1/0023.
This place covers:
Details of error control at intermediate node, e.g. exclusive OR signal coding or stronger re-encoding arrangements at relay.
This place does not cover:
Cooperative diversity | |
Active relay systems |
Coding in both space and time is covered by H04L 1/0618.
Topology aspect is covered by H04L 2001/0097.
This place does not cover:
Physical mapping |
Adaptive formatting is covered by H04L 1/0006.
FEC coding, e.g. CRC is covered by H04L 1/004.
This place does not cover:
By using return channel in which the signals are sent back to the transmitter to be checked | |
Baseband systems | |
Modulated-carrier systems |
Acknowledgement formats is covered by H04L 1/16 and H04L 1/1607.
Arrangements for preventing errors in the return channel, e.g. handshaking are covered by Indexing Code H04L 2001/125.
This place does not cover:
by using forward error control | |
Bit loading is covered by | |
Constellation mapping aspects |
UEP for coding is covered by H04L 1/007.
General aspects of UEP is covered by old Indexing Code H04L 2001/0098.
This place covers:
Hardware circuit design or functional computer-implemented functions.
This place covers:
Hardware circuit design or functional computer-implemented functions.
This place does not cover:
Data rate detection is covered by |
Code rate detection is covered by H04L 1/0046.
This place covers:
Space-time coding techniques (i.e. for radio) are classified beneath, see relevant subclasses.
In addition, non-radio diversity arrangements involving redundant, simultaneous signal transmission.
Attention is drawn to the following places, which may be of interest for search:
Radio diversity arrangements (except space-time coded arrangements) are covered by |
The class should be assigned only if any subclass is not applicable.
This place covers:
Arrangements with constellation plane partitioning taking space-time diversity into account in equivalence to trellis coded modulation in non-diversity schemes.
This place covers:
Hardware circuit design or functional computer-implemented arrangement.
This place covers:
Hardware circuit design or functional computer-implemented arrangement.
This place does not cover:
Sphere detection |
This place covers:
Transmitted space-time matrices that are considered each as one block coded entity.
For symbol block coding prior to space-time matrix transmission H04L 1/0057.
For symbol convolutional coding prior to space-time matrix transmission H04L 1/0059.
This place covers:
Semi-orthogonal space-time matrix arrangements to increase the transmission rate.
This place covers:
Signaling pertaining to the space-time matrix.
For normal adaptive transmissions H04L 1/0001.
This place does not cover:
Transmission or retransmission of more than one copy of an acknowledgement message | |
Transmission or retransmission of more than one copy of a message |
Attention is drawn to the following places, which may be of interest for search:
Adaptive and non-adaptive rate matching |
Arrangements for preventing errors in the return channel, e.g. handshaking are covered also by Indexing Code H04L 2001/125.
Attention is drawn to the following places, which may be of interest for search:
Loop-back testing | |
Echo cancellation |
Attention is drawn to the following places, which may be of interest for search:
Status reports for improving the reliability of multicast or broadcast data in data switching networks |
This place covers:
Explicit indications of ranges of acknowledged data packets, e.g. sequence numbers SN:5 to 16, 23 to 25. Rules may be involved to further compress the sequence number or other signaling.
Bitmaps where list acknowledgements appear as 0s and 1s are in H04L 1/1614.
Attention is drawn to the following places, which may be of interest for search:
Implementation or adaptation of Internet protocol [IP], of transmission control protocol [TCP] or of user datagram protocol [UDP] |
This place does not cover:
Window size / update for TCP/IP |
This place does not cover:
Buffer level management for video bitstream receiver. |
Attention is drawn to the following places, which may be of interest for search:
Repetition coding in general |
This place covers:
Constellation / mapping rearrangements due to retransmissions, and mapping of receiver-initiated transmissions to resource blocks.
This place does not cover:
Allocation of signaling |
Acknowledgement signaling per se is classified in H04L 1/1607.
This place does not cover:
Window size / update for TCP/IP |
This place does not cover:
Buffer level management for video bitstream receiver |
Attention is drawn to the following places, which may be of interest for search:
Repetition coding in general |
This place covers:
Constellation / mapping rearrangements due to retransmissions, and mapping of transmitter-initiated transmissions to resource blocks.
This place does not cover:
Physical resource mapping in general |
This place does not cover:
Measurement characteristics of individual pulses | |
Measurement of noise, signal-to-noise | |
Measurement of signal quality by testing | |
Measurement of optical signal-to-noise, bit error rate, quality factor | |
Measuring or estimating channel quality parameters |
Frame indication per se H04L 1/0082.
This place does not cover:
Measurement of noise, signal-to-noise | |
Jitter measurement by testing |
This place covers:
E.g. redundant stand-by links.
Attention is drawn to the following places, which may be of interest for search:
Redundancy in electrical buses | |
Redundant control systems | |
Error detection / correction | |
Redundant systems in computer networks | |
Switching spare elements | |
Other transmission systems with redundant channels |
This place covers:
Testing correct operation.
This place does not cover:
Testing / monitoring arrangements | |
Measurement of non-linear distortion | |
Measuring characteristics of individual pulses, e.g. deviation from pulse flatness, rise time, duration | |
Arrangements for testing circuits and fault location | |
Testing storage memories | |
Testing of line transmission systems | |
Testing for optical arrangements | |
Testing of transmitters / receivers | |
SDH/SONET monitoring | |
Monitoring / testing of exchanges | |
Testing arrangements for wireless transmission |
Echo systems are in H04L 1/14.
This place covers:
Arrangements for dividing a transmission path, for allocating sub-channels, signalling for multiple channel indication and duplex/half-duplex systems.
This group works at the physical layer, for wireless or line communications (ADSL).
The arrangements for dividing the transmission path involve multiple access techniques capable of supporting multiple users by sharing the available system resources. Examples of such multiple-access techniques include Frequency Division Multiple Access (FDMA) systems, Orthogonal FDMA (OFDMA) systems, multicarrier Code Division Multiple Access (multicarrier CDMA) systems, i.e. any combination of multicarrier signals and a code division.
An OFDM system may implement a radio technology such as Evolved UTRA (E-UTRA), Ultra Mobile Broadband (UMB), IEEE 802.11 (Wi-Fi®), IEEE 802.16 (WiMax®), IEEE 802.20 (Flash-OFDM®).
3GPP Long Term Evolution (LTE) is a release of UMTS that uses E-UTRA, which employs OFDM on the downlink and SC-FDMA on the uplink.
Attention is drawn to the following places, which may be of interest for search:
Data switching networks | |
Systems using multi-frequency codes | |
Multicarrier modulation techniques | |
Multicarrier demodulation techniques | |
Multicarrier synchronisation aspects | |
Spread spectrum techniques in general | |
Frequency hopping for spread spectrum | |
Conditioning for two-way transmission in general | |
Spatial multiplexing for diversity systems (the same signal is transmitted by the different antennas) | |
Multiplex communication in general | |
Time division multiple access (TDMA) | |
Orthogonal CDMA (i.e. using Walsh codes) | |
Code division multiple access (CDMA) | |
Code allocation | |
Wireless communication networks; Local resource management |
When the multiple access scheme relies on the use of multicarrier signals, and if what is important is how the signal is modulated/demodulated, or "hardware" aspects in the transmitter or the receiver to produce or recover (like synchronisation) such signal or aspects related to the peak power reduction, then the classes under H04L 27/2601 are relevant. Otherwise, to indicate that the signal involved is, for example, an OFDM signal, then the class under H04L 5/0007 is used instead.
Subgroups H04L 5/22, H04L 5/225, H04L 5/24, H04L 5/245, H04L 5/26 are inactive. The classification should be done in H04J 3/00.
In this place, the following terms or expressions are used with the meaning indicated:
ADSL | Asymmetric Digital Subscriber Line |
DMT | Discrete Multi-Tone |
MC-CDMA | Multicarrier CDMA |
OFDM | Orthogonal Frequency Division Multiplexing |
OFDMA | Orthogonal Frequency Division Multiple Access |
SC-FDMA | Single-Carrier Frequency Division Multiple Access |
CC | Component Carrier |
CoMP | Cooperative Multi-point |
FDM | Frequency Division Multiplexing |
FDMA | Frequency Division Multiple Access |
IFDMA | Interleaved Frequency Division Multiple Access |
MIMO | Multiple-Input Multiple-Output |
PRB | Physical Resource Block |
RA | Resource Allocation |
SDMA | Spatial Division Multiple Access |
SRS | Sounding Reference Signal |
TDD | Time Division Duplex |
In patent documents, the following words/expressions are often used with the meaning indicated:
"pilot signals" | "Reference Signals" or "training signals" or "sounding signals". |
"persistent allocation" | that the resources allocated to the user equipment (UE) are valid until the UE receives another allocation which will then override the previous one. This would typically happen in case the channel conditions have changed (or AMR codec changes) and, thus, the previous allocation would no longer be suitable for the user. |
This place covers:
Arrangements for dividing the transmission path.
This group answers the question "How is the transmission path split up?". Since the signals are digital, it is considered that there is always a time dimension, and thus, the minimum number of dimensions is two.
This place does not cover:
Two-way operation using the same type of signal |
Attention is drawn to the following places, which may be of interest for search:
Multiplexing communication |
Attention is drawn to the following places, which may be of interest for search:
MIMO systems | |
Multi-antenna systems using spatial multiplexing at the transmitting station | |
Orthogonal multiplex systems | |
Code division multiplex systems |
This place covers:
Access methods allowing multiple users to share the same frequency band by subdividing the band into orthogonal frequency channels, frequency hopping for multicarrier signals, SC-FDMA or IFDMA.
Attention is drawn to the following places, which may be of interest for search:
Spread spectrum techniques using frequency hopping |
Attention is drawn to the following places, which may be of interest for search:
MIMO systems | |
Multi-antenna systems using spatial multiplexing at the transmitting station |
This group should contain the cases of spreading codes in the time domain, where chips of the code are applied in sequence, once at a time, to each of the subcarriers.
This group should contain the cases of spreading codes in the time domain, where each frequency sees the same spreading code (for example, multicarrier DS-CDMA).
This group should contain the cases of spreading codes in the frequency domain. Each chip of the spreading code is transmitted through a different subcarrier.
This place covers:
The combination OFDM and MIMO; or frequency reuse.
Attention is drawn to the following places, which may be of interest for search:
Spatial transmit diversity using a single antenna at transmitter | |
Selection of precoding matrices or codebooks in MIMO systems | |
Spaced antennas at the transmitting station using spatial multiplexing |
This place covers:
Changes from time-frequency to time-frequency-space.
This place does not cover:
Signalling an indication of how the channel is divided |
This place covers:
Sub-channels are what the path is split up into according to H04L 5/0001.
This place covers:
This group answers the question of "Who makes the allocation?". Cooperative allocation (for example in CoMP systems or cognitive radio systems or when dealing with ICIC, Inter-cell Interference Cancellation) is classified under H04L 5/0032, which implies a plurality of base stations that cooperates or exchanges information to perform the allocation.
This place covers:
The allocation for plurality of users, thus, to indicate which user gets what.
This place covers:
Single user case, what a single user does with its resources.
This place covers:
Allocation of payload or data in the available subchannels.
This place covers:
The case of having different modulations in the different subcarriers.
This place covers:
Allocation of pilots or sounding reference signal patterns and synchronisation signals.
CK/NACK signals, CQI signals not known to the receiver are classified under H04L 5/0053.
This place does not cover:
Allocation of control signalling | |
Signalling for the administration of the divided path |
This place covers:
Sending ACK/NacK signals, channel quality indicator [CQI] signals and in general any control signalling which is not a known signal to the receiver. Physical resources used for signalling.
This place is intended for allocation of control signalling, while H04L 5/0091 is intended for use of control signalling.
Attention is drawn to the following places, which may be of interest for search:
Allocation of pilot signals, i.e. of signals known to the receiver |
According to QoS (Quality of Service) is also classified here.
Attention is drawn to the following places, which may be of interest for search:
Allocation or scheduling criteria for wireless resources based on terminal or device properties |
Attention is drawn to the following places, which may be of interest for search:
Interference mitigation or co-ordination of intercell interference in orthogonal multiplex systems |
This place covers:
The subgroups answer the question "How often the allocation is updated?". For Persistent allocation (if the update is due to channel conditions change, then H04L 5/0085), fixed allocation (H04L 5/008).
This place is intended for use of control signalling, while H04L 5/0053 is intended for allocation of control signalling.
Attention is drawn to the following places, which may be of interest for search:
Allocation of signalling | |
Channels characterised by signals being represented by different amplitudes or polarities | |
Channels characterised by signals being represented by different frequencies | |
Channels characterised by signals being represented by different phase modulations of a single carrier |
This place covers:
How the channel is divided, for instance, for indicating that the whole frequency band is divided into a certain number of subcarriers, or that the base station informs the mobile how according to H04L 5/0001 the channel is divided. Both uplink or downlink.
This place covers:
The signalling of the Content of the allocation. For example, which carriers are allocated, how many bits are allocated to each subcarrier, etc. Both uplink or downlink.
This place does not cover:
Code allocation applied as frequency-domain sequences |
Attention is drawn to the following places, which may be of interest for search:
Code allocation in code division multiplex systems |
This place covers:
FDM. Different data signals for transmission on a single communications channel are multiplexed, whereby each signal (single carrier) is assigned a non-overlapping frequency range within the main channel.
This place does not cover:
combined with the use of different frequencies |
Attention is drawn to the following places, which may be of interest for search:
Frequency regulation arrangements |
This place covers:
ADSL systems. FDD systems.
Attention is drawn to the following places, which may be of interest for search:
Repeaters for converting two wires to four wires | |
Reducing echo effects or singing | |
Selecting arrangements |
Attention is drawn to the following places, which may be of interest for search:
Networks simulating a line of certain length |
This place covers:
Zipper (a time-synchronised frequency division duplex implementation of discrete multi-tone [DMT] modulation).
This place does not cover:
Two-way operation using the same type of signal using time-sharing |
Attention is drawn to the following places, which may be of interest for search:
Arrangements for coupling to multiple lines, e.g. for differential transmission | |
Phantom interconnection between telephone switching centres |
This place does not cover:
Details not particular to receiver or transmitter | |
Apparatus or local circuits for transmitting or receiving dot-and-dash codes | |
Apparatus or local circuits for transmitting or receiving codes wherein each character is represented by the same number of equal-length code elements | |
Apparatus or local circuits for step-by-step systems | |
Apparatus or local circuits for mosaic printer telegraph systems | |
Apparatus or local circuits for systems adapted for orthogonal signalling |
Attention is drawn to the following places, which may be of interest for search:
Arrangements in which pulses are delivered at different times at several outputs, i.e. pulse distributors | |
Switching arrangements with several input- or output-terminals, e.g. multiplexers, distributors | |
Distributors combined with modulators or demodulators |
This place covers:
Bit or symbol synchronization of digital receivers.
Synchronization of packets or bursts in radio or optical transmission.
Bit or symbol synchronization of digital recording system, if this system is not specially adapted to recording.
Bit or symbol synchronization of in a memory system, if the system is not specially adapted to memorizing.
This place does not cover:
Attention is drawn to the following places, which may be of interest for search:
Synchronization of OFDM | |
Synchronisation of electronic time-pieces | |
Recording | |
Memory systems | |
Synchronization in CDMA | |
Synchronization of frames and in TDM networks, including timestamps | |
Synchronising in TV system | |
Regeneration of clock signals for television systems |
In this place, the following terms or expressions are used with the meaning indicated:
OFDM | Orthogonal Frequency Division Multiplexing |
CDMA | Code Division Multiple Access |
TDM | Time Division Multiplex |
PLL | Phase Locked Loop |
DLL | Delay Locked Loop |
This place covers:
Calibration of synchronizers.
H04L 7/0075 and H04L 7/10 take precedence.
This place covers:
Source synchronous systems.
Transmission of clock on a dedicated channel, line or link.
Clockwise and counterclockwise clock distribution.
Clock distributed as sinus or standing wave
This place does not cover:
This place covers:
The received clock is compared with a local clock of the receiver. The comparison controls the synchronisation.
This place does not cover:
Synchronization of received clock and local clock by PLL or DLL, H03L 7/00 takes precedence.
This place covers:
Correction of the synchronisation error in receiver or transmitter
This place does not cover:
Detection of synchronisation error by means of signal transition, e.g. PLL |
This place covers:
Applies also to clock interpolation in the transmitter for the purpose of synchronisation.
If clock interpolation for synchronization is performed at the transmitter, also H04L 7/0091 should be applied.
This place covers:
Covers interpolation of received clock of source synchronous systems.
Covers interpolation of local, e.g. interpolation among several local phase shifted clocks.
Attention is drawn to the following places, which may be of interest for search:
Selection out of many clock phases for synchronisation, e.g. phase picking, if the control uses transitions of the received data |
Attention is drawn to the following places, which may be of interest for search:
Detection of synchronization error by monitoring at least on equalizer tap weight | |
Equalizers per se | |
Rate adaption | |
Digital Filters, e.g. FIR Filter |
In patent documents, the following abbreviations are often used:
SRC | Sample Rate Conversion |
This place covers:
Delay of other signals than clock or information data, e.g. delay of additional signalling among transmitter and receiver
This place does not cover:
Delay of command signals specific for memory systems, e.g. strobe signal DQS |
Attention is drawn to the following places, which may be of interest for search:
Selection out of many clock phases for synchronisation, e.g. phase picking, if the control uses transitions of the received data |
This place covers:
Delay of a received clock signal, e.g. a clock signal received by via a clock line. Delay of a clock signal in the receiver or in the transmitter
This place does not cover:
H04L 7/0337 takes precedence if the synchronization makes use of the transitions of the received data signal
This place covers:
Delay of a received data signal.
Delay of the data signal in the transmitter, e.g. the transmitter receiver an information regarding the synchronisation error.
This place does not cover:
H04L 7/0337 takes precedence if the synchronization makes use of the transitions of the received data signal
This place covers:
An elastic buffer or FIFO is used to compensate the synchronisation error
Attention is drawn to the following places, which may be of interest for search:
Rate adaption, e.g. from 8 kHz to 9.2 kHz | |
Elastic buffers in computer systems | |
Synchronisation using elastic buffers in time multiplexing systems or packet multiplexing systems |
In this place, the following terms or expressions are used with the meaning indicated:
FIFO | First-In First-Out buffer |
This place covers:
Synchronization by sample processing, e.g. Wave-Difference-Method.
Determination of gradients.
This place does not cover:
By means of signal transition |
Synchronization by determining maximum of first derivation of sampled waveform as estimate of zero or threshold crossing: H04L 7/0334 takes precedence.
Synchronization by determining zero of the second derivation of the sampled waveform: H04L 7/007 takes precedence.
This place covers:
Detection of error by monitoring of equalizer taps, e.g. center tap tracking.
This place covers:
Error of the data decision, e.g. subtracting input from output of the decision device, to control synchronisation.
Timing Function: Combining of the error with input signals or not decided symbols.
Attention is drawn to the following places, which may be of interest for search:
Synchronization based on data transition by sample processing of at least three levels, e.g. soft decisions. |
This place covers:
Synchronization using properties of line codes like Manchester, PPM or RZ. Synchronization using properties of block codes as 4b/5b.
Also covers violations of such coding rules to transmit synch information.
Attention is drawn to the following places, which may be of interest for search:
Line coding | |
Block coding mb/nb |
In this place, the following terms or expressions are used with the meaning indicated:
PPM | Pulse Position Modulation |
This place covers:
Covers SCCL detectors, Sample Correlate Choose Largest.
Attention is drawn to the following places, which may be of interest for search:
Synchronization by maximum signal power on symbols known to the receiver, e.g. fixed synchronization information or UW. Correlation of UW for synchronization |
In this place, the following terms or expressions are used with the meaning indicated:
UW | Unique Word |
This place covers:
This group covers clock synchronisation using at least one optical device that is essential for the functioning of the synchronizer. A synchronizer used in an optical transmission system but using exclusively electrical means for synchronization has to be classified in the other respective groups of H04L 7/00.
Attention is drawn to the following places, which may be of interest for search:
Non-linear optical devices | |
Computer systems or integrated circuits with clock distribution at least partially optical | |
Optical regenerators and retiming, e.g. 2R,3R | |
Optical TDM, alignment of optical frames and time slots |
In patent documents, the following abbreviations are often used:
NOLM | Non-linear Optical Loop Mirror |
TOAD | Terahertz Optical Asymmetric Demultiplexer |
This place covers:
Details in the construction of the synchronizer in the receiver, e.g. adaption of signals among various parts of the receiver; constructional details
Attention is drawn to the following places, which may be of interest for search:
Details of RF receivers |
Attention is drawn to the following places, which may be of interest for search:
Introducing fill or idle bits into the data to maintain synchronization | |
Error detection or correction of clock faults in computer systems | |
PLL or DLL with redundancy | |
PLL or DLL with arrangements for protection against power supply fail | |
Fail safe clock arrangements in TDM equipment |
This class can be applied additionally to any other class in H04L 7/00
Attention is drawn to the following places, which may be of interest for search:
Synchronization by spectral filtering |
This place covers:
The transmitter is adapted to the synchronisation process, e.g. the receiver provides signalling concerning the synchronisation error to the transmitter.
This place covers:
The error is based on the received code signal.
Synchronisation is achieved by intermediate buffering, multiple phases and/or intermediate clocks. Synchronisation of interfaces or among equipments having different clock phases or clock domains
This place does not cover:
with photonic or optical means |
Attention is drawn to the following places, which may be of interest for search:
Synchronization based on transition of the received code signal | |
Using the properties of error detecting or error correcting codes | |
Computer systems with synchronization between clock domains | |
Computer systems with buffering between clock domains | |
Tuning resonant circuits | |
Bistable circuits with means to increase reliability, e.g. avoid metastability |
This place covers:
A spectral line at clock rate of NRZ data can be generated, e.g. by squaring or differentiating and subsequent filtering, e.g. SAW filter or FFT.
Covers detection of synchronization error by measuring a spectral property of a known code signal, e.g. UW or dotting.
Attention is drawn to the following places, which may be of interest for search:
Repeaters with retiming | |
Manipulating pulses with desired output intervals by the use of time reference signals, e.g. clock signals | |
Manipulating pulses by resonant circuits |
In patent documents, the following abbreviations are often used:
Dotting | Sequence of alternating pulses, e.g. 1010.. |
UW | Unique Word |
This place covers:
PLL with edge detectors, and at least partial analog loop elements, e.g. VCO;
Edge detectors like HOGGE type or ALEXANDER type.
The term "control" does not limit the scope to "tracking" or "closed loop" but includes also feed-forward control.
Attention is drawn to the following places, which may be of interest for search:
Measuring phase angle between a voltage and a current | |
Transition or edge detectors | |
PLL or DLL |
Initialization of the PLL is further classified in H04L 7/0004.
Special adaptions for preventing loss of synchronization or loss of lock are also classified in H04L 7/0083
This place covers:
This group also covers detection of the synchronization error by measuring the length of the received bits, e.g. by oversampling and sample processing of binary samples.
Covers correction of the synchronization error by add/subtract logic.
Digital implementation of DTTL.
Attention is drawn to the following places, which may be of interest for search:
Synchronization by integrate/dump | |
Selection or interpolation among plural phase shifted clocks | |
Comparing the phase or frequency | |
DPLL in general |
H04L 7/0337 takes precedence
For the pulse length measurement is done by analogue means, e.g. integrate/dump, H04L 7/0332 takes precedence.
In patent documents, the following abbreviations are often used:
PWD | Pulse Width Distortion |
DTTL | Data Transition Tracking Loop |
This place covers:
Analogue techniques of determining the synchronization error by measuring a pulse length esp. for line codes with a transition in the bit cell like Manchester coding or NRZI.
Analogue implementation of DTTL.
This place does not cover:
Digital implementation of DTTL |
Attention is drawn to the following places, which may be of interest for search:
Line coding |
In this place, the following terms or expressions are used with the meaning indicated:
DTTL | Data Transition Tracking Loop |
This place covers:
Samples processed of more than binary values, if the processing evaluates a symbol transition.
First and also higher order derivatives of the sampled waveform, if a transition is detected.
Statistical analysis of the samples, e.g. histogram.
This place does not cover:
Synchronization by detection of decision error of samples |
Attention is drawn to the following places, which may be of interest for search:
Demodulators |
This place covers:
The selected phase is looped back into the phase error detection.
Comparison of the actually selected phase with a previously selected phase is not feed backward under this definition. Such a comparison functions as a filter, e.g. for reducing large phase jumps or jitter.
Phase aligners in switches of communication networks or packet receivers.
Phase aligners for electronic displays, e.g. DVI or HDMI interfaces, if the invention is not specially adapted to such a display, e.g. using special signals.
Synchronization by phase picking.
Covers also interpolation among different clock phases.
Attention is drawn to the following places, which may be of interest for search:
Computer interfaces or busses | |
Electronic displays | |
Synchronization in a TDM node |
Selection in an open loop control: H04L 7/0338 takes precedence.
This place covers:
Documents that only refer to the use of a synchronisation signal, e.g. UW, without further specifying their structure or the way it is detected.
Comma free codes.
Forbidden code words.
Synchronization signals in TDM frames: H04J 3/0602.
This place does not cover:
With photonic or optical means |
Attention is drawn to the following places, which may be of interest for search:
Arrangements for synchronising receiver with transmitter | |
Synchronization information for carrier synchronization in demodulators | |
For changing the speed of data flow, i.e. speed regularizing |
Special synchronisation signals, e.g. midambles or variable UW: H04L 7/041.
In patent documents, the following abbreviations are often used:
Dotting | Alternating 1010... sequence or sequence of complex phase reversal, e.g. ABAB constellation points during training of a MODEM |
UW | Unique Word as generic synonym for synchronisation data in the received signal. |
This place covers:
Code construction.
Theory of codes used for synchronization.
Training sequences or midambles.
Variable Synchronization codes, e.g. according to synchronization state or for transmission of low rate data like signalling.
Attention is drawn to the following places, which may be of interest for search:
Training sequences for carrier synchronisation | |
Corresponding special codes for TDM frames |
This place covers:
Cross-correlation or auto-correlation.
Peak detection, threshold control at the output of the correlator.
Attention is drawn to the following places, which may be of interest for search:
Correlation computing | |
Detectors of FAW in TDM frames | |
Selective call receivers |
Windowing around expected location of the synchronization information, H04L 7/08 takes precedence.
Synchronization state machines or diagrams for acquisition, search, verify or lock, H04L 7/10 takes precedence.
In patent documents, the following abbreviations are often used:
UW | Unique Word. This term is even used even if the bits of the synchronization information could occur in other places of the received data, e.g. mimic in the payload |
This place covers:
PN codes used for synchronisation, if the PN synchronisation signals is varying during transmission, e.g. by a feedback shift-register. Fixed synchronisation signals, e.g. unique words, FAW signals, are not to be classified in this group. This also applies even if the synchronisation signal can be presented as a state of such a PN-code generator. Only if the generator is active and shifts, then the document is classified here.
This place does not cover:
Scrambling | |
Synchronisation of Spread Spectrum receivers | |
PN codes for synchronization of TDM frames |
In this place, the following terms or expressions are used with the meaning indicated:
PN code | Pseudo-Noise or pseudorandom code |
FAW | Frame Alignment Word |
This place covers:
Synchronization by using a start bit or start/stop bit, incl. the use of the transition of the stop bit to the adjacent start bit.
Covers single synch pulses with differing length from information pulse length.
This place does not cover:
Two or more pulses with differing length compared to the length of the data bits |
Attention is drawn to the following places, which may be of interest for search:
Start/Stop transmission in general |
This place covers:
Complex phase reversals used for symbol synchronization in digital demodulators.
This place does not cover:
Transmission of a dotting sequence without further transmission of user data is a transmission of a clock signal |
Attention is drawn to the following places, which may be of interest for search:
Detection of dotting by spectral analysis, e.g. filter around basic frequency | |
If the dotting is degraded at the receiver to a sinus | |
Digital demodulators |
In this place, the following terms or expressions are used with the meaning indicated:
Dotting sequence | Alternating sequence, e.g. 1010... , 01010, ABAB |
This place covers:
Use of Error Correcting or detecting codes for alignment of packets or ATM cells.
Attention is drawn to the following places, which may be of interest for search:
Error Detection or correction codes in general, e.g. ECC or FEC | |
Synchronisation based on error coding or decoding or code conversion |
In this place, the following terms or expressions are used with the meaning indicated:
ATM | Asynchronous Transfer Mode |
This place covers:
H04L as such is directed to transmission of digital signals, meaninig the information is transmitted in binary form. Synchronisation signals classified here have a different form than the information signal, e.g. a higher amplitude, a longer pulse width.
Attention is drawn to the following places, which may be of interest for search:
Detection the differing parameter based on the coding rule | |
Detection of the differing length by a digital means | |
Single pulse for synchronization | |
Line codes and detectors therefore |
This place covers:
Synchronisation information is not transmitted in series with the information signals, i.e. as this is the case for packet headers. Instead, a synchronisation signal is provided by modulation of the information signal, e.g. by an amplitude modulation using a low modulation index
This place covers:
Detection by windowing around the expected recurring location of the synchronization information.
This place does not cover:
Frame synchronization of TDM frames |
This place covers:
Variable synchronization information for initialisation.
During initialisation, variable means of the detector, e.g. low detection threshold and increasing threshold when synchronisation information is detected.
Signalling or handshaking for initialisation.
This place does not cover:
Details of the phase-locked loop for assuring initial synchronisation |
Other means for synchronisation, H04L 7/0004 takes precedence.
Start/Stop bit detection, H04L 7/044 takes precedence.
Dotting detection, H04L 7/046 takes precedence.
This place covers:
Cryptographic mechanisms including cryptographic protocols and cryptographic algorithms, whereby a cryptographic protocol is a distributed cryptographic algorithm defined by a sequence of steps precisely specifying the actions required of two or more entities to achieve specific security objectives (e.g. cryptographic protocol for key agreement), and whereby a cryptographic algorithm is specifying the steps followed by a single entity to achieve specific security objectives (e.g. cryptographic algorithm for symmetric key encryption).
H04L 9/00 focuses on cryptographic mechanisms such as encryption schemes, digital signatures, hash functions, random number generation, key management, said cryptographic mechanisms providing information security such as privacy or confidentiality, data integrity, message authentication, entity authentication, authorization, validation, certification, time-stamping.
H04L 9/00 covers also Financial cryptography.
H04L 9/00 covers also countermeasures against attacks on cryptographic mechanisms.
H04L 63/00 Networking architectures and network communication protocols for securing the traffic flowing through data packet networks and providing secure exchanges among applications communicating through data packet networks.
H04L 63/00 covers specifically network architectures and network communication protocols for supporting:
- filtering (e.g. transferring, blocking, dropping) traffic according to security rules;
- authenticating and authorizing the entities sending and/or receiving the traffic;
- protecting the data packets against unauthorized reading or modification;
- detecting intruders and preventing the transmission of unauthorized, malicious or forged packets;
- lawful interception for legally authorised parties to access protected information.
H04L 63/00 focuses on network architectures (i.e. network entities involved, roles played by these entities) and network communication protocols (i.e. how these network entities communicate) regardless of the specifics of the cryptographic mechanism used.
G06F 21/00 Security arrangements for protecting computers or computer systems against unauthorised activity, where the cryptographic mechanisms are not relevant.
Attention is drawn to the following places, which may be of interest for search:
Network architectures or network communication protocols for network security | |
Pseudo-random number generators (if not intended for cryptographic purposes) | |
Finite field arithmetic over elliptic curve (if not intended for cryptographic purposes) | |
Protection against unauthorized use of memory | |
Pattern recognition | |
Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity | |
Payments on Internet | |
Smarts-cards | |
Coding or ciphering apparatuses for cryptographic or other purposes involving the need for secrecy | |
Circuits for prevention of unauthorised reproduction | |
Aspects related to secret communication for (analogue) speech signals | |
Secrecy systems for scanning, transmission or reproduction of documents | |
Subscription TV encryption | |
Content distribution | |
Network architectures or network communication protocols for wireless network security |
The classification of additional information is not seen as mandatory; it will be up to the classifier to decide whether the additional information should be classified or not (is pertinent or not). If considered pertinent, it should be classified.
Indexing Codes are to be used as orthogonal cross.
Invention may be assign more than one code if necessary.
In patent documents, the following abbreviations are often used:
MAC | Message authentication code |
DPA | Differential power analysis |
SPA | Simple power analysis |
PRNG | Pseudo random number generator |
PKI | Public key infrastructure |
KDC | Key distribution server |
TTP | Trusted third party |
CA | Certificate authority |
IBE | Identity based encryption |
DH | Diffie-Hellman |
QKD | Quantum key distribution |
TPM | Trusted platform module |
PUF | Physically unclonable function |
CRL | Certificate revocation list |
In patent documents, the following words/expressions are often used as synonyms:
- "encryption" and "ciphering"
This place covers:
Subject-matter directed to protection and enhancement of cryptographic mechanisms against cryptographic attacks as replay, brute force or birthday attacks.
This place does not cover:
Network architectures or network communication protocols for protection against malicious traffic |
This place covers:
Subject-matter directed to authentication infrastructures based on public-key cryptography.
This place does not cover:
Network architecture or network communication protocol for supporting authentication of entities using certificates in a packet data network |
This place covers:
Subject-matter directed to homomorphic cryptographic mechanisms.
This place covers:
Subject-matter directed to symmetric-key encryption as DES, (i.e. same keys are used for encryption and decryption), hash functions as MD5, stream ciphers as RC4 or pseudorandom sequence generation.
This place covers:
Encrypting groups of characters of a plain text message using a fixed encryption transformation.
This place covers:
Subject-matter directed to cryptographic mechanisms as Feistel based algorithms, DES, FEAL, IDEA or KASUMI algorithms.
This place covers:
Ciphers composed of a number of stages/rounds each involving linear or nonlinear transformations, as AES algorithm.
This place covers:
Subject-matter directed to modes of operation for block ciphers, as CBC (cipher block chaining), CFB (cipher feedback) or OFB (output feedback).
This place covers:
The design, structure or function of cryptographic hash functions, as message authentication codes (MAC) or modification detection codes (MDC).
This place covers:
Subject-matter directed to synchronous or asynchronous stream ciphers (i.e. encrypting individual characters of a plaintext message one at a time, using an encryption transformation which varies with time), and to key-stream generation.
This place covers:
Subject-matter directed to encryption (combination) of data with (pseudo)random key-stream.
This place covers:
Subject-matter directed to the design, structure, functionality or mechanism of pseudorandom sequence generators.
This place covers:
Subject-matter directed to the design, structure, functionality or mechanism of pseudorandom sequence generators using non-linear functions.
This place covers:
Subject-matter directed to management of secret material including generation, distribution, sharing, updating of cryptographic keys or passwords.
This place does not cover:
Network architectures or network communication protocols for supporting key management in a packet data network |
This place covers:
Subject-matter directed to processes or cryptographic protocols whereby a secret (as cryptographic key, password) becomes available to two or more parties, for subsequent cryptographic use.
This place covers:
Subject-matter directed to key establishment techniques where one party creates or otherwise obtains a secret value, and securely transfers it to other(s).
This place does not cover:
Network architectures or network communication protocols for key distribution in a packet data network |
This place covers:
Subject-matter directed to managing (e.g. transport, distribute) cryptographic keys for securing information by using key encryption keys. Before transmission/distribution the cryptographic keys are encrypted with the key encryption keys. Passwords may be also used as cryptographic keys for encryption.
This place covers:
Subject-matter directed to managing (e.g. transport, distribute) cryptographic keys for securing information by using public key encryption. The cryptographic key is either encrypted with a private key (i.e. signature) and decrypted with the corresponding public key, or it is encrypted with a public key and decrypted with the corresponding private key. A public key infrastructure (PKI) may be also used wherein the public keys are certified.
This place covers:
Subject-matter directed to exchanging/distributing cryptographic keys between communication partners by using distinctive intermediate devices or communication paths/channels. The paths/channels may be out-of-band channels or virtual paths.
This place does not cover:
Network architectures or network communication protocols using different networks |
This place covers:
Subject-matter directed to centralized key units as key distribution center (KDC), trusted third party (TTP) or key translation center (KTC) that are used for cryptographic key management.
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 546-549.
This place covers:
Subject-matter directed to secure mechanisms for distributing cryptographic group keys to different communication entities. To ensure the security of a multi-party communication, the multi-party communication messages are transmitted in encrypted form. The group key used for encrypting and decrypting the multi-party communication messages are only known to the group members, so as to ensure that the encrypted messages may be interpreted only by the group members.
This place does not cover:
Network architectures or network communication protocols for key management in group communication in a packet data network |
This place covers:
Subject-matter directed to mechanisms for distributing cryptographic conference or group keys to different communication entities involving tree or hierarchical structures wherein the central key unit is the root and the group members are the leafs.
This place covers:
Subject-matter directed to key establishment techniques in which a shared key is derived by parties as a function of information contributed by, or associated with, each of these, ideally such that no party can predetermine the resulting value.
This place does not cover:
Network architectures or network communication protocols for key exchange in a packet data network |
This place covers:
Subject-matter directed to key agreement protocols that allow users or entities to exchange public key values and from these values and knowledge of their own corresponding private keys, securely compute a shared key, allowing for further secure communication.
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 515-516.
This place covers:
Subject-matter directed to key agreement protocols providing user authentication or key authentication, to schemes as ElGamal, MTI, MQV or related protocols, to key agreement protocols using implicitly-certified keys, or to password-authenticated key agreement mechanisms as PAKE (password-authenticated key exchange), EKE (encrypted key exchange) or SPEKE (simple password exponential key exchange).
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 517-523.
This place covers:
Subject-matter directed to key agreement protocols involving IBE schemes (the public key of a user is the binary sequence corresponding to information identifying him in a non-ambiguous way).
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 561-562.
This place covers:
Subject-matter directed to distribution of a secret amongst a group of participants, each of which is allocated a share of the secret; the secret can be reconstructed only when a sufficient number of shares are combined together; individual shares are of no use on their own (threshold schemes).
This place covers:
Subject-matter directed to quantum key distribution (QKD), i.e. the process of using quantum communication to establish a shared key between two parties without a third party learning anything about that key, even if said third party can eavesdrop on all communication between said two parties.
This place does not cover:
Transmission systems employing electromagnetic waves other than radio-waves | |
Wavelength-division multiplex systems |
This place covers:
Subject-matter directed to QKD involving additional nodes as quantum relays, repeaters, intermediate or remote nodes.
This place covers:
Subject-matter directed to reconciliation, error correction, privacy amplification, polarisation or phase coding for QKD systems.
This place covers:
Subject-matter directed to generation, derivation, calculation or extraction of cryptographic keys or passwords.
This place covers:
Subject-matter directed to derivation or generation of encryption keys from passwords.
This place does not cover:
Network architectures or network communication protocols for using one-time keys in a packet data network |
This place covers:
Subject-matter directed to cryptographic key derivation or extraction involving user or device identifiers as serial number of a device, measurable physical characteristics provided by a device like a PUF (physical unclonable function), or biometrical information of a user.
This place covers:
Subject-matter directed to cryptographic mechanisms for cryptographic keys generation involving random numbers or seeds.
This place covers:
Subject-matter directed to cryptographic key derivation/generation using data regarding geographical position, time, relative or proximity position to other entities.
This place covers:
Subject-matter directed to mechanisms for cryptographic key generation / derivation using channel characteristics.
This place covers:
Subject-matter directed to cryptographic keys generation using secure crypto-processors as trusted platform modules, smartcards or hardware security modules.
This place covers:
Subject-matter relating to cryptographic techniques (as control vectors, key notarization) for restricting cryptographic keys to pre-authorized uses, to crypto-periods of keys (long-term, short-term, ephemeral keys), or to controlling encryption strength (export regulation for cryptographic algorithms).
This place does not cover:
Network architectures or network communication protocols for using time-dependent keys in a packet data network |
This place covers:
Subject-matter relating to cryptographic keys revocation (compromised keys have to be revoked) or updating (old key is replaced by new key).
This place covers:
Subject-matter directed to cryptographic mechanisms for secret key escrow (user traffic is encrypted such that the session keys used for the encryption are available to properly authorized third parties under special circumstances), for secret key recovery (encrypted data have to be recovered following loss or destruction of keying material due to equipment failure or malicious activities), or for storing/restoring of secret keys (as backups).
This place covers:
Subject-matter directed to involving additional (portable) units (as TPM, smartcards) in the cryptographic mechanisms for escrow, recovery or storing of secret information.
This place covers:
Subject-matter directed to cryptographic mechanisms using a plurality of keys or algorithms (as hybrid encryption, i.e. combination of symmetric and public-key encryption) for providing information security.
Attention is drawn to the following places, which may be of interest for search:
Network architectures or network communication protocols wherein the sending and receiving network entities apply hybrid encryption, i.e. combination of symmetric and asymmetric encryption |
This place covers:
Subject-matter directed to cryptographic mechanisms using a plurality of keys or algorithms changing dynamically or during operation.
This place covers:
Subject-matter directed to asymmetric-key or public key cryptography.
This place covers:
Subject-matter directed to the interaction between the intractability of several computational problems (as the quadratic residuosity problem) and the security of public-key cryptosystems, or to details relating to public-key parameters (as generators and elements of high order).
This place covers:
Subject-matter directed to public-key schemes based on the discrete logarithm problem.
This place covers:
Subject-matter directed to public-key schemes based on the integer factorization problem.
This place covers:
Subject-matter directed to polynomials generation in public-key schemes.
This place covers:
Subject-matter directed to pseudo-prime or prime number generation in public-key schemes.
This place covers:
Subject-matter directed to public-key schemes involving error correction codes.
This place covers:
Subject-matter directed to details of the algebraic or abelian varieties used in the public-key cryptographic schemes, as algebraic groups, rings, fields or elliptic curves.
This place covers:
Subject-matter directed to public-key schemes involving pairings or mappings, as identity based encryption (IBE) schemes.
This place covers:
Subject-matter directed to public-key schemes involving Lattices (e.g. vector spaces) or polynomial equations.
This place covers:
Subject-matter directed to cryptographic mechanisms for authentication or identification, including mechanisms (involving cryptographic primitives or data structures as signatures, certificates, credentials) for authorization, entity authentication, message authentication, data integrity, key authentication, non-repudiation, verification or proof of knowledge.
This place covers:
Subject-matter directed to cryptographic mechanisms for authentication between two devices involving a third device.
This place covers:
Subject-matter directed to cryptographic mechanisms for authentication using tickets or tokens (as Kerberos authentication protocols).
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 501-502.
This place does not cover:
Network architectures or network communication protocols for entities authentication using tickets in a packet data network |
This place covers:
Subject-matter directed to authentication involving the use of a plurality of channels, as for example the use of a wire channel and a wireless channel.
This place does not cover:
Network architectures or network communication protocols using different networks |
This place covers:
Subject-matter directed to identification mechanisms using knowledge proofs, as (NIZKP) non-interactive zero-knowledge proofs (Fiat-Shamir, Schnorr protocols).
This place covers:
Subject-matter directed to identification mechanisms using interactive zero-knowledge proofs.
This place covers:
Subject-matter directed to cryptographic mechanisms for authentication or authorization using predetermined codes as passwords, passphrases, personal identification numbers (PIN).
This place does not cover:
Network architectures or network communication protocols for supporting authentication of entities using passwords in a packet data network |
This place covers:
Subject-matter directed to authentication or authorization using predetermined codes, said predetermined codes comprising information which is sent for every authentication or authorization, as one-time-password, one-time-token or one-time-key.
This place covers:
Subject-matter directed to cryptographic mechanisms for identification or verification of an individual using biometrical data as fingerprint, voice or retina.
This place does not cover:
Network architectures or network communication protocols for supporting authentication of entities using biometrical features in a packet data network |
This place covers:
Subject-matter directed to cryptographic mechanisms for authentication or authorization involving hardware tokens like trusted platform module (TPM), smartcard, USB or software tokens.
This place does not cover:
Network architectures or network communication protocols for supporting authentication of entities using an additional device in a packet data network |
This place covers:
Subject-matter directed to authentication mechanisms using cryptographic hash functions.
This place covers:
Subject-matter directed to authentication mechanisms involving modification detection codes (MDC's) as MD5, SHA or RIPEMD, also called non-keyed hash functions.
This place covers:
Subject-matter directed to authentication mechanisms involving message authentication codes (MAC's) as CBC-MAC or HMAC, also called keyed hash functions.
This place covers:
Subject-matter directed to authentication mechanisms involving digital signatures.
This place covers:
Subject-matter directed to authentication mechanisms involving RSA or related signature schemes, as the Rabin signature scheme.
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 433-447.
This place covers:
Subject-matter directed to authentication mechanisms involving DSA or related signature schemes, as elliptic curve digital signature algorithm ECDSA or ElGamal signature scheme.
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 452-462.
This place covers:
Subject-matter directed to authentication mechanisms using digital signatures where signers can establish groups such that each member of the group can produce signatures anonymously on behalf of the group.
This place covers:
Subject-matter directed to authentication mechanisms using signatures schemes in which the content of a message is disguised before it is signed.
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Page 475.
This place covers:
Subject-matter directed to cryptographic mechanisms involving digital certificates as public key certificates or attribute certificates, or to public key infrastructure (PKI) based authentication/verification using certificates.
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 559-561.
This place does not cover:
Network architectures or network communication protocols for supporting authentication of entities using certificates in a packet data network |
This place covers:
Subject-matter directed to authentication mechanisms involving multiple certification authorities (CA) in public-key systems. Trust relationships between the CA's determine how certificates issued by one CA may be utilized or verified by entities certified by distinct CA's. Hierarchical trust models for certification and cross-certificates are also covered by this subgroup.
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 572-575.
This place covers:
Subject-matter directed to cryptographic mechanisms involving certificate generation, validation, registration, distribution (pull, push model) or revocation (certificate revocation list CRL).
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 576-577.
This place covers:
Subject-matter directed to cryptographic mechanisms comprising protocols where a verifier sends a claimant a challenge (usually a random value or a nonce) that the claimant combines with a shared secret (often by hashing the challenge and secret together) to generate a response that is sent to the verifier. The verifier knows the shared secret and can independently compute the response and compare it with the response generated by the claimant.
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 397-405.
This place covers:
Subject-matter directed to authentication between parties that may corroborate their identities to the other.
This place does not cover:
Network architectures or network communication protocols for achieving mutual authentication in a packet data network |
This place covers:
Subject-matter directed to authentication using PUF.
This place covers:
Subject-matter directed to cryptographic mechanisms for authentication involving time stamps or generation of timestamps.
Examples: "Handbook of Applied Cryptography" by A.J. Menezes, P.C. van Oorschot, S. A. Vanstone, 5th Edition, June 2001, Pages 581-583.
This place covers:
Subject-matter directed to cryptographic mechanisms involving interchanging in time bits or block of bits of the message.
This place does not cover:
by transmitting the information of elements thereof at unnatural speeds or in jumbled order or backwards |
This place covers:
Subject-matter directed to cryptographic mechanisms involving means for detecting characters not meant for transmission.
This place covers:
Subject-matter directed to cryptographic mechanisms involving encryption effected by mechanical apparatus, as rotating cams, switches or key-tape punchers.
This place covers:
Transfer of information having been supplied in digital form in data switching networks, e.g.
Systems characterised by network topology;
Systems in which paths are physically permanent during the communication, e.g. connection oriented communication, virtual circuits;
Systems in which the path identification data is included in each information unit, e.g. connectionless communication, datagram;
Hybrid switching systems;
Arrangements for connecting networks having different types of switching systems;
Topology management and discovery;
Local area networks and interworking arrangements there between;
Flow control and congestion control. Traffic scheduling and balancing;
Routing, pathfinding;
Access control and network resource allocation;
Asynchronous transfer mode networks.
This place does not cover:
Interconnection of, or transfer of information or other signals between, memories, input/output devices or central processing units | |
Interprocessor communication using networks |
Attention is drawn to the following places, which may be of interest for search:
Cryptographic protocols | |
Network security protocols | |
Protocols for real-time services in data packet switching networks | |
Real-time session management in data packet switching networks | |
Network protocols for data switching network services | |
Session management in data packet switching networks | |
Computer-aided management of electronic mailing [e-mailing] | |
Multiplexing systems in general | |
Automatic or semi-automatic exchanges | |
Telephony conferences arrangements | |
Manual exchanges | |
Conferences, e.g. video conferences | |
Selecting equipment |
In this place, the following terms or expressions are used with the meaning indicated:
Circuit switching | A system in which a communication path is physically permanent during the communication |
Packet switching | A system in which information is divided into discrete data units, characterised by a data payload and an address part known as a header part. The data units are able to travel over different communication paths to the destination |
Message switching systems | A system in which a message is sent into a network with the address of its destination added and it is routed to its destination through the network, e.g. electronic mail network systems |
Hybrid switching | Combinations of different switching systems (e.g. packet switching systems and circuit switching systems) |
Gateway | Arrangements for connecting between networks having different types of switching systems |
In patent documents, the following words/expressions are often used as synonyms:
- "packet", "cell" and "frame"
This place covers:
Devices for a human operator manually and/or physically routing or switching communications between source and destination.
Attention is drawn to the following places, which may be of interest for search:
Routing or path finding of packets in data switching networks |
This place covers:
- Usage of an independent power supply network
- Extracting power from the data signal in the line
- Power-over-Ethernet technologies (PoE, PoE+, PoE plus, IEEE 802.2af, IEEE 802.3at)
This groups contains documents dealing with different ways to supply power to terminals connected to a network.
This place does not cover:
Internal power supply in a computer | |
Transmission of data over power lines | |
Current supply to telephones |
Attention is drawn to the following places, which may be of interest for search:
Details regarding the feeding of energy to the node from the bus |
In this place, the following terms or expressions are used with the meaning indicated:
PoE | Power-over-Ethernet |
PSE | Power Sourcing Equipment |
PD | Powered Device |
This place covers:
- Transition between different power-saving modes
- Conditions of entry into a sleep mode
- Wake-on LANs
- Energy Efficient Ethernet (IEEE 802.3az)
It covers activation or deactivation of terminals or nodes connected to a network. Sometimes, a power on/off is involved, while other documents deal more with logical (de-)activations.
This place does not cover:
Power modes management in wireless networks |
Attention is drawn to the following places, which may be of interest for search:
Details regarding the setting of the power status of a node according to activity on a bus |
In this place, the following terms or expressions are used with the meaning indicated:
WoL | Wake-on-LAN |
This place covers:
Aspects of billing, charging, accounting, tariffing for the transport of data packets in wireless or wireline data networks, including data sub networks of voice networks.
When documents disclose aspects of charging or billing in combination with aspects of wired or wireless data or voice communication, e.g. voice over IP (VoIP, VoLTE), then multiple classification should be considered in groups H04L 12/14, H04M 15/00, H04M 17/00 or H04W 4/24.
Examples of places where the subject matter of this place is covered when specially adapted, used for a particular purpose, or incorporated in a larger system:
Arrangements for maintenance or administration with service quality level-based billing | |
Metering arrangements in telephonic communication, such as billing and charging of telephone calls or the billing architecture of telephonic networks | |
Prepayment voice telephony systems | |
Accounting or billing for services or facilities specially adapted for wireless communication |
Attention is drawn to the following places, which may be of interest for search:
Payment schemes, architectures or protocols | |
Commerce |
Features for which there is no matching subgroup under H04L 12/14 should be classified under H04M 15/00 or H04M 17/00 if appropriate subgroups are provided there.
This place covers:
This group is used for features related to the interrelation between network nodes, addition of new network nodes, software downloaded to user, self-billing, sampling, backup of billing data, etc. for charging purposes.
This place covers:
Charging aspects of the Policy and Charging Rules Function / Policy Charging Rules Node, or Policy and Charging Control architectures.
If flow control or admission control aspects are relevant, this is classified in H04L 47/20 , H04L 47/70 or H04W 28/10.
If network maintenance or administration aspects are relevant, this is classified in H04L 41/0893.
This place covers:
Advice of charge (AoC) during a communication.
This place covers:
Advice of charge (AoC) with a threshold, e.g. user indicating maximum cost.
This place covers:
This includes e.g. providing the user a preview of estimated costs before he/she starts a communication, for example before start of a file transfer.
This place covers:
Special fields, for example in IP-headers of SIP-headers, used for charging or billing.
This place does not cover:
Invoicing in general |
This place covers:
This group is used for metric aspects whereby the charging is based neither on volume nor on time, for instance based on distance / number of hops, or the use of more complicated formulas for determining the charging.
This place covers:
This group is used for exceptional volume based charging, for instance only charging for volume of useful data, not overhead data (overhead data being for example: session set-up / tear down, retransmission of erroneous packets).
This place covers:
This group is used for exceptional time based charging, for example only charging for actual transmission time, or time based charging where this would otherwise be uncommon.
This place covers:
This includes for example: clearing of revenue, format conversion, meta format for billing.
This place covers:
This includes for example the exchanges for trading the capacity, or selecting operators / routes based on tariff.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for maintenance or administration with service quality level based billing, |
This place covers:
Aspects of payment or settlement of charges involving interaction with the data transmission network, see the subgroups below.
This place covers:
Payment using e-cash, credit units, tokens, points.
This place covers:
Features related to prepayment accounts are classified here.
The on-line / real-time metering / charging aspects are additionally classified under "Architecture" by tagging with the subgroup code H04L 12/1403.
More detailed features are classified under H04M 17/00.
This place covers:
Cost splitting involving a third party, such as an advertiser, a sponsor.
This could include a discount to the user based on the acceptance of an advertisement where e.g. the advertiser pays the remaining amount.
Even when the third party bears the full cost, this is still classified here.
This place covers:
Cost splitting involving only the communication parties, e.g. the "A" party and the "B" party in a standard two-party communication, or additional parties in case of teleconferencing.
This place covers:
This includes e.g. the use of call detail record CDR, or the Intelligent Network infrastructure.
This place covers:
This includes variable tariff dependent on subscription-contract, time-of day, flow, QoS/diffserv, bandwidth usage.
Aspects related to network maintenance or administration with service quality level based billing are also classified under H04L 41/5029.
This place covers:
This includes variable tariffs dependent on congestion, i.e. congestion pricing.
This place covers:
This includes negotiation of the tariff, between the user and the provider, or between providers. Also automatic negotiation by algorithms, i.e. without user involvement, is classified here.
This place covers:
Discounts on the overall charge where only one communication party, typically the "A" party, pays the cost.
If another communication party is involved, this is classified under H04L 12/1475 .
This place covers:
- Computer conferences, e.g. whiteboard applications or multimedia conferences, which take place (at least partially) over a data switching network.
- Multicast transmission, since it is considered as a kind of restricted broadcast.
It is a subgroup of H04L 12/00 and hence contains only documents with broadcast, multicast or conference arrangements in data switching networks, and where there is a disclosure of subject-matter relevant for the broadcast, multicast or conference per se.
Further details of subgroups
This subgroup is not active and contains networks adapted for stock quotations. Computer supported buying and selling of stocks without network aspects is classified in G06Q 40/04 .
This subgroup is not active and contains networks specifically adapted for auctions. Computer supported auctioneering such as Internet auctions without network aspects is classified in G06Q 30/08 .
This subgroup includes documents regarding data exchange in real-time between a group of user equipment connected to a data-switching network. The documents provide solutions suitable for groups of more than two pieces of user equipment but do not exclude two users in a degenerate situation.
Instant messaging is classified in H04L 51/04.
This subgroup contains documents related to conference administration arrangements for setting up and starting a conference. It covers aspects related to events before the actual conference takes place.
This subgroup contains documents related to conference administration arrangements during the conference itself.
Examples of documents classified here: US2007274460, US7408890, US7426540.
This subgroup contains documents directed to solving problems such as transmission errors and/or delays, and terminals with limited capabilities.
Examples of documents classified here: EP1876755, WO2004008336
This subgroup contains documents directed to the recording of conference content, participant activities and/or behaviour, etc. for later retrieval.
This subgroup contains documents where not all the receivers of the broadcast or multicast data are connected through the same kind of networks, which influences the broadcast/multicast service.
This subgroup contains documents where not all the receivers have the same capabilities, which influences the broadcast/multicast service.
Layered encoding of data as such is classified in H04N 19/00.
The size of the location is not relevant; the data transmission can take place within a room, a building, a city, or a nation etc. (location of the user terminal in data switching networks H04L 67/52; services specially adapted for wireless communication networks making use of the location of users or terminals H04W 4/02)
This subgroup contains inter alia documents related to the IGMP or MLD protocols for joining and leaving a multicast group.
It also contains documents dealing with changes to the multicast service as the result of a node failure or a member joining or leaving the group.
Routing tree calculation is classified in H04L 45/48 .
This subgroup contains documents dealing with systems where the data forwarding to every receiver is also the responsibility of the receivers themselves, e.g. application layer multicast.
This subgroup covers documents where the multicast or broadcast aspect is relevant for the push service, such as pushing common data to a group of users. Pushed-based network services H04L 67/55.
Push systems in relation to Internet retrieval, see G06F 16/951.
This subgroup contains documents dealing with the problem of how to make sure that each receiver has received the data and what to do when this is not the case.
This subgroup contains documents dealing with any action (e.g. verifications, increased resources, alternative paths, etc.) taken prior to transmission in order to ensure network reliability. Arrangements for detecting or preventing errors in received information in general, see H04L 1/00.
This subgroup contains documents concerning the transmission order of multicast and/or broadcast data packets onto the network, e.g. vis-à-vis unicast data.
The restrictions are for instance applied to avoid flooding of data by dividing the recipients into multicast groups or using subnets or subdomains.
This subgroup only contains documents dealing with multicast or broadcast problems that are a result of (at least some) network links being wireless, e.g. intermittent connectivity or bandwidth constraints.
Documents concerned with the wireless part of the network for broadcast or multicast services such as MBMS are classified in H04W 4/06, e.g. radio channel allocation.
This subgroup contains documents where real-time information is unidirectionally communicated to a group of recipients.
H04H: Broadcast communication in broadcast networks, e.g. radio or television networks.
H04N: Pictorial communication, e.g. television.
Attention is drawn to the following places, which may be of interest for search:
Routing aspects for multicast | |
Flow control for multicast | |
Packet switches for multicast or broadcast | |
Arrangements for multi-party communication, e.g. for conferences | |
Push-to services, e.g. push-to-talk or push-to-video | |
Network services for supporting one-way streaming services | |
Telephone conferences | |
Video conferences | |
Arrangements for the radio link of a wireless network for broadcast or multicast services such as MBMS, e.g. radio channel allocation | |
Push-to-Talk [PTT] or Push-On-Call services |
The rule for classification in this group is "multiple places, no priority". This means that a document should be classified in all the subgroups that are appropriate for the document.
In this place, the following terms or expressions are used with the meaning indicated:
Chat room | A chat room is a special type of computer conference where the users normally are not aware of the (true) identities of other participants' before joining the chat. The chat room application executes mainly on a server which is often accessed through a web browser. No participant has control over the admission of other participants. |
Instant messaging, IM | Instant messaging is data exchange in real-time between at least two end users connected to a packet-switching network where the users are aware of the identity and the presence of the other party or parties before starting the data exchange. |
This place does not cover:
Instant messaging | |
Protocols for multimedia communication | |
Arrangements for multi-party communication | |
Telephonic conference arrangements | |
Television conference systems |
This place does not cover:
Protocols for adapting network applications to user terminal location | |
Services specially adapted for wireless communication networks making use of the location of users or terminals |
This subgroup was initially used to classify network security aspects, which are now classified in:
- H04L 63/00: Network architectures or network communication protocols for network security and/or
- H04W 12/00: Network architectures or network communication protocols for wireless network security
This place does not cover:
Cryptographic means for verifying the identity or authority of a user of the system |
This place covers:
Header group accommodating those networks whose topology respond to regular LAN topologies (bus, ring or star). His head group contains also WAN and MAN topologies. Documents dealing with very generic network topologies on Layer 2 should be classified here.
This place does not cover:
Wireless communication networks | |
Arrangements for dividing the transmission path |
Attention is drawn to the following places, which may be of interest for search:
Connectivity information management, e.g. connectivity discovery or connectivity update |
This place covers:
- DOCSIS-related technologies (cable modems, cable modem termination systems);
- MoCA networks;
- HFC networks.
This group concerns mostly cable modems and developments of data services on existing cable infrastructures. One can find in this group variations on the basic IEEE 802.14 standard for accessing an optical cable using mostly TDMA. Some architectures for access to video on demand networks using HFC (Hybrid Fibre Coax) physical media. Of course some LANs using ATM as transport technology are also to be fund in the group.
Attention is drawn to the following places, which may be of interest for search:
Cryptographic protocols | |
Point-to-multipoint connection of the data network to end users in an access network | |
Arrangements for combining access network resources elements, e.g. channel bonding | |
Network security protocols | |
Real-time communication protocols in data switching networks | |
Network protocols for data switching network services | |
Telephony over cable network | |
Video on demand and video coding |
In this place, the following terms or expressions are used with the meaning indicated:
DOCSIS | Data Over Cable Service Interface Specification |
CMTS | Cable Modem Termination System |
CM | Cable Modem |
MoCA | Multimedia over COAX Alliance |
This place covers:
Network of appliances in a same home exchanging within said network messages which are generic with regard to the type of appliance.
This group covers all network aspects of domotics.
It covers:
- Transmission media such as power transmission lines or dedicated wiring for controlling home appliances;
- Using the home telephone wiring for building a LAN. HomePNA(Phone-line Networking Alliance).
- Addressing issues concerning the identification of devices in different
- areas of a dwelling
- Network control. Using e.g. a regular TV receiver or dedicated terminal Tapping devices used to connect appliances to the selected wiring (Echelon's LON network).
- Some standard architectures for home control use: CEBUS or FieldBus, PNA.
This place does not cover:
Factory automation | |
Transmission of data over power lines | |
Remote control of lights using a control bus |
Attention is drawn to the following places, which may be of interest for search:
Access arrangements | |
High-speed IEEE 1394 serial bus | |
Single bridge functionality | |
Network monitoring | |
Device-related reporting | |
Monitoring functionality | |
Arrangements for network security | |
Web-based protocols | |
Remote control or remote monitoring of applications in data packet switching networks | |
Discovery or management thereof, e.g. service location protocol [SLP] or web services | |
Protocol conversion | |
Retrieval from the Internet | |
Arrangements for transmitting signals characterised by the use of a wireless electrical link | |
Telephonic communication systems adapted for combination with telemetering systems | |
Telephonic communication systems adapted for combination with remote control systems | |
Adaptations of television systems for transmission by electric cable for domestic distribution | |
Receiver circuitry for displaying additional information being controlled by a remote control apparatus | |
Arrangements in telecontrol or telemetry systems for selectively calling a substation from a main station, in which substation desired apparatus is selected for applying a control signal thereto or for obtaining measured values therefrom |
This group covers all network aspects of domotics.
The following topics are well represented in the group:
Use of networks (involving wireless links, power transmission lines, home telephone wiring) for controlling or monitoring home appliances or for exchanging control messages between audio video appliances.
In the definition above, the following criteria are emphasized:
- There should be at least one network of appliances; this condition is not fulfilled for a simple application of remote control of a heating system by telephone or Internet;
- The devices connected to the network are appliances, i.e. devices having a sensor or actor role in the home automation; a network involving printers and computers (these computers having no appliance function) only does not fulfill this condition;
- There should be general aspects of the network, i.e. aspects which are not specific to a single type of application; this is the case for instance when the invention relates to a message data field used for controlling appliances, but not if the invention concerns specifically the use of a few commands to accomplish a certain operation; this difference can be understood as a difference of layer;
The subgroup relates to control or monitoring with several appliances in a same home; this condition is not fulfilled when the appliances are communicating only via the Internet or the mobile cellular network; this condition is also not fulfilled by the interconnection of audio-video devices with their broadcast network; hotels can be considered as home if the privacy concept coincides with the hotel; building automation of purely mechanical and lighting devices can be considered as a home if it is separate from the city infrastructure.
This place covers:
HAVi networks encompasses connections to control Audio and Video hardware using FireWire.
In this place, the following terms or expressions are used with the meaning indicated:
HAVi | Home Audio Video Interoperability |
This place covers:
Exchange and retrieval of information regarding which element having which attributes are present in the network.
This place does not cover:
for automatically determining the actual topology of a network | |
using GUI (Graphical User Interface) | |
Address allocation |
This place covers:
Exchange of information indicating which services or operations are available on the home network appliances.
This place does not cover:
based on functioning | |
Arrangements for service discovery, e.g. Service Location Protocol |
Attention is drawn to the following places, which may be of interest for search:
Discovering of devices as part of configuration | |
Address allocation to terminals or nodes connected to a network |
This place covers:
Description of capabilities of devices and services in a home network.
Exchange of information describing access methods and parameters of devices or services available on the home network appliances.
Emphasis is on "description", i.e. the data structure indicating the commands and parameters with which control of the operation of a device's appliance can be triggered.
This place does not cover:
Network monitoring | |
Remote control or remote monitoring of applications in data packet switching networks |
This place covers:
Description of contents available in a home network. Exchange of information describing contents available on the home network appliances. Emphasis is on "contents".
This place does not cover:
Web-based protocols | |
Information retrieval from the Internet |
This place covers:
Self explanatory, pieces of software, firmware used to control home appliances.
This place does not cover:
Configuration management of network or network elements |
Attention is drawn to the following places, which may be of interest for search:
Network arrangements or protocols for supporting network services or applications in data packet networks | |
Program loading or initiating |
This place covers:
Exchange of information that triggers action of at least one device.
This place does not cover:
Arrangements in telecontrol or telemetry systems for selectively calling a substation from a main station, in which substation desired apparatus is selected for applying a control signal thereto or for obtaining measured values therefrom |
This place covers:
Complex home network provisions for being remotely accessed. Access to a home network (with at least two appliances) from a device outside the home network.
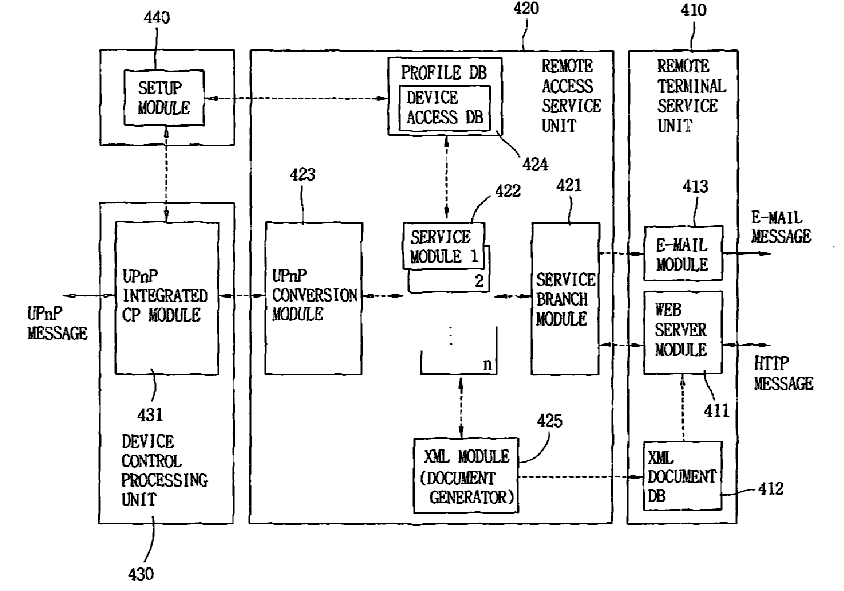
In that example, a device control processor which communicates with a remote access service unit and operating a home network device using universal plug and play (UPnP) message, stores list of controlled devices, each device state, event list and service request list.
The processor converts request/message received from service unit/UPnP device into message/request for transmission to respective units.
This place does not cover:
Access arrangements, e.g. Internet access | |
Remote control or remote monitoring of applications in data packet switching networks | |
Arrangements for transmitting signals characterised by the use of a wireless electrical link | |
Remote control via a telephone connection |
This place covers:
User interaction from within network for the control of appliances, e.g. through remote controller, PDA, cell phone, RF ID etc.
This place does not cover:
User interface for managing and configuring a home network | |
Receiver circuitry for displaying additional information being controlled by a remote control apparatus |
This place covers:
The home appliance or another device prevents the home appliance from having to execute commands which disturb ongoing operations.
This place does not cover:
Cryptographic protocols | |
Network security protocols |
Attention is drawn to the following places, which may be of interest for search:
Network access security |
This place covers:
Exchange of information for reporting or monitoring the operation of home appliances so as to trigger operation of other home appliance functions. The status of a service or the sensed situation of an appliance is advertised on a home network for reaction by other home devices to create an environment conforming to specific rules or profiles.
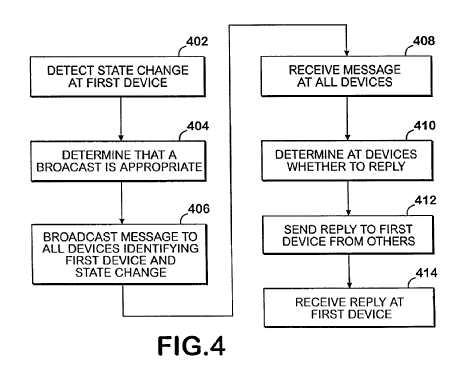
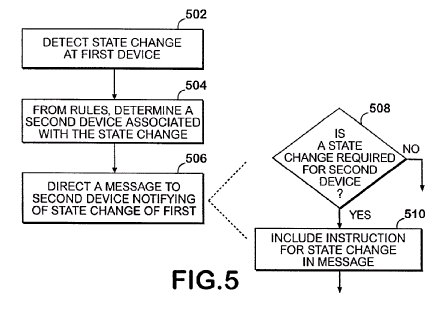
In that document, the rules of device interaction may include instructions that are to be transmitted from the aggregator in response to the aggregator receiving change of state messages from devices of the environment.
This place does not cover:
Advertising the status of network devices | |
Alarm systems in general | |
Arrangements in telecontrol or telemetry systems for selectively calling a substation from a main station, in which substation desired apparatus is selected for applying a control signal thereto or for obtaining measured values therefrom |
This place covers:
Self-explanatory : reporting the operation of home appliances or a particular network event affecting a home appliance to one or more external devices, i.e. to devices outside the home network.
This place does not cover:
Access arrangements | |
For remote control or remote monitoring of applications | |
Telephonic communication systems adapted for combination with telemetering systems |
Attention is drawn to the following places, which may be of interest for search:
Network monitoring in data packet switching networks |
This place covers:
Self explanatory: in contrast to the preceding class, the exchange of messages only occurs among home appliances within the same home automation network.
This place covers:
Self explanatory: a user profile defines rules or a policy for triggering specific actions or the emission of a command to a device in response to the occurrence of an event at a given home appliance.
This place covers:
Device adapted to communicate with different types of networks.
This place covers:
Bridges between home networks (e.g. HAVi/UPNP).
Home gateway performing interface adaptation (also lower layer adaptation, kind of bridge).
This place does not cover:
Single bridge functionality |
Attention is drawn to the following places, which may be of interest for search:
Bridging devices | |
Protocols for interworking; Protocol conversion | |
Multiprotocol handlers, e.g. single devices capable of handling multiple protocols |
This place covers:
Switching (or forwarding, routing) at a gateway between external network(s) and home network(s). Contains operational details on residential/home gateways.
This place does not cover:
Multiplexing of signals from an external network for distribution to the home network | |
Access arrangements | |
Bridging devices |
This place covers:
Protocol conversion between home network(s) and external network(s). If the conversion is only from one controlling protocol to another, the corresponding Indexing Code entry should be used.
This place does not cover:
from a device located outside both the home and the home network | |
Protocol conversion |
Attention is drawn to the following places, which may be of interest for search:
Multiprotocol handlers, e.g. single devices capable of handling multiple protocols |
This place covers:
Distribution of signals within a home network. Data signal distribution from/to appliances within the home network. The mere transmission of signals in a home network without a particular way to convey said signal in the home network should not be classified here.
Example: WO2006100515.
The main aspect of the document is that the signals are all distributed in the home through one Ethernet cable on which all packets are transmitted according to TCP/IP. There are no improvements to the TCP/IP no details on the head end and the switching within the head end. No details about control of devices, that's why signal distribution appears to be the only main aspect within home network.
Second example: US6751441
Signals from cable network are split into TV and data signals; the data signals are modulated at the WLAN frequency but distributed to the rooms along the cables. Within the rooms the signals are radiated through an antenna.
This place does not cover:
Hybrid transport | |
Domestic distribution of TV signals |
This place covers:
A MAN, Metropolitan Area Network, refers to the access technology as well as to the size. The reference book "Computer Networks" written by Tanenbaum gives a definition of it: "A MAN is a network that covers an entire city, but uses LAN technology".
This place covers:
This group is very general about WANs. It contains public data networks such as Frame Relay and X.25 packet networks.
This place covers:
An access network is a part of a global wired communication network that connects subscribers to their service providers in the public data network.
It consists generally of end-user equipments connected to an access multiplexer. The access multiplexer is connected to an access server through an aggregation network, wherein the access server is the interface between the access network and the public data network.
This place does not cover:
Switching of information between an external network and a home network | |
Management of WDM parameters in optical multiplex systems | |
Access arrangements for providing telephone service in networks other than PSTN/ISDN | |
Circuit-switched access networks | |
Telephonic communication systems adapted for combination with other electrical systems | |
Transfer of video data (multimedia streaming) from a video content server to a subscriber | |
Wireless communications networks |
Attention is drawn to the following places, which may be of interest for search:
Access to a packet-switched data network over a hybrid coaxial infrastructure | |
Asynchronous Transfer Mode (ATM) networks | |
Access to open networks | |
Admission & flow control, QoS management | |
Addressing and naming aspects | |
Establishment of secure connections and subscriber authentication | |
Digital subscriber line end-user equipment, DSL modems, xDSL splitters, and bit-level processing of data on PSTN-based network | |
Provision of optical access or distribution networks | |
Wireless access networks |
This place covers:
There are various ways to deploy an access network, but most of them rely on an existing wired infrastructure. Originally, access to the Internet was mostly provided by DSL access technologies, where a point-to point connection between a subscriber and a service provider is provisioned via a PPP over ATM connection, thereby re-using the existing wired network and their functionalities (ATM PVCs). Nowadays, the trend is clearly to integrate Ethernet as carrier technology for access network segments while remaining the main carrier for the backbone networks, thereby coping with the increasing demand for value-added services such as VoIP, HDTV, IPTV and Triple-Play. In parallel to the development of DSL access technologies, broadcast networks such as cable and optical networks are more and more employed to convey data packets in addition to other signal types, such as video or audio streaming.
This place does not cover:
Access to open networks, incl. selection between different service providers |
This place covers:
This group covers essentially the original access technologies wherein a connection between an end-user and the service provider is established by means of a point-to-point protocol, over various types of aggregation networks, such as ATM or Ethernet (PPPoX sessions). This group also includes pseudo-wire techniques, i.e. encapsulation over an IP-based access network.
Attention is drawn to the following places, which may be of interest for search:
Packet Encapsulation | |
Virtual Local Area Networks | |
ATM networks | |
Routing of packets |
This group has a quite broad definition and ideally should not be the only symbol allocated to a document dealing with access networks. Only documents focusing on the access network infrastructure taken as a whole, i.e. from the public data network to the end-user device, implementing a form of point-to-point technology shall be allocated this subclass as unique symbol.
This place covers:
In this entry, new access technologies relying on the existing cable infrastructure (e.g. DOCSIS, MoCA) or optical networks (PONs) are addressed. Data is transmitted over a shared communication medium on the downlink and the uplink. On the downlink, data is broadcast by the service provider to all subscribers, and each subscriber extracts the data which is aimed to him, out of the stream of multiplexed data.
Attention is drawn to the following places, which may be of interest for search:
Broadband Local Area Networks | |
Provision for optical access or packet networks |
See the reasoning for the symbol H04L 12/2859.
This place covers:
Aspects related to an optimized usage of the available access network resources in order to enable provision of greedy multimedia services over bandwidth-limited access networks. This could consist of bundling subscriber lines, arranging a logical combination of network resources, such as frequency bands on a HFC network or the simultaneous usage of multiple PPPoX connections for transporting the same data service.
This place does not cover:
Multichannel or multilink protocols |
Attention is drawn to the following places, which may be of interest for search:
Modem pooling | |
Routing of packets | |
Virtual concatenation in SDH/OTN networks |
This place covers:
Essentially, comprises arrangements for multiplexing individual subscriber connections or grouping of frequency slots on a cable network. The emphasis is on the combination of logical or abstract entities, i.e. frequency or bandwidth resources combinations, not physical entities such as cables or hardware elements.
This place covers:
Refers to the concept of grouping or combining physical access network resources such as devices, interfaces, wires, cables, in order to enhance the total throughput provided to a given subscriber.
This place covers:
Functional characteristics of various devices commonly present in an access network.
Attention is drawn to the following places, which may be of interest for search:
Admission control & resource allocation in access networks |
This place covers:
A remote access server is a device that routes traffic to and from an access multiplexer (e.g. DSLAM) on a public data network.
In this place, the following terms or expressions are used with the meaning indicated:
BRAS | Broadband Remote Access Server |
BAS | Broadband access server |
This place covers:
Covers essentially the handling of PPPoX sessions : how the Point-to-Point sessions are initiated, maintained, or terminated. Only PPPoX-related operations at the remote access server are covered by this subclass.
This place covers:
Details about specific data processing operations for distributing various multimedia flows, originally formatted to optimize their transport through an IP network, over the access network to the subscribers.
The emphasis is on a particular way to re-arrange or adapt a flow received at a remote access server from the public data network before distributing the flow to subscriber(s) over the access network, wherein this particular way reflects the characteristics of the access networks.
Example: a remote access server adds MAC address tag information to a packet received from an ISP.
This place covers:
Differentiated policies for distributing data to subscribers, based for instance on user profiles, time of the day, traffic volume etc.
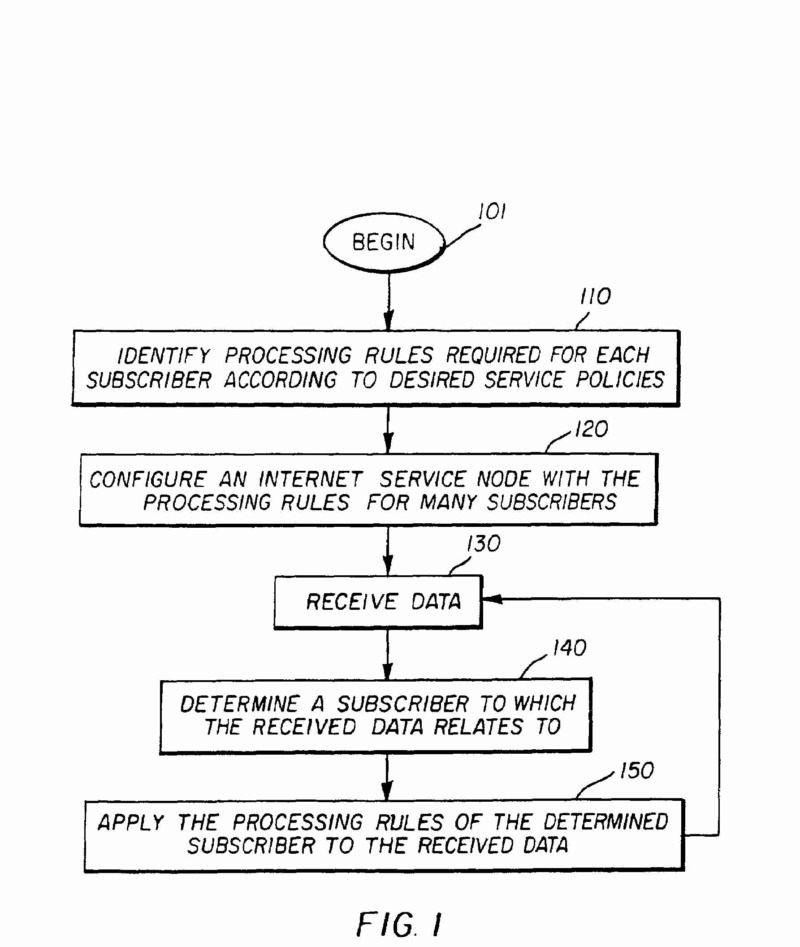
This place does not cover:
Group management policies |
This place covers:
Operational details of an access multiplexer is a device, located normally in a telephone exchange or in multi-dwelling units of a service provider, that connects multiple end-user terminals to a public data network access node (e.g. a BRAS) through an aggregation network. Examples : DSLAM, fiber distribution hubs or active splitters, etc.
Attention is drawn to the following places, which may be of interest for search:
Generic distributed time multiplexers, e.g. TDM/TDMA | |
DSL modem with DSLAM functionalities |
This place covers:
Self-explanatory : this group characterizes the access multiplexer by the type of aggregation network used on the uplink (not to the end-user equipment).
This place covers:
- Optical Line Terminals
- Cable modem Termination System.
This place does not cover:
Determination of optical signal parameters (e.g. wavelength) as a function of data characteristics from Layer-2 or above, like VLAN number, IP address, subscriber profile | |
Optical multiplexers |
In this place, the following terms or expressions are used with the meaning indicated:
OLT | Optical Line Terminals |
CMTS | Cable Modem Termination System |
This place covers:
Self-explanatory: in contrast to the group H04L 12/2879, this group covers the type of connection linking the access multiplexer to subscriber devices.
Normally, a document shall be allocated one of the symbols from this group only when the document focuses on the communication services offered between the access multiplexer and the subscriber devices.
This place covers:
A Multi-service access Node, also known as a Multi-service access gateway is a device typically installed in a telephone exchange (although sometimes in a roadside serving area interface cabinet) which connects customers' telephone lines to the core network, to provide telephone, ISDN, and broadband such as DSL all from a single platform.
In this place, the following terms or expressions are used with the meaning indicated:
MSAN | Multi-service Access Node |
MSAG | Multi-service Access Gateway |
This place covers:
Self-explanatory. Essentially one DSL type is supported by the access multiplexer.
This place covers:
This group covers specific implementation designs of an access multiplexer, e.g. specific hardware resources or line cards arrangements.
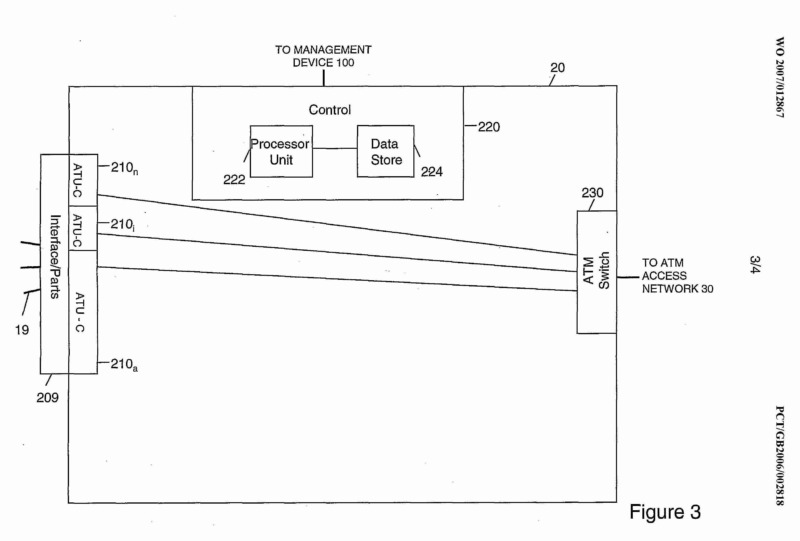
This place does not cover:
DSLAM modems |
This place covers:
All complex traffic processing (e.g. classification, filtering, QoS, etc.) is performed on a single central chip, e.g. on the uplink card.
This place covers:
Some or all complex traffic processing is off-loaded to the line cards, which may include dedicated processors.
Examples : US6587476, US2002159462, US2008101401.
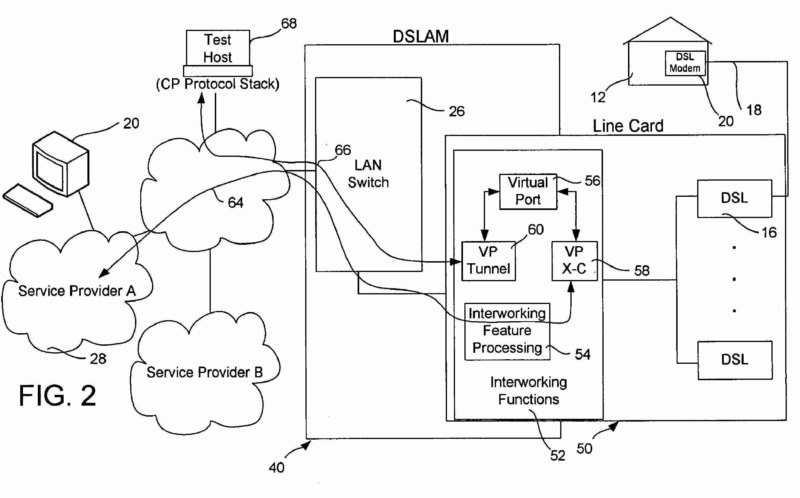
This place covers:
- Optical Network Units, Optical Line Terminals
- Set-top boxes
- Home network access point
- Cable modems in cable networks, e.g. DOCSIS
Entry concerning the design of devices carrying out generic L2 or L3 data processing operations, located at the interface between a private or home environment and the access network.
This place does not cover:
Broadband local area networks | |
Home network gateways, residential gateways | |
DSL modems and xDSL splitters |
This subclass shall only be allocated to documents giving operational details of subscriber equipments which interact with other access network devices, e.g. via the exchange of messages. The sole description of a stand-alone end-user device without any active connection to an access network shall not be classified in H04L 12/2898.
This place covers:
A bus network includes one or a plurality of shared communication lines interconnecting at least 3 distant stations, wherein data is transferred serially in the form of frames or bitstrings along the bus.
Attention is drawn to the following places, which may be of interest for search:
Transmission of data and power over a link, and not over a bus network as defined above | |
Serial data transmission over a shared medium having a ring or star topology | |
Fibre-channel aspects related to topology, i.e. ring, or switch architecture | |
Bus networks including at least one bridging device | |
Bus networks employed restrictively for a specific automotive application (e.g. power steering, brake-by-wire) | |
Bus systems being deployed on an airplane specifically for controlling parts of an aircraft | |
Bus to control actuators/sensors or any other industrial appliance in an automation system | |
Parallel bus systems | |
Daisy chain buses using an embedded synchronisation | |
Point-to-point communication between 2 stations over a bus | |
Wireless networks comprising several communication nodes using contention resolution mechanisms |
This place covers:
Details on the hardware elements comprised in a bus communication node. In particular, this class covers the inter-working of the various hardware components and implementation details of specific hardware components. A document shall get an EC code from this group only if the document deals with a particular inventive hardware or software realization. If the document includes the mere illustration of a hardware or software design for implementing a protocol, this document shall only get an Indexing Code in this group.
Example : A FlexRay communication node:
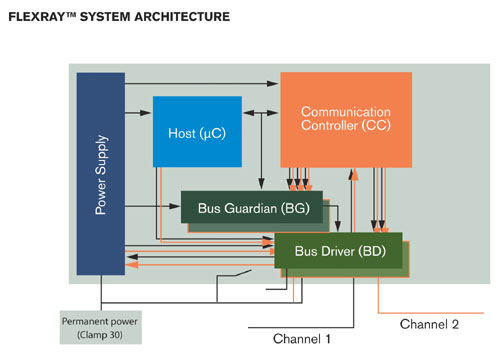
Attention is drawn to the following places, which may be of interest for search:
Current supply arrangements for the communication nodes | |
Intermediate storage or scheduling | |
Hardware architecture of a processing unit in general |
This place covers:
A bus controller refers to a microprocessor that is dedicated to input and output of data by a node on a bus. Structure of a carrier sense functionality is also classified here.
This place covers:
A bus master is a device controlling which node accesses the bus at particular time. See also H04L 12/403 for access control aspects
This place covers:
A bus guardian is a device monitoring the timing of node accesses on the bus, used for instance in FlexRay systems to avoid babbling idiots (faulty, continuously sending nodes).
This place does not cover:
Passive fault-masking in a computer environment |
This place covers:
Interface between the communication line and the other elements of the communication node, having some autonomous functionalities such as message pre-filtering, bus monitoring...
This place covers:
Power management aspects, such as management of the transition between various power states (sleep, active or stand-by). These documents shall also be classified in H04L 12/12
Attention is drawn to the following places, which may be of interest for search:
Arrangements for remote connection or disconnection of substations or of equipment thereof |
This place covers:
Refers to field devices for instance, which use the voltage and/or current level present on the bus to draw energy from the bus. Note that H04L 12/10 contains documents classified before 2008 having this functionality.
Attention is drawn to the following places, which may be of interest for search:
Current supply arrangements |
This place covers:
All documents dealing primarily with transmission on a Firewire bus.
This place does not cover:
Bus transfer protocol on a daisy chain bus using an embedded synchronization |
Attention is drawn to the following places, which may be of interest for search:
Synchronisation, e.g. post-wait, barriers, locks |
This place covers:
Documents referring generally to synchronization aspects of Firewire communication, incl. jitter compensation and clock synchronizations.
This place covers:
Aspects of resource allocation for Firewire networks.
This place does not cover:
Home automation networks |
Attention is drawn to the following places, which may be of interest for search:
Flow control aspects |
This place covers:
Self-explanatory, deals with operations on packets in a Firewire bus system.
Attention is drawn to the following places, which may be of interest for search:
Packet switches | |
Intermediate storage or scheduling |
This place covers:
Typically bus reset operations on Firewire.
This place does not cover:
Home automation networks |
Attention is drawn to the following places, which may be of interest for search:
Arrangements for maintenance or administration |
This place covers:
Control to the access to the communication medium on Firewire.
This place covers:
Interconnection aspects in Firewire bus systems.
Attention is drawn to the following places, which may be of interest for search:
LAN interconnection over a bridge based backbone | |
Single bridge functionality |
This place covers:
Gateway to other network sections, to other Firewire networks.
Attention is drawn to the following places, which may be of interest for search:
Bridging devices in local area networks |
This place covers:
Security aspects in Firewire networks.
This place does not cover:
Cryptographic protocols | |
Network security protocols |
This place covers:
Interconnection with multimedia devices over a FireWire bus.
Attention is drawn to the following places, which may be of interest for search:
Home automation networks |
This place covers:
Interconnection of computers with specific extension elements such as peripherals over a Firewire bus.
Attention is drawn to the following places, which may be of interest for search:
Printer information exchange with computer |
This place covers:
Documents referring generally to the selection of a particular data rate on a bus network, based on different factors, i.e. instantaneous network load. Rate adaptation on a bus maybe be necessary for achieving optimal transmission performance, by finding a good trade-off between packet loss and transmission speed. A LIN bus supports for instance various bitrates.
This place does not cover:
Systems modifying transmission characteristics according to link quality |
Attention is drawn to the following places, which may be of interest for search:
Allocation of payload | |
Negotiation of transmission parameters of transmission speed prior to communication |
This place covers:
Physical link properties include bus capacity such as 10Mbit/s or 100Mbit/s Ethernet network.
This place covers:
Documents related to the introduction of certain criteria to prioritize the transmission of data on the bus. On a vehicle bus for instance, information about car safety shall have priority over messages carrying monitoring data.
Attention is drawn to the following places, which may be of interest for search:
Hybrid switching fabrics | |
Intermediate storage or scheduling | |
Time-division multiplexing |
This place covers:
Queue management at the transmitting node.
This place covers:
In a TDMA bus communication system, certain time slots might be reserved for transmission of data having a high level of priority.
This place covers:
Typically a message field or tag indicates a priority level, which can be read by any node connected to the bus.
This place covers:
Documents covering various flexibility aspects, such as fast network re-configuration, flexible topology change, seamless connection or disconnection of a new node to/from the bus. In general, this class covers scalability of bus networks and reconfiguration aspect.
This place does not cover:
Arrangements for maintenance or administration involving management of faults; events, alarms | |
Automatic restoration of network faults |
This place covers:
Different forms of redundancy which do not correspond to the following related fields.
This place does not cover:
Error detection or correction of the data by redundancy in hardware using active fault | |
where persistent mass storage functionality or persistent mass storage control functionality is redundant |
This place covers:
A single bus system may comprise at least one back-up communication line, in case of failure of the main communication line. Each station has then typically two or more bus drivers, one for each communication line.
This place covers:
Two bus systems running independently of each other may provide protection against problems affecting the whole active bus system.
This place covers:
Duplication of a part or of an entire communication node in order to ensure fast recovery from a node defect without affecting the bus operations.
This place covers:
Switching from an active master station to a back-up master station is needed for safety-critical bus systems with centralized access control. See also H04L 12/403.
This place covers:
Contains documents with a central control node controlling the transmissions on the bus. Polling is known for a long time so a "new" polling scheme could be found in rather old documents (<1970).
This place covers:
Self-explanatory. Shall not be used for documents dealing with FlexRay in general.
This place does not cover:
Hybrid switching systems | |
Allocation of channels in TDM/TDMA networks |
This place covers:
This is a subgroup with general aspects of decentralized control. It contains documents about implicit token passing and some slotted buses.
This place covers:
Deals with access schemes in which access to the medium is granted at random after an arbitration process in case several nodes send requests simultaneously (collision). CSMA/CD (carrier sense multiple access with collision detection) also called Ethernet (basic document by Xerox US4063220) is one of these schemes. Ethernet aspects not linked with CSMA/CD shall not be classified in this class, but documents concerning some specific Ethernet functionalities such as contention resolution, back-off or interframe gap shall be classified in this group.
This place covers:
This is a special case for relatively low transmission speeds and/or short buses. Nodes competing for bus access read the superposed signals back from the bus and stop transmission when the bus signal is not identical with the transmitted signal. Many bus systems used e.g. in vehicles can be found in this subgroup.
This place does not cover:
Computer buses with bit-wise arbitration |
CAN bus aspects not linked with bit-wise arbitration shall not be classified in this class.
This place covers:
Contains documents with access schemes granting access to requests within a predetermined time limit. On token buses nodes are arranged in a logical ring passing the access right (token) from node to node. Bus networks having a master are not classified here. Aspects of FlexRay related to the deterministic access to static time slots are also classified here.
This place covers:
Deals with networks in which nodes are connected in a physical ring.
This place covers:
Deals with link by link synchronization between nodes and network
synchronization.
This place does not cover:
Synchronization in general | |
for ring networks |
Attention is drawn to the following places, which may be of interest for search:
Time division multiplex systems |
Double classification with H04J 3/00 is allowed.
This place covers:
Same as for bus networks but in a physical ring network.
Attention is drawn to the following places, which may be of interest for search:
Bus networks with centralized control |
This place covers:
Analog to bus networks, see H04L 12/417.
This place does not cover:
Bus networks with decentralized control |
This place covers:
Slotted rings; can be with fixed time slot allocation to the nodes or with access schemes for transmission access to a part of the bandwidth (slot).
This place covers:
Nodes having the access right (token) can transmit. When finished, the token is other nodes is buffered in a register until a node has finished its own transmission. This is the main group for FDDI and Fiber Channel rings when the access method is the issue.
This place covers:
Rings are vulnerable to faults. This subgroup contains documents dealing with recovery from faults like loop-backs or subrings when a ring systems is cut.
This place does not cover:
Fault recovery in general | |
Fault recovery systems for SDH/SONET(Protection Switching) ring networks |
This place covers:
Deals with networks in a physical star or tree configuration.
In case of Ethernet repeaters or hubs, transmission is broadcast and the bus access schemes are applied (e.g. Ethernet in 10baseT).
This place covers:
- Interconnection of network segments of different types. e.g. between Fire Wire and Ethernet segments;
- Internetworking in CEBUS, MAP/TOP, CAN and other application oriented topologies;
- Repeaters (LAN segmentation).
This group contains general documents on internetworking in packet-switched networks.
This place does not cover:
Coupling between buses internal to a computer |
This place covers:
- Header group for network backbone functionality
- SONET, SMDS, DQDB
- XNS, SNA, CATV
- Internet
Attention is drawn to the following places, which may be of interest for search:
Implementation or adaptation of Internet protocol [IP], of transmission control protocol [TCP] or of user datagram protocol [UDP] |
This place covers:
- LAN emulation
- IP or other proprietary protocols (e.g. IPX, SNA, netBIOS, Appletalk...) over ATM. MPOA.
- VP switching for multiplexing connections in VLAN/BVPN Connectionless support in ATM for LAN interconnection (type D service. I.364 rec., ATM Forum's scheme).
- Some documents about remote address resolution (ARP,NHRP).
This place covers:
- Internetworking over the PSTB
- Narrowband ISDN both using BA or PR access, Channel B or D
- X.25 based internetworks
This place covers:
Contains mainly documents about LAN interconnection using a FDDI backbone. Do not forget that some SNA implementations use a Token Ring backbone, so if you do not find your document here have a look to the H04L 12/4604 just in case.
This place covers:
Topology aspects: where the bridges are placed. Bridging different type 802.X LAN's. General documents on Source Routing, Spanning Tree or DLS (no much detail on how the actual routing is carried out.
This place does not cover:
Routing of packets |
Attention is drawn to the following places, which may be of interest for search:
Routing tree calculation | |
Layer 2 routing, e.g. Ethernet-based MAN's |
Spanning tree protocol shall be classified in this group, but also possibly H04L 45/00 and subgroups when applied on a generic routing protocol that can be applied on Layer 2 as well as Layer 3 networks.
This place covers:
Bridge functionalities.
It covers:
- Multistandard for heterogeneous 802.X LAN environment
- Address learning and filtering with the suitable table lookup or CAM techniques. Address caching.
- Internal buffer and memory management.
- Bridges doing repeater functions or routing (Brouters)
This place does not cover:
Router functionalities or routing protocols |
Attention is drawn to the following places, which may be of interest for search:
Fast packet switching |
It is difficult to determine whether to begin the search in H04L 12/462 or in H04L 12/4625. As a rule of thumb you could say that bridge/router functionality that does not require cooperation among bridges/routers, should be classified in H04L 12/4625. Therefore, network aspects that involve exchange among bridges/routers are meant to be in H04L 12/462.
This place covers:
Encapsulation is the embedding of a protocol in another protocol at the same or different OSI layer. This technique is often used in a backbone to be able to deal with a plurality of end user protocols using a common transport entity.
Tunneling is a very important part of this group (e.g. L2TP).
This place does not cover:
Pseudo-wire emulation, e.g. IETF WG PWE3 |
Attention is drawn to the following places, which may be of interest for search:
Point-to-point connection between the data network and the subscriber in access networks (e.g. PPPoX protocols) | |
Virtual LANs | |
VPN tunnels for security | |
Protocol conversion |
This place covers:
- Complex meshes of rings; Topological aspects
- MAN, WAN ring based architectures
- Hierarchical ring topologies
- Streets of Manhattan, interlaced rings and similar architectures
Attention is drawn to the following places, which may be of interest for search:
FDDI WANs |
This place covers:
Virtual local area network, virtual LAN or VLAN. A group of hosts with a common set of requirements that communicate as if they were attached to the same broadcast domain, regardless of their physical location. Networks with the same attributes as a physical local area network (LAN), but that allow for end stations to be grouped together even if they are not located on the same network switch.
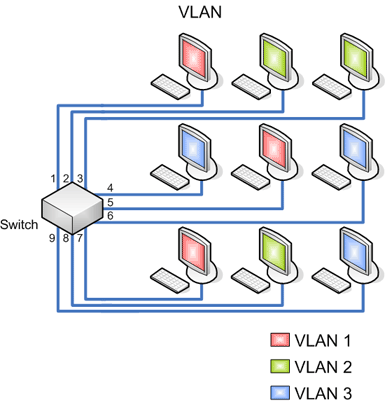
This place does not cover:
LAN interconnection over a bridge based backbone | |
Encapsulation techniques | |
Routing of packets | |
Packet switches | |
Virtual private networks for security |
This place covers:
Details on tagging of a frame with VLAN information, involving mainly the use of a dedicated field for tagging a frame. When a packet enters a VLAN, a switch adds a VLAN field to the packet including a VLAN ID, the tag. Covers converting untagged frames to tagged frames. A typical VLAN tagged frame:
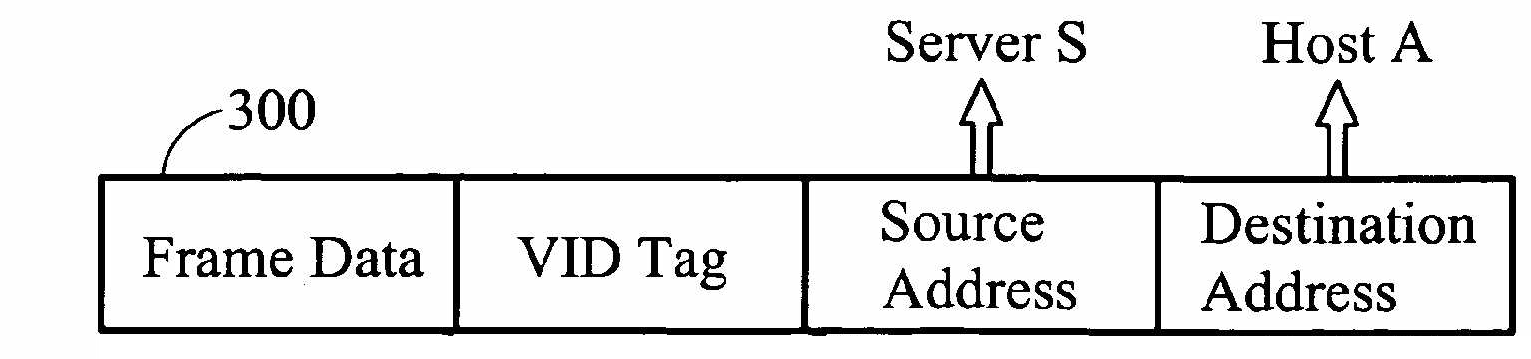
This place does not cover:
Routing of packets | |
Routing of packets using label swapping, e.g. MPLS | |
Switching devices with support for virtual LAN |
Multi-tagging of frames shall not be classified in H04L 12/4645, only in H04L 12/465 or the subgroups of it.
This place covers:
Description and creation of single frames including a plurality of VLAN tags.
Frequently refers to QinQ (see IEEE standard 802.1ad) and the derivatives of this protocol. Covers tagging an already tagged packet, thereby producing a "multiple-tagged" frame, or a VLAN stack. A typical QinQ frame:
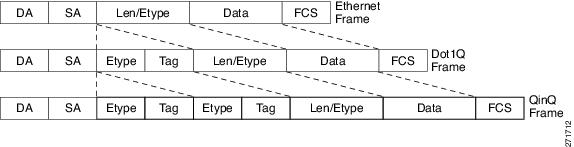
This place does not cover:
Encapsulation of packets |
A document shall only be allocated this class if no relevant subgroup of this class can be found. On the other hand, different classes from this group (i.e. H04L 12/4654, H04L 12/4658, H04L 12/4662) might be assigned to a single document.
This place covers:
In multi-tagged frames, a VLAN tag representing a customer VLAN is a VLAN tag uniquely associated to a particular end user, subscriber or
local network entity (computer, user station).
This place covers:
Covers the outer tagging of Ethernet packets in PBB (Provider Backbone Bridge) networks, see IEEE Standard 802.1ah. A service provider backbone VLAN spans over a carrier network, not over a single LAN
Attention is drawn to the following places, which may be of interest for search:
Encapsulation techniques |
This place covers:
Covers documents associating a VPN with a PBB and assigning an I-SID. FIG. 3 below (US2008170573) is a simplified representation of a frame format 150 for VPN data packets transmitted through a PBB tunnel. The frame format 150 includes a PBB header 152 comprised of a backbone destination address (B-DA) 154, a backbone source address (B-SA) 156, a backbone VLAN ID (B-VID) 158, and a backbone I-component service ID (I-SID) 160.
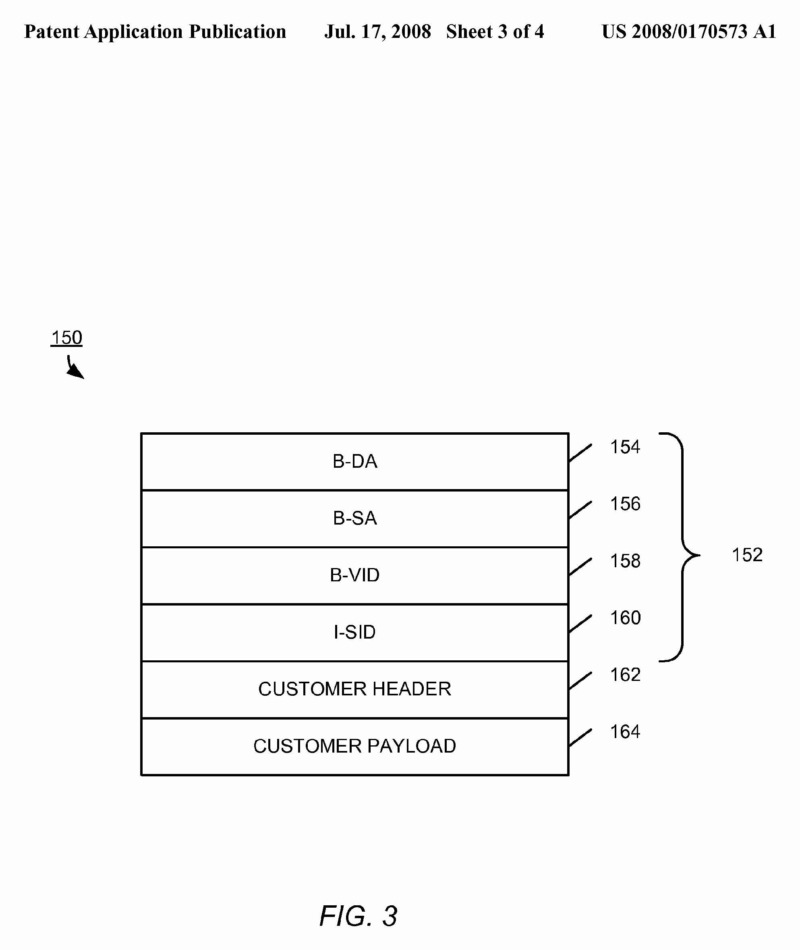
In this place, the following terms or expressions are used with the meaning indicated:
PBB | Provider Backbone Bridge |
This place covers:
Covers operations carried out on a packet header, such as adding and/or removing tags, usually according to a particular algorithm or specific structure. An emphasis is put on the operational details of adding or stripping VIDs, at a particular node, e.g. US2010226368:
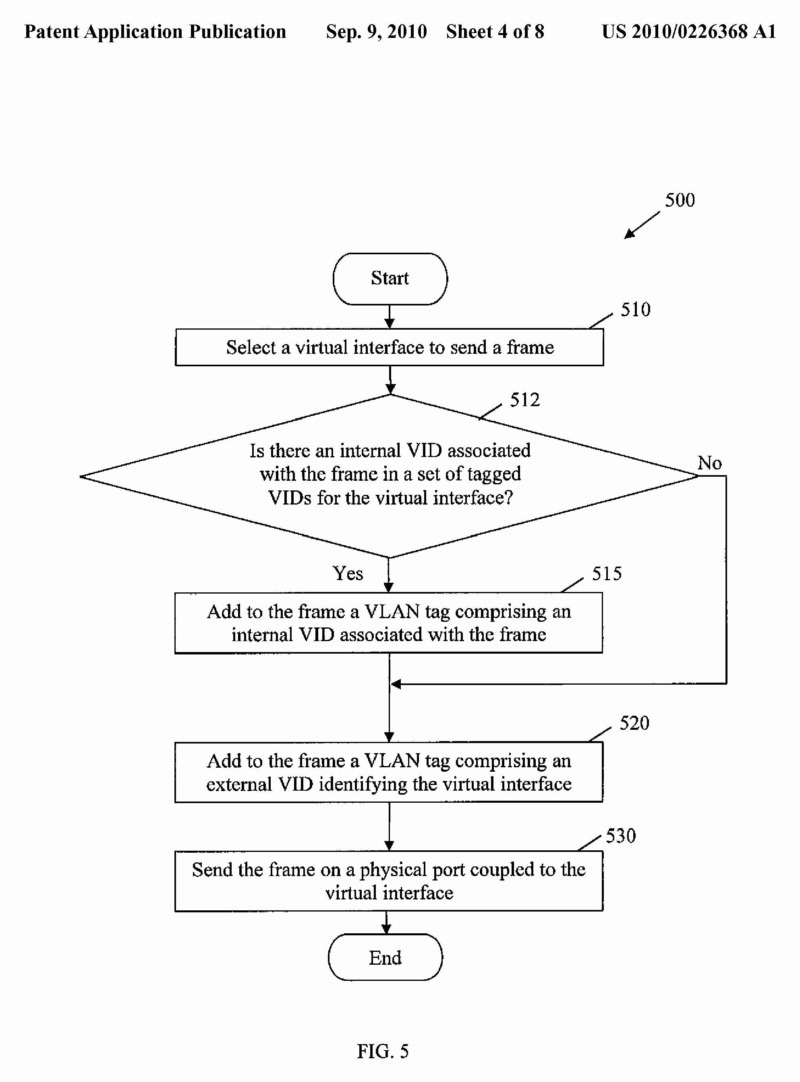
The mere tagging of packets or removal of tags without particular operational details shall only be classified in H04L 12/4645 or in the subgroups of H04L 12/465
This place covers:
The port is assigned to a specific VLAN independent of the user or system attached to the port. All users attached to the port should be members in the same VLAN. Usually the port configuration is static. A port based VLAN switch determines the membership of a data frame by examining the configuration of the port that received the transmission.
Classes from the H04L 12/4645 subgroups and the class H04L 12/467 might be allocated to a single document only if two VLAN operational modes (i.e. tag-based VLANs and port-based VLANs) are presented in the document as part of the invention
This place covers:
Sharing of information between networks elements: information about the identifier, about the member status, about the port based VLAN distribution. Sometimes this layer 2 information is intended to be displayed or monitored. Even though failure recovery is not covered in this class, Layer-2 information might be dynamically shared between the elements on the network after detection of a network failure.
This place does not cover:
Failure recovery | |
Configuration of the network, or of network elements |
This place covers:
Registration or de-registration of VLAN memberships. Also includes removing, discovering and identifying VLAN members. Covers also the exchange of messages for modifying an entry in a mapping table for switches supporting port-based VLANs.
This place does not cover:
Configuration of switching devices |
This place covers:
Details on a specific standardized or proprietary protocol for maintaining a VLAN, for registering, de-registering VLAN members
This place does not cover:
Group membership management |
Only for defining particular routines, packets types or format when maintaining VLANs. Can include extensions or modifications of an existing protocol
This place covers:
A commonly-used VLAN registration protocol generic framework defined by the IEEE 802.1ak revision to the IEEE 802.1Q standard.
This place covers:
This is a standards-based Layer 2 network protocol, for automatic configuration of VLAN information on switches. It was defined in the 802.1ak amendment to 802.1Q-2005.
In this place, the following terms or expressions are used with the meaning indicated:
GARP | Generic Attribute Registration Protocol |
In patent documents, the following abbreviations are often used:
MVRP | Multiple VLAN Registration Protocol |
This place covers:
VTP is a proprietary protocol that propagates the definitions of Virtual Local Area Networks (VLAN) on a whole local area network.
This place covers:
Systems in which information is sent to an intermediate station where it is kept and sent at a later time to the final destination or to another intermediate station.
This place does not cover:
Routing or path finding of packets in data switching networks | |
Traffic control in data switching networks |
This place covers:
Basic functionality of packet switching networks. Namely: routing, flow control, admission control, switching architectures and other general issues on packetized data handling.
This place does not cover:
Interprocessor communication | |
Packet based communication in satellite networks | |
Networks specially adapted for the exchange of pictorial information |
Examples of places where the subject matter of this place is covered when specially adapted, used for a particular purpose, or incorporated in a larger system:
Arrangements for packet switching specially adapted for wireless networks |
Attention is drawn to the following places, which may be of interest for search:
In patent documents, the following abbreviations are often used:
ATM | Asynchronous Transfer Mode |
TCP/IP | Transmission Control Protocol/Internet Protocol |
This place covers:
Asynchronous Transfer Mode(ATM) technical aspects.
This place does not cover:
Routing in wireless networks |
This place does not cover:
Apparatus or local circuits for transmitting or receiving dot-and-dash codes | |
Apparatus or local circuits for transmitting or receiving codes wherein each character is represented by the same number of equal-length code elements |
Attention is drawn to the following places, which may be of interest for search:
Couplings for transmitting rotation; clutches | |
Spread spectrum techniques using chirp |
Attention is drawn to the following places, which may be of interest for search:
Electronic switching or gating |
This place does not cover:
Educational or demonstration appliances; appliances for teaching or communicating with, the blind, deaf or mute; models; planetaria; globes; maps; diagrams | |
Switches with abutting contact carried by operating part |
Attention is drawn to the following places, which may be of interest for search:
Having a plurality of operating members associated with different sets of contacts | |
Characterised by the way in which the control signal is generated | |
Coding in connection with keyboards or like devices |
Attention is drawn to the following places, which may be of interest for search:
Having a plurality of operating members associated with different sets of contacts | |
Characterised by the way in which the control signal is generated | |
Coding in connection with keyboards or like devices |
This place does not cover:
Apparatus or local circuits for transmitting or receiving dot-and-dash codes |
This place covers:
Code Shift Keying and CCK (Complementary Code Keying).
The generation of sequences, like orthogonal CAZAC, Zadoff-Chu or Generalized Chirp sequences that are used for signalling purposes.
Attention is drawn to the following places, which may be of interest for search:
Codes types for Code Division Multiplex systems (CDMA) | |
Generation of orthogonal codes for CDMA |
This place covers:
Baseband aspects of digital data transmission.
Arrangements for supplying electrical power along data transmission lines.
Channel estimation techniques.
Arrangements for detecting the data rate of an incoming signal.
Arrangements for coupling to transmission lines.
Line equalizers (digital).
Shaping networks in transmitter or receiver.
Digital equalizers: structure and adaptation algorithms.
Arrangements involving sequence estimation techniques.
Electric or magnetic storage of signals before transmitting or retransmitting for changing the transmission rate.
Decision circuits providing symbol by symbol detection; DC level restoring means; Bias distortion correction.
Modifications for reducing interference in line transmission.
Digital repeater/relay circuits.
Line codes.
Pulse width modulation; pulse position modulation.
This place does not cover:
Error correction coding | |
Arrangements for synchronising receiver with transmitter | |
Joint detection techniques in CDMA | H04B1/70105 |
Interference related aspects of DSSS | |
Systems for transmitting signals via power distribution lines | |
Details on optical domain processing |
Attention is drawn to the following places, which may be of interest for search:
Bus networks | |
Digital adaptive filters | |
Matched filters | |
Kalman filters | |
Circuits in general for handling pulses | |
Coupling arrangements in general | |
Conversion to or from representation by pulses | |
Coding in general | |
Details in line transmission systems in general | |
Echo cancellation | |
Reducing cross-talking | |
MIMO diversity systems | |
Feedback content | |
Wireless repeaters in general | |
Modelling the propagation channel | |
Interference aspects in orthogonal multiplex systems (i.e. using Walsh codes) |
The groups under H04L 2025/0335 classify the type of signal the equalizer is intended for.
The groups under H04L 2025/03433 provide further details on the equalizer structure implementation.
The groups under H04L 2025/03592 deal with details of the adaptation algorithms for equalisation.
The groups under H04L 2025/03777 provide details on signalling.
In this place, the following terms or expressions are used with the meaning indicated:
DFE | Decision Feedback Equaliser |
SVD | Singular Value Decomposition |
FIR | Finite Impulse Response |
FDE | Frequency Domain Equalizer |
GPRS | General Packet Radio Service |
ICI | Inter-Carrier Interference |
ISI | Inter-Symbol Interference |
LLR | Log-Likelihood Ratio |
LMMSE | Linear Minimum Mean Squared Error |
LMS | Least Mean Square |
LS | Least Squares |
MAP | Maximum A-posteriori Probability |
MLD | Maximum Likelihood Detector |
MMSE | Minimum Mean Squared Error |
RLS | Recursive Least Square |
In patent documents "pilot signals" can be called sometimes "Reference signals", "Sounding signals" or "Training signals".
This place does not cover:
Systems for transmitting signals via power distribution lines |
This place covers:
The structure of the sounding signals or the pilot pattern. For details of the allocation of the sounding signals: H04L 5/0048.
This place covers:
This group answer the question of how the sounding signals are used to derive an estimation. For example, by averaging.
This place covers:
Use of data (in addition to the sounding signals) for channel estimation
This place covers:
Iterative channel estimation for the same symbol, for example the EM (maximum expectation).
This place covers:
Singular value decomposition, SVD.
This place covers:
All iterative algorithm (not for the same symbol), for example: RLS.
This place does not cover:
Line drivers (duplexing arrangements |
This group should not be used. Subject-matter is classified under H04L 25/0264.
This place covers:
This involves frequency estimation or detection, but not synchronisation.
This place covers:
The arrangements are at either end.
This place covers:
How to couple the driver to the transmission line or how to configure the driver.
This place covers:
Implies some knowledge of the actual line, although it might be rather vague, such as "this is 100 m long". Thus, the coupling provides the pre-emphasis, otherwise, if it is not in the coupling, H04L 25/03885 is the proper place to classify.
This place does not cover:
the shape being matched to the transmission line (pre-equalisation per se |
This place covers:
Shaping networks in transmitter or receiver, e.g. adaptive shaping networks, receivers or arrangements for processing base band signals.
Attention is drawn to the following places, which may be of interest for search:
Impedance networks, e.g. resonant circuits; resonators |
This place covers:
The subgroups under H04L 25/03006 cover digital equalisation and detection techniques. Digital equalisers not only try to make the channel flat and remove ISI, but they also implement detection and decision.
This place covers:
For example, DFE equalisers.
This place covers:
MLSE techniques, and in general the estimation of a sequence of symbols (not just one symbol).
In the case of multiuser environment, it covers the estimation of the different users.
This place covers:
The cases where desired user is estimated and the other users are seen as interferences, such that their estimation is removed (for example, by subtraction).
This place does not cover:
Joint sequence estimation and interference removal (joint detection of several desired signals |
This place covers:
Pre-equalisation.
Pre-coding for MIMO channels can be seen as a pre-equaliser or as a beam-former.
The selection of codebook or precoding matrix for MIMO diversity systems is classified under H04B 7/0456, while the design of the codebook matrices is classified under H04L 25/03898.
This place covers:
Not limited to radio systems but also covers the case of cross-talk between cables as a MIMO system.
This place covers:
For example: FFF (feed forward filter).
This place covers:
The cases of the feedback of codebook index to be able to choose a precoding matrix at the transmitter.
Attention is drawn to the following places, which may be of interest for search:
Detection of unique words or other known elements |
This place covers:
When the soft decisions are part of a sequence estimation, then the place to classify is H04L 25/03318, otherwise, when the soft decisions are symbol by symbol is classified in H04L 25/067.
This place does not cover:
Sequence estimation techniques | |
By sampling faster than the nominal bit rate | |
By detecting edges or zero crossings |
Attention is drawn to the following places, which may be of interest for search:
Balancing during the coupling of signals |
Attention is drawn to the following places, which may be of interest for search:
Impedance matching in coupling arrangements |
This place covers:
The parallel transmission of a single bit stream and the reassembling (skew compensation) of all the content of the parallel channels at the receiver in order to retrieve the single bit stream.
This place covers:
Wired digital repeaters. For wireless repeaters see classes under H04B 7/15.
Attention is drawn to the following places, which may be of interest for search:
Repeaters for converting two wires to four wires |
This place does not cover:
Repeater circuits, relay circuits |
Attention is drawn to the following places, which may be of interest for search:
Arrangements for synchronising receiver with transmitter | |
Using the transitions of the received signal to control the phase of the synchronising-signal-generating means | |
Transmitting and receiving encryption devices synchronised or initially set up in a particular manner |
Attention is drawn to the following places, which may be of interest for search:
Electronic distributors in general |
This place does not cover:
Spectral shaping |
Attention is drawn to the following places, which may be of interest for search:
Preprocessing of received signal for synchronisation, e.g. by code conversion | |
Coding, decoding or code conversion, in general |
This place covers:
For example: Manchester code; Biphase space or mark code (e.g. double frequency code).
This place covers:
For example: PAM with more than 2 levels.
This place covers:
PCM modems V.90.
This place covers:
For example: Tolimson-Harashima precoding, Trellis precoding, GPRS.
This place does not cover:
Transmitters and receivers for partial response systems equalizers at the transmitter end |
Attention is drawn to the following places, which may be of interest for search:
Response systems (transversal equalizers | |
Partial response continuous phase modulation systems |
This place covers:
Modulated-carrier systems.
Passband aspects of data transmission, e.g. modulating and demodulating, arrangements for provision and recovery of carriers.
The most fundamental digital modulation techniques: ASK, FSK, PSK and QAM.
Multicarrier modulation systems.
The modulated carrier systems covered in this groups are independent on the type of physical signal, i.e. the signal can be audio, RF, optical,..., but the signals must be digital.
When the multiple access scheme relies on the use of multicarrier signals,
and if what is important is how the signal is modulated/demodulated, or "hardware" aspects in the transmitter or the receiver to produce or recover (like synchronisation) such signal or aspects related to the peak power reduction, then the classes under H04L 27/2601 are relevant. Otherwise, to indicate that the signal involved is, for example, an OFDM signal, then the class under H04L 5/0007 is used instead.
Attention is drawn to the following places, which may be of interest for search:
Block-coded modulation | |
Trellis-coded modulation | |
Arrangements affording multiple use of the transmission path | |
Modulated-carrier systems (code shift keying in combination with frequency multiplexing | |
Simultaneous bidirectional transmission of AC signals | |
Code Shift Keying; CCK (complementary code keying) | |
Pulse width modulation; Pulse position modulation | |
Pulse amplitude modulation | |
CORDIC | |
Modulator circuits in general (analogue modulators) | |
Demodulator circuits in general (analogue demodulators) | |
Modifications in amplifiers to reduce non-linear distortions, by pre-distortion | |
Pulse Amplitude modulation, i.e. PAM | |
Delta modulation | |
Details on optical domain processing | |
Polarisation shift keying | |
Transmission of data during the active part of a television frame |
In this place, the following terms or expressions are used with the meaning indicated:
ASK | Amplitude Shift Keying |
CPM | Continuous Phase Modulation |
FSK | Frequency Shift Keying |
OOK | On-Off Keying |
PSK | Phase Shift Keying |
DPSK | Differential Phase Shift Keying |
QAM | Quadrature Amplitude Modulation |
In patent documents the following expression "multiresolution systems" is often used as synonym of non-uniform or asymmetric or layered modulation or hierarchical modulation or superposed modulation.
This place does not cover:
Baseband equalizers at the transmitter | |
In analogue transmission systems |
Attention is drawn to the following places, which may be of interest for search:
Control of amplification |
Attention is drawn to the following places, which may be of interest for search:
Demodulation of amplitude-modulated pulses |
This place does not cover:
Carrier systems in general comprising amplitude-modulated carrier systems, and phase-modulated carrier systems |
Attention is drawn to the following places, which may be of interest for search:
The signals being represented by different frequencies | |
The synchronisation signals differing from the information signals in amplitude, polarity, or frequency | |
Frequency multiplication | |
Continuous phase systems |
This place does not cover:
Spread spectrum techniques |
Attention is drawn to the following places, which may be of interest for search:
Spread spectrum techniques using chirp |
Attention is drawn to the following places, which may be of interest for search:
Continuous phase modulation | |
Frequency or rate pulse modulation |
Attention is drawn to the following places, which may be of interest for search:
For continuous phase modulation systems | |
Demodulation of frequency- or rate-modulated pulses |
Attention is drawn to the following places, which may be of interest for search:
Position modulation |
Attention is drawn to the following places, which may be of interest for search:
Demodulation of position-modulated pulses |
This place covers:
All techniques related to the multiple carriers processing of electrical signals (at the transmitter and receiver), to the structure of such signals (pilot signals, guard interval), and problems related to the frequency domain processing of such signals (Peak to Average Power Ratio PAPR).
Example of systems covered: OFDM, OFDMA, SC-FDMA, IFDMA, LTE, DVB, DSL, Optical OFDM ...
Practically the coverage of this subgroup in term of features is:
- within a transmitter, it starts at the serial to parallel transformation of the data and ends after the IFFT (or any other frequency domain to time domain converter) or post-PAPR processing, and includes the PAPR processing, the pilot insertion, and if present the DFT precoding of the data (for SC-FDMA systems).
- within a receiver, it starts at the FFT (or any other time domain to frequency domain converter) and includes the synchronisation arrangements (time, frequency).
This place does not cover:
Resource allocation techniques | |
Bit loading of the subcarriers for OFDM(A) systems | |
Pilot allocation for OFDM(A) systems | |
Techniques like MC-CDMA involving code and frequency multiplexing | |
Carrier systems |
Attention is drawn to the following places, which may be of interest for search:
Channel estimation techniques | |
Interference cancellation techniques (Inter Carrier Interference, multiusers) | |
Pulse shaping | |
Details of Fourier transforms | |
Optical transmitters | |
Higher Layer (network, routing) techniques |
Although mentioned as modulation, it can of course be interpreted as multiplexing depending on the way the processing is interpreted. In a way it is a modulation since the main carrier signal is mixed with a modulating signal being the output of the IFFT after cyclic prefix addition. However it is also multiplexing since data being either from one user or from multiple users are orthogonally mapped to the subcarriers.
This group is generally given to aspects not covered by any of the following lower subgroups, or to documents where OFDM is a secondary technical aspect.
The two main aspects under this group are the cyclic prefix classified under H04L 27/2605 and the pilot structure under H04L 27/261.
Basically documents classified here have their main feature in the mapping of particular data to the subcarriers or properties of the resultant OFDM time domain signal after IFFT, rather than particular means for processing the signal.
This place covers:
Different constellations (modulations) used on the subcarrier. For the allocation aspect (i.e. waterfilling for instance), see H04L 5/0044.
This place does not cover:
Multiresolution modulation methods |
Attention is drawn to the following places, which may be of interest for search:
Details of impulse response | |
Symbol synchronization (locating the FFT window within a useful data portion + guard period) | |
Delay profiles |
Most of the OFDM systems (except OQAM OFDM) use a cyclic extension added in time domain after each symbol in order to capture all multipath components that would result otherwise in Inter Symbol Interference (H04L 25/03006). Documents classified here either use a particular extension (adaptive or with a specific pattern) or provide for a specific processing of this extension.
In patent documents, the following words/expressions are often used as synonyms:
- "Symbol Extension", "Cyclic Prefix/Postfix/Suffix/Extension" and "Guard Period/Interval"
The Guard Period is a repetition of a portion of the useful data segment of the symbol transmitted.
This place covers:
Properties of the reference sequences used as preamble or pilot sequence.
Attention is drawn to the following places, which may be of interest for search:
Sounding signals for channel estimation | |
Linked to code properties | |
CAZAC sequences |
The Inverse Fourier transform at the transmitter transforms modulated symbols on each subcarrier, modulated by usual constellation patterns (QPSK, QAM), to time domain symbols presenting high peak to average power ratio. This problem is a recurrent problem in OFDM systems.
This high PAPR creates linearity problems at the following power amplifiers and must be remedied for in the time domain (i.e. after the IFFT, for instance by clipping) or in the frequency domain (i.e. before the IFFT) using iteration and feedback loop (using empty subcarrier, constellation extension ...).
When none of the following subclasses matches the technique used in the document, this class H04L 27/2614 has to be given.
In patent documents, the following words/expressions are often used as synonyms:
- "peak to average power ratio", "PAPR " and "Crest factor"
Through coding the series of bits before the modulation and the serial to parallel transformation, the situation where all modulated symbols on each subcarrier have the same phase thus generating the highest power is avoided. (See Jones and Wilkinson: "Block coding scheme for reduction of peak-to-average envelope power ratio of multicarrier transmission systems", 1994).
This place covers:
For instance: Tone Injection or Tone Reservation. A subset of subcarriers is used for generating a PAPR reduction signal c added to the remaining signal transmitted.
This place covers:
One of the most active subfields of PAPR reduction: Encompasses techniques like Selective Mapping (SLM) or Partial Transmission Sequence (PTS). Considering N subcarriers, SLM performs M multiple parallel N point IFFTs, each using a different N-phase vector (one phase value applied to each subcarrier) and selects out of the M outputs the resulting time domain OFDM with the lowest PAPR value. PTS divides the N subcarriers in V disjoint subcarriers subsets, multiplies each by a phase value and performs V partial IFFT before adding the resulting V outputs producing the OFDM symbol to be sent.
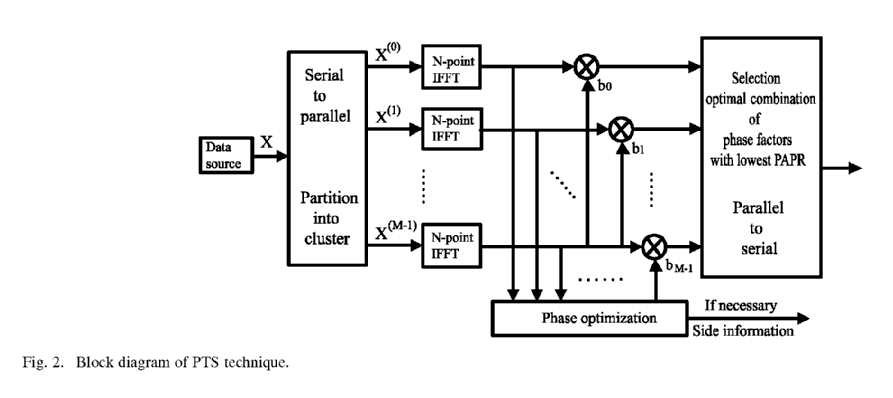
From Tao Jiang & al. "An Overview: Peak-to-Average Power Ratio Reduction Techniques for OFDM Signals"
This place covers:
Large field: Can happen in time domain (usual understanding where the parts outside the allowed power region are filtered or clipped out) but also in frequency domain (modulated symbols on each subcarrier are moved, see Active Constellation Extension). Can consist in decreasing higher power samples (by filtering or clipping) or enhancing low power samples (see nonlinear companding transforms using for instance μ-law companding from speech processing). Modify the dynamics of the signal.
Attention is drawn to the following places, which may be of interest for search:
Clipping in the frequency domain of the modulated symbols |
This place covers:
Based on Quantization aspects (linked to digital to analog conversion as well), see for instance the nonlinear companding method.
This place covers:
As depicted below, the features covered under this class extend from the serial to parallel conversion to the Guard Interval insertion and/or PAPR reduction block.

This place covers:
This part concerns the frequency domain to time domain conversion using either the classical Fourier transform, the filter bank approach or direct modulation of individual subcarriers.
This place does not cover:
Inverse Fourier transform modulators or inverse discrete Fourier transform modulators |
This place covers:
Filter bank applications.
In patent documents, the following abbreviations are often used:
FMT | Filtered Multitone |
This place covers:
Less subcarriers processed than the actual number of subcarriers to be transmitted.
Attention is drawn to the following places, which may be of interest for search:
Modulation circuits in general (Amplitude modulation) | |
Frequency modulation | |
Phase modulation | |
Combined modulation, like QAM | |
DFT and FFT computation methods and devices in general |
This place covers:
A DFT precoding of the symbols to be transmitted is performed prior to the IDFT. This gives good PAPR properties to the resulting signal.
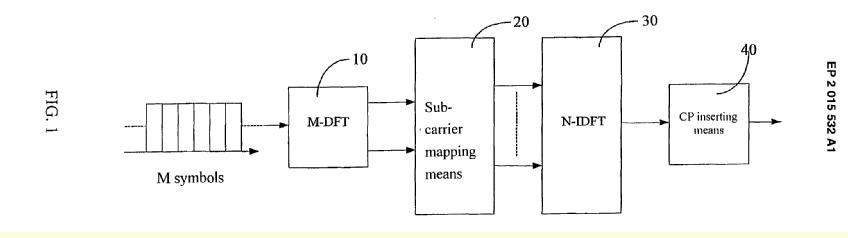
Conventional SC-FDMA Transmitter
This place covers:
The frequency domain to time domain conversion is not performed using any inverse Fourier transform.
Attention is drawn to the following places, which may be of interest for search:
Details on Discrete Cosine Transform |
This place covers:
Loss of orthogonality between the carriers due to the use of synthesis and analysis filter banks instead of the rectangular pulse of OFDM. Advantages: More freedom for the choice of pulses which can be more confined in time and frequency. No guard interval needed. Often combined with the use of higher density of basis functions (twice if only orthogonality in real domain should be ensured) like OQAM scheme.
Attention is drawn to the following places, which may be of interest for search:
Sounding signals for channel estimation |
This place covers:
Discrete Wavelet Multitone, Wavelet based multicarrier ...
This place does not cover:
Using Wavelet for dividing the transmission path |
Attention is drawn to the following places, which may be of interest for search:
Wavelet transforms per se |
This place covers:
For the uplink of some standards.
This place covers:
More than one sample per subcarrier. Oversampling OFDM.
Attention is drawn to the following places, which may be of interest for search:
Filtered Multitone |
Attention is drawn to the following places, which may be of interest for search:
Timing Advance |
This place does not cover:
Equalisation |
Attention is drawn to the following places, which may be of interest for search:
Arrangements for removing intersymbol interference |
This place covers:
The synchronisation of multicarrier signals received implies a three-step synchronisation: a symbol synchronisation, a frequency synchronisation and a frame synchronisation.
Reference Article: "Robust Frequency and Timing Synchronization for OFDM"; Timothy M. Schmidl and Donald C. Cox, Fellow, 1997, IEEE
Also linked to Primary Synchronisation Signal (PSCH) and Secondary Synchronisation Signal (SSCH) in LTE.
Attention is drawn to the following places, which may be of interest for search:
Synchronisation at the physical level not specific to multicarrier systems | |
Carrier Synchronisation not specific to multicarrier systems | |
Determination of the cell ID (cell search) | |
Synchronisation protocols at higher layers |
This place covers:
Frame synchronisation is generally achieved by time domain correlation using a repetition preamble. Technique is similar as that for achieving symbol synchronisation.
Attention is drawn to the following places, which may be of interest for search:
Preamble design | |
Symbol synchronisation |
This place covers:
Carrier Synchronisation in OFDM systems often consists in a first round for identifying an offset corresponding to an integer number of subcarrier spacings (coarse synchronisation), and a second round identifying the fractional subcarrier spacing offset (i.e. less than a subcarrier spacing).
In H04L 27/2657, only the cases not decomposing the synchronisation in these coarse and fine steps should be classified. Otherwise the subgroups H04L 27/2659 and H04L 27/266 should be used.
In patent documents the following expressions "frequency offset", "frequency shift", "frequency drift", "frequency error", "frequency correction", "carrier recovery" are often used in relation with this subgroup.
This place covers:
An integer subcarrier spacing frequency offset causes at the receiver a shift of the subcarriers in the frequency domain.
Coarse frequency offset determination is often performed in the frequency domain: It consists in identifying the amount of subcarrier shifts by correlating the received signal after FFT with a reference signal.
This place covers:
A fractional subcarrier spacing offset causes at the receiver an attenuation of each subcarrier symbol in the frequency domain.
Usually this fractional offset is identified by autocorrelating the received preamble in the time domain.
This place covers:
The same distinction between coarse and fine synchronisation as for the frequency synchronisation applies.
The symbol boundaries replace the carrier spacing: While the coarse symbol synchronisation will align the received symbol stream with a reference time, the fine symbol synchronisation mainly consists of synchronisation within the symbol boundaries (i.e. including the Guard Interval) and the best positioning of the FFT window within these boundaries.
As for frequency synchronisation, this class H04L 27/2662 should only be allocated to cases not decomposing the synchronisation in these coarse and fine steps. Otherwise the subgroups H04L 27/2663 and H04L 27/2665 should be used.
This place covers:
Generally coarse symbol synchronisation is achieved by autocorrelation in the time domain of the preamble sequence.
This place covers:
A FFT window of length corresponding to the useful symbol part must be positioned within the wider part including the Guard Interval. The ideal FFT location minimizes Inter Symbol Interference (ISI) and ensures the highest desired signal energy captured.
This place covers:
In some systems using OFDM, transmission parameters like the Guard Interval length, the carrier spacing and/or bandwidth are variable or unknown to the receiver and thus have to be determined at the receiver (without any control channel). This class covers the different algorithms and methods to determine these parameters at the receiver.
This place does not cover:
Allocation of subcarriers |
This place covers:
This class has been foreseen as a complementary class to the synchronisation classes above. It aims at further describing the synchronisation algorithm performed. Multiple classes may be allocated to describe the algorithm as precisely as possible.
This place covers:
This first subclass concerns the domain (time or frequency) in which the algorithm takes place. For mixed domain (files where parts of the algorithm takes place in time domain and other parts in frequency domain), this class H04L 27/2669 should be allocated.
This place covers:
The main algorithm of the invention has its essential steps performed in time domain.
This place covers:
The main algorithm of the invention has its essential steps performed in frequency domain.
This place covers:
This subclass should be allocated to describe which part of the received signal is used for achieving synchronisation: This can be known symbols (a preamble or pilot symbols), or it can be blind by using only unknown symbols (the decision of these symbols or their cyclic extension, or the presence of a repetition pattern).
Attention is drawn to the following places, which may be of interest for search:
Allocation of pilot signals | |
Structure of pilot symbols | |
Cell search in orthogonal multiplex systems |
Classification here should take place when the synchronisation algorithm of the document uses known symbols and their location at the receiver to achieve synchronisation. The value of these symbols is known.
This place covers:
In this case, the algorithm does not use any known symbols (the value of these symbols and their location is not known in advance).
This place covers:
The Guard Interval structure (when the Guard Interval consists of a cyclic repetition of the useful symbol part, see H04L 27/2607) or any other cyclostationarity of the received signal is used for achieving synchronisation.
The use of a repetition pattern (where instead of a preamble, a data symbol is sent twice, and the receiver uses only the location and the fact that repetition occurred) is considered as being blind and belongs to this class since it uses a kind of cyclostationarity in the received signal.
This place covers:
The algorithm has a feedback loop where decision on received symbols are used to achieve synchronisation.
This place covers:
The constraints given to the algorithm or in other words, the advantage of the algorithm versus conventional algorithms.
This place covers:
The algorithm of the document achieves a better precision (in time or frequency) than conventional algorithms.
This place covers:
The algorithm of the document has a lesser complexity than conventional algorithms.
This place covers:
The algorithm of the document reaches synchronisation more quickly than conventional algorithms.
This place covers:
The algorithm of the document has a wider range of frequencies or delays tested than conventional algorithms.
This place covers:
The algorithm of the document is more resistant to such perturbations or errors than conventional algorithms.
This place covers:
This particular subgroup applies when a synergistic effect is present between the synchronisation arrangement and any other circuit in the course of the synchronisation process (example: Locating the FFT window is often associated with particular peak tracking arrangements for channel estimation).
This place covers:
For the cases where the synchronisation process interacts non-obviously with an interference estimation/cancellation circuit.
Interference aspects are covered in many other classes:
Attention is drawn to the following places, which may be of interest for search:
Inter Symbol Interference removed in Equalizers | |
Interference in receivers | |
Further interference aspects at the receiver (EMI) | |
Interference due to the multiplexing of users (inter-users, inter-cell, adjacent channel) |
This place covers:
The preamble sent by transmitter is constructed or negotiated in the light of the synchronisation process/algorithm used at the receiver.
This place covers:
As mentioned in the example above, the synchronisation process may interact with a particular channel estimation/tracking method.
This place does not cover:
Channel estimation per se |
Attention is drawn to the following places, which may be of interest for search:
Measuring or estimating channel quality parameters |
This place covers:
This subclass like H04L 27/2634 above covers interaction between the OFDM multiplexing and other circuit components.
This place covers:
OFDM/OQAM generally has a real value modulated on each subcarrier and does not necessitate any Guard Interval to be inserted between contiguous symbols. It generally necessitates well localized (in time as well as in frequency domain) pulse shaping function.
This place covers:
Arrangements for the operation, administration, maintenance or provisioning [OAMP] or troubleshooting [OAMPT] of heterogeneous data packet networks, e.g. IP, Ethernet, Next Generation Network or Home Networks, using proprietary or standardised network management architectures (e.g. SDN, NFV) or protocols (e.g. TMN, SNMP, OMA-DM), irrespective of the physical transport medium, the type of service carried or the type of virtualisation (e.g. VNFs, cloud).
Aspects related to the management of the fulfilment of an agreement between two different parties (usually not within the same network/domain), typically known as Service Level Agreement [SLA], are classified in group H04L 41/50.
Aspects related to the monitoring of the performance of network communications are classified in main group H04L 43/00 (e.g. monitoring of QoS parameters).
Aspects related to the testing of a network or a network element are classified in group H04L 43/50.
Aspects relating to specific functions of data storage and retrieval, e.g. in a database, are classified in main group G06F 16/00.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for detecting or preventing errors in the information received | |
Network security protocols | |
Charging, metering or billing arrangements specially adapted for data communications | |
Operation and Maintenance of homogeneous ATM networks | |
Arrangements for monitoring or testing data switching networks | |
Network architectures or network communication protocols for network security | |
Protocols specially adapted for proprietary or special-purpose networking environments involving control of end-device applications over a network | |
Information retrieval; Database structures therefor; File system structures therefor | |
Arrangements for supervision, monitoring or testing for automatic or semi-automatic exchanges | |
Interconnection arrangements between voice switching centres; Network operation, administration, maintenance or provisioning | |
Arrangements providing connection between exchanges | |
Selecting arrangements for multiplex systems using optical techniques | |
Supervisory, monitoring or testing arrangements for wireless communication networks | |
Network traffic or resource management for wireless communication networks |
In this place, the following terms or expressions are used with the meaning indicated:
administration | keeping track of resources in the network and how they are assigned. It includes all the "housekeeping" that is necessary to keep the network under control. |
agent | a software module that performs management functions requested by a manager. |
maintenance | performing repairs and upgrades—for example, when equipment must be replaced, when a router needs a patch for an operating system image, when a new switch is added to a network. Maintenance also involves corrective and preventive measures to make the managed network run "better", such as adjusting device configuration parameters. |
network element | manageable logical entity uniting one or more physical devices which are networked. Network elements usually have management agents responsible for interfacing with the network manager. They can be any type of device, including, but not limited to: nodes, routers, switches, bridges, hubs, network interface controller [NIC] hosts, gateways, servers, modem, IP telephones, IP video cameras, data-centres, computer hosts and printers. A network element can also comprise virtual components and can be partially or completely virtualised. |
network function, NF; Virtual NF, VNF; Physical NF, PNF | functional blocks within a network infrastructure with external interfaces which can be implemented as a virtual network function, VNF or a physical network function, PNF. |
network management, NM | methods, systems, procedures and tools that pertain to the operation, administration, maintenance, provisioning, analysis and troubleshooting of networked systems. |
network management functions | functions that are performed as part of network management including fault management, configuration, accounting, performance, security management [FCAPS]. For virtualised network functions in networked systems NM functions comprise management and orchestration functions for these virtualised network functions. |
network management system, orchestrator network management system | entity that acts in a network manager role for performing network management functions. |
operation | keeping the network up and running smoothly. |
provisioning | configuring resources in the network to support a given service. For example, this might include setting up the network so that a new customer can receive the requested service. |
quality of service | quality measurement or description of the performance of a service, the quality measurement relating to specific network parameters of the network packets related to the service which describe the treatment experienced by the packets while passing through the network, e.g. packet loss, bit errors, bit rate, throughput, goodput, delay, availability or jitter. |
service level agreement | part of a service contract where the level of service between a service provider and a service user is formally defined. |
troubleshooting | maintenance carried out as a result of fault or failure determination, and may result in emergency workarounds until a permanent fix can be carried out. |
In patent documents, the following abbreviations are often used:
MANO | Management and orchestration |
MIB | Management information base |
NM | Network management |
NE | Network element |
NFV | Network function virtualisation |
NMS | Network management system |
OA&M, OAM | Operation, administration and maintenance |
OAM&P, OAMP | Operation, administration, maintenance and provisioning |
OSS | Operations support systems |
PNF | Physical network function |
QoS | Quality of service |
SDN | Software defined networks |
SLA | Service level agreement |
SNMP | Simple network management protocol |
SOAP | Simple object access protocol |
TMN | Telecommunications management network |
VNF | Virtualised (virtual) network function |
In patent documents, the word/expression in the first column is often used instead of the word/expression in the second column, which is used in the classification scheme of this place:
configured to | adapted to or suitable for defining functional features of structural elements |
managed device or managed node | network element [NE] |
managed object | an abstract representation of network resources of the network element that is managed |
management | controlling, commanding or operating |
network manager | Network Management System |
This place covers:
Use of standards NM protocols, standards architecture, arrangement and representation instrumental for a integrated management
This group covers a hierarchy of different miscellaneous aspects focusing on integration and standardisation. Classification is preferably made in the appropriate subdivision below.
This place covers:
Aspects related to modification or specific use of standards NM protocols. Additional examples are TR-069, OMA-DM.
If the type of standardized protocol is merely cited as general information the group is not to be allocated. Not conventional management protocol, like web-based, web service are classified under H04L 41/0246.
This place covers:
Managing network equipments from different vendors following different communication protocols and standards technologies;
Integration products capable of communicating with different managed nodes in their own protocol and capable of representing a unified network view to the network managers.
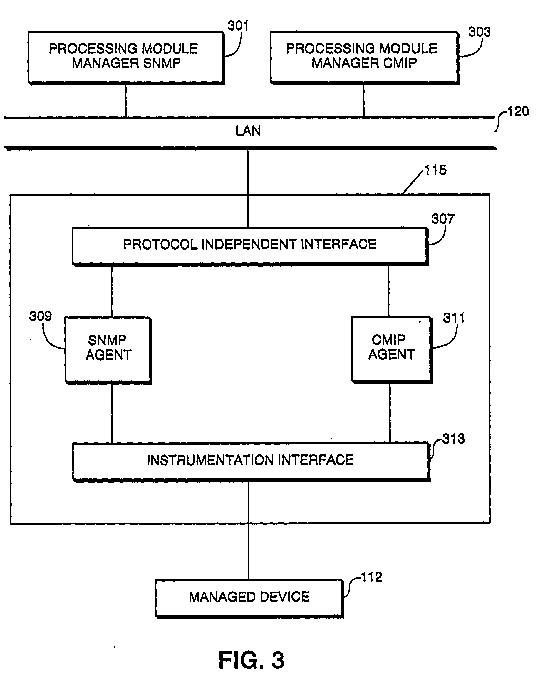
This place covers:
Using different NM protocols, conversion of NM commands and reports from one NM protocol (e.g. CMIP) into another protocol (e.g. SNMP), mapping between different version of the same NM protocols (SNMP v2 and v3);
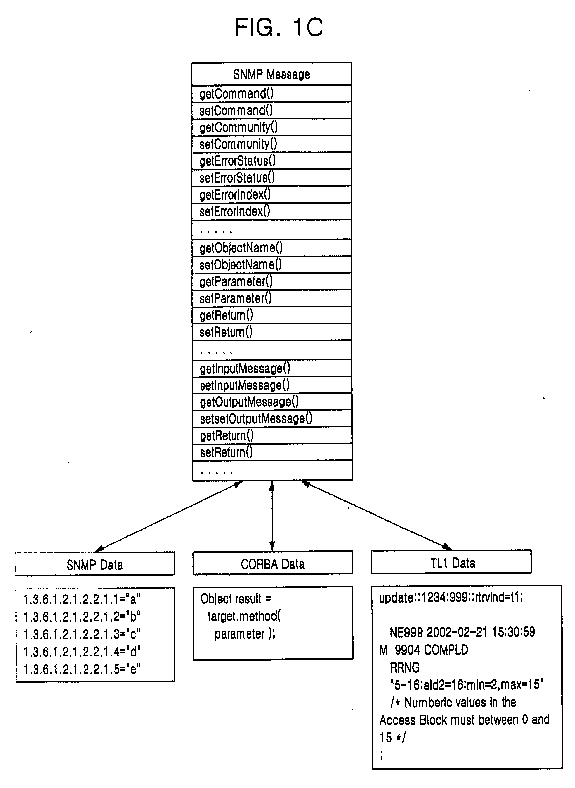
This place covers:
Using object oriented techniques (e.g. CORBA) for representation of NM data. Processing managed entities as Objects.
This class is to be allocated for OO-Techniques other than or beyond the typical use of objects in, e.g., SNMP (e.g. MIB's objects or OMA) which can be considered in the class H04L 41/0213 .
This place covers:
Use of networks being modelled by a (1:1) image in a relational database, e.g, management is done by issuing respective (SQL) commands.
Attention is drawn to the following places, which may be of interest for search:
Information retrieval in structured data stores |
This group relates to aspects where the Internet or web applications and protocols are used for management, and it does not for conventional management protocol, like SNMP.
Aspects of Internet or web applications and protocols in general which are not instrumental to network management functions should be classified in H04L 67/00, in particular H04L 67/02.
The specific management functions should also be classified in the other appropriate H04L 41/00 subgroups, e.g. configuration in H04L 41/08, fault management in H04L 41/06.
Attention is drawn to the following places, which may be of interest for search:
Conversion of network management protocols | |
Web-based network application protocols in general | |
Web-based network application protocols for remote control of end-devices or monitoring of remote application data | |
Proprietary application protocols for remote control of end-devices in special networking environments | |
Retrieval from the Internet |
This place covers:
Aspects relating to accessing the management information by browsing web pages focusing on the communication capabilities.
Attention is drawn to the following places, which may be of interest for search:
Generic visualisation aspects of Graphical User Interface (GUI) for management |
This place covers:
Aspects relating to embedding management objects or management commands or management data by using applications like email, chat.
This place covers:
Aspects relating to use of Internet language data, e.g. html, xml, for formatting management information, e.g. web services data.
This place covers:
Aspects relating to use of SOAP, or other protocols for enveloping/encapsulation of management data.
This place covers:
Aspects relating to timing between the client and server communication (request, response) for monitoring or exchanging management data.
aspects related to push or pull or polling or event-based transmission of management data.
This place covers:
Finding a list of available services, e.g. by using UDDI;
aspects related to how the service is to be accessed, e.g. by using WSDL
Attention is drawn to the following places, which may be of interest for search:
Network applications and protocols for service discovery |
This place covers:
Aspects relating to address resolver (e.g. URL) or path identification for accessing web resources.
Aspects related to physical or logical identification of management client/server.
Aspects of naming and addressing in general is covered by H04L 61/00
This place covers:
Aspects on how the NMS is structurally organised;
Aspects on how the NMS is connected for retrieving the management information.
Attention is drawn to the following places, which may be of interest for search:
Architecture of monitoring probes |
This place covers:
Multiple NM centers or NM units communicating with each other and managing the network together and all managers being on the same hierarchical level - peer to peer relation.
Synchronisation and coordination among different managers.
Examples: EP1624615, EP2053780
The different multivendor network managers under the group H04L 41/022 do not necessarily cooperate with each other but they operate independently.
This place covers:
Hierarchical structures like main manager > medium (mid - level -) managers > sub-managers.
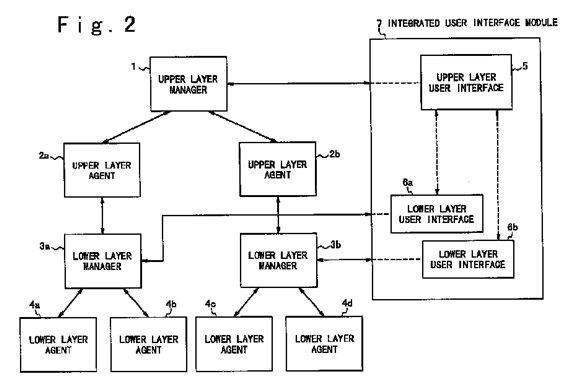
This place covers:
Aspects related to the specific type of NM architecture comprising client and server type of relationship, i.e. one central server and one or multiple clients connected to the server, wherein the management network provides the client-server architecture (architecture of the managed network is irrelevant).
Attention is drawn to the following places, which may be of interest for search:
Standardised network management protocols, e.g. simple network management protocol [SNMP] | |
Protocols for client-server architectures |
This place covers:
Usage of NM agents. Management agents are usually implemented in the managed network nodes themselves or reside "close" to the managed nodes in the network. They usually support the standard NM protocols or provide a mapping functionality between the nodes' proprietary and the managers standardized protocol (e.g. proxy).
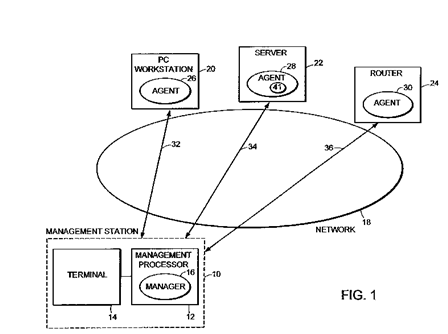
This symbol is to be allocated for use and features of Agents other than or beyond the typical use already done in, e.g., SNMP standardised protocols, which can be considered in the group H04L 41/0213.
This place covers:
Agent which are able to move from one place to another, e.g. from a NMS to a managed element.
This place covers:
Aspects related to the specific type of standard NM architecture used.
This place covers:
Aspects related to the generation, processing of notifications, error messages, managements messages originated from the network instrumental to determine the network behaviour.
Aspects related to active monitoring of the status or availability of the network elements which are triggered by a NMS or a monitoring system are classified under the H04L 43/00 subgroups.
Fault tolerance in computer systems is classified under G06F 11/00. In general, if restoration of faults is performed without a NMS but rather with the involvement of the end nodes (CPUs in multiprocessor systems, Personal Computers in computer networks, or Operating System or applications running on the end nodes) then classification should be done in the G06F 11/00 groups, as indicated below:
Responding to the occurrence of a fault, e.g. fault tolerance | |
Error or fault processing without redundancy, i.e. by taking additional measures to deal with the error/fault | |
Error detection or correction of the data by redundancy in operations | |
Error detection or correction of the data by redundancy in hardware |
Attention is drawn to the following places, which may be of interest for search:
Alarm or failure messages notified by the user, customer (trouble ticket); Alarm or messages triggered by the user, handling of user's trouble tickets | |
Active monitoring the status or the connection of network elements | |
Tracking events generated by the networked application user's | |
Fault management in exchanges' connections |
In this place, the following terms or expressions are used with the meaning indicated:
Error | A deviation of a system from normal operation. |
Fault or failure | Lasting error or warning condition. |
Event | Something that happens which may be of interest. A fault, a change in status, crossing a threshold, or an external input to the system, for example. |
Notification | Unsolicited transmission of management information from network managed entity to network manager. |
Trap | Asynchronous notification from managed device (or agent thereof) to NMS |
Alarm or alert | Indication of the occurrence of a fault. |
faulty entity | a network element or a sub-part thereof in charge of communication functionalities, e.g. NIC. |
This place covers:
Reduction of the notifications' number. Often the network manager is overwhelmed with floods of alarms in complex networks. Filters can be set to only show these events the network managers considers "relevant" at a given time representing a subset.
Aspects related to classification, suppression, grouping of notifications
Attention is drawn to the following places, which may be of interest for search:
Filtering or reduction of monitored data packets | |
Error or fault reporting or logging, in computer systems |
This place covers:
Aspects relating to discriminate among messages which are less or more relevant or urgent.
This place covers:
Aspects relating to discriminate among messages which are originated by different kind of devices (e.g. routers instead of switches).
This place covers:
Filtering/reducing based on topological/geographical information of the network elements.
This place covers:
Filtering/reducing depending on the time the messages were generated.
This place covers:
Aspects related to interventions on the notifications source for stopping or limiting the sending of messages.
This place covers:
Correlating notifications or messages for identifying the relevant information pointing to the same problem.
Determination of the root of a problem in general;
Attention is drawn to the following places, which may be of interest for search:
Identification of network element affecting the current service quality | |
Error or fault localisation, by collation, in computer systems |
This place covers:
Use of additional signalling for locating the root of a problem.
This place covers:
Recovery from network faults with the involvement of a NMS.
Aspects relating to the management signalling for re-establishing the communication functionalities of elements.
Automatically "repairing" broken links, nodes, routes by a NMS when the network is up.
Redundancy within network elements, for example routers with redundant CPUs or interconnections, is classified under G06F 11/00. Where the G06F 11/00 groups refer to "interconnections", they are meant to be physical media and are of point-to-point type or of bus type.
This place does not cover:
Ring fault isolation or reconfiguration |
Attention is drawn to the following places, which may be of interest for search:
Selection of a alternate/backup route | |
Route fault recovery | |
Techniques for recovering from a failure of a protocol instance or entity | |
Error or fault handling in computer systems |
This place covers:
Removing or switching off a faulty entity without replacement.
Command or instructions for dynamically by-passing the faulty entity toward other paths, possibly by informing the neighbouring nodes.
Attention is drawn to the following places, which may be of interest for search:
Reconfiguration of paths in computing systems | |
Active fault-masking in computer systems, where interconnections are redundant |
This place covers:
Re-booting/re-starting (possibly after a waiting time), re-initialise, re-setting or re-configuring (by changing parameters) in order to repair the faulty entity and re-connect it to the network.
Attention is drawn to the following places, which may be of interest for search:
Re-configuration in response to network events | |
Bootstrapping procedure in computers | |
Error or fault handling in computer systems | |
Faults occurring during boot-up procedure in computer systems |
This place covers:
Offline failover planning, command and instructions from the NMS to re-direct to a different path previously calculated.
This place covers:
Replacement by the best or redundant element in terms of similar capabilities/functionalities, not just replacement of the path.
Attention is drawn to the following places, which may be of interest for search:
Active fault-masking in computer systems, where processors are redundant |
This place covers:
Determining or detection of a fault with particularly emphasis on the physical or logical position of the problem with or without event correlation.
Aspects related to the active monitoring of the status of network elements is under H04L 43/00, specifically H04L 43/0817. However, if the monitoring activity gives rise to a the determination of a failure's position then the group H04L 41/0677 is also to be allocated.
Attention is drawn to the following places, which may be of interest for search:
Error or fault detection or monitoring in computer systems |
This place covers:
Aspects relating to the setting of events, fault, alarm or trap conditions or threshold, metrics, which give arise to a error message,definition of a fault.
Aspects relating to when an alert is to be generated.
Attention is drawn to the following places, which may be of interest for search:
Threshold monitoring |
This place covers:
Notification data-model.
Added-value aspects of the content of the notifications, like position, time, failure type, etc..
Adding information to the notifications, description of the notifications' attributes.
This place covers:
Using of libraries, database or data structure parameters for saving alarms, notifications or events.
Off-line extraction or post-processing for statistics purposes or graphical representation
Examples: WO2013023837
Attention is drawn to the following places, which may be of interest for search:
Error or fault reporting or logging in computer systems |
This place covers:
Actions when the manager itself fails;
This place covers:
Aspects relating to dynamic or off-line functionality to perform operations that will provide physical and logical parameters settings to/from network or network elements.
Determination and storing of configuration information.
This place does not cover:
Address allocation |
Attention is drawn to the following places, which may be of interest for search:
Proprietary application protocols for remote control of end-devices in special networking environments | |
Configuration management in the context of software development | |
Configuration of software in general | |
Automatic configuration in wireless networks |
This place covers:
Aspects relating to assign configurations;
Attention is drawn to the following places, which may be of interest for search:
Provisioning or reconfiguring application services over wireless networks | |
automatic configuration in wireless networks |
Attention is drawn to the following places, which may be of interest for search:
Configuration of networked applications configuration parameters | |
Configuration management in the context of software development | |
Configuration of software in general |
This place covers:
Aspects relating to configuration as soon as an element is being connected.
The network element having already configuration parameters ready.
Attention is drawn to the following places, which may be of interest for search:
Software configuration of peripheral devices | |
electrical coupling for live connection to bus |
Attention is drawn to the following places, which may be of interest for search:
topology update or discovery for routing purposes |
This place covers:
Aspects focusing on the aim of the configuration settings, for improving certain conditions, e.g. reliability or reducing downtime.
This place does not cover:
Optimising operational conditions of wireless networks |
This place covers:
Configuration aiming at reducing the number or use or maintenance of network components, devices, links, functionalities or the cost associated to a function of the network or the path.
This place does not cover:
For reduction of network energy consumption |
This place covers:
Aspects relating to reading or auditing configuration information of network elements;
This group covers a hierarchy of different miscellaneous aspects focusing on retrieving configuration data. Classification is preferably made in the appropriate subdivision below.
Attention is drawn to the following places, which may be of interest for search:
Point-in-time backing up or restoration of persistent data |
Attention is drawn to the following places, which may be of interest for search:
Details of restoration of backup data |
This place covers:
Aspects relating to validation, comparison of configuration's data.
This group covers a hierarchy of different miscellaneous aspects focusing on how automatic the configuration is carried out. Classification is preferably made in the appropriate subdivision below.
These groups are usually to be allocated in combination with the other groups of H04L 41/08.
This place covers:
Aspects related to the logical clustering of network elements, e.g. grouping according to configuration parameters or network element functionality.
This place covers:
Aspects related to the definition and/or use of policies and/or rules for the processing of network element configuration data.
Aspects related to network management functionalities within Policy and Charging Control, e.g. 3GPP policy architecture (PCRF, PCEF, SPR).
Attention is drawn to the following places, which may be of interest for search:
Policy and charging Control architecture for metering, charging or billing | |
Network security policies |
This place covers:
Aspects covering specifically operations defined for configuration management when the network or network elements are virtualised.
As far as configuration of the virtualised networks or network elements involves relevant aspects covered by subgroups H04L 41/0803 - H04L 41/0894, these aspects are additionally classified under the relevant subgroups, e.g. operations defined for the activation or instantiation of virtualised entities such as VNFs or Service Chains of VNFs are classified with H04L 41/0895 and H04L 41/0806.
This place covers:
Involvement of a manager for configuring elements in order to cope with the bandwidth request.
This place does not cover:
Flow or congestion control using dynamic resource allocation, e.g. in-call renegotiation |
This place covers:
Aspects dealing with the scaling by instantiating additional or removing virtualised entities or by adapting the capacity of the virtualised entities, e.g. runtime optimisation of network slices or VNFs or VMs.
Aspects dealing with the migration of virtualised entities in a virtualised environment in order to ensure the consistent transfer of information and connections.
Aspects of the orchestrator, cloud manager, SDN controller or virtual network manager entities performing these scaling and migration operations.
Attention is drawn to the following places, which may be of interest for search:
Hypervisor specific management aspects | |
Virtual machine migration in general |
This place covers:
- Determination, retrieval or use of network topology (also based on routing table information) for network management purposes (e.g. Fault localisation, network analysis, configuration, graphical representation, mapping...) Both a link or network layer.
- Discovery of links, network elements and adjacencies within a network;
- Aspects relating to topology change after migration;
- Planning of the appropriate topology.
Attention is drawn to the following places, which may be of interest for search:
Monitor simple connectivity of an element | |
Topology update for routing purposes | |
Point-in-time backing up or restoration of persistent data | |
Topology discovery in wireless networks for routing purposes |
This place covers:
Arrangements and functions wherein the appropriate topology for the virtualised network is determined and established, e.g. based on requirements such as the ones derived from "multi-tenant sites", "multi-sites" and customers' requirements.
Aspects related to the mapping of virtual or logical elements to physical elements, the virtualised network topology comprising hierarchies or layers of network elements and aspects of the distribution of controllers and forwarding entities in the network.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for network security, VPNs | |
Local partitioning of resources |
This place covers:
Aspects related to the analysis or the plan of a network.
Attention is drawn to the following places, which may be of interest for search:
Network monitoring |
This group covers miscellaneous aspects focusing on the analysis of the network.
Classification is preferably made in the appropriate subdivision below.
The sub-groups do not simple relate to monitoring of packets H04L 43/00 but more advanced analysis, analysis of management messages, aggregation of information in different part of the network, analysis of the network as a whole.
If the analysis is only "punctual" (single link, single path, specific elements) monitoring H04L 43/00 is to be considered.
This place covers:
Evaluation of monitored data applying advanced statistical methods and tests going beyond basic counting and averaging of frames, errors. Detecting anomalies, The analysis can be based on input from real data, when the network is or was operative.
Aspects of traffic modelling, e.g. Poisson, Markov, self-similar.
Attention is drawn to the following places, which may be of interest for search:
Generation of artificial traffic for testing |
This place covers:
Network design tools (e.g. with integrated simulation and design testing).
Modelling or abstraction of the network for behaviour simulation.
Attention is drawn to the following places, which may be of interest for search:
Modelling of isolated elements of the network, auditing | |
Network topology's graph or modelling | |
Network design in exchanges connections | |
Radio cell planning |
This place covers:
The outcome of the network's analysis are instrumental for determining the future behaviour of the network, e.g. bandwidth forecast.
Attention is drawn to the following places, which may be of interest for search:
Modelling of isolated elements of the network, auditing | |
Fault management | |
Radio cell planning |
This place covers:
Aspects related to the prediction of the maintenance needs due to the future forecast behaviour of network or network elements.
Attention is drawn to the following places, which may be of interest for search:
Fault management |
This place covers:
Applying artificial intelligence methods (expert systems, rule based systems, genetic algorithms) in NM.
This place covers:
Giving the customer (limited) access to NM functions.
This place covers:
Particular aspects (e.g., customization, programmability or configuration) of NM software tools like HP Openview, Netview 6000, with GUIs (Graphical User Interfaces) capable of managing large and complex data networks.
This place covers:
Using a GUI to represent the architecture of the network.
Which/how the management information are displayed.
Attention is drawn to the following places, which may be of interest for search:
Using a browser for accessing management information | |
Graphical visualization of monitored data |
In group H04L 41/22, the focus is on the graphical representation of the managed network, elements, objects, whereby H04L 41/0253 relates to the access to web-based management content via a browser. Graphical/visualization aspects of web browsers are therefore classified under H04L 41/22.
This place covers:
(Portable) hardware equipment for managing (e.g. configuring, logging management data, etc.) a device at a time.
Craft terminals used by fields technicians.
Built-in NM hardware.
This place covers:
Usually NM tools operating at MAC level.
Examples: US2010281106, US2009113046
This place covers:
Only security related to the NM system.
Aspects relating to keeping the manager and the management data secure.
Restricting access control to the NMS, encryption of management data.
Attention is drawn to the following places, which may be of interest for search:
Cryptography for secret or secure communication | |
Protocols or architecture for network security | |
Protecting computers or computer systems against unauthorised activity | |
Wireless network security |
This place covers:
Process for electing a unit as a master.
Bidding and electing units based on best QoS level.
This place covers:
NM for traditional broadband digital cross-connect switches supporting user's communication, now being replaced by ATM or DSL-based infrastructure.
This place covers:
Aspects of how network administration and management data are transferred, e.g. details of the transport procedure or details of transfer schemes for in-band transport of management data over the same physical and logical infrastructure as the user plane data traffic.
Data signalling between network management entities.
Aspects related to the use of network management tunnels between network devices, e.g. protocols for enveloping/encapsulation of management data.
Attention is drawn to the following places, which may be of interest for search:
Conversion of network management protocols | |
Exchanging or transporting network management information using Internet; Embedding network management web servers in network elements; Web-services-based protocols | |
Web-based network application protocols in general | |
Web-based network application protocols for remote control of end-devices or monitoring of remote application data | |
Proprietary application protocols for remote control of end-devices in special networking environments |
This place covers:
Actions and arrangements involving the communication between virtual network management entities, e.g. NFV-MANO orchestrator, cloud managers, VNFM, VIM, VMs, VNFs.
Actions and arrangements involving communication between a plurality of SDN controllers or communication between a network management entity and orchestrator(s)/controller(s). The communication including signalling between SDN controllers for indicating forwarding information on reachability at one or more layers for network management purposes.
Actions and arrangements involving the communication between an SDN controller and one or a plurality of forwarding entity/entities for network management.
Attention is drawn to the following places, which may be of interest for search:
Management of faults, events, alarms or notifications | |
Configuration management | |
Policy based network configuration management | |
Ensuring SLA | |
Monitoring or testing data switching networks | |
Updating the topology between route computation elements | |
Using an overlay routing layer |
This place covers:
Definition or use of an out-of-band management signalling layer.
Aspects concerning management data transfer via outband or out-of-band (OOB) channel, e.g. wherein OOB signalling is channeled via dedicated NEs which are independent and physically distinct from those in the data network.
Aspects wherein NMS manages NEs even if an inband service channel fails by using a secondary transmission channel dedicated for the transport of network management information.
Attention is drawn to the following places, which may be of interest for search:
Using different networks or paths for security, e.g. using out of band channels |
This place covers:
Aspects covering specific management or orchestration operations to explicitly specify them as being associated to network function virtualisation or resources virtualisation, e.g. virtualisation aspects in fault management.
Aspects covering logical centralisation of network intelligence and state, e.g. virtualisation of network resources as most relevant features such as those defined in Software Defined Network and ETSI NFV Network Function Virtualisation, e.g. NFV Management and Orchestration (NFV-MANO) or 3GPP Network Slice Subnet Management Function (NSSMF) as shown in the figure below.
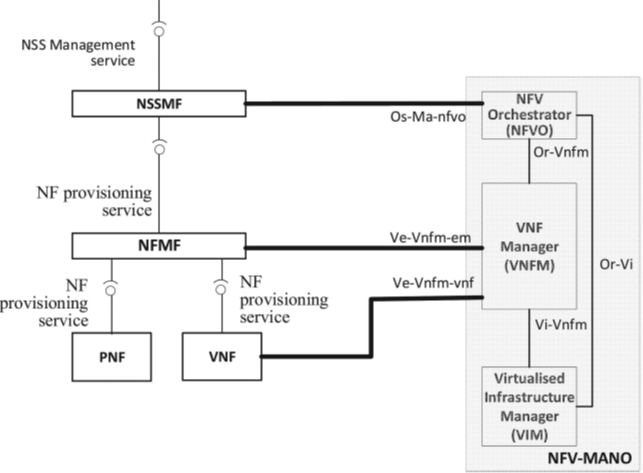
Attention is drawn to the following places, which may be of interest for search:
Arrangements for monitoring or testing data switching networks | |
Routing or path finding of packets in data switching networks | |
Traffic control in data switching networks | |
Packet switching elements | |
Network arrangements or protocols for supporting network services or applications | |
Optical switching |
As far as network management using virtualisation of networks or network elements involves relevant aspects covered by H04L 41/00 subgroups which are not exclusively defined for virtualised entities, these aspects are additionally classified under the relevant subgroups. For instance, root cause analysis in a virtualised network is classified in groups H04L 41/0631 and H04L 41/40
This place covers:
aspects relating to Service level management between parties for service deployment, assurance and review over heterogeneous packet-switched data networks (e.g. IP, Ethernet, ...) irrespective of the physical transport medium and the type of service carried and the type of virtualisation (e.g. cloud).
In this place, the following terms or expressions are used with the meaning indicated:
Service Level Management | provides for continual identification, monitoring and review of the levels of IT services specified in the Service Level Agreements (SLAs). Service Level Management ensures that arrangements are in place with internal IT Support-Providers and external suppliers in the form of Operational Level Agreements (OLAs) and Underpinning Contracts (UCs), respectively. |
Service Level Management functions | ensuring that the agreed IT services are delivered when and where they are supposed to be; liaising with Availability Management, Capacity Management, Incident Management and Problem Management to ensure that the required levels and quality of service are achieved within the resources agreed producing and maintaining a Service Catalogue (a list of standard IT service options and agreements made available to customers) ensuring that appropriate IT Service Continuity plans exist to support the business and its continuity requirements. |
Service Level Agreement, SLA | service level agreement is a part of a service contract where the level of service is formally defined. |
Quality of Service, QoS | quality measure relating to specific network parameters of traffic packets (bit rate, delays, packet loss...) which describe the treatment experienced by the packets while passing through the network . |
SLA vs QoS | In order to meet the SLA requirements specific internal QoS management processes are to be implemented. SLA is namely directed to an 'aggregation' of (end-to-end) QoS parameters rather than to specific internal network metrics or is directed to QoS related to a customer (QoE). |
Quality of Experience, QoE | a subjective measure of a customer's experiences with a service. |
In patent documents, the following words/expressions are often used with the meaning indicated:
"QoS" | of "Service Level performance" (e.g. AU2008201028, paragraph 8) |
This place covers:
General aspects relating to the description of the terms or properties of the SLA.
Aspects relating to mapping/converting SLA requirements into QoS parameters.
Illustrative example of subject matter (ITU-T Rec. E.860) classified in this group.
Attention is drawn to the following places, which may be of interest for search:
SLA negotiation in wireless networks |
This place covers:
Aspects relating to the benchmarking for specific services.
Aspects relating to mean time to failure (mttf), mean time to recover (mttr).
Aspects relating to the overall performance of a network, e.g. Delay, reliability based on aggregation of qos parameters.
Measuring specific key performance indicators (kpi).
Attention is drawn to the following places, which may be of interest for search:
Monitoring performance metrics on a simple network level |
Attention is drawn to the following places, which may be of interest for search:
flow or congestion control at network level |
Attention is drawn to the following places, which may be of interest for search:
Network faults recovery | |
Changing configuration due to adaption |
Attention is drawn to the following places, which may be of interest for search:
Charging, metering or billing arrangements specially adapted for data communications |
This place covers:
Generating a report based on data showing the performance levels for individual customers or individual services
Attention is drawn to the following places, which may be of interest for search:
Initializing Configuration, i.e. provisioning of network or devices |
This place covers:
Identifying service elements or services and dependencies among the elements and services of a network
Attention is drawn to the following places, which may be of interest for search:
Determining the actual topology of a network | |
Topology discovery in routers | |
Arrangements for service discovery, e.g. Service Location Protocol (SLP) |
This place covers:
Order and problem handling, informing end-user of service situation.
This place covers:
- Handling of customer data, contracts, customer history
- Monitoring and recording customer interactions with the provider
- Data mining techniques for customer's data processing
Attention is drawn to the following places, which may be of interest for search:
Arrangements involving Customer Network Management, i.e. giving the customer access to network management functions |
This place covers:
Aspects relating to the quality or satisfaction as perceived by the customer/user, Quality of Experience (QoE).
Aspects relating to reports provided by the customer about the service quality.
This place covers:
Identifying customers affected by service problems as network element failures, network congestion or service degradation.
This place covers:
Aspects relating to the generation of error messages, notifications, issues, incident originated by a customer or a customer's terminal to be treated by the Service Provider.
Attention is drawn to the following places, which may be of interest for search:
Alarm messages (automatically) triggered by faulty network elements |
This place covers:
Aspects wherein access or connectivity to the network itself is the service, e.g. offering VLAN.
The H04L 41/508 groups should be allocated only in combination with at least one of the groups from H04L 41/50 - H04L 41/5074 and only if essential for the characterisation of the service management aspects.
Attention is drawn to the following places, which may be of interest for search:
Web-based network application protocols | |
Web site content organisation and management | |
Video-hosting |
This place does not cover:
Management of VoIP services |
Attention is drawn to the following places, which may be of interest for search:
Protocols for real-time multimedia communications | |
Management of telephonic communication services |
Attention is drawn to the following places, which may be of interest for search:
Protocols for real-time multimedia communications | |
Interactive television or video on demand [VOD] |
Attention is drawn to the following places, which may be of interest for search:
Conducting a computer conference | |
Messaging, e.g. e-mail or instant messaging in packet-switching networks |
Attention is drawn to the following places, which may be of interest for search:
Management of file systems | |
Management of structured data stores |
This place covers:
Network monitoring or telemetry or testing of heterogeneous data packet networks, such as IP, Ethernet, Next Generation Network or Home Networks, irrespective of the physical transport medium, the type of service carried or the type/grade of virtualisation (e.g. SDN, NFV).
Traffic and packet monitoring techniques in main group H04L 43/00 are irrespective of the use which is done of the result and focuses on the monitoring techniques as such, not on the application which may be of different nature.
The group H04L 43/50 focuses on the testing platform, routine, apparatus and configuration.
Aspects related to the generation or insertion of specific type of packets (e.g. ICMP, ping, traceroute) are classified in group H04L 43/10 whereas (test) traffic injection of data according to a pattern and characterisation is classified in group H04L 43/50.
Attention is drawn to the following places, which may be of interest for search:
Network service management, e.g. ensuring proper service fulfilment according to agreements | |
Filtering policies for separating internal from external traffic for security | |
Monitoring for detecting or protecting against malicious traffic | |
Protocols specially adapted for monitoring users' activity | |
Monitoring of computing systems | |
Recording or statistical evaluation of computer activity | |
Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems | |
Supervisory, monitoring or testing arrangements for wireless communication networks |
In this place, the following terms or expressions are used with the meaning indicated:
Active monitoring | Observing the network by actively, adding, marking or injecting data into the network to provide monitoring results with very limited or negligible impact on the monitored network or traffic. |
Monitoring | Monitoring comprising passive and active monitoring. |
Passive monitoring | Observing the network by measuring passing traffic or setting counters, probes or analysers at different points in the network without impacting the network traffic, e.g. traffic mirroring to a sniffer. |
Quality of service | Quality measurement or description of the performance of a service, the quality measurement relating to specific network parameters of the network packets related to the service which describe the treatment experienced by the packets while passing through the network, e.g. packet loss, bit errors, bit rate, throughput, goodput, delay, availability or jitter. |
Testing | Observing the network by adding or injecting data into the network to provide test results with considerable impact on the network or traffic. |
In patent documents, the following abbreviations are often used:
NFV | Network function virtualisation |
QoS | Quality of service |
SDN | Software defined networks |
In patent documents, the following words/expressions are often used with the meaning indicated:
"testing" | "monitoring" or "active monitoring". |
This place covers:
Aspects relating to the selection of specific type/group of packets
This place covers:
Aspects relating to the storing of selection of packets being which is a representative subset of packets.
This place covers:
Dynamically adjusting the sampling rate according to specific criteria, e.g. traffic burstiness, packet rate, statistics.
This place covers:
Aggregating captured packet data into flows, a flow being defined as a unidirectional sequence of packets all sharing same network parameters mainly based on header information.
Monitoring flow, wherein the flow is usually characterised by a n-tuple of network parameters, e.g. Source/destination address, port number, protocol number (e.g. Ietf ipfix, netflow)
Monitoring, identify or classify the flow on different osi-layers.
This place covers:
Reduction of monitored data by applying filters to extract specific type of packets or part of packets;
Deep packet inspection (e.g. Bpf, libpcap) including payload analysis.
Using hashing, masking for extracting and storing packets or part of packets.
Attention is drawn to the following places, which may be of interest for search:
Alarm or event filtering | |
Filtering policy for separating internal from external traffic for security |
This place covers:
Aspects focusing on aggregation and post-processing (including exporting, transmitting) of the monitored data, post-correlation.
Storing or logging of (part of) monitored packets.
Creation of specific data structure of the monitored packets.
This place covers:
Displaying, showing of the monitoring data/result in graphs, x-y axis, drawings.
Attention is drawn to the following places, which may be of interest for search:
Use of a GUI as a tool for monitoring or managing a network | |
Display of network or application conditions affecting the applications | |
Visual indication of the functioning of a computing machine |
This place covers:
Aspects focusing on accumulation of data extracted from packet flows for reporting or for simple statistics purposes.
This place covers:
Reporting the overall traffic on a Tap-Point in the network.
This place covers:
Reporting traffic characteristics for a specific device or network node.
Attention is drawn to the following places, which may be of interest for search:
Reporting of sensed information of home appliances managing a network |
This place covers:
Formatting traffic reports with respect to certain time intervals, e.g. per second, minute, hour, day or week, or configurable timeframes
This place covers:
Aspect of monitoring of packets on a network (link/node) level including QoS parameters;
Aspect of monitoring of network elements' parameters (temperature, power consumption, etc.) via network protocols.
Attention is drawn to the following places, which may be of interest for search:
Measuring performance on a service level |
This place covers:
Monitoring whether a link is active or a device is connected
Checking or verifying both physical and logical connectivity, e.g., by using connectivity/continuity check messages;
Use of techniques at layer 2 or 3 of the OSI-stack.
Attention is drawn to the following places, which may be of interest for search:
Topology's determination |
This place covers:
Monitoring the status of the connected device for whether the device is working properly, monitoring network element resource metrics like memory utilization or printer utilization.
Attention is drawn to the following places, which may be of interest for search:
Monitoring appliance functionality of home appliances | |
Monitoring the activity of the application user |
Attention is drawn to the following places, which may be of interest for search:
Management of events, faults or alarms |
This place covers:
Monitoring of transmission data loss for all upper layers (Layers 2, 3 and above), as e.g. packet/frame/PDU loss, is classified in groups H04L 43/0829/low. A loss is often recognized via expiration of a timer (timeout) and can be caused by full buffer, overloading, discarding.
This place covers:
Monitoring of transmission errors include all layer independent errors which can be recognized after reception of any transmitted data as bit errors (as e.g. CRC/checksum errors), packet errors (as e.g. duplicate packet errors, packets received after close errors), framing errors (frames too long/short), alignment errors, framing checksum (FCS) errors, bad header errors, carrier sense errors, packet collisions, late collision errors, excessive collision errors, backward errors, duplicate message acknowledgements (ACKs), out of order packet errors.
This place covers:
Different type of packet delays (transition time), also due to node or stack processing, buffering.
This class and the groups refer to delays irrespective of the use that is done of the delay information. For example the use of delay information for synchronizing time/clock is to be classified in H04J 3/0635.
This place covers:
Aspects relating to the number of packets.
This place covers:
Level of congestion, i.e. percentage or absolute value of link capacity available or used.
This place covers:
Observing the time required to get a certain amount of bits across a link or path, thus the ratio of bits per time unit.
This place covers:
Monitoring bandwidth or packet data rate used by a traffic stream.
This place covers:
Aspects related to identification of network entities such as nodes, links, applications, that contribute to or are responsible for actual Service Level performance, such as service failure or service quality degradation, wherein the network entities provide the service for which a Service Level Agreement exists.
Aspects related to measuring the contribution of network entities to the actual Service Level.
Aspects of Service Level Management between parties for Service Level Agreement definition, Service Level assurance or Service deployment are covered by H04L 41/50 and its subgroups.
Attention is drawn to the following places, which may be of interest for search:
Management of faults, events, alarms or notifications using root cause analysis; Using analysis of correlation between notifications, alarms or events based on decision criteria, e.g. hierarchy, tree or time analysis | |
Network service management, e.g. ensuring proper service fulfilment according to agreements |
This place covers:
Aspects related to the use of specific (standardised / well-known) 'smart' packets (ICMP, ping, probe packets, etc.) in the monitored network which stimulates a certain reaction from the monitored network.
Attention is drawn to the following places, which may be of interest for search:
Injection or characterization of test traffic |
This place covers:
Inserting time-related information to the exchanged packets.
This place covers:
Aspects specifically related to passive devices, e.g. meters, capturing data units (packets, cells, frames) transiting the monitored communications network;
Distribution, architecture, topology of the monitoring devices like sniffers, taps;
Internal architecture of a probe (buffer, processor).
Attention is drawn to the following places, which may be of interest for search:
Protocol analyser |
This place does not cover:
monitoring for network security |
This place covers:
Monitoring if observed parameters or metrics are within upper or lower thresholds.
This place covers:
Devices able to capture data (i.e. cells, packets or frames) and "understand / parse / decode" the field structure of different networking protocols in a promiscuous mode (i.e. all the data they receive) and able to process the captured data for representing the parsed / decoded data fields along with their meanings of different packets specified by different networking protocols (e.g. Wireshark) in order to facilitate the analysis for a user.
Attention is drawn to the following places, which may be of interest for search:
Simple packet capture with probes | |
Protocol compliance testing |
This place covers:
Aspects covering operations specifically defined for monitoring or testing data switching networks for virtualised systems, virtualised network functions, virtualised entities and network slices, e.g. being performed by an orchestrator, OpenFlow controller, NFV-MANO entities and cloud managers.
As far as the virtualised monitoring system or monitored elements involve relevant aspects covered by other H04L 43/00 subgroups, these aspects are additionally classified under the relevant subgroups.
Attention is drawn to the following places, which may be of interest for search:
Fault Management |
This place covers:
Testing of data networks, with specific focus on the following aspects:
Architectural aspects of testing: layout of the testing environment, design of the testing system, distribution of the testing nodes in the network at specific locations, devices dedicated for testing, or networking devices that have dedicated test modes.
Functional aspects of testing: benchmark testing, design of test scripts, test sequences, traffic patterns to be injected in the network system or device to be tested.
Testing groups of devices: testing groups of devices at once, for speeding-up the testing.
Compliance testing: testing whether a device complies to the specific protocol that it is supposed to adhere to.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for detecting or preventing errors in the information received; testing correct operation | |
Alarm or event or notifications correlation; root cause analysis; by additionally acting on or stimulating the network after receiving notifications | |
Active monitoring (e.g. heartbeat protocols or polling or ping or trace-route) | |
Protocol analysers | |
Testing of service level quality | |
Testing presence of Network Address Translation [NAT], e.g. STUN, TURN, MMUSIC/ICE | |
Arrangements for testing electric properties | |
Software testing in computer systems | |
Line transmission systems; Monitoring; Testing | |
Transmission of information-carrying signals; Monitoring; Testing | |
Time-division multiplex systems; Provisions for broadband connections in integrated services digital network using frames of the Optical Transport Network [OTN] or using synchronous transfer mode [STM], e.g. SONET, SDH; Testing | |
Telephonic communication; Supervisory, monitoring, or testing arrangements in automatic or semi-automatic exchanges | |
Diagnosis, testing or measuring for television systems or their details | |
Selective content distribution; detecting features or characteristics in audio or video streams | |
Selecting arrangements for multiplex systems; Using optical techniques; Testing; Monitoring |
This place covers:
Testing the quality level of a service, e.g. by simulating or emulating service usage by active agents to automatically measure Service Level compliance, testing based on artificial traffic, artificial customer's behaviour.
The determination and monitoring of Service Level performance and of violations of Service Level requirements is covered by H04L 41/5009. Measuring the contribution of individual network components to actual Service Level is covered by H04L 43/091.
Attention is drawn to the following places, which may be of interest for search:
Network Service Management, e.g. ensuring proper service fulfilment according to agreements |
This place covers:
Techniques or arrangements for selectively establishing and maintaining one or a plurality of non-wireless communication paths, from information sources to information sinks, over which information is communicated.
Techniques or arrangements for discovering, establishing or maintaining connectivity information among affiliated equipments, e.g. routing lists. Techniques and arrangements for path selection or path optimisation in the network, be it physical or virtualised, e.g. SDN or NFV.
This place does not cover:
Communication routing or communication path finding in wireless communication networks |
Attention is drawn to the following places, which may be of interest for search:
Arrangements for detecting or preventing errors in the information received by using return channel that carries supervisory signals | |
Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks | |
Arrangements for monitoring or testing data switching networks | |
Flow control or congestion control in data switching networks | |
Packet switching elements characterised by the switching fabric construction | |
Buffering arrangements in packet switching elements | |
Network arrangements, protocols or services for supporting real-time applications in data packet communication | |
Network arrangements, protocols or services independent of the application payload | |
Selective content distribution, e.g. interactive television or video on demand [VOD] | |
Supervisory, monitoring or testing arrangements for wireless communication networks | |
Load balancing or load distribution in wireless communication networks | |
Flow control in wireless communication networks |
This place covers:
Details on network reconfiguration for routing purposes, topology database update and exchange, update of link metrics in a distributed routing system, conversion of physical to logical topology for routing.
Attention is drawn to the following places, which may be of interest for search:
Topology discovery and update for network management | |
Routing tree calculation | |
Topology issues related specifically to wireless networks |
This place covers:
Arrangements to make sure that the routing table contained in each router corresponds to the latest available version.
This place covers:
Delay of the implementation of the just received updates, e.g. so that all nodes implement the update at the same time.
This place covers:
Updating techniques in which update information is broadcast with a hop counter so that only nodes at a certain distance receive the update; region-wise or limited-scope updates.
This place covers:
Routing update or discovery using "hello" or "keep-alive" packets sent or broadcast by a specific router in order to inform the neighbouring routers of its presence or to verify that the neighbouring routers are still up and running.
Attention is drawn to the following places, which may be of interest for search:
Avoiding end of session, e.g. keep-alive, heartbeats, resumption message or wake-up for inactive or interrupted session |
This place covers:
Conditions under which the exchange of routing table updates takes place.
This place covers:
Details on updating link state protocols for routing purposes.
This place covers:
Details on updating distance vector protocols for routing purposes.
This place covers:
Interaction between route computation elements for the purpose of routing topology update, e.g. between controllers located in different network domains.
Attention is drawn to the following places, which may be of interest for search:
Configuration of virtualised networks or elements, e.g. virtualised network function or Openflow elements | |
Interdomain routing, e.g. hierarchical routing |
This place covers:
Route determination in which at least one of the nodes that must be part of the route is selected based on the type of application to be routed.
This place covers:
Selection of paths in order to comprise nodes or devices that provide specific services to end users or end devices, e.g. according to a sequence of actions to be applied to the flow.
This place covers:
Inter-cluster routing Internet routing; provisions in routers for interdomain routing; inter LAN routing with bridges; routing in Hierarchical Networks; all hierarchical aspects of BGP and PNNI.
Attention is drawn to the following places, which may be of interest for search:
Cluster building |
This place covers:
Forwarding, by routing nodes of the received autonomous network data packets, without buffering in order to reduce traffic and network complexity. Hypercubes and hypertorus routing in multiprocessor networks such as the routing used for supercomputers.
Attention is drawn to the following places, which may be of interest for search:
Combinations of two or more digital computers |
This place covers:
Routing with genetic algorithms, fuzzy logic, artificial intelligence (AI) for routing purposes, ants-routing.
Attention is drawn to the following places, which may be of interest for search:
Machine learning per se |
This place covers:
Provisions for routing with virtual circuits; routing in Frame Relay.
Attention is drawn to the following places, which may be of interest for search:
Hierarchy definition for routing in ATM-PNNI | |
Virtualisation or emulation of application or operating system execution engines |
This place covers:
Different techniques for the calculation of the shortest path based on any kind of single metric (Objective Functions) or metrics combination.
Attention is drawn to the following places, which may be of interest for search:
Function evaluation by approximation methods per se |
This place covers:
Using minimum path delay or latency (e.g. queuing delay, round-trip time) in order to determine the best route.
This place covers:
Using the number of intermediate nodes between the source and the destination in order to determine the best route.
This place covers:
Applying a function to a basic parameter such as delay in order to create a new metric, e.g. delay statistics; refine a parameter to create a new metric. The link metric is obtained after operation of a link performance value, e.g. a link metric could be the average loss rate over a time interval.
This place does not cover:
Techniques for monitoring network metrics |
This place covers:
Details on using a combination of parameters to determine the best path, including constrained shortest path calculation. The parameter is a basic parameter or a combined/new parameter.
This place covers:
Routing based on minimum link metrics relating to available rate in the links; congestion, link occupancy.
This place covers:
Routing based on determining the paths having the minimum physical length
This place covers:
Using different parameters of intermediate routing nodes as a route calculation metric, e.g. processing or storage capabilities.
Attention is drawn to the following places, which may be of interest for search:
Battery capabilities in wireless routing |
This place covers:
Determining whether two routes between the same end-points do not share nodes or links.
This place covers:
Determining whether two routes between the same end-points do not share links.
This place covers:
Determining whether two routes between the same end-points do not share nodes.
This place covers:
Performance, stability and graph theory, e.g. Directed Acyclic Graph, DAG, Bellman-Ford, Dijkstra and other basic routing algorithms for path selection.
Attention is drawn to the following places, which may be of interest for search:
Function evaluation by approximation methods per se |
This place covers:
Specific arrangements for supporting broadcast such as dedicated routing tables or route discovery for multipoint packets.
Attention is drawn to the following places, which may be of interest for search:
Broadcast in general |
This place covers:
Specific arrangements for shortcut routing, e.g. NHRP.
This place covers:
Routing arrangements for avoiding packets from travelling in loops, e.g. an identifier in a message is saved in a node to check if the same message is again passing the node; updating of a routing table is inhibited for a certain period of time, routing is only allowed in a certain direction.
Attention is drawn to the following places, which may be of interest for search:
Updating of a routing table, wherein the updated routing values are inhibited for a certain period of time | |
Spanning tree techniques |
This place covers:
Age, time to live or hop counting for broadcast or loop free, such as Layer 2 TTL, timestamp to age out.
This place covers:
Routing techniques using different routes for communication between two nodes in which only one of the routes is used at a time; route diversity; primary and secondary routes; re-routing; 1:1 protection; link or path protection; shared link risk groups.
This place covers:
Routing techniques using multiple routes between two nodes used simultaneously for load sharing or higher speed, including when involving packet fragmentation; redundant transmission, 1+1 and n:m path redundancy.
Attention is drawn to the following places, which may be of interest for search:
Load sharing/balancing (without additional routing features) |
This place covers:
Details on multipath routing using a different number of parallel active paths for redundancy purposes.
This place covers:
Using a logical identity for the selection of a physical link among all possible physical links between two terminals or nodes; trunk group/Link aggregation.
This place covers:
Details on multipath routing using a different number of active and standby paths for redundancy purposes.
This place covers:
Packets adapted for discovery of communication paths; scout packet; delay measuring packet; buffer occupancy measuring packet; path restoration message after route fault; traceroute; exploratory agent packet.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for monitoring or testing data switching networks | |
RREQ-RREP for wireless routing |
This place covers:
Recovery of communication routes after route fault or node failure.
Attention is drawn to the following places, which may be of interest for search:
Using network fault recovery |
This place covers:
Selection of a path for multiclass traffic.
Attention is drawn to the following places, which may be of interest for search:
Routing based on transmission quality or channel quality |
This place covers:
Route selection based on a requested QoS, such as delay, bandwidth etc., in which the selected route has a minimum requested QoS.
Attention is drawn to the following places, which may be of interest for search:
Routing based on shortest path evaluation |
This place covers:
Selecting a path specially adapted for signalling purposes, route determination for signalling traffic, setting up and reservation of special routes for signalling and control traffic.
Attention is drawn to the following places, which may be of interest for search:
Modification of handling priority for control packets, e.g. for ACK or signalling traffic |
This place covers:
Selecting a path based on the nature of the application, e.g. browsing traffic HTTP, FTP traffic; content delivery networks using name based addressing.
This place covers:
Route determination for real time traffic, e.g. voice and video.
Attention is drawn to the following places, which may be of interest for search:
Real-time or near real-time messaging, e.g. instant messaging [IM] | |
Network arrangements, protocols or services for supporting real-time applications in data packet communication | |
Selective video distribution |
This place covers:
Route determination based on the profile of the user or Service Level Agreement of the user; policy-based routing.
This place covers:
Techniques of routing in which packets are sent unconstrained into the network with a unicast address and only one destination is expected to receive the packets, the other nodes act as blind relays; limited flooding with a hop count.
This place does not cover:
Denial of service attacks |
This place covers:
Routing techniques in which route preference (e.g. intermediate nodes) is declared in the packet or in which intermediate nodes record in a specific object the set of nodes through which a route establishment message passes and contents of record object are used for explicitly routing packets in subsequent messages.
Attention is drawn to the following places, which may be of interest for search:
Routing using backward learning |
This place covers:
Routing based on learning address/port relationship from the passing traffic; learning the route followed from source to destination to use it again for the return traffic; update routing tables with learned relationship from passing traffic.
This place covers:
Routing techniques in which all packets in a flow are routed in the same manner along a routing path.
This place covers:
Routing operation pipelining for faster processing, e.g. cut-through, streaming or on the fly.
Attention is drawn to the following places, which may be of interest for search:
Cut-through or Wormhole switching | |
Store and forward switching |
This place covers:
Routing in which a central entity collects (query/response) the routing metrics, calculates the appropriate routes and disseminates the routing information to the rest of the routers.
This place covers:
Arrangements for routing performed in a distributed manner, e.g. each node calculates the appropriate routes and disseminates the routing information to the rest of the routers and no central entity is responsible for routing.
This place covers:
Routing in hierarchical networks; hierarchy definition; criteria for cluster membership.
Attention is drawn to the following places, which may be of interest for search:
Interdomain routing | |
Wireless routing for defining a routing cluster membership |
This place covers:
Routing techniques adapted to tree topologies; spanning tree.
This place covers:
Routing aspects related to multiple trees, including definition, update and use of multiple tree topologies; multiple spanning trees.
This place covers:
Routing aspects related to determination of the route node in tree topologies.
This place covers:
Routing techniques using label swapping, e.g. multi-protocol label switching MPLS.
Attention is drawn to the following places, which may be of interest for search:
Traffic engineering |
This place covers:
Routing techniques using label swapping on frame-based transport, e.g. MPLS over IP based technology.
This place covers:
Routing techniques using label swapping on cell-based transport, e.g. MPLS over Asynchronous Transfer Mode (ATM) networks.
This place covers:
Routing techniques detailing how to spread the labels among the nodes, e.g. Label Distribution Protocol (LDP).
This place covers:
Routing in networks having coexisting different routing protocols, e.g. RIP and OSPF, separated IPv4 and IPv6 routing stacks.
This place covers:
Details of the information and format of the routing tables; special routing tables.
This place covers:
Details on operating systems for routers, routing software architecture, scheduling of routing tasks software.
This place covers:
Details on download or update of software for routing, e.g. initialization of download of routing software or software for improving security of routing decisions, downloading of modified versions of routing software.
This place covers:
Data packets containing routing instructions, e.g. routing instructions to modify the routing tables.
This place covers:
Association of routers for multiple purposes, e.g. Active (working)-Standby (reserve) routers, load balancing or load sharing, multiple physical routers or multiple routing instances (hard or soft) in the same device behave as a single logical routing entity.
This place covers:
Plurality of router instances (hard or soft) connected to, for example, the same backplane; physical association of routers, e.g. located in the same hardware chassis.
This place covers:
Plurality of physical routers behaving as a logical unit, e.g. working in active/standby, Virtual Router Redundancy Protocol (VRRP).
Attention is drawn to the following places, which may be of interest for search:
Virtualisation or emulation of application or operating system execution engines |
This place covers:
Details concerning physical or hardware structure of a routing unit.
This place covers:
Routing specially adapted for optical networks, e.g. selection of the wavelength.
This place does not cover:
Optical switching |
Attention is drawn to the following places, which may be of interest for search:
Optical communications | |
Selecting arrangements for multiplex systems |
This place covers:
Multiple layers comprising a routing control layer specialized in topology update and routing policy determination, and a data layer under the routing layer, including separation of controlling and forwarding.
This place covers:
Impact in the routing strategy of a separation between the routing control (computation) layer and the data (forwarding) layer. The route selection intelligence is (logically) centralised in software-based controllers (Path Computation Elements) that maintain a global view of the network topology, which appears to forwarding elements as a single, logical entity.
Attention is drawn to the following places, which may be of interest for search:
Network topology discovery or management |
This place covers:
Forwarding and updating of routing rules or flow table information between controllers and forwarding elements, e.g. routing table reconfiguration.
Attention is drawn to the following places, which may be of interest for search:
Network topology discovery or management |
This place covers:
Routing based on data link layer, e.g. using MAC address for routing.
This place covers:
Routing comprising emulation of services such as Frame Relay, ATM, ethernet, TDM and SONET/SDH over packet switched networks using IP or MPLS.
This place covers:
Routing based on monitoring, measuring or observing of parameters needed for routing or how these parameters are measured.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for monitoring or testing packet switching networks |
This place covers:
Route or next hop determination based on the sender's node address indicated in a data packet.
This place covers:
Details on address processing for routing purposes.
Attention is drawn to the following places, which may be of interest for search:
Network arrangements, protocols or services for addressing or naming |
This place covers:
Routing between domains using different addressing schemes.
This place covers:
Details on route cache as a way to shorten table lookup operations, e.g. the complex lookup operation in the general table is done only on the first packet of a sequence, aging of route cache entries.
This place covers:
Details on address table lookup and address filtering for routing purposes.
Attention is drawn to the following places, which may be of interest for search:
Network arrangements, protocols or services for addressing or naming |
This place covers:
Details of lookup operations that are conducted in parallel or in serial (cascading or series of consecutive lookups), using different lookup strategies.
This place does not cover:
Lookup operation involving Bloom filters |
This place covers:
Details on routing techniques using hashing operations.
This place covers:
Use of Bloom filters in lookup operations as an alternative to the single hashing lookup.
Attention is drawn to the following places, which may be of interest for search:
Complex mathematical operations |
This place covers:
Details on address table lookup operations and address filtering for routing purposes using content-addressable memories [CAM].
This place covers:
Use of longest prefix match in routing operations.
This place covers:
Routing in virtual network topologies where virtual machines are adapted to run routing protocols.
Attention is drawn to the following places, which may be of interest for search:
Virtualisation or emulation of application or operating system execution engines |
This place covers:
Details on ingress point selection by the source node for routing purposes.
This place covers:
Selection among different networks for routing purposes.
This place covers:
Dynamic network selection or re-selection for routing purposes, e.g. using artificial intelligence (AI).
This place covers:
Traffic control in data switching networks such as traffic regulation, flow or congestion control.
This place does not cover:
Arrangements for detecting or preventing errors in the information received |
Attention is drawn to the following places, which may be of interest for search:
Arrangements for connecting between networks having differing types of switching systems, e.g. gateways | |
Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks | |
Arrangements for monitoring or testing data switching networks | |
Routing or path finding of packets in data switching networks | |
Packet switching elements characterised by the switching fabric construction | |
Buffering arrangements in packet switching elements | |
Network arrangements, protocols or services for supporting real-time applications in data packet communication | |
Network arrangements or protocols for supporting network services or applications | |
Network arrangements, protocols or services independent of the application payload | |
In-band adaptation of TCP data exchange; In-band control procedures | |
Parsing or analysis of headers independent of the application payload | |
Software simulation, e.g. virtualisation or emulation of application or operating system execution engines | |
Allocation of resources in multiprogramming arrangements | |
Computing arrangements using neural network models | |
Learning methods for neural networks | |
Machine learning | |
Selective content distribution, e.g. interactive television or video on demand [VOD] | |
Supervisory, monitoring or testing arrangements for wireless communication networks | |
Load balancing or load distribution in wireless communications networks | |
Flow control in wireless communications networks | |
Communication routing or communication path finding in wireless communication networks | |
Wireless resource allocation |
In this place, the following terms or expressions are used with the meaning indicated:
congestion control | preventing a sender from overwhelming the network, wherein the network is prevented from becoming congested. |
flow control | preventing a sender from overwhelming a receiver wherein traffic is controlled between a sender and receiver such that only the receiver controls the transmission rate. |
policing | performing an action (typically transmit/pass) to packets that conform to a specified rate and performing another action (typically drop) to packets that violate that rate. |
quality of service, QoS | description or measurement of the overall performance of a service, typically represented by packet loss, bit errors, bit rate, throughput, goodput, delay, availability or jitter. |
queuing and scheduling | splitting traffic into a plurality of queues or buffers based on various criteria (such as type of packet, QoS requirements or user) so that a scheduler can decide which packet to service next based on a service discipline, e.g. longest queue first, round robin. |
traffic shaping | a bandwidth management technique to make traffic conform to a certain rate by delaying the transmission of packets in a buffer. Delayed packets may be subsequently transmitted/released as bandwidth becomes available. |
In patent documents, the following abbreviations are often used:
ACK / NAK / NACK | Acknowledgement / Negative acknowledgement |
DSCP | Differentiated service code point |
FIFO / LIFO | First / Last in first out |
HOL | Head of line |
MTU | Maximum transmission unit |
QoS | Quality of service |
RED | Random early discard |
RR | Round robin |
WRR | Weighted round robin |
RSVP | Resource reservation protocol |
RTCP | Real-time transport control protocol |
RTP | Real-time transport protocol |
RTT | Round trip time |
SLA | Service level agreement |
TCP | Transmission control protocol |
ToS / CoS | Type of service / Class of service |
TTL | Time to live |
UDP | User datagram protocol |
VC | Virtual channel |
VQ | Virtual queue |
WFQ | Weighted fair queuing |
This place covers:
General aspects of flow control or congestion control which do not fall under a sub-class.
In this place, the following terms or expressions are used with the meaning indicated:
Flow control | Prevent a sender from overwhelming a receiver, traffic is controlled between a sender and receiver, only the sender controls the transmission rate |
Congestion control | Prevent a sender from overwhelming the network, the network is prevented from becoming congested |
This place covers:
Congestion monitoring to detect a degradation in network performance, using QoS parameters which indicate congestion or impending congestion. Typically exemplified by increased delays, jitter, packet losses or errors, increased retransmission rates. In response, congestion control or congestion avoidance is activated.
Attention is drawn to the following places, which may be of interest for search:
Maintenance or administration or management of packet switching networks; Bandwidth or capacity management, i.e. automatically increasing or decreasing capacities, e.g. bandwidth on demand | |
Network monitoring of the performance of a network communications and QoS parameters | |
Routing; Evaluation of link metrics |
This place covers:
Either the receiver or intermediate nodes in the network can explicitly signal back to the sender that congestion has been identified using a dedicated packet rather than piggybacking a congestion indication in a data packet. The dedicated packet indicating congestion can be sent by a network controller, receiver, or intermediate node.

Attention is drawn to the following places, which may be of interest for search:
Maintenance or administration or management of packet switching networks | |
Network monitoring of the performance of a network communications and QoS parameters |
This place covers:
Techniques for avoiding congestion including: monitoring ACKs and retransmissions at the sender, receiving feedback from the receiver. In response, the transmission rate, window size, etc. are adjusted.
Attention is drawn to the following places, which may be of interest for search:
Routing | |
Load balancing, e.g. traffic engineering | |
Wireless Routing |
This place covers:
Localising congestion and selecting a different path/port/route with less congestion.
Attention is drawn to the following places, which may be of interest for search:
Routing | |
Routing to minimize delay | |
Routing based on performance – link metrics | |
Routing based on performance – bandwidth | |
Alternate routing – switching to a different path | |
Multipath routing – using multiple paths simultaneously | |
Wireless Routing |
This place covers:
General field which relates to redistributing or balancing the flow to either avoid or recover from congestion. Load distribution can divert flow to different intermediate network nodes, paths, ports, queues or servers.
This code should be considered as a general one and applicable to H04L 45/00 and H04L 47/00 as well as to other fields in H04L.
Attention is drawn to the following places, which may be of interest for search:
Routing; Routing – Load balancing; Wireless Routing | |
Network-specific arrangements or communication protocols supporting networked applications; Load balancing among servers | |
Wireless flow control; Wireless load balancing |
This place covers:
By monitoring to detect or forecast the onset of congestion and pre-emptively trigger congestion avoidance and recovery techniques.
Attention is drawn to the following places, which may be of interest for search:
Network monitoring of the performance of a network communications and QoS parameters | |
Resource allocation of traffic control in data switching networks, based on usage prediction | |
Real-time communications e.g. video streaming, voice conferencing QoS aspects |
This place covers:
Techniques for congestion avoidance or recovery at a destination node.
Attention is drawn to the following places, which may be of interest for search:
Resource usage – mobile terminals |
This place covers:
Techniques for congestion avoidance or recovery in a local area network, e.g. LAN segment, ring network or bus network.
Attention is drawn to the following places, which may be of interest for search:
Bus networks with decentralised control | |
Loop networks with decentralised control with asynchronous transmission, e.g. token ring, register insertion | |
LAN switches, e.g. ethernet switches |
This place covers:
When a collision condition is detected, the station stops transmitting that frame, transmits a jam signal, and then waits for a random time interval before trying to resend the frame, e.g. CSMA/CD in Ethernet segments.
This place covers:
Flow and congestion control for multicast/multipoint flows, e.g. source based control, receiver driven layered approaches, exploitation of IGMP and multicast routing protocols, admission control, TCP friendly rate control.
This place does not cover:
Arrangements for multicast in data networks |
Attention is drawn to the following places, which may be of interest for search:
Arrangements for providing special services to substations for broadcast or conference, e.g. multicast with traffic restrictions for efficiency improvement, e.g. involving subnets or subdomains | |
Routing multicast |
This place covers:
Neighbouring nodes cooperate to control the flow either using reservation, policies, PAUSE, backpressure, e.g. a congested node stops receiving packet from upstream node. This may cause the upstream node or nodes to become congested and rejects receiving data from above nodes. Backpressure is a node-to-node congestion control technique that propagate in the opposite direction of data flow.
Attention is drawn to the following places, which may be of interest for search:
Flow control or congestion control using information about buffer occupancy at either end or transit nodes | |
LAN switches, e.g. ethernet switches | |
Backpressure | |
Queuing arrangements |
This place covers:
Congestion control and flow control is implemented between the sender and receiver.
This place covers:
Protocols adapted to include flow and congestion control techniques often in the context of client-server applications, e.g. TCP friendly rate control for UDP, TFRC. Application layer protocols adapted to support real-time communications: RTP, RTCP, RTSP, SIP etc.
When this scheme is crossed with H04L 67/00, it will yield documents concerning flow control in client/server communication.
Note: There is a specific subgroup dedicated to TCP related congestion control, see H04L 47/193 and H04L 69/163.
This place does not cover:
Network-specific arrangements or communication protocols supporting networked applications; For scheduling or organising the servicing of application requests |
Attention is drawn to the following places, which may be of interest for search:
Network monitoring of the performance of a network communications and QoS parameters | |
Network-specific arrangements or communication protocols supporting networked applications; For scheduling or organising the servicing of application requests | |
Application independent communication protocol aspects or techniques in packet data networks; Adaptation of TCP data exchange control procedures;Adaptation of UDP |
This place covers:
Modifications or adaptations of classical TCP behaviour.
Attention is drawn to the following places, which may be of interest for search:
Monitoring; Delay | |
Network delay | |
Slow start – only if it describes a modification to the standard slow start | |
TCP/IP; Adaptations of TCP exchange control procedure | |
Traffic management, e.g. flow control or congestion control adapting protocols for flow control or congestion control to wireless environment, e.g. adapting transmission control protocol [TCP] |
This place covers:
Congestion control techniques based on integration of transport layer protocols.
Attention is drawn to the following places, which may be of interest for search:
Application independent communication protocol aspects or techniques in packet data networks | |
Combined use of TCP and UDP |
This place covers:
Monitoring network traffic for compliance with a traffic contract and taking steps to enforce that contract at an ingress node. Traffic is monitored, metered and classified as being compliant/exceeding/violating the contract. The traffic contract can be described through various parameters: committed Information Rate CIR, Committed Burst Size CBS, and Excess Burst Size EBS. To enforce the contract, traffic can be discarded, flow control can be implemented (e.g. leaky buckets, traffic shaping and token buckets) or traffic can be marked as non-compliant, e.g. setting an ECN flag, DE, DSCP).
Attention is drawn to the following places, which may be of interest for search:
Ensuring SLA | |
Network monitoring of the performance of a network communications and QoS parameters |
This place covers:
A sender's packet is buffered in a leaky bucket. Packets are egressed from the leaky bucket at a constant rate. Consequently, bursty traffic is controlled and egressed as constant rate. Typically, the bucket is a finite queue that outputs at a finite rate.
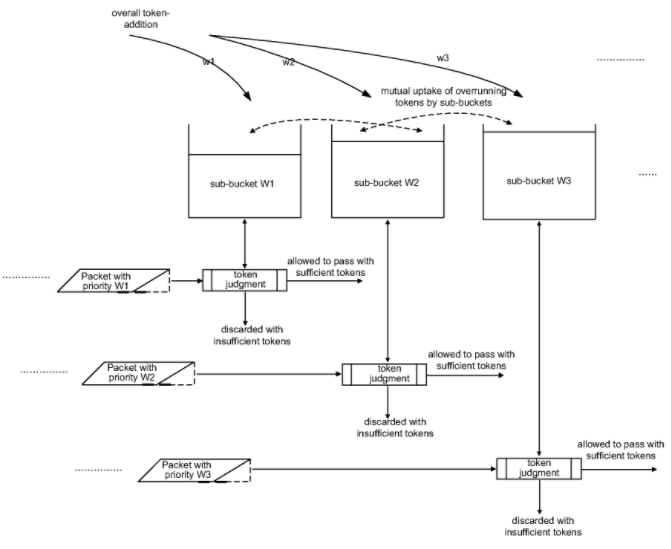
Attention is drawn to the following places, which may be of interest for search:
Network monitoring of the performance of a network communications and QoS parameters |
This place covers:
A token bucket extends from the leaky bucket to allow flexibility for bursty traffic. Packets are egressed from the bucket in accordance with a deduction of corresponding tokens. Tokens are replenished at regular intervals.
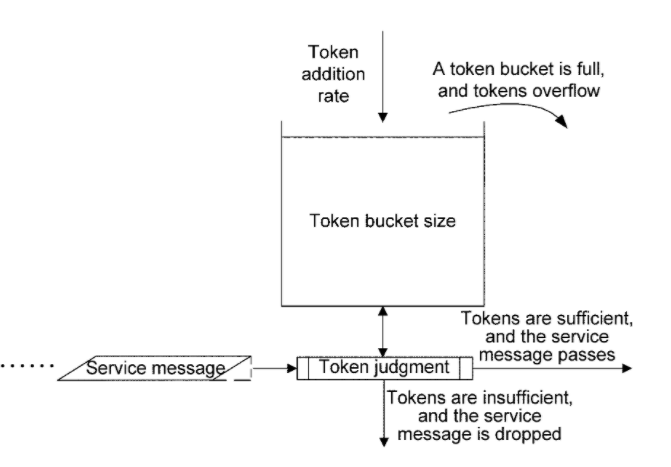
Attention is drawn to the following places, which may be of interest for search:
Network monitoring of the performance of a network communications and QoS parameters |
This place covers:
Traffic shaping (also known as packet shaping) is a bandwidth management technique that delays the flow of certain types of network packets in order to ensure network performance for higher priority applications. Traffic shaping limits the amount of bandwidth that can be consumed by certain types of applications.
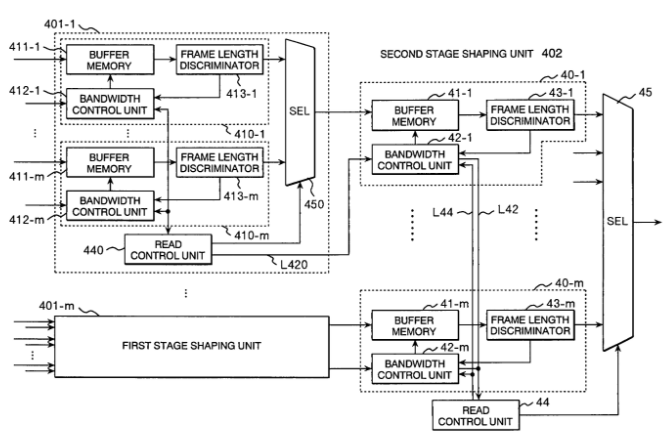
Attention is drawn to the following places, which may be of interest for search:
Maintenance or administration or management of packet switching networks | |
Bandwidth or capacity management, i.e. automatically increasing or decreasing capacities, e.g. bandwidth on demand |
This place covers:
The shaping rate throttles the rate of packet transmission by setting a maximum bandwidth as a transmission rate or a maximum percentage of bandwidth for a queue or a forwarding class set.
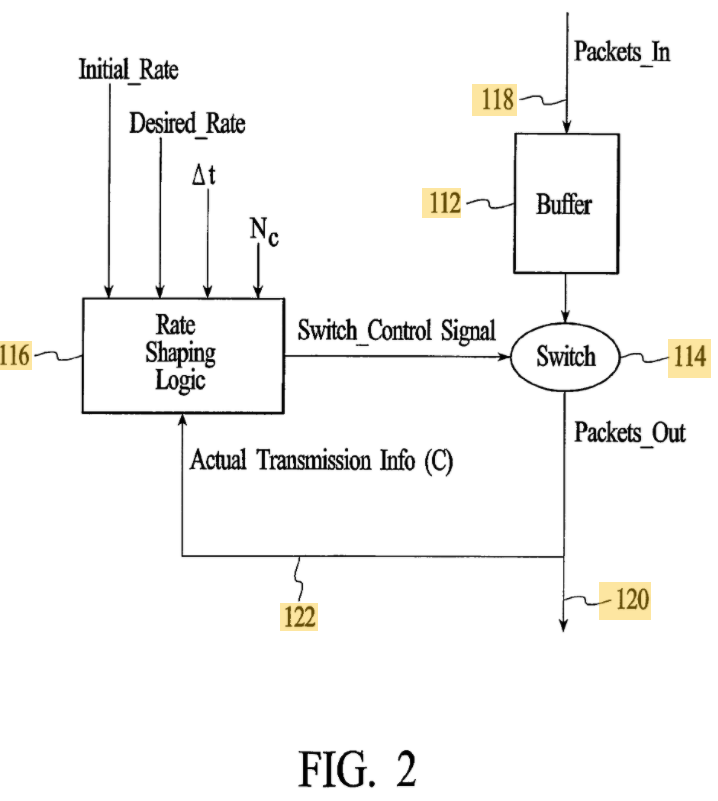
Attention is drawn to the following places, which may be of interest for search:
Packet Switching Systems | |
Quality of Service based |
This place covers:
Network arrangements for networked applications for scheduling or organising the servicing of application requests whereby quality of service or priority requirements are taken into account.
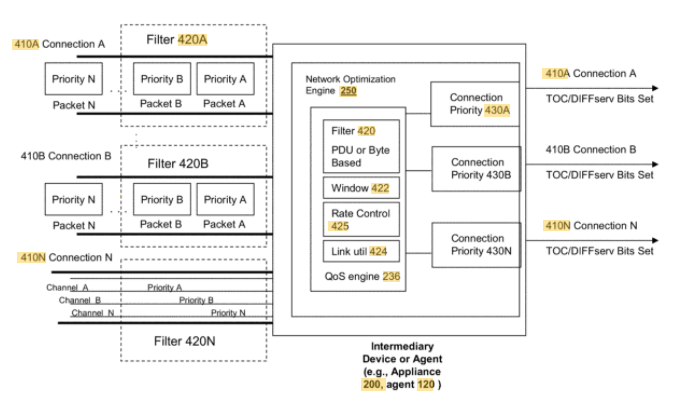
This place covers:
Diff-Serv or differentiated services. Tags or labels (e.g. Class of Service CoS, Type of Service ToS, DSCP) in the packet header are used to provide a classification category of the type of traffic, wherein based on the tag or label, the packet receives a particular treatment or QoS in the network, for example: assured, expedited, default forwarding, class selection.
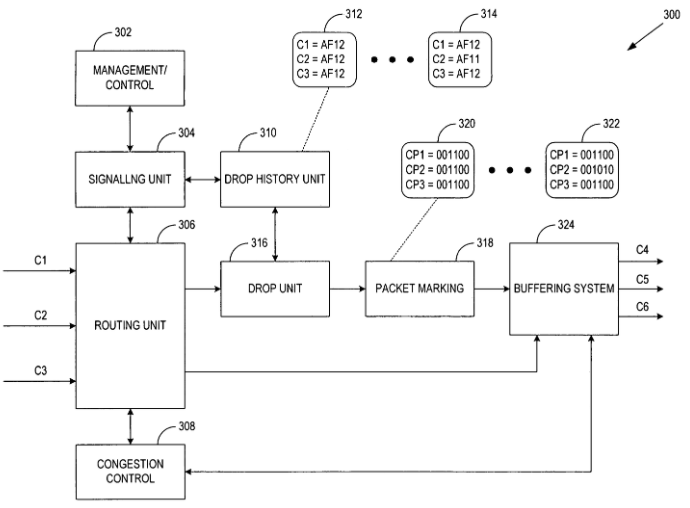
Attention is drawn to the following places, which may be of interest for search:
Special provisions for routing multiclass traffic | |
Route determination based on requested QoS |
This place covers:
Flow control actions in relation to, for example, voice or video traffic.
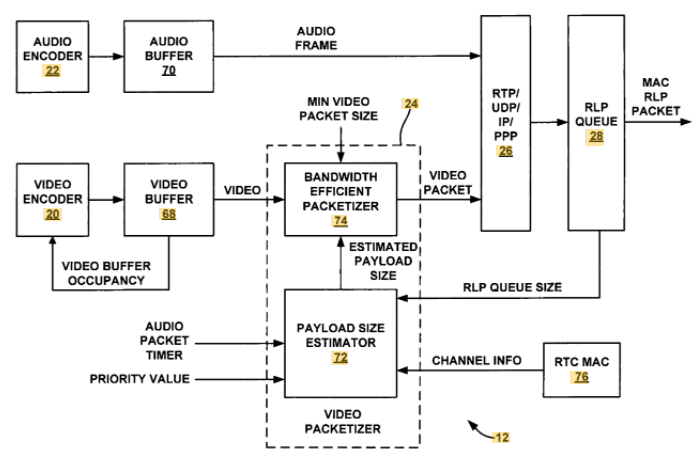
Attention is drawn to the following places, which may be of interest for search:
Real-time bi-directional transmission of motion video data | |
Selective content distribution, e.g. interactive television or video on demand [VOD] |
This place covers:
Service-level agreements [SLAs] are contracts that specify the performance parameters within which a network service is provided. The SLA might define parameters such as the type of service, data rate, and what the expected performance level is to be in terms of delay, error rate, availability, and network uptime.
Attention is drawn to the following places, which may be of interest for search:
General aspects of SLA management | |
Determining service level performance, e.g. measuring SLA quality parameters, determining contract or guarantee violations, response time or mean time between failure [MTBF] | |
Ensuring SLA |
This place covers:
Congestion avoidance techniques adapted to perform allocation of priorities for each traffic type.
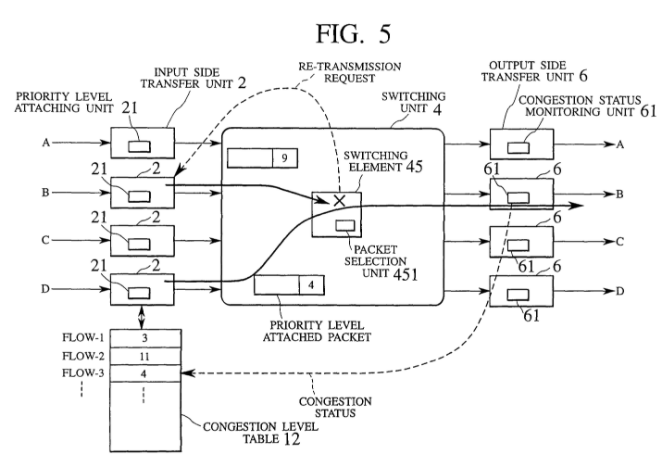
Attention is drawn to the following places, which may be of interest for search:
Priority, marking, classes | |
Quality of Service based |
This place covers:
IntServ is an architecture that identifies the elements needed to specify and guarantee QoS in networks. IntServ architecture is adapted to determine and classify incoming flows to apply the suitable policy. Every node in the system implements IntServ, and every application that requires some kind of QoS guarantee has to make an individual reservation. Flow specifications describe what the reservation is for, while RSVP is the underlying mechanism to signal it across the network.
This field can be generally applied to the determination of the class of the flow according to a given criteria(e.g. QOS). Queuing actions or corresponding flow control actions can be applied thereafter.
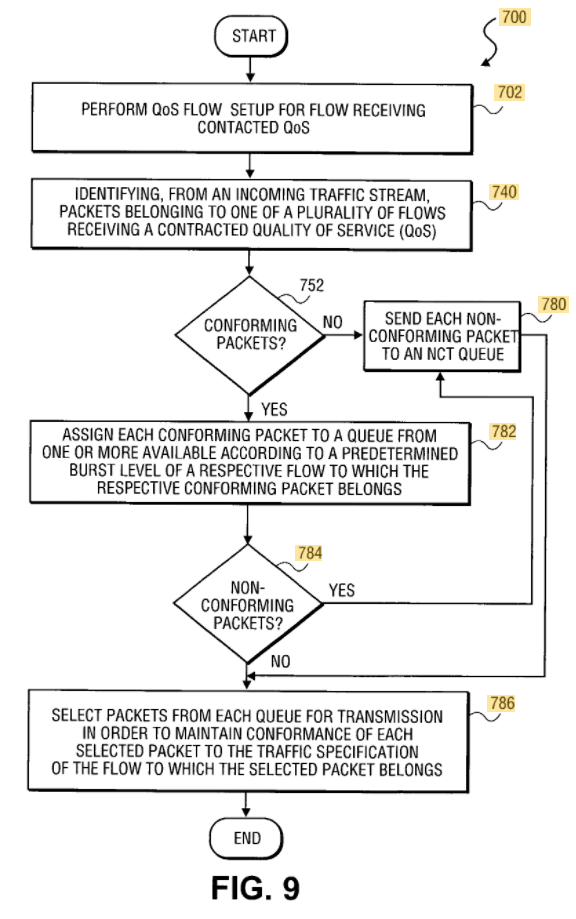
This place covers:
Higher priority traffic (real-time, critical, public safety) is allowed to take precedence or pre-empt lower priority traffic when being scheduled, queued, allocated resources, or more generally when being communicated through the network.
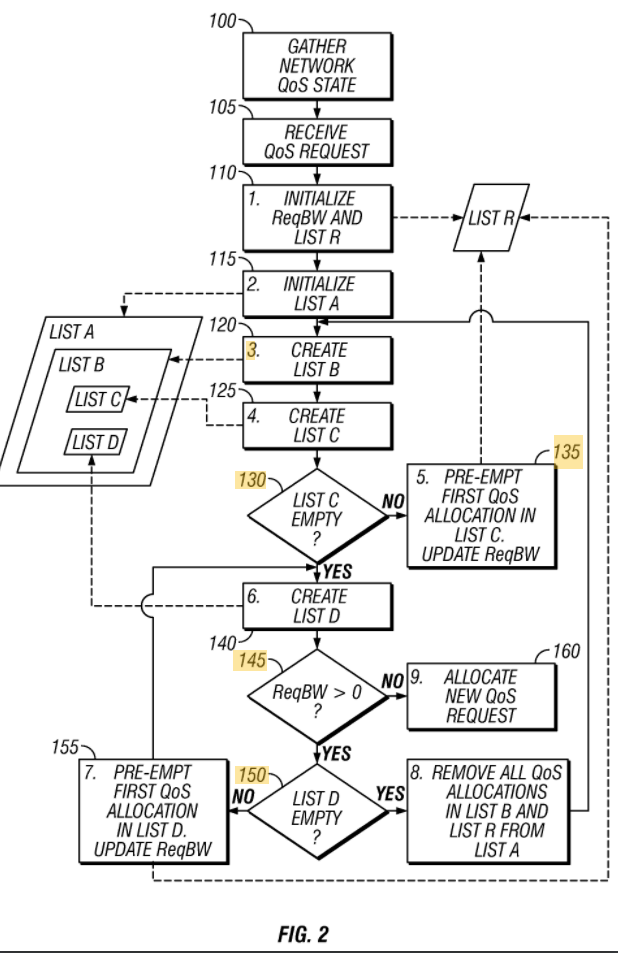
Attention is drawn to the following places, which may be of interest for search:
Traffic management, e.g. flow control or congestion control using specific QoS parameters for wireless networks, e.g. QoS class identifier [QCI] or guaranteed bit rate [GBR] |
This place covers:
The priority of the packet is indicated in the packet and the priority in the packet is modified.
This place covers:
The priority indicated within the packet is not modified; rather priority is applied to signalling traffic, ACKs, etc.
Attention is drawn to the following places, which may be of interest for search:
Scheduling and prioritising arrangements | |
Route determination for signalling traffic | |
Network-specific arrangements or communication protocols supporting networked applications for the provision of proxy services, e.g. intermediate processing or storage in the network for providing operational support to end devices by emulation, e.g. when they are unavailable, or by off-loading in the network | |
Adaptation of TCP data exchange control procedures |
This place covers:
Flow control actions that take into consideration the type of application.
Attention is drawn to the following places, which may be of interest for search:
Special provisions for routing multiclass traffic | |
Header parsing or analysis |
This place covers:
Techniques to identify different flow types and apply flow control accordingly. Analysis of the packet header 5-tuple or statistical analysis of packets can be used to infer the particular flow type, e.g. small constant sized packets are indicative of voice.
Flow types include: Aggregated flows, Elephant or macro flows comprised of flowlets, sub-flows, mice flows, suspect or suspicious flows, audio, video etc.
Attention is drawn to the following places, which may be of interest for search:
Enhancement of application control based on intercepted application data | |
Header parsing or analysis |
This place covers:
Conversion of IP TOS to QCI.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for connecting between networks having differing types of switching systems, e.g. gateways | |
Interdomain routing | |
Traffic management, e.g. flow control or congestion control | |
Traffic management, e.g. flow control or congestion control based on communication conditions | |
Negotiating wireless communication parameters | |
Negotiating SLA [Service Level Agreement]; Negotiating QoS [Quality of Service] |
This place covers:
Autonomous determination of congestion by the source endpoint in which there is no explicit feedback. Every source terminal or source node is able to determine the evolution of the congestion, e.g. by determining ACK packet loss or using techniques covered in other groups, such as H04L 47/50 or H04L 47/70.
This place covers:
The source endpoint is requested by the destination endpoint to apply rate correction actions. Explicit feedback can include feedback reports, e.g. RTCP, choke packets, e.g. a packet sent by a node to the source to inform it of congestion. Each router monitors its resources and the utilization at each of its output lines. Whenever the resource utilization exceeds the threshold value, which is set by the administrator, the router directly sends a choke packet to the source giving it a feedback to reduce the traffic. The intermediate nodes through which the packets have travelled are not warned about congestion.
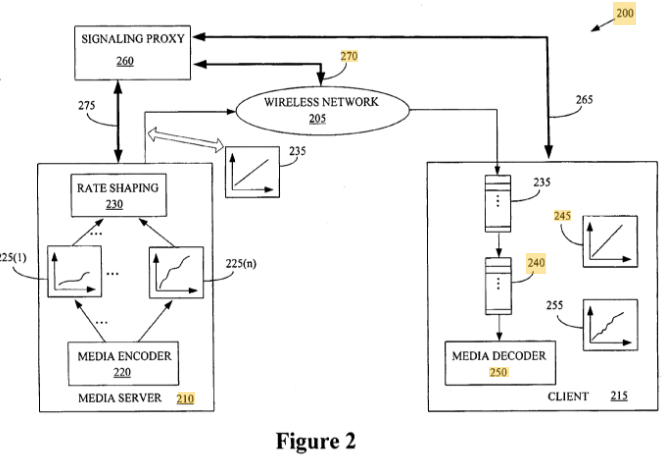
Attention is drawn to the following places, which may be of interest for search:
Monitoring of the downstream path of the transmission network, e.g. bandwidth available | |
Controlling the complexity of the video stream, e.g. by scaling the resolution or bitrate of the video stream based on the client capabilities | |
Traffic management, e.g. flow control or congestion control based on conditions of the access network or the infrastructure network | |
Traffic management, e.g. flow control or congestion control using buffer status reports |
This place covers:
Techniques for flow control in which source is adapted to modify its transmission rate after receiving feedbacks.
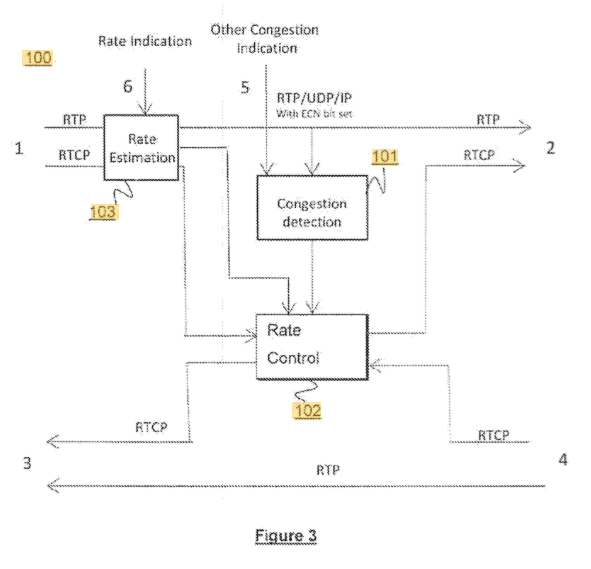
Attention is drawn to the following places, which may be of interest for search:
Reallocation of resources, renegotiation of resources, e.g. in-call triggered by the end-points | |
Backpressure | |
Flow control between communication endpoints |
This place covers:
Rate modification at intermediate network nodes on behalf of the source node.
This place covers:
Flow control action is based on interrupting the source of packet transmission until congestion is alleviated.
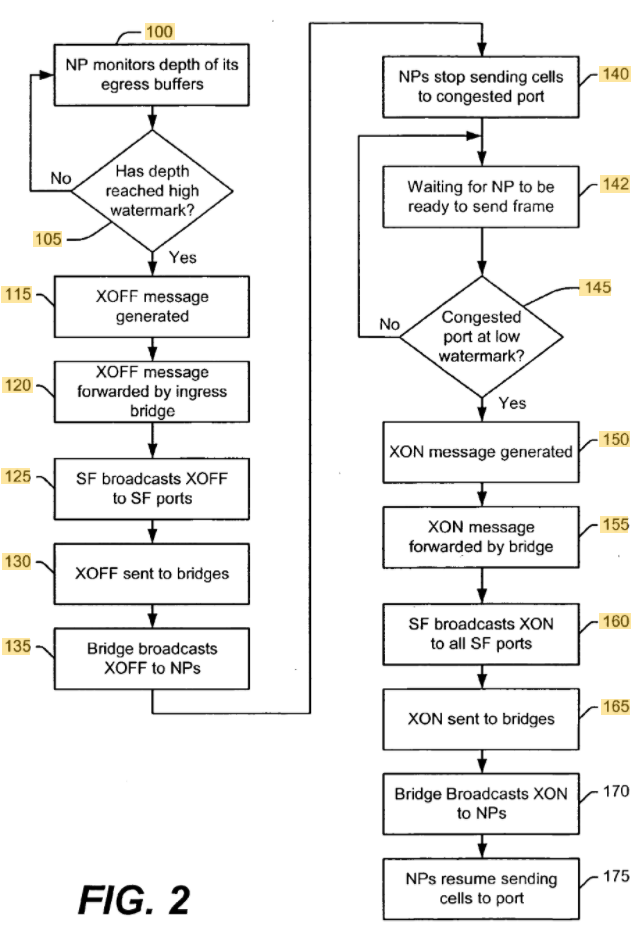
This place covers:
The destination node is adapted to send explicit feedback to the source node.
This place does not cover:
Network streaming of media packets with control of the source by the destination |
This place covers:
Recalculation of the congestion window to adapt to the network or destination endpoint situation.
This code is not meant for all documents that concerns windows based flow control.
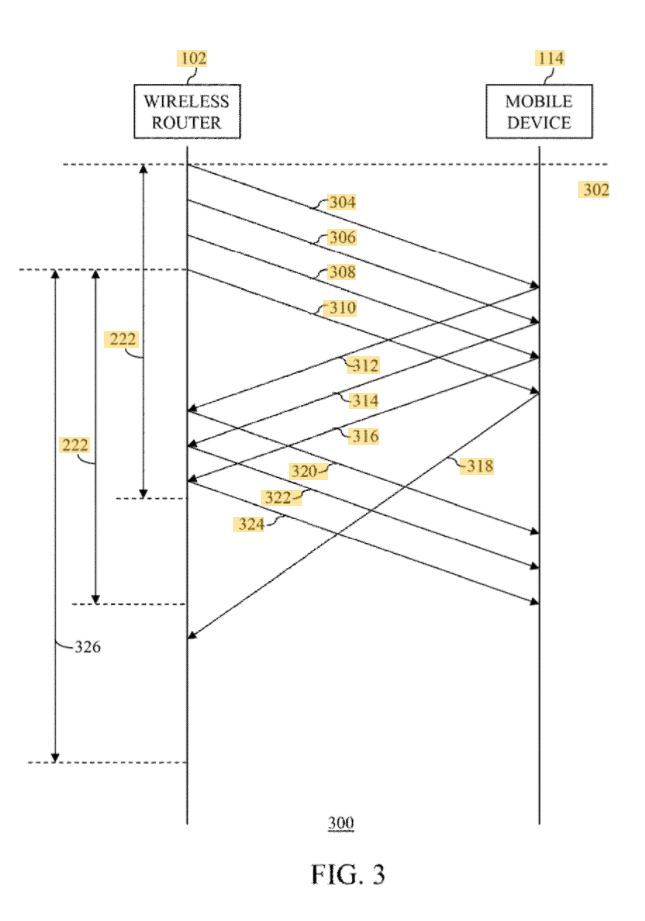
Attention is drawn to the following places, which may be of interest for search:
Sliding window management | |
Adaptation of TCP data exchange control procedures |
This place covers:
Flow control techniques taking into account time parameters, e.g. delays, latencies.
This place covers:
Flow control techniques taking into account processing delays.
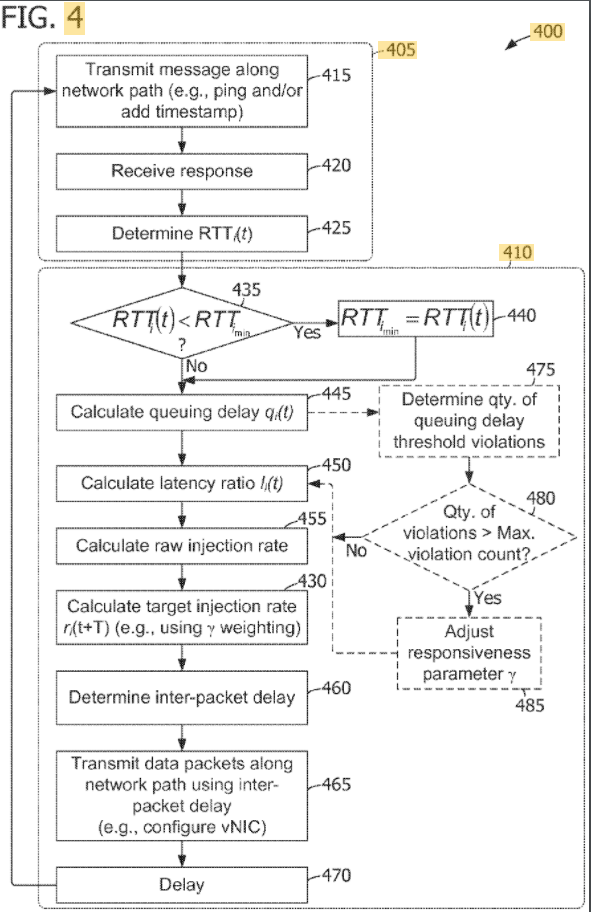
Attention is drawn to the following places, which may be of interest for search:
Network monitoring of the performance of a network communications and QoS parameters | |
Delay | |
Round trip delays |
This place covers:
Flow control techniques based on TTL.

Attention is drawn to the following places, which may be of interest for search:
Hop count for routing TTL | |
Self-organising networks, e.g. ad-hoc networks or sensor networks |
This place covers:
Using plural thresholds triggering different actions when they are reached, for example, hysteresis.
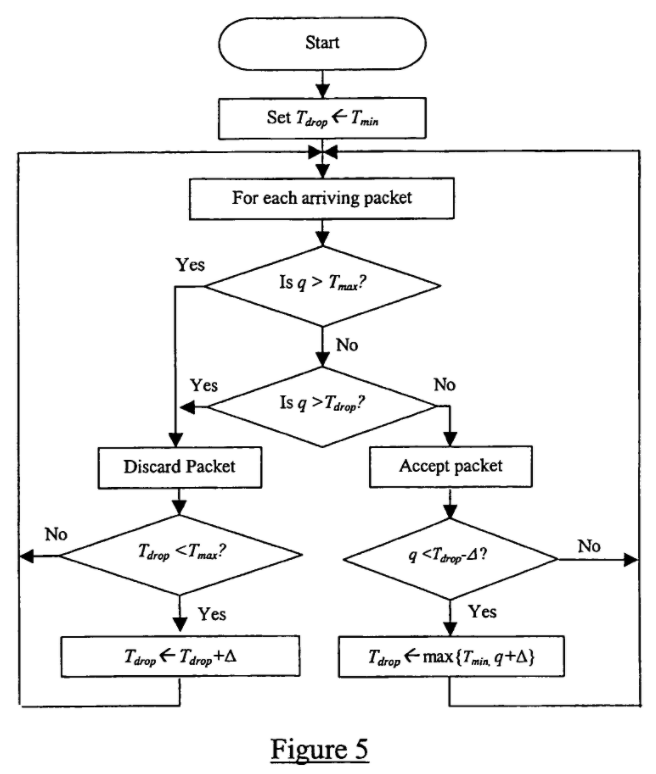
Attention is drawn to the following places, which may be of interest for search:
Network monitoring of the performance of a network communications and QoS parameters |
This place covers:
Flow control techniques taking into account buffer occupancy of nodes toward destination.
When giving this code, it is important to add the end-to-end or hop-by-hop codes if the feature is present.

Attention is drawn to the following places, which may be of interest for search:
Flow control or congestion control with hop by hop codes | |
Flow control or congestion control with end to end codes | |
Queueing arrangements many subclasses relating to buffers | |
Wireless buffer status reports |
This place covers:
Flow control techniques using tagging of packets.
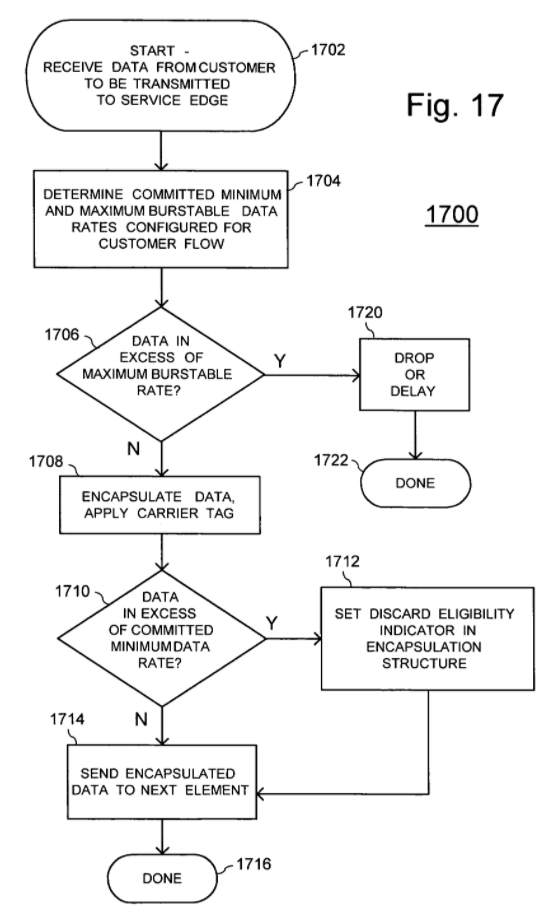
This place covers:
Using discard policies for preventing congestion, e.g. partially discarding corrupted, excessively delayed or non-critical packets.
Attention is drawn to the following places, which may be of interest for search:
One way delays | |
Flow control between communication endpoints |
This place covers:
Techniques for preventing congestion related to acknowledgment. Since acknowledgement are also the part of the load in network, the acknowledgment policy imposed by the receiver may also affect congestion. The receiver should send acknowledgement for N packets rather than sending acknowledgement for a single packet. The receiver should send an acknowledgment only if it has to send a packet or a timer expires.
Special actions on ACK traffic not related to delay or discard are classified in H04L 47/2466.
This place covers:
Flow control actions by using random early detection [RED], also known as random early discard or random early drop, e.g. queuing discipline for a network scheduler suited for congestion avoidance.
Various discard algorithms include: Weighted random early detection [WRED]; adaptive RED or active RED [ARED]; and Robust random early detection [RRED].
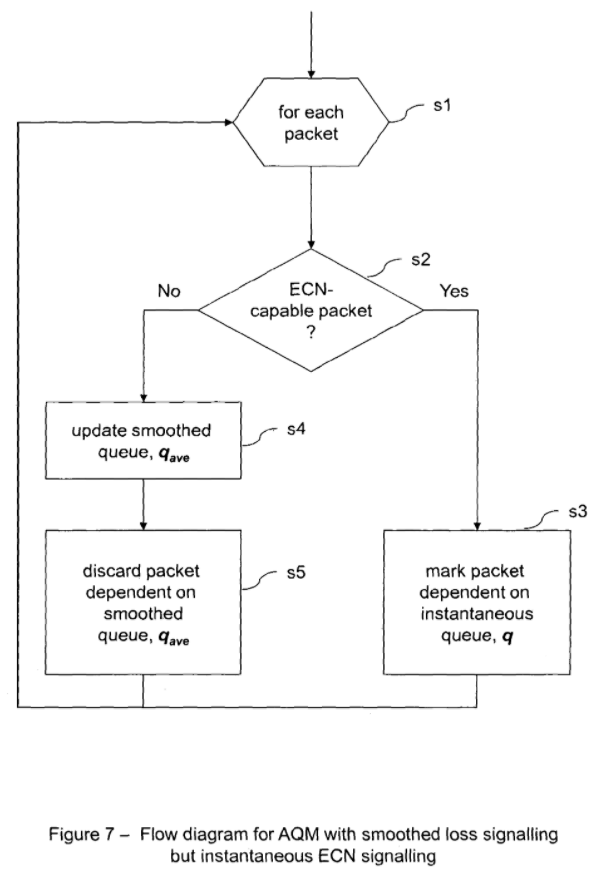
Attention is drawn to the following places, which may be of interest for search:
Network monitoring of the performance of a network communications and QoS parameters | |
Packet Switching Systems | |
Queueing in packet switching networks |
This place covers:
Communication of the congestion information to the destination terminal. This is a kind of feedback to the destination.
This place covers:
Flow control actions in combination with ensuring sequence integrity.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for connecting between networks having differing types of switching systems, e.g. gateways | |
Alternate routing | |
Queuing arrangements |
This place covers:
Flow control actions adapted to embedding specific flow control packets in data traffic packets.
This place covers:
Flow control actions in combination with packet size determination, sometimes performed at the beginning of the communication.
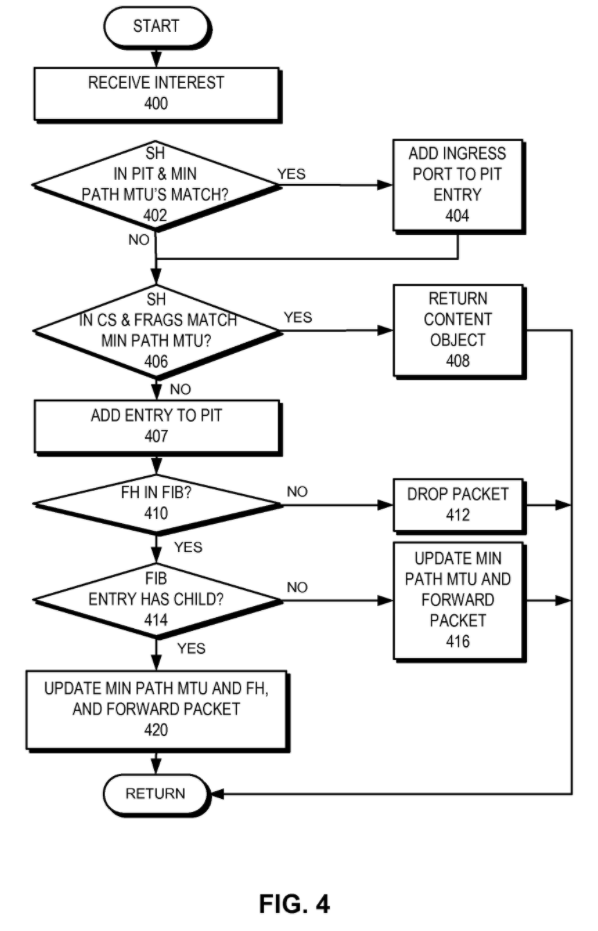
Attention is drawn to the following places, which may be of interest for search:
Routing based on monitoring results | |
IP fragmentation or TCP segmentation aspects |
This place covers:
Dynamic adaptation of the packet size during communication.
This place covers:
Modification of the starting window. This specific feature of TCP could appear in any other environment.
This code is used when the document describes an evolution from the standard procedure.
Attention is drawn to the following places, which may be of interest for search:
Adaptation of TCP data exchange control procedures |
This place covers:
Flow control actions in combination with adapting coding or compression rates, e.g. in video transmission with the purpose of adapting the multimedia signal to the receiving terminal.

Attention is drawn to the following places, which may be of interest for search:
Media handling, encoding, streaming or conversion | |
Content on demand | |
Controlling the feeding rate to the network, e.g. by controlling the video pump |
This place covers:
Flow control actions in combination with credits indicating availability or available buffer space of the receiver. Before data can be forwarded over a link, the sender needs to receive credits from the receiver.
At various times, the receiver sends credits to the sender indicating availability of buffer space for receiving data.
This place covers:
Using a performance enhancing proxy access node that divides the end-to-end TCP connection between the client and the server into a multi-overlay-hop path where each overlay hop is an independent TCP connection, such that the RTT of each overlay hop is lower than the direct RTT between A and B, e.g. TCP splitting.
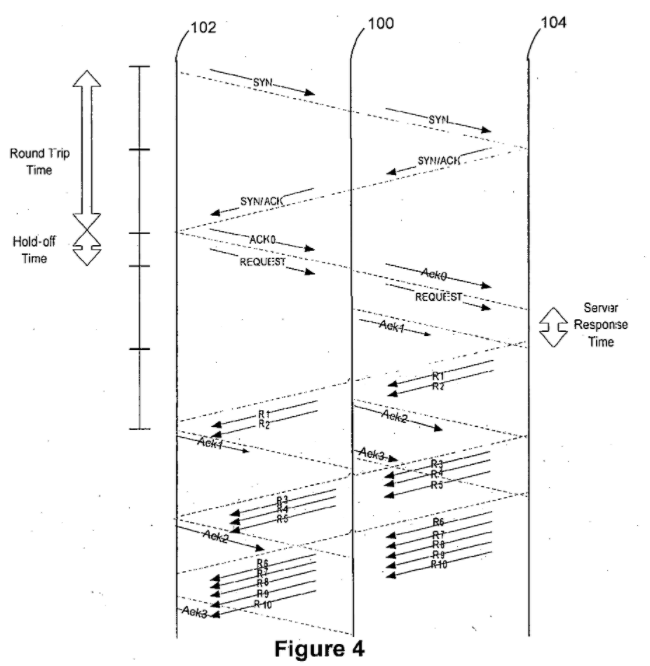
This place covers:
Flow control actions are applied to a bundle of links with the purpose of achieving an aggregate result. Corrective actions are applied to a set of links or flows corresponding to the same logical or physical entity.

Attention is drawn to the following places, which may be of interest for search:
Link aggregation, e.g. trunking |
This place covers:
Flow control actions in combination with assembling or disassembling of packets.
This place covers:
Flow control actions in combination with padding or de-padding of packets.
This place covers:
Packet scheduling when multiple queues are competing to transmit packets on a common link. A typical example of queue scheduling is illustrated below.

Attention is drawn to the following places, which may be of interest for search:
Packet Switching Systems | |
Input queuing | |
Output queuing | |
Shared queuing | |
Virtual queuing | |
Policing | |
Head of Line Blocking Avoidance | |
Queueing and buffering in packet switching networks | |
Plurality of buffers per packet | |
Common buffer combined with individual queues |
This place covers:
Scheduling policies that schedule the transmission of the data stored in the queue(s) taking into account the bandwidth consumed by the data. Such scheduling policies aim at optimizing the use of system bandwidth, by scheduling transmissions that neither underutilize nor saturate the transmission medium.

Attention is drawn to the following places, which may be of interest for search:
Bandwidth or capacity management, i.e. automatically increasing or decreasing capacities, e.g. bandwidth on demand |
This place covers:
Data in each queue are assured a portion of the total bandwidth as in the Weighted Fair Queueing scheduling method (see H04L 47/56) or the queue service slot (meaning the time that a queue is active each round) is fixed.
This place covers:
Schedulers which adapt the queue service slot (the time that a queue is active each round) or the bandwidth allocation in each service round based on different parameters. The queue service order can be fixed or variable and is classified under the group H04L 47/62.

This place covers:
H04L 47/524 is a special case of H04L 47/522, wherein the scheduler does not assign any bandwidth to a given queue.
This place covers:
In this case, there is a minimum guaranteed bandwidth per each queue and the residual bandwidth is redistributed among the queues.
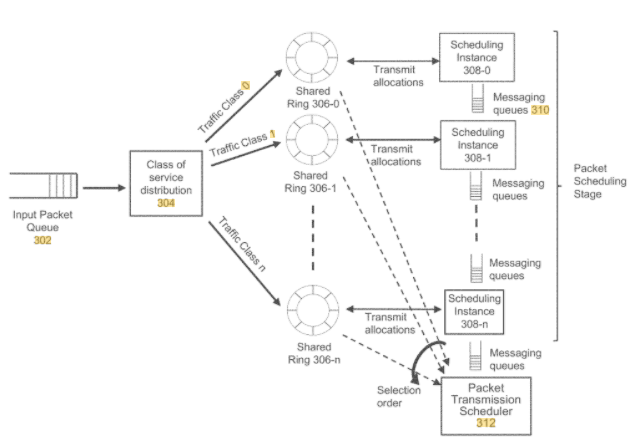
This place covers:
Scheduling in which each poll session is assigned a weight (quantum) of bits to be transmitted.
If the queue has less bits, a credit is assigned to said queue and quantum credit can be transmitted during the next poll (see also H04L 47/6265).
Token banks involve assigning tokens to the queues and storing said tokens in a finite capacity bank. The tokens assigned to a queue whose associated bank has reached its maximum capacity are assigned to another queue whose bank is below its capacity. Access to the resources is allowed if the queue has a predetermined number of tokens in its associated bank, otherwise it is denied.
This place covers:
The scheduler assigns a guarantee minimum bandwidth to each queue.
This place covers:
Scheduling taking into account the history of losses per flow or per class in order to prioritise the flows or classes accordingly. Changing the loss tolerance, value used for scheduling, of packets depending on whether or not another packet from the same stream has been scheduled for transmission before or after its deadline.
This place covers:
Scheduling taking into account delay constraints of packets, for example, real time packets. Under this code disciplines in which packets are scheduled according to a system potential (also referred to as virtual time) are also covered. The scheduler uses this global function to compute timestamps which specify when packets should be served. Packets are scheduled in increasing order of the corresponding timestamps. The specific function used as system potential determines the delay and fairness properties.
If different priorities are involved, then the corresponding group H04L 47/24 is also used. For example, groups H04L 47/245 and H04L 47/2416 also apply.
This place covers:
Scheduling in which packets are grouped in buffers according to the corresponding session rate and only one timestamp is maintained per rate.
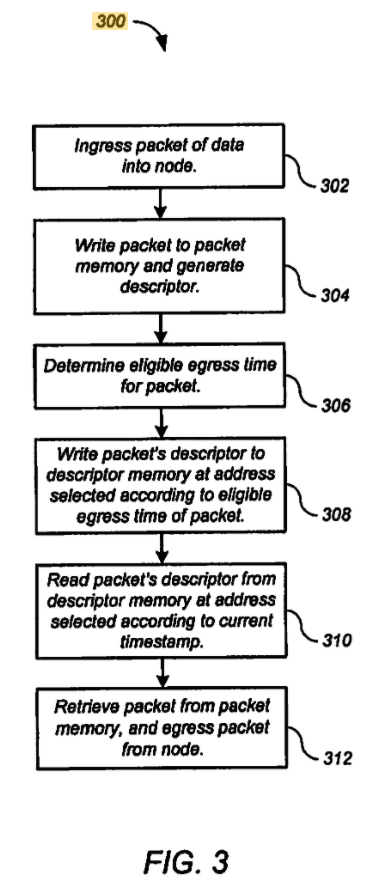
This place covers:
Scheduling in which each packet is assigned a timestamp for transmission, for example, earliest.
This place covers:
Excess bandwidth is used to try to equalize the delays of the connections.
This place covers:
Scheduling using calendar queues or timing rings.
A calendar queue is an ordered structure of bins representing possible values of timestamps in the system. The bins are ordered by increasing value of their timestamps. When the maximum difference between timestamps of backlogged sessions in the system is bounded, the calendar queue can become a circular queue where the bins can be reused as the time progresses. The bin associated with the minimum value must correspond with the value of the system potential at that time, and the total number of bins must be sufficient to cover the possible range of timestamps. Each bin is implemented as a list of pointers to individual connections. Every time a connection receives a new timestamp, it is linked to the corresponding bin.
The calendar queue can be automatically resized, i.e. the number of bins and the width of the bins (the number of possible timestamp values of a bin) can be changed depending on the distribution of backlogged connections in the bins. The granularity of the bins or slots in one calendar queue can be variable, for example, in the logarithmic calendar queue.
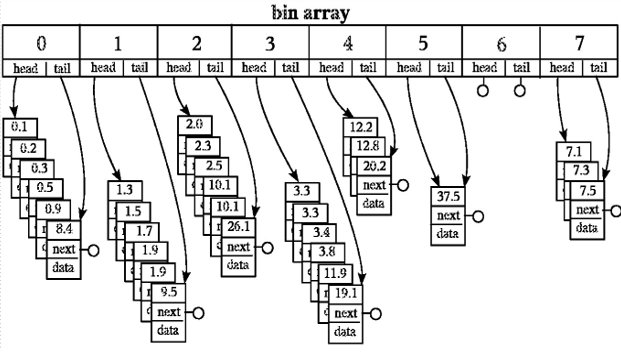

This place covers:
Changing the scheduling discipline upon an event such as congestion.
This place covers:
Hierarchical integration of schedulers.
A hierarchical scheduler can be represented by a tree where the root node corresponds to a scheduler which multiplexes the packets on the physical link, each intermediate node corresponds to a scheduler at that level of the hierarchy, and the leaf nodes correspond to the allocated sessions. Each leaf is connected to the root through a single path of intermediate nodes.
The classes for the specific schedulers should be also given. If different types of schedulers are used, the class H04L 47/58 should be given also.


This place covers:
Various general aspects of queue scheduling.
This place covers:
Scheduling techniques adapted to avoid Head of Line [HOL] Blocking, e.g. the first packet in a queue which is waiting for the corresponding output to be free prevents other packets from that queue to be transferred to the corresponding outputs which are free.
This place covers:
Scheduling techniques adapted to process each individual queue in a flow or connection.
This place covers:
Scheduling techniques adapted to consider an individual queue for each QoS class, rate or priority of traffic.
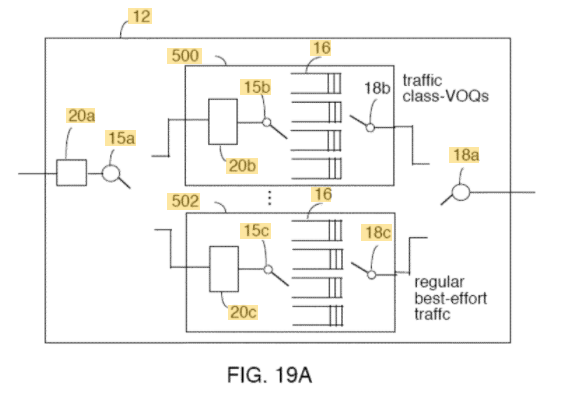
This place covers:
Scheduling techniques adapted to consider the service order of the queues. The service order can be fixed, as in Round Robin scheduling method, or variable.
This place covers:
Scheduling techniques in which the service order of the queues is variable.
Therefore, if in the first round queues 1, 2 and 3 are served in that order, in the second round queue 3 could be served as first queue followed by 1 and 2. To be used in conjunction with H04L 47/625.
This place covers:
Scheduling techniques adapted to change the ordering of packets in a queue, e.g. a buffer manager manages a sequence of pointers each referencing a separate cell of the buffer, the sequence of pointers being ordered to indicate the order in which the buffer manager has to write/read into/from the single cell.
This place covers:
Scheduling techniques in which the standard FIFO or LIFO procedure for writing/reading data in the queue is modified under certain conditions.
This place covers:
Scheduling techniques adapted to apply other criteria for service slot or service order than those covered by H04L 47/6205 - H04L 47/6245.
This place covers:
Scheduling techniques in which the load of the queue is constantly monitored and the next scheduled queue is the queue with the highest load. One or more predetermined thresholds can be used and priority can be set for choosing between queues which are in the same condition.
In this case, the classes H04L 47/29 and H04L 47/30 should also be considered. Otherwise, the bandwidth, for example, number of packets read from a queue can be changed based on load condition of a specific queue.
This place covers:
Scheduling techniques where the order in which the respective queues are visited is chosen as a function of the propagation conditions on the transmission channel associated to each queue.
The same can apply to the bandwidth dedicated to each queue per service slot.
This place covers:
Techniques in which the scheduling of the queue is changed according to the previous bandwidth allocation. A credit (counter) system per queue is introduced. The history credit count of each queue is increased when data transmission from the queue is blocked and decreased when arbitration has been won on the basis of the history credit count. In this way, the reading sequence of the queues is determined.
This place covers:
Scheduling techniques in which each flow is metered to determine whether its bitrate is below/over its guaranteed bitrate requirement, and based on the measurement, a scheduling weight is determined. The traffic queues are then scheduled according to the determined scheduling weights.
This place covers:
Scheduling techniques in which the order in which the respective queues are visited is chosen according to the queue priority, often in combination with H04L 47/6215.
Attention is drawn to the following places, which may be of interest for search:
Individual queue per QoS, rate or priority |
This place covers:
The scheduler takes into account the packet size.
This place covers:
Scheduling techniques in which low priority queues are prevented for being empty.
This place covers:
Scheduling techniques designed in order to achieve a fair sharing of resources among different users.
This place covers:
Scheduling techniques which further organise packets having same QoS/connection/flow/priority into multiple queues.
This is a further subdivision with respect to H04L 47/6215.
This place covers:
The interaction between an endpoint and the network for ensuring resource availability for a requesting user.
A requested or negotiated resource can take many forms, for example, bandwidth, slots, buffer capacity or other transmission resources. Typically following negotiation, a reservation phase is performed before the actual communication is established, for example, call setup. Other aspects covered in this class is renegotiation, for example, bandwidth reallocation either requested by an already active user or by the ingress node network to adapt the available resources to serve new calls with higher priority.
In particular, it should be noted that the following classes have been allocated for network slicing applications:
Architecture | |
Service chaining and classification |
Attention is drawn to the following places, which may be of interest for search:
Network dimensioning or reallocation of resources between areas of the network | |
Network fault recovery selecting new candidate element | |
Bandwidth management and trading | |
Routing | |
Alternate routing | |
Route fault recovery | |
Flow classification | |
Resource allocation architecture | |
Protocols for multimedia access such as IMS or SIP | |
For peer-to-peer [P2P] networking; Functionalities or architectural details of P2P networks | |
Wireless load balancing or load distribution | |
Wireless resource allocation | |
Wireless resource scheduling |
This place covers:
Admission control in which resources are reserved over the network in advance, usually at call setup time in order to assure a quality of service QoS. A traffic descriptor is provided so that the network can reserve enough bandwidth resource to handle the specified QoS.
This place covers:
Admission control ensuring that enough resources, e.g. buffer space, can be reserved at the receiver for the communication.
This place covers:
Admission control in which resources are reserved at the intermediate nodes, e.g. in the resource reservation protocol RSVP.
RSVP, described in RFC 2205, can be used by either hosts or routers to request or deliver specific levels of quality of service QoS for application data streams or flows. RSVP defines how applications place reservations and how they can relinquish the reserved resources once the need for them has ended. RSVP operation will generally result in resources being reserved in each node along a path.
This place covers:
Admission control in which the reservation is performed over a plurality of paths for the communication, for example for load balancing.
This place does not cover:
Reserving resources by balancing the load |
Attention is drawn to the following places, which may be of interest for search:
Wireless load balancing |
This place covers:
Admission control in which the reservation is performed for backup paths which are used in case of failure of the main path.
This place covers:
Admission control reacting to the situations in which there are not enough resources for a connection, including a new connection or an existing connection, e.g. due to a failure.
Typical reactions are rejecting the connection or storing the request until resources become available. For existing connections and in case the reaction is a flow control or congestion control action as, for example, packet dropping, flow control subgroups under H04L 47/10 should be considered. An example is policing actions where H04L 47/20 would apply. This group could be used in combination with the group H04L 47/76 if the reaction is the reallocation of resources.
This place covers:
Admission control in which an incoming request is held in a queue until the requested resources become available.
This place covers:
Admission control that includes reactions at the end nodes.
This place covers:
Admission control that includes reactions in the network, e.g. when a new connection is accepted by diminishing the bandwidth reserved to other connections even if there is no sufficient bandwidth available.
This place covers:
Admission control in which specific actions are performed as a reaction to a failure.
This place covers:
Admission control in which, if the user requests cannot be satisfied due to lack of resources, the user resubmits (or is offered) an alternative request or is offered an alternative to the request, e.g. a connection at a bandwidth lower than the originally requested one.
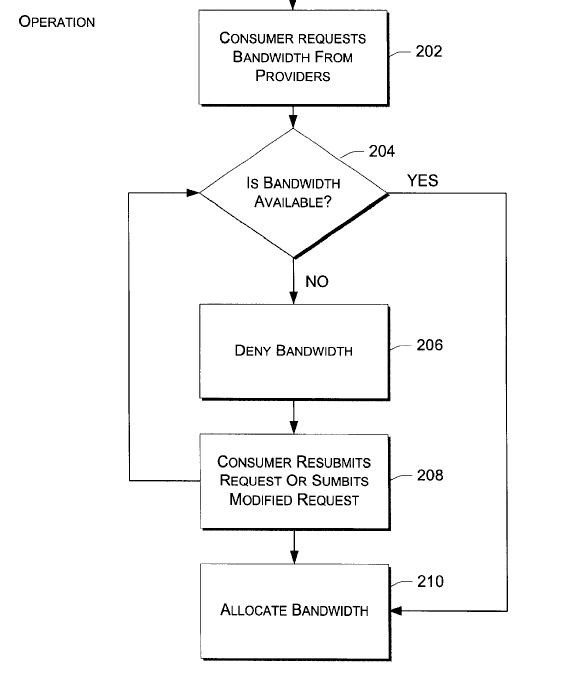
This place covers:
Admission control in which resources of existing connections are reallocated, e.g. to accommodate a new connection being triggered by an end-point, to upgrade a connection or to improve efficiency according to monitored patterns by the network.
For existing connections and in case the action is a flow control or congestion control/avoidance action, e.g. modification of packet priorities while in transit, flow control subgroups under H04L 47/10 should be considered. An example is policing actions where H04L 47/20 would apply.
This place covers:
Admission control in which specific actions are initiated by the network.

This place covers:
Admission control in which specific actions are initiated by the end nodes.

This place covers:
Admission control in which specific actions are performed after changing of the attachment point such as an access node.
This group could be used in combination with H04L 47/783 (Distributed allocation of resources) when, for example, as a result of the hand-off there is a change of network domain.
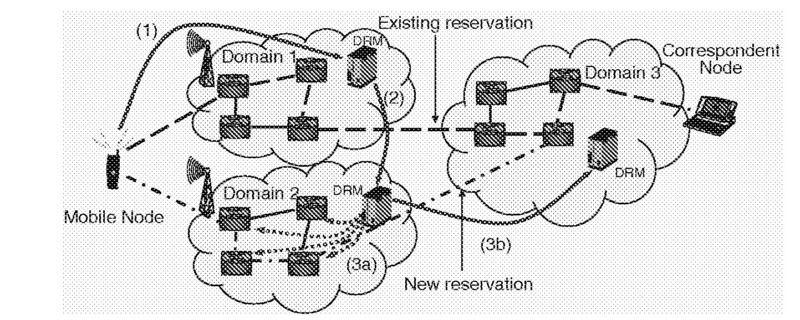
Attention is drawn to the following places, which may be of interest for search:
Distributed allocation of resources, e.g. bandwidth brokers |
This place covers:
Admission control relevant to specific network architectures.
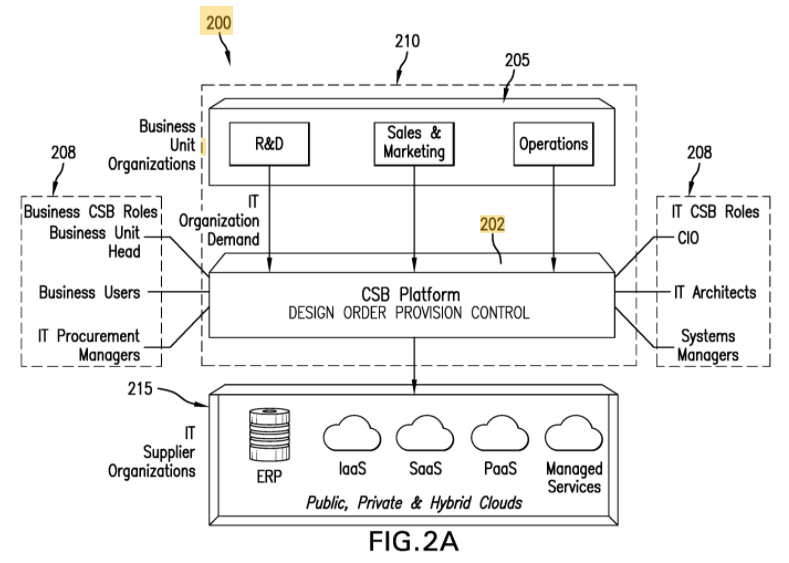
This place covers:
Admission control in which resources are allocated by a central unit.
This place covers:
Hierarchical allocation of resource, e.g., involving entities which are related in a hierarchical configuration.
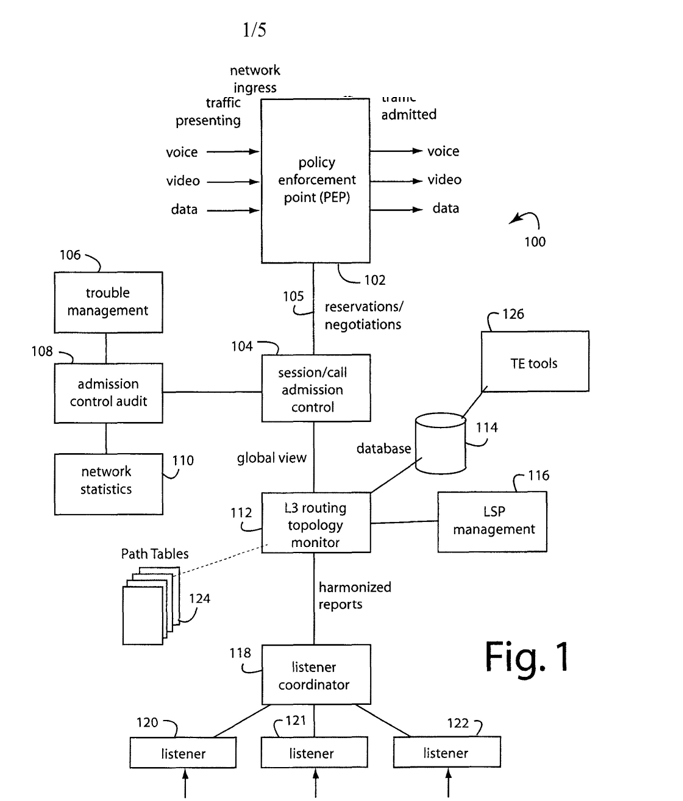
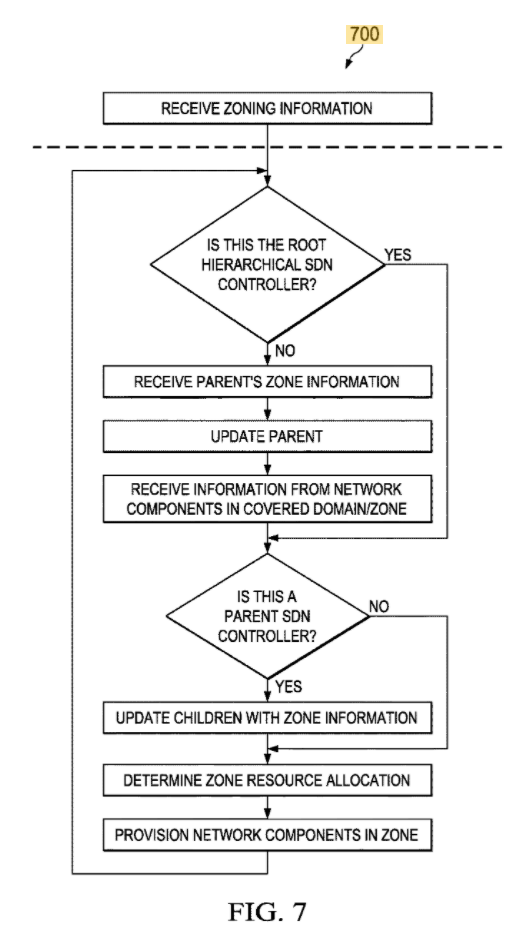
This place covers:
Admission control in which the allocation of resources is performed in a distributed way, e.g. by employing Bandwidth Brokers as agents that manage a domain and adapted to communicate with its adjacent peers, allowing end-to-end services to be constructed as a result of bilateral agreements.
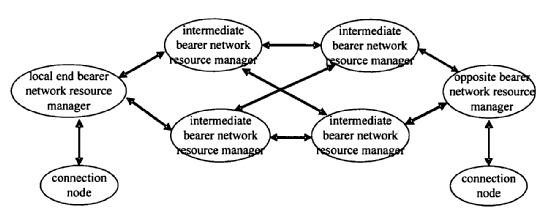
This place covers:
Admission control in which the allocation of resources is performed within multiple network domains allowing end-to-end services to be constructed as a result of multilateral agreements.
This place covers:
Admission control in which the allocation of resources comprises inter-domains correspondence of reservations.
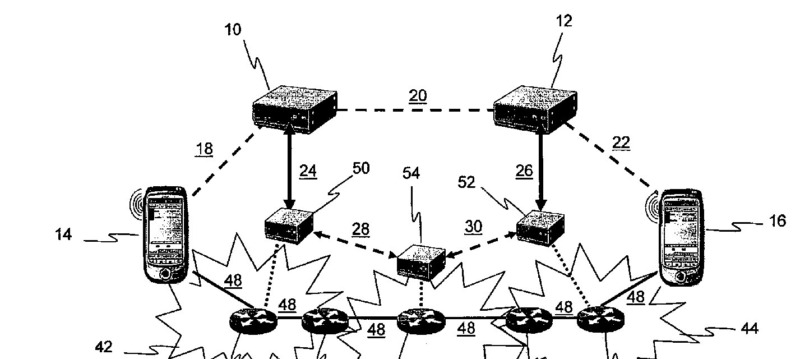
This place covers:
Multi-domain admission control in which the allocation of resources comprises bandwidth trade among domains.
This place covers:
The allocation of resources is done in an autonomous way by, e.g. an access point. The access point is responsible for the admission of new requests based on the current allocation of resources.
This place covers:
Reservation actions depending on the type of traffic, e.g. real time vs. non-real time traffic, quality of service, priority, application dependent etc. or user, e.g. service level agreement, SLA.
This place covers:
Resource allocation is done with preference to real time traffic in case of mixed real time and non-real time traffic, due to the sensitivity of the real time traffic to delay.
This place covers:
Allocation of resources or requesting of an access based on the application that is going to use the resources/access.
The bandwidth allocation problem becomes more difficult in multiservice networks that have a large variety of different applications, each one with different requirements in terms of bandwidth, duration or delay and information loss.

This place covers:
Allocation/reservation of resources based on specific QoS parameters requested by the connection.
This place covers:
Allocation/reservation for broadcast and multicast traffic.
Attention is drawn to the following places, which may be of interest for search:
Multicast in flow control | |
Multicast or broadcast media | |
Resource management for broadcast services |
This place covers:
Allocation/reservation of resources is based on the type of user profile which is specified by the service level agreement SLA.
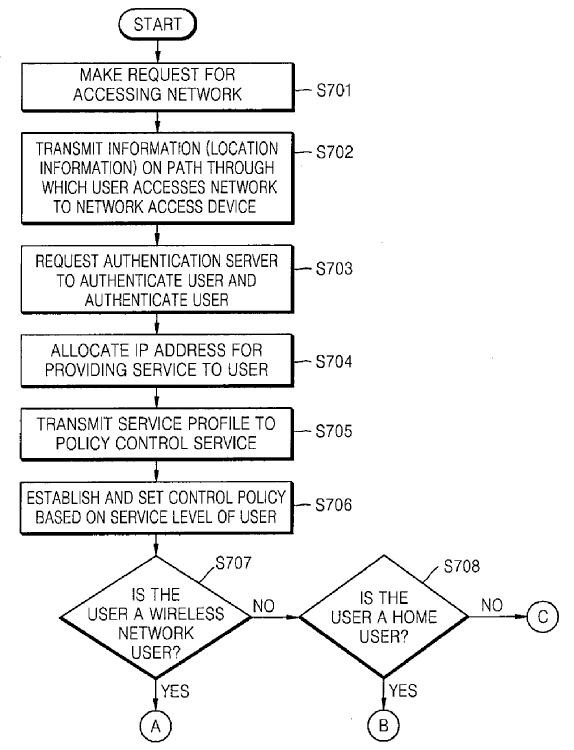
This place covers:
Prioritizing or aggregating resource reservation/allocation based on availability, prediction or applicability.
This place covers:
Prioritisation of the resource allocation/reservation requests.
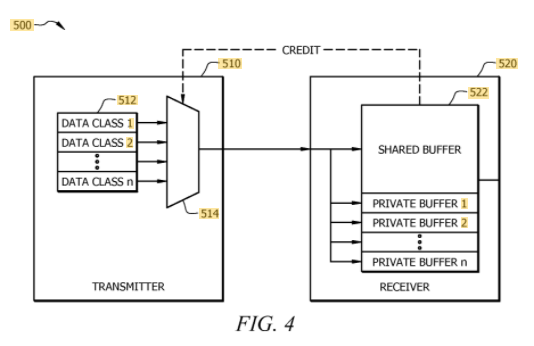
This place covers:
Prioritisation of the resource allocation/reservation requests.
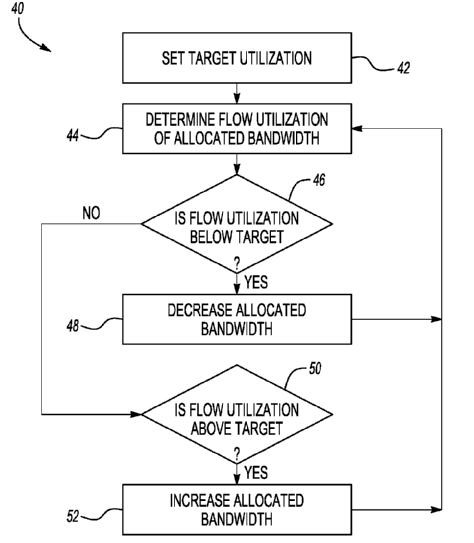
This place covers:
Resource allocation/reservation wherein a portable or mobile terminal is involved.
This place covers:
Resource allocation/reservation in networks using packet encapsulation techniques, e.g. MPLS or mobile IP networks.
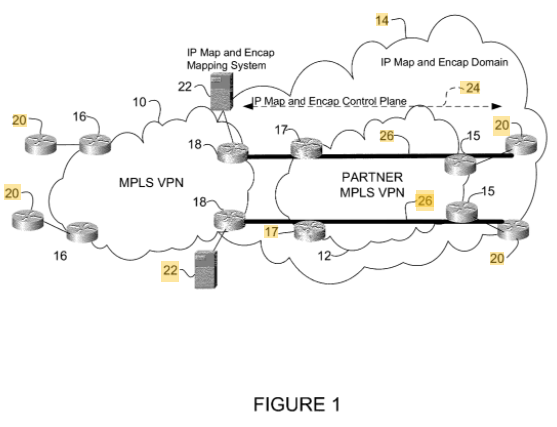
This place covers:
Resource allocation/reservation taking into account time parameters or performed in different periods of time, e.g. sending first data with high priority and at a later point in time data with less priority.
The class can also be used for resource reservation policies that vary with the time.
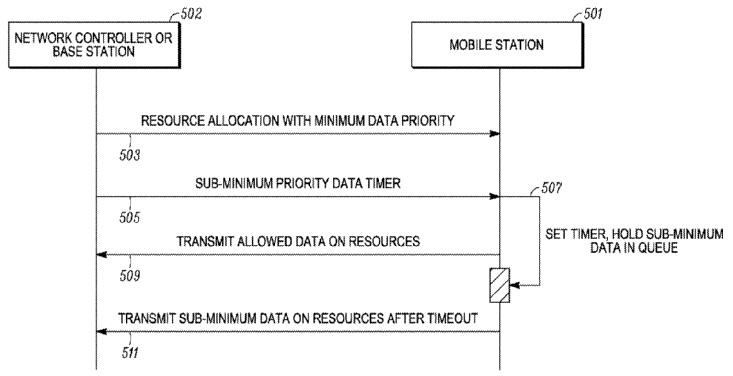
This place covers:
Admission control in which the resource reservations are aggregated and sent to the node that requested the reservation.
This place covers:
Admission control in which the allocation of resources is performed in relation to a group of connections.

This place covers:
Admission control in which the allocation of resources is based on a particular topology or in relation to the change of topology of the network.
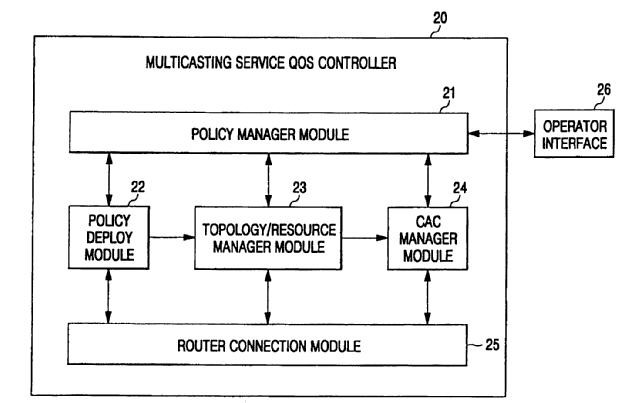
This place covers:
Admission control in which the allocation of resources is based on predicted usage of said resources.
This place covers:
Systems and elements for switching of packets or cells, e.g. virtual switches or asynchronous transfer mode [ATM].
Attention is drawn to the following places, which may be of interest for search:
Selecting arrangements for multiplex systems |
This place covers:
Construction of the interconnect, or switching fabric or switching network, which connects every input port of the switch to every output port of the switch.
This place covers:
Interconnection of the basic switching modules that are part of a switch fabric.
A switch fabric is built of basic switching building blocks, i.e. the switching modules.
A switching module is the basic unit of the switch fabric. It can be implemented in a single integrated circuit element or on a printed circuit board. The routing information of the incoming packet is analysed at the input port, and the cell is then directed to the correct output port (outlet). In general, the switching element consists of an interconnection network, an IC (input controller) for each incoming line and an OC (output controller) for each outgoing line. The OC transports cells which have been received from the interconnection network toward the destination. The IC and OC are coupled by the interconnection network.
This place covers:
Details of specific features of packet switches for support of certain services, e.g. application services or a certain quality of service (QoS).
This place covers:
Details of the peripherals units of a switch comprising functionalities taking place either between the end of the input link and the switching fabric, or between the switching fabric and the output link.
This place covers:
Packet switches, routers or bridges which are designed to support specific applications or protocols, e.g. LAN switches, Fibre Channel switches.
This place covers:
Details of the constructional aspects of a packet switch.
The constructional details may not only be mechanical but may also relate to clock distribution, connectors, backplane distribution, etc.
This place covers:
Details concerning the upgrading of a switch, expanding a switch, e.g. a switch which is already in operation needs to be upgraded in terms of adding more ports to the switch or other upgrades concerning the switching fabric, the processing capacity of the controller or the number of line cards.
This place covers:
Details concerning all functions within a packet switch that are used to detect an overload situation and/or to protect the packet switch from the negative consequence of degraded throughput due to overload, including functions used to prevent failure of the switch or errors in the switch, such as loss of packets, due to overload.
The overload may be either at the packet or at the call control level. It may be detected in any part of the switch, peripherals, switching fabric, control.
The most common overload situation of packet switches is the burst arrival of more packets than can be handled by the switch. This results in packets being discarded or a malfunction of the entire switch. However, other reasons for overload do exist, for instance the control plane for connection oriented packet switches (e.g. ATM switches) may receive more signalling messages than can be processed.
Attention is drawn to the following places, which may be of interest for search:
Diverting traffic away from congested spots | |
Load balancing | |
Congestion Prediction | |
Reactions to storage capacity overflow | |
Replacing packets in a storage arrangement, e.g. pushout |
This place covers:
Details concerning prevention, detection and corrections of errors such as packet loss, switch failure, internal routing errors.
This place covers:
Switches specially adapted for software-defined operations in cooperation with SDN controllers in network structures that centralise network intelligence in one network component, e.g. SDN controller, and separate the forwarding process or data plane from the routing process or control plane.
Attention is drawn to the following places, which may be of interest for search:
Updating the topology between route computation elements, e.g. between OpenFlow controllers | |
Splitting route computation layer and forwarding layer, e.g. routing according to path computational element [PCE] or based on OpenFlow functionality | |
Interaction between route computation entities and forwarding entities, e.g. for route determination or for flow table update |
This place covers:
Details concerning aligning the physical properties of the switch with the control software of that particular switch as an activity that is either executed by the switch itself (e.g. by the control software) or via a connected operation and maintenance system.
This implies that prior to the (re-)configuration of the switch, a change in the hardware structure of the switch has taken place. Such a change may comprise an addition or removal of hardware, for instance a line card or a switch card, the change of status of availability of some hardware, for instance due to a failure. Another reason can, for instance, be the need to expand the switch or to increase its functionality.
This place covers:
Details concerning switching functionalities implemented as software programs that allows communications between virtual machines.
A virtual switch does more than just forward data packets. It can intelligently direct communication on the network by inspecting packets before passing them on. Some vendors embed virtual switches right into their virtualisation software, but a virtual switch can also be included in a server's hardware as part of its firmware.
Apart from the pure software implemented virtual switch, there are hybrid virtual switches comprising a real physical switching fabric interconnecting physical machines with a network. The control software of the switch implements virtual ports, i.e. emulates multiple logical ports on a physical port. This can have advantages if connections have to be moved from one physical port to another physical port and it also seems to have advantages in load balancing within the switch.
Another type of virtualisation is the provision of a logical switch or cluster switch that emulates a single switch on a plurality of physical switches.
This place covers:
Queueing arrangements in packet switching networks, buffer allocation to packets, e.g. memory location (internal, external), buffer pools, memory partition to adapt to packet size, linked list of buffers.
NIC-mainframe interface
Intermediate buffering before the packet is transferred to the packet memory in the mainframe. Intermediate FIFO, circular list of descriptors, early interrupt after a number of bits has arrived, etc. In relation to those functions you will find also features like detection of too large, too short packets or CRC control.
When packets reach a store-and-forward unit they have to be temporarily buffered until the forwarding decision is made by the routing engine.
This place covers:
User-to-user messaging in packet-switching networks, transmitted according to store-and-forward or real-time protocols, e.g. e-mail, or real-time protocols, e.g. instant messaging. A message switching system is a system that switches messages on the application layer. The messages have one or more individually identified recipients.
The message can be audio or video.
Attention is drawn to the following places, which may be of interest for search:
Message passing systems or structure for program control, e.g. messaging middleware | |
Computer aided management of electronic mailing [e-mailing] | |
User interfaces specially adapted for cordless or mobile telephones with interactive means for internal management of messages | |
Voice mail systems for recording message comprising any combination of audio and non-audio components | |
Client devices for e-mailing in television systems | |
Messaging; Mailboxes; Announcements | |
Messaging devices for wireless communication networks, e.g. message centre |
In this place, the following terms or expressions are used with the meaning indicated:
social network | websites and applications for the informal communication and sharing of information with other users |
store and forward | a telecommunications technique in which information is sent to an intermediate station where it is kept and sent at a later time to the final destination or to another intermediate station |
instant messaging [IM] | real-time transmission and exchange of short messages between two parties |
users | chatbots, user readable or user-oriented messaging |
In patent documents, the word/expression in the first column is often used instead of the word/expression in the second column, which is used in the classification scheme of this place:
Message switching system | A system that switches messages on the application layer in the user plane. The messages have one or more individually identified recipients, although a user may have defined them to be part of a distribution list. |
This place covers:
Any system or technique for creating and sending automatic replies to messages, e.g. smart speaker interaction, Alexa or Hey Google.
This place covers:
Instant messaging is data exchange in real-time between at least two end users connected to a packet-switching network where the users can be aware of the identity and the presence of the other party or parties.
Attention is drawn to the following places, which may be of interest for search:
Messaging using presence information | |
Messaging combined to or interacting with other services or applications | |
Network arrangements or protocols for real-time communications | |
Presence management and presence servers as such |
This place covers:
Instant Messaging in which user presence information is used for the message exchange.
Attention is drawn to the following places, which may be of interest for search:
Use or manipulation of presence information in messaging presence management |
This place covers:
Instant Messaging combined or interacting with other applications, which may be real-time or not.
This place covers:
Any manipulation of the message while in transit between the sender and the recipient for optimizing its delivery and display.
Attention is drawn to the following places, which may be of interest for search:
Protocols specially adapted for terminals or networks with limited capabilities | |
Networked arrangements for intermediate processing of conversion or adaptation of application content or format |
This place covers:
Content adaptation for body or attachments. This can include the deletion of unwanted parts of the message, e.g. parental guidance, or multimedia data, the augmentation of the message or the replacement of data with links or summaries.
This place covers:
Format adaptation, conversion or compression of a part of message of the entire message, e.g. changing a picture from BITMAP to JPEG format or text-to-speech conversion, changing message protocol. Although this may lead to loss of information due to different compression techniques or content that cannot be converted, the content is intentionally adapted, but any loss of information (due to the examples listed) is not intentional, and can be attributed to the adaptation (translation).
Attention is drawn to the following places, which may be of interest for search:
Speech synthesis; Text to speech systems |
This place covers:
Exchange of messages including content other than plaintext.
This place covers:
The attachment to a message that impacts transmission and/or handling of the message in the network.
This place covers:
Messages including multimedia data which impact transmission and/or handling of message in the network.
Attention is drawn to the following places, which may be of interest for search:
Network arrangements or protocols for real-time communication | |
Voice messaging in telephonic communication using automatic or semi-automatic exchanges with non-audio components |
This place covers:
Messages including links, URLs, executable codes, etc. to be executed either at an intermediate node or at the recipient.
Attention is drawn to the following places, which may be of interest for search:
Networked applications for remote control or remote monitoring of the application | |
Networked applications involving the movement of software or configuration parameters | |
Computer aided management of electronic mail |
This place covers:
Message monitoring and processing over the network.
This place covers:
Blocking or partial filtering of messages based on predetermined criteria, e.g. based on the age of the message(s).
Attention is drawn to the following places, which may be of interest for search:
Message adaptation to remove unwanted content | |
Firewalls and in particular filtering policies | |
Malware detection or handling | |
Access security using filters or firewalls in wireless networks |
This place covers:
Redirection of messages by an intermediate network node, e.g. a server, either for delivery optimisation especially based on network conditions and user profile.
Attention is drawn to the following places, which may be of interest for search:
For profiles in general |
This place covers:
- Grouping messages in conversations
- Forking conversations
- Keeping track of conversations
This place covers:
Transmission or handling of the message in the network based on the location of the sender's and/or recipient's terminal.
Attention is drawn to the following places, which may be of interest for search:
Protocols for adapting network applications to user terminal location | |
Services specially adapted for wireless communication networks making use of the location of users or terminals |
This place covers:
Alternative means for notifying a user that a message has been received.
Examples:
- Notification that a message has been received by the server;
- Notification of pre-defined events;
- Notification on a wearable device.
Alternative means includes an out-of-band communication channel, an audible alert, a visual alert or a vibration alert.
Attention is drawn to the following places, which may be of interest for search:
Push-based network devices, pushed-based messaging | |
Execution arrangements for user interfaces | |
Computer aided management of electronic mail | |
User interfaces specially adapted for cordless or mobile telephones |
This place covers:
Scheduling (both delaying or prioritising) message transmission depending of determined priority levels to guarantee a better user service.
Attention is drawn to the following places, which may be of interest for search:
Networked applications for intermediate processing whereby quality of service or priority requirements are taken into account |
This place covers:
Informing the sender of a message about the correct reception of the message by the recipient, or on the missed or partial reception of the message.
Attention is drawn to the following places, which may be of interest for search:
Generation of monitoring or testing reports |
This place covers:
Detecting and reporting the progress of messages along the network, i.e. on the nodes located between the sender and the recipient excluding those two ends.
This place covers:
Message storage, synchronisation, categorisation and retrieval, e.g. mailboxes.
Attention is drawn to the following places, which may be of interest for search:
Computer aided management of electronic mail |
This place covers:
Hiding, modifying, retrieving, converting addresses of messages.
Attention is drawn to the following places, which may be of interest for search:
Arrangements and protocols for addressing and naming |
This place covers:
Messages exchanged over one or more social networks.
Attention is drawn to the following places, which may be of interest for search:
Business processes related to social networking or social networking services |
This place covers:
Messages exchanged and accessed by the users through different platforms, protocols, applications.
Attention is drawn to the following places, which may be of interest for search:
Instant messages format conversion |
This place covers:
Transmission of messages using wireless communication services, e.g. SMS or MMS.
The messages are not modified. The group concerns solving problems typical for wireless networks, e.g. transmission slot allocation, issues with base station or new 5G challenges.
Attention is drawn to the following places, which may be of interest for search:
Services specially adapted for wireless communication networks Messaging; Mailboxes; | |
Short messaging services | |
Messaging devices, e.g. message centre |
This place covers:
The following aspects of addressing and naming in data networks:
- Conversion and mapping of addresses, which includes mapping between different types of addresses, e.g. ARP or mapping between telephone numbers and IP addresses and mapping between the same type of addresses, e.g. NAT
- Directories and name-to-address resolution, e.g. DNS, LDAP, X.500, address books
- Allocation of addresses, e.g. DHCP
- Logical names, in particular aspects relating to the registration, conversion and structure of e.g. domain names, e-mail addresses or SIP-URIs
- Use of addresses for implementing special network functionalities.
Attention is drawn to the following places, which may be of interest for search:
Network security protocols | |
Data switching networks; Arrangements for providing special services to substations for broadcast or conference | |
Data switching networks characterised by a path configuration; Home automation networks | |
Exchanging configuration information on appliance services in a home automation network | |
Data switching networks configured as bus networks | |
High-speed IEEE 1394 serial bus | |
Data switching networks characterised by a path configuration; Interconnection of networks using encapsulation techniques, e.g. tunnelling | |
Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks | |
Arrangements for maintenance or administration or management of packet switching networks using standardised network management protocols | |
Arrangements for maintenance or administration or management of packet switching networks; Configuration management of network or network elements | |
Routing or path finding of packets in data switching networks | |
User-to-user messaging in packet-switching networks, transmitted according to store-and-forward or real-time protocols, e.g. e-mail | |
Network architectures or network communication protocols for network security for separating internal from external traffic, e.g. firewalls | |
Network architectures or network communication protocols for network security for separating internal from external traffic; Firewall traversal, e.g. tunnelling or creating pinholes | |
Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks | |
Network architectures or network communication protocols for network security for supporting authentication of entities communicating through a packet data network | |
Network arrangements, protocols or services for supporting real-time applications in data packet communications | |
Network arrangements or protocols for real-time communications; Signalling, control or architecture; Session control; Registration | |
Network arrangements or protocols for supporting network services or applications | |
Network-specific arrangements or communication protocols supporting networked applications in which an application is distributed across nodes in the network for accessing one among a plurality of replicated servers, e.g. load balancing | |
Network-specific arrangements or communication protocols supporting networked applications adapted for proprietary or special purpose networking environments | |
Network-specific arrangements or communication protocols supporting networked applications involving the movement of software and/or configuration parameters | |
Network-specific arrangements or communication protocols supporting networked applications; Service discovery or service management | |
Network-specific arrangements or communication protocols supporting networked applications; Presence management | |
Network-specific arrangements or communication protocols supporting networked applications for the provision of proxy services, e.g. intermediate processing or storage in the network | |
Protocols for interworking or protocol conversion | |
Accessing, addressing or allocating within memory systems or architectures | |
Bus transfer protocol, e.g. handshake; Synchronisation | |
Information retrieval using distributed data base systems | |
Retrieval of information from the web using information identifiers, e.g. uniform resource locators [URL] | |
Administration, e.g. office automation or reservations | |
Commerce, e.g. shopping or e-commerce | |
Telephone directories in user terminals | |
Telephone user terminals with static electronic memories for the storage of multiple subscriber numbers | |
Arrangements for providing interactive information services to subscribers, e.g. directory enquiries | |
Directory assistance systems | |
Arrangements for interconnection between switching centres | |
Details of addressing, directories or routing tables of networks other than PSTN/ISDN providing telephone service, e.g. Voice over Internet Protocol | |
Details of addressing, directories or routing tables for working between exchanges having different types of switching equipment, where the types of switching equipment comprises PSTN/ISDN equipment and switching equipment of networks other than PSTN/ISDN | |
Processing of mobility data, Registration at HLR or HSS | |
Network data management; Mobility data transfer | |
Network addressing or numbering for mobility support in wireless communication networks | |
Registration; Multiple registrations, e.g. multihoming | |
Network layer protocols in wireless communication networks, e.g. mobile IP | |
Network topologies; Self-organizing networks, e.g. ad-hoc networks or sensor networks | |
Devices specially adapted for wireless communication networks | |
Devices specially adapted for wireless communication networks adapted for operation in multiple networks |
- Address resolution is classified in group H04L 61/10, whereas name-to-address-resolution is classified in group H04L 61/50.
- ENUM is based on DNS and should therefore be classified under Directories in H04L 61/4557 and not in H04L 61/106.
- The Address Allocation subgroup H04L 61/5084 covers "portability" aspects not covered in H04W 8/26 or H04W 80/04, e.g. nomadic users in a hotel.
- IPv4 and IPv6 addresses are considered to be of the same type. Therefore, a mapping between these address types should be classified in H04L 61/251 and not in H04L 61/10.
- The Details subgroups (H04L 2101/00) should be used as an additional classification in H04L 61/00, i.e. if other H04L 61/00 subgroups in the range H04L 61/10 - H04L 61/35 have already been assigned.
In patent documents, the following abbreviations are often used:
ARP | Address resolution protocol |
DAD | Duplicate address detection |
DHCP | Dynamic host configuration protocol |
DNS | Domain name system |
EPP | Extensible provisioning protocol |
GRUU | Globally routable User Agent URI |
IP | Internet protocol |
IPv4, IPv6 | Internet protocol addresses version 4 and 6 |
LDAP | Lightweight directory access protocol |
M2M | Machine-to-machine communication |
MAC address | Media access control address |
NAT | Network address translation |
NAPT | Network address port translation |
PAT | Port and address translation |
RARP | Reverse address resolution protocol |
RRP | Registry registrar protocol |
SLAAC | Stateless address autoconfiguration (IPv6) |
STUN | Session traversal utilities for NAT |
TURN | Traversal using relay NAT |
UPnP | Universal plug and play |
URI | Uniform resource identifier |
This place covers:
The pairing of addresses, which require a mapping or a conversion in the network. Specific examples are given in the subgroups.
The mapping of names to addresses is classified in the subgroups of H04L 61/45.
This place covers:
The pairing of addresses of different types which require a mapping or conversion in the network.
IPv4 and IPv6 addresses are considered to be of the same type in the context of this group.
Directory aspects should be classified in the subgroups of H04L 61/45. Mapping of addresses of the same type, e.g. NAT, is classified in H04L 61/25 and mapping of IPv4 and IPv6 addresses is classified in H04L 61/2503.
The type of addresses should be classified with orthogonal indexing H04L 2101/00 groups.
This place covers:
The pairing of addresses across network layers, e.g. the pairing of an IP address and a MAC address (ARP).
Examples: IETF RFC 826 (ARP), IETF RFC 6830 (LISP).
Attention is drawn to the following places, which may be of interest for search:
Data switching networks characterised by a path configuration; Interconnection of networks using encapsulation techniques, e.g. tunnelling |
This place covers:
The pairing of addresses across networks. The paired addresses relate to the same network entity. A typical example for a pairing across networks is the mapping of an IP address to a telephone number or to an address of a special purpose network.
IPv6 and IPv4 addresses are considered to be of the same type in the context of this group and the pairing of IPv4/IPv6 addresses is therefore classified in H04L 61/2503.
Attention is drawn to the following places, which may be of interest for search:
Data switching networks; Arrangements for connecting between networks having differing types of switching system, e.g. gateways | |
Network arrangements of protocols for real-time communication; Signalling, control or architecture; Gateways | |
Application independent communication protocol aspects of techniques in packet data networks; Protocols for interworking or protocol conversion |
This place covers:
The pairing of addresses of the same type. A typical example with regard to IP is NAT, i.e. the mapping between local and public addresses or the mapping between IPv4 and IPv6 addresses, which are considered to be of the same type in the context of the groups H04L 61/25 and H04L 61/106.
This place covers:
The pairing of IP addresses, i.e. the translation between local and public IP addresses or the translation between IPv4 and IPv6 addresses, see the specific subgroups below.
Attention is drawn to the following places, which may be of interest for search:
Network architectures or network communication protocols for network security for separating internal from external traffic, e.g. firewalls | |
Network-specific arrangements or communication protocols supporting networked applications in which an application is distributed across nodes in the network for accessing one among a plurality of replicated servers, e.g. load balancing |
This group should be used for the classification of any aspect of IP address translation that is not covered by the specific scenarios in the sub-groups, such as IP redirection.
This place covers:
Pairing of IPv4 and IPv6 addresses, e.g. NAT64.
Attention is drawn to the following places, which may be of interest for search:
Data switching networks characterised by a path configuration; Interconnection of networks using encapsulation techniques, e.g. tunnelling |
Encapsulation is classified in H04L 12/4633.
This place covers:
The pairing of local and global addresses, such as Network Address Translation [NAT].
Examples: IETF RFC 3022, IETF RFC 4787
Attention is drawn to the following places, which may be of interest for search:
Network architectures or network communication protocols for network security for separating internal from external traffic, e.g. firewalls |
This place covers:
The translation of TCP/UDP port numbers, such as in Network Address Port Translation [NAPT].
This place covers:
Architectures different from a single NAT server, see the specific scenarios covered by the subgroups.
This place covers:
Architectures where (a part of) the translation/conversion is performed at a client or a host. The translation performed in hypervisors is also classified here.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for program control using stored programs; Arrangements for executing specific programs; Emulation, Software simulation |
This place covers:
Architectures where (a part of) the translation/conversion is performed at an intermediary network element (other than a NAT server).
Attention is drawn to the following places, which may be of interest for search:
Application level gateways, ALGs, for NAT traversal | |
Network-specific arrangements or communication protocols supporting networked applications for the provision of proxy services, e.g. intermediate processing or storage in the network |
This place covers:
Multiple servers performing coordinated address translation operations.
This place covers:
Architectures connecting multiple LANs and requiring a translation of addresses due to overlapping address ranges.
Attention is drawn to the following places, which may be of interest for search:
Resolving address conflicts in the context of address allocation | |
Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks |
This place covers:
Architectures in which the translation/conversion is used to keep addresses anonymous. The architecture may be similar to H04L 61/2514, the main reason for the conversion however is the privacy aspect.
Attention is drawn to the following places, which may be of interest for search:
Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks; Anonymous communication, i.e. the party's identifiers are hidden from the other party or parties. |
Aliases classified in H04L 61/30 are not, per se, considered to be anonymous.
This place covers:
Mechanisms for avoiding unnecessary address translation, e.g. to avoid the routing of traffic via NAT devices to an external network, if both endpoints are in the same internal network.
Attention is drawn to the following places, which may be of interest for search:
Routing or path finding of packets in data switching networks |
This place covers:
Aspects relating to the maintenance of the mapping (translation/binding) table, such as table setup, timers for deletion of entries, etc.
This place covers:
Aspects relating to the renewal of mapping table entries.
Attention is drawn to the following places, which may be of interest for search:
Network architectures or network communication protocols for network security for separating internal from external traffic; Firewall traversal, e.g. tunnelling or creating pinholes | |
Network-specific arrangements or communication protocols supporting networked applications for session management; provided for avoiding end of session |
This place covers:
Any aspects relating to particular address translation policies or rules.
This place covers:
Any aspects relating to the traversal of NAT, e.g. enabling the connection between internal network nodes and external network nodes.
Attention is drawn to the following places, which may be of interest for search:
Network architectures or network communication protocols for network security for separating internal from external traffic; Firewall traversal, e.g. tunnelling or creating pinholes |
This place covers:
Traversal of NAT for OSI protocol layers 5 to 7, such as SIP or SNMP.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for maintenance or administration or management of packet switching networks using standardised network management protocols | |
Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks | |
Network arrangements or protocols for real-time communication; Signalling or session protocols, SIP |
This place covers:
Retrieving the routable (external) address of a client behind a NAT server for the purpose of NAT traversal.
This place covers:
Traversal methods in which a client retrieves its translated addresses, e.g. to share the address with potential peers.
This place covers:
Address translation traversal methods, which are transparent to the NAT server, contrary to the methods classified in H04L 61/2582.
This place covers:
Address translation traversal methods, which require direct communication with the NAT server to control the behaviour of the NAT server, contrary to the methods classified in H04L 61/2521. Popular examples are UPnP, Port Control Protocol (PCP) / Internet Gateway Device Protocol (IGD).
Attention is drawn to the following places, which may be of interest for search:
Data switching networks characterised by a path configuration; Home automation networks |
This place covers:
Address translation traversal methods using an ALG, which translates addresses and ports above Layer 4. Used for protocols that include lower layer addresses in the application layer payload, such as FTP or SIP.
Attention is drawn to the following places, which may be of interest for search:
Network-specific arrangements or communication protocols supporting networked applications for the provision of proxy services, e.g. intermediate processing or storage in the network |
This place covers:
Address translation traversal methods using a relay server for the communication between two peers.
Attention is drawn to the following places, which may be of interest for search:
Network-specific arrangements or communication protocols supporting networked applications for the provision of proxy services, e.g. intermediate processing or storage in the network |
This place covers:
The use of encapsulation/tunnelling in the context of address translation or address translation traversal.
Attention is drawn to the following places, which may be of interest for search:
Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks | |
Data switching networks characterised by a path configuration; Interconnection of networks using encapsulation techniques, e.g. tunnelling |
This place covers:
Translation of the same type of addresses, other than IP addresses, such as the translation between MAC addresses.
Attention is drawn to the following places, which may be of interest for search:
Routing or path finding of packets in data switching networks |
This place covers:
Aspects relating to any kind of names used in a network context (in contrast to a client-side only context) and the management of these names, such as conversion or registration.
This place does not cover:
Name-to-address mapping |
Attention is drawn to the following places, which may be of interest for search:
Detail of database functions independent of the retrieved data types; Retrieval from the web using information identifiers, e.g. uniform resource locators, URL |
This place covers:
Any kind of name conversion, such as conversions to short names, anonymized names or character conversion.
This place covers:
The registration of names, such as the registration of domain names and the use of RRP or EPP protocols for registration and management of domain names.
Attention is drawn to the following places, which may be of interest for search:
Administration, e.g. office automation or reservations | |
Commerce, e.g. shopping or e-commerce |
This place covers:
Aspects related to the generation of names and assignment of names to network nodes.
This place covers:
Distributed or centralised data network directories.
Attention is drawn to the following places, which may be of interest for search:
Information retrieval using distributed data base systems | |
Directory assistance systems | |
Details of addressing, directories or routing tables of networks other than PSTN/ISDN providing telephone service, e.g. Voice over Internet Protocol | |
Details of addressing, directories or routing tables for working between exchanges having different types of switching equipment, where the types of switching equipment comprises PSTN/ISDN equipment and switching equipment of networks other than PSTN/ISDN |
This place covers:
The use of standardised directories according to the sub-groups.
This place covers:
The Domain Name System [DNS]
Examples: IETF RFC 1035
This place covers:
Directories based on the X.500 standard.
This place covers:
The use of the LDAP protocol, e.g. Active Directory.
Aspects relating to the directories based on the X.500 standard are classified in H04L 61/4517.
This place covers:
Directories aspects of address exchange platforms, such as particular data stored in the directory, directory management etc.
Attention is drawn to the following places, which may be of interest for search:
Address translation traversal over a relay server, e.g. traversal using relay for network address translation [TURN] | |
Directories containing mobile subscriber information, e.g. home subscriber server [HSS] | |
Network arrangements or protocols for real-time communications; Signalling, control or architecture; Session control; Registration | |
Network-specific arrangements or communication protocols supporting networked applications for the provision of proxy services, e.g. intermediate processing or storage in the network |
This place covers:
Directories for the discovery of network services, e.g. printing services in the network. Example technologies are the Directory Agents in the Service Location Protocol [SLP], or DNS Service Discovery [DNS-SD].
Attention is drawn to the following places, which may be of interest for search:
Network-specific arrangements or communication protocols supporting networked applications; Service discovery or service management |
This place covers:
Directories linking a personal identifier of a user to multiple identifiers (e-mail address, telephone numbers etc.) associated with different communication channels of the user (similar to an address book) and e.g. providing the best way to reach the user.
Attention is drawn to the following places, which may be of interest for search:
Network-specific arrangements or communication protocols supporting networked applications; Presence management |
This place covers:
Aspects related to lookup mechanisms in a directory, lookup mechanisms between directories or synchronisation between directories, using e.g. OMA-SyncML.
Attention is drawn to the following places, which may be of interest for search:
Information retrieval; Database structures therefore; File system structures therefore of structured data, e.g. relational data |
This place covers:
Directories storing references to objects, e.g. COS Name service, for remote procedure calls.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for program control; Multiprogramming arrangements; Distributed object oriented systems |
Attention is drawn to the following places, which may be of interest for search:
Message switching systems, e.g. electronic mail systems |
This place covers:
Directories used in hybrid voice communication networks, e.g. ENUM.
Attention is drawn to the following places, which may be of interest for search:
Mapping addresses across networks, e.g. mapping telephone numbers to data network addresses | |
Network directories; Name-to-address mapping using domain name system [DNS] | |
Network directories; using an address exchange platform which sets up a session between two nodes, e.g. rendezvous servers, session initiation protocols, SIP, registrars or H.323 gatekeepers | |
Directories containing mobile subscriber information, e.g. home subscriber server [HSS] |
This place covers:
Directories used in mobile communication systems, such as HSS, HLR, VLR.
Attention is drawn to the following places, which may be of interest for search:
Processing of mobility data, Registration at HLR or HSS |
This place covers:
Directories containing contact information of users and involving a network aspect, such as address books located in the network, e.g. the Converged Address Books of the Open Mobile Alliance (OMA).
This place does not cover:
Telephone directories in user terminals |
This place covers:
The allocation of addresses to network devices.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for maintenance or administration or management of packet switching networks; Configuration management of network or network elements |
This place covers:
Allocation of IP addresses to network devices.
Any aspects relating to the allocation of IP addresses which are not covered by any of the subgroups should be classified in this group.
This place covers:
The use of the DHCP or BOOTP protocol for allocating IP addresses and sending further configuration information to network devices.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for maintenance or administration or management of packet switching networks; Configuration management of network or network elements | |
Network-specific arrangements or communication protocols supporting networked applications involving the movement of software and/or configuration parameters |
This place covers:
Allocation of IP addresses involving an AAA node, such as in 3GPP networks.
Attention is drawn to the following places, which may be of interest for search:
Network architectures or network communication protocols for network security for supporting authentication of entities communicating through a packet data network |
This place covers:
Allocation of any kind of addresses in data networks for local use in the network only, such as in a LAN, USB, bus or special purpose network, including the allocation of MAC addresses, e.g. in virtual machines.
Attention is drawn to the following places, which may be of interest for search:
Data switching networks characterised by a path configuration; Bus networks | |
Network-specific arrangements or communication protocols supporting networked applications adapted for proprietary or special purpose networking environments | |
Network topologies; Self-organizing networks, e.g. ad-hoc networks or sensor networks |
This place covers:
Methods for preventing address allocation conflicts in data networks, i.e. preventing that the same address is allocated to multiple devices.
This place does not cover:
Resolving address allocation conflicts in the context of address self-assignment, such as IPv4 and IPv6 DAD/SLAAC |
This place covers:
Aspects relating to the lease time or the renewal of allocated addresses.
This place covers:
Aspects related to pools of addresses in the context of address allocation, such as splitting an address pool in sub-pools and assigning the sub-pools to different DHCP servers.
This place covers:
Generation and allocation of group address used to address multiple recipients.
Attention is drawn to the following places, which may be of interest for search:
Data switching networks; Arrangements for providing special services to substations for broadcast or conference |
This place covers:
Update or notification mechanisms in the context of address allocation, e.g. notifying an entity which is originally not involved in the address allocation of a newly allocated address.
Attention is drawn to the following places, which may be of interest for search:
Address allocation by self-assignment, e.g. picking addresses at random and testing if they are already in use |
This place covers:
Address allocation arrangements in the context of device mobility/portability, such as in the Locator/Identifier Separation Protocol or Virtual Machine migration.
This place does not cover:
Network addressing or numbering for mobility support in wireless networks | |
Wireless network protocols or protocol adaptations to wireless operation; Network layer protocols, e.g. mobile IP |
This place covers:
The self-assignment of addresses, such as IPv6 Stateless Address Autoconfiguration, SLAAC or APIPA.
This place covers:
Temporary storage of addresses or names in a cache, such as in an ARP cache or in a DNS cache.
Attention is drawn to the following places, which may be of interest for search:
Network-specific arrangements or communication protocols supporting networked applications for the provision of proxy services; for storing data temporarily at an intermediate stage, e.g. caching |
This place covers:
Proxies for entities which are used for addressing, see the groups above: DHCP proxy, ARP proxy etc.
Attention is drawn to the following places, which may be of interest for search:
Network-specific arrangements or communication protocols supporting networked applications for the provision of proxy services, e.g. intermediate processing or storage in the network |
This place covers:
Networking architectures and network communication protocols for securing the traffic flowing through data packet networks and providing secure exchanges among applications communicating through data packet networks. The group covers specifically network architectures and network communication protocols for supporting:
- filtering (e.g. transferring, blocking, dropping) traffic according to security rules;
- authenticating and authorizing the entities sending and/or receiving the traffic;
- protecting the data packets against unauthorized reading or modification;
- detecting intruders and preventing the transmission of unauthorized, malicious or forged packets;
- lawful interception for legally authorised parties to access protected information.
H04L 63/00 focuses on network architectures (i.e. network entities involved, roles played by these entities) and network communication protocols (i.e. how these network entities communicate) regardless of the specifics of the cryptographic mechanism used.
H04W 12/00 Wireless networking architectures and wireless network communication protocols for securing the traffic flowing through wireless data packet networks and providing secure exchanges among applications communicating through wireless data packet networks. The group covers
specifically wireless network architectures and wireless network
communication protocols for supporting:
- Authenticating and authorizing the entities sending and/or receiving the traffic;
- Protecting the data packets against unauthorized reading or modification;
- Detecting intruders, rogue entities and preventing the transmission of unauthorized, malicious or forged packets;
- Lawful interception for legally authorised parties to access protected information.
H04W 12/00 focuses on wireless network architectures (i.e. wireless network entities involved, roles played by these entities) and wireless network communication protocols (i.e. how these network entities communicate) regardless of the specifics of the cryptographic mechanism used.
Details for wireless network security are classified where appropriate by the combination of H04W 12/00 subgroup and H04L 63/00 detailed subgroup.
H04L 12/22 subject-matter is always classified in the corresponding subclasses of H04L 63/00 and or H04W 12/00.
H04L 9/00 Cryptographic mechanisms including cryptographic protocols and cryptographic algorithms, whereby a cryptographic protocol is a distributed cryptographic algorithm defined by a sequence of steps precisely specifying the actions required of two or more entities to achieve specific security objectives (e.g. cryptographic protocol for key agreement), and whereby a cryptographic algorithm is specifying the steps followed by a single entity to achieve specific security objectives (e.g. cryptographic algorithm for symmetric key encryption).
H04L 9/00 focuses on cryptographic mechanisms such as encryption schemes, digital signatures, hash functions, random number generation, key management, said cryptographic mechanisms providing information security such as privacy or confidentiality, data integrity, message authentication, entity authentication, authorization, validation, certification, time-stamping, anonymity, revocation, non-repudiation.
H04L 9/00 covers also countermeasures against attacks on cryptographic mechanisms.
G06F 21/00 Security arrangements for protecting computers or computer systems against unauthorised activity, where the network communication aspect is not important.
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements for secret or secure communication | |
Security arrangements for protecting computers or computer systems against unauthorised activity | |
Network architectures or network communication protocols for wireless network security |
Attention is drawn to the following places, which may be of interest for search:
Non security aspects of VPN | |
Restricting access to network management systems or functions, e.g. using authorisation function to access network configuration | |
Arrangements for monitoring or testing data switching networks | |
Monitoring or handling of messages using filtering or selective blocking | |
Unsolicited communication attempts in real-rime communications, e.g. spam in IP telephony [SPIT] | |
Protocols specially adapted for proprietary and special purpose networking | |
Fittings or systems for preventing or indicating unauthorized use or theft of vehicles | |
Operating or controlling locks or other fastening devices by electric or magnetic means | |
Payment schemes, architectures or protocols | |
Burglar, theft and intruder alarms | |
Alarms responsive to two or more different undesired or abnormal conditions, e.g. burglary and fire, abnormal temperature and abnormal rate of flow | |
Alarm systems in which the location of the alarm condition is signalled to a central station, e.g. fire or police telegraphic systems | |
Lawful interception of plain old telephony systems [POTS] calls | |
Secrecy in the context of scanning, transmission or reproduction of documents or the like | |
Analogue secrecy and Subscription systems in television systems | |
Selective content distribution, e. g. interactive television, video on demand [VOD] involving stream encryption |
Classification of the additional aspects of an application in H04L 63/00 is mandatory.
In some cases specific protocols (e.g. IPsec, EAP, TLS) and/or architectures (firewalls, AAA) are used. In other cases existing network protocols, architectures and services are modified to achieve the security goals. In such cases, the documents are classified both in the corresponding security subgroups and in the respective application subgroups of e.g. addressing H04L 61/00, mobile services H04W 4/00, routing H04L 47/00 or cryptographic mechanisms H04L 9/00).
In this place, the following terms or expressions are used with the meaning indicated:
RFC 4949 | internet security glossary, version 2; definition of internet security terms |
This place covers:
Here are classified the documents related to the (logical) separation of traffic/(sub-) networks to achieve protection.
In this place, the following terms or expressions are used with the meaning indicated:
ALG | Application Level Gateway |
This place covers:
Here are classified devices and arrangements like firewalls, perimeter networks, bastion hosts, demilitarized zones, etc that are placed at the interface between two or more (sub-)networks, usually a private network (e.g. Intranet) and the public network.
This place covers:
Systems where every host, e.g. network interface card or dedicated security box, includes firewall capabilities or systems where firewalls communicate to share attack information and improve their efficiency.
Distributed architecture for accessing one among a plurality of replicated servers |
This place covers:
Aspects related to how traffic is filtered.
This place does not cover:
Mail message filtering |
This place covers:
Filtering of traffic based on address information, e.g. IP-address or URL or packet header information, e.g. protocol number or port number.
This place covers:
Filtering of information is performed based on the contents of the application payload.
Documents referring to content filtering in general and just mentioning virus scanning as a possible application are also classified here
When the application payload is inspected specifically to detect viruses, worms, exploits etc, the documents are classified in | |
Parental control, rating systems etc where the filtering depends on user or machine profile are also classified in |
Attention is drawn to the following places, which may be of interest for search:
Specialized CPUs or hardware for application information filtering/parsing |
This place covers:
Stateful firewall keeping track of the state of network connections, e.g. TCP streams, travelling across it being able to filter packets according rules and/or taking appropriate action (e.g. cleaning, discarding, forwarding).
Monitoring of connection state to detect and mitigate attacks (e.g. SYN attacks) |
This place covers:
Aspects related to how the filtering rules are organized, defined, evaluated or added in a firewall are classified here.
Rule management in the sense of access control rules to access to network resources (authorisation) | |
Security policies in general |
This place covers:
Restricted-use, logical networks constructed from the system resources of a relatively public, physical network, e.g.Internet, realised e.g. using encryption or tunnelling links of the virtual network across the real network, e.g. using IPsec ESP between security gateways.
Attention is drawn to the following places, which may be of interest for search:
Non security aspects of VPN |
This place covers:
Relaying protocol(s) between e.g. client and server systems, by appearing to the client to be the server and appearing to the server to be the client.
Instead of a client in the protected enclave connecting directly to an external server, the internal client connects to the proxy server which in turn connects to the external server. The proxy may be transparent to the clients, or they may need to connect first to the proxy server, and then use that association to also initiate a connection to the real server. Proxies may provide protocol/application specific functionality (e.g. HTTP Proxy) or may provide generic connection services (e.g. SOCKS). Proxies can provide security service beyond that which is normally part of the relayed protocol, such as access control based on peer entity authentication of clients, or peer entity authentication of servers when clients do not have that capability. These aspects should be classified in the appropriate sub-groups.
Attention is drawn to the following places, which may be of interest for search:
Non security aspects of proxies where processing is performed in an intermediate network node |
Using a proxy for authentication is classified here in combination with H04L 63/08 (and subgroups).
This place covers:
The mechanisms for achieving connections through firewalls are classified here, e.g. tunnelling the application protocol in a protocol that is allowed through the firewall (e.g. HTTP, SMTP) or using of an application layer gateway which understands the application message and opens the appropriate pinholes in the firewall.
Attention is drawn to the following places, which may be of interest for search:
Non secure NAT traversal |
For some documents H04L 63/0281 is also to assign.
This place covers:
Network architectures and communication protocols for implementing confidentiality of information transmitted over a data packet network, most often by applying cryptographic mechanisms. Also classified here are networking architectures and protocols for anonymous communications.
Protecting privacy or anonymity | |
Protecting confidentiality, e.g. by encryption |
Attention is drawn to the following places, which may be of interest for search:
Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity for protecting data |
This place covers:
Protecting the identity of a party (origin or destination) against disclosure to a third party (eavesdropper) or the other party.
Attention is drawn to the following places, which may be of interest for search:
Protecting personal data on a computer, e.g. for financial or medical purposes |
This place covers:
The identity is only known to the other party or parties involved in the communication. Protecting the party's identity usually involves specific techniques which are different from message confidentiality, since the identity is used for routing and authentication purposes.
This place covers:
The identity of one of the parties is not disclosed to the other party. Some techniques involve the use of aliases, anonymizer proxies, onion routing, etc.
Attention is drawn to the following places, which may be of interest for search:
Protecting personal data on a computer by anonymising |
This place covers:
Communication protocols used to protect the information exchanged through networks. Also are classified here architectural arrangements to achieve the protection, e.g. encryption proxies. The subgroups identify specific techniques therefore.
This place covers:
Symmetric and asymmetric encryption is combined. Usually symmetric encryption is used to protect the message and the symmetric (session) key is encrypted using asymmetric encryption, so no one other than the intended recipient can "open" the message.
This place does not cover:
Cryptographic mechanisms using a plurality of keys or algorithms |
In this place, the following terms or expressions are used with the meaning indicated:
digital envelope | the combination of the encrypted data and the encrypted key |
This place covers:
The use of stream encryption, i.e. serially and continuously modifying data streams.
This place does not cover:
Cryptographic mechanisms for stream encryption |
This place covers:
Hardware and software architectures, e.g. IPsec offloading, specifically adapted for improving the process of encrypting and decrypting packets and handling the security association tables.
This place covers:
Network architectures and communication protocols for negotiation, transport, validation, or update of security keys or credentials (i.e. specific network entities involved and the network protocols used) regardless of whether they are used for confidentiality (privacy), authentication, access control or for integrity validations in order to strictly differentiate between the initialisation phase (i.e., key distribution/exchange phase) of any secure communication and the secure communication itself.
Key management specially adapted for wireless networks |
This place does not cover:
Cryptographic mechanisms for key management |
This place covers:
Exchanging the respective security keys directly between two communicating parties such as e.g. in peer-to-peer networks.
This place does not cover:
The cryptographic mechanisms or cryptographic arrangements for key agreement |
In this place, the following terms or expressions are used with the meaning indicated:
Typical standardised protocols for key exchange are IKE (Internet Key Exchange) or ISAKMP (Internet Security Association and Key Management Protocol).
This place covers:
Distributing the respective security keys from a central trusted party such as a Key Distribution Centre (KDC) to the attached network nodes. A typical (hierarchical) architecture for key distribution is represented by PKI (Public Key Infrastructure).
This place does not cover:
The cryptographic mechanisms or cryptographic arrangements for key distribution involving a central third party |
This place covers:
Key exchange or distribution within multicast/broadcast networks typically by using a group key for confidentiality and/or authentication purposes (typical protocol standard: Group Key Management Protocol GKMP).
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements for key management involving conference or group key |
This place covers:
Keys are only used once.
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements for generation of one-time passwords |
This place covers:
Periodically changing keys, e.g., based on time stamps.
The aspects related to password renewal |
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements for controlling usage of secret information |
This place covers:
Performing authentication of users, devices or applications trying to gain access to resources of a network.
Authentication specially adapted for wireless networks |
This place does not cover:
Cryptographic mechanisms for entity authentication |
Attention is drawn to the following places, which may be of interest for search:
Authentication in the context of security arrangements for protecting computers | |
Active credit-cards provided with means to personalise their use |
The selection of an authentication mechanism is classified in H04L 63/08 in combination with H04L 63/205 or H04L 69/24.
Using a proxy for authentication is classified here in combination with H04L 63/0281.
Authentication using multiple network paths is classified in appropriate H04L 63/08 subgroup in combination with H04L 63/18.
In this place, the following terms or expressions are used with the meaning indicated:
Authentication | Identify if the entity is the one he/she claims to be. Remark: authentication and authorisation are sometimes used with the other meaning in patent literature as well as in non patent literature |
This place covers:
Ticket-based authentication mechanisms, e.g. Kerberos, SESAME. Tickets may be transmitted in different ways, e.g. in a cookie.
When the same ticket enables the authentication to a plurality of network resources, e.g. Single-Sign-On |
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements for entity authentication using tickets or tokens |
Attention is drawn to the following places, which may be of interest for search:
Digital data processing restricting access to computer systems by authenticating users, devices or programs using a predetermined code using a certificate from a trusted centre or via a trusted hierarchical route |
This place covers:
Mechanisms where a user/device supplies a single authentication credential and gets access to a plurality of resources in a network.
This place covers:
Authentication is based on certificates; also issuing or retrieval of certificates.
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements for entity authentication involving certificates |
Attention is drawn to the following places, which may be of interest for search:
Computer user authentication using certificates |
Documents related to the use of certificates for authorization (e.g. attribute certificates) are classified in combination with H04L 63/10.
This place covers:
If string of characters, not only actual words, but also passcodes (like PIN), software tokens or keys, is used for authentication.
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements for entity authentication using a predetermined code |
This place covers:
Time synchronisation exists between e.g. the supplicant and the authenticator or periodically changing passwords or password expiration or password ageing aspects.
This place covers:
The authentication is performed using additional devices, e.g. smartcards, SIM or similar devices for authentication, an additional communication device (e.g. using a mobile telephone for authenticating a session established through a computer connected to a data network)
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements for entity authentication involving additional secure or trusted devices |
Attention is drawn to the following places, which may be of interest for search:
Digital data processing restricting access to computer systems by authenticating users, devices or programs using a predetermined code in combination with an additional device | |
Authentication involving the use of external additional devices, e.g. dongles or smart cards | |
Payment schemes, architectures or protocol using wireless devices | |
Active credit cards provided with means to personalise their use, e.g. with PIN-introduction/comparison system |
When the additional device establishes an additional channel for performing the authentication, the document is also classified in H04L 63/18
This place covers:
Authentication in network or networks based on biometric features e.g. fingerprint, retina-scan
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements entity authentication using biological data |
Attention is drawn to the following places, which may be of interest for search:
User authentication on a computer using biometric features |
This place covers:
Authentication of both parties communicating over network.
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements for mutual authentication |
Attention is drawn to the following places, which may be of interest for search:
Mutual authentication between programs |
This place covers:
The authentication is performed based on the identity of the terminal e.g. MAC address or other address or configuration of hardware or software or device fingerprint.
This place covers:
The authentication is delegated to another entity which acts on behalf of the entity to be authenticated.
This place covers:
AAA servers or protocols are used to authenticate entities.
This place covers:
Mechanisms to allow or restrict the access to devices or resources, for example by restricting access to a particular group of computers or contents based on their addresses or based on user requests (e.g. list of forbidden websites, parental control) or smart locks.
Access control in wireless networks |
Attention is drawn to the following places, which may be of interest for search:
Restricting access to network management systems or functions | |
Protection of software on a computer against unauthorized usage (e.g. DRM) | |
Protection of data on a computer against unauthorized access or modification |
In this place, the following terms or expressions are used with the meaning indicated:
Authorisation | Identify which rights are assigned to an entity. Remark: authentication and authorisation are sometimes used with the other meaning in patent literature as well as in non patent literature |
This place covers:
Authorization is implemented via access control lists.
This place covers:
Documents are classified here when they focus on the use of entity profiles, e.g. device profiles or user profiles to manage access decisions. Also documents related to identity management are classified here.
This place covers:
Mechanisms for implementing access control to group or groups of entities.
Role based access control (each entity is associated to a group/role, and each role has a different privilege level) |
This place covers:
Mechanisms for implementing multiple levels of security or different access rights according to entities (e.g. device or user) security clearance, to security profiles, roles or to security perimeters (i.e. different zones of a network need different security clearance/levels; data pump i.e. low level security is able to communicate with higher level and not vice versa)
This place covers:
Security policies being different for a user or an entity dependent on the current location
Attention is drawn to the following places, which may be of interest for search:
Mobile application services making use of the location of users or terminals |
This place covers:
Network architectures and communication protocols mechanisms, e.g. signatures, MIC/MAC codes and others more, for guarantying the integrity of the information exchanged through a packet data network are classified here. Both the aspect of verifying the content and the identity of the source are classified here. Documents emphasizing one of the sub-aspects are classified in the corresponding subclass.
When specially adapted to wireless networks |
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements for data integrity and verification |
Attention is drawn to the following places, which may be of interest for search:
Protecting data on a computer against unauthorised access or modification, protecting integrity |
This place covers:
Network ensures that the content has not been tampered with during transmission through the network.
This place covers:
Verification of the identity of the original source of received data is applied (non-repudiation with proof of origin, non-repudiation with proof of receipt, trust level of identity and/or source).
This place covers:
Detection and protection against network attacks.
Detection and protection aspects specific of wireless networks (e.g. detection of rogue entities, access points); if appropriate, the corresponding H04L 63/14 subgroup is also to assign. |
Attention is drawn to the following places, which may be of interest for search:
Virus detection algorithms within a computer | |
Intrusion is detected based on the activity within a computer (e.g. controlling the memory access, watching the execution of the programs, watching traces of failed login attempts, etc.), this is what usually is referred to in the bibliography as Host-based IDS |
This place covers:
Detection of attacks involves monitoring the traffic on the network. Detection can be performed by different means; anomaly detection (comparing monitored traffic against normal traffic); misuse detection (detecting specific traces which imply an attack).
Attention is drawn to the following places, which may be of interest for search:
General traffic monitoring aspects |
This place covers:
Real time detection of attacks or intrusion attempts (e.g. "misuse detection").
This place covers:
Traffic logging for security purposes (e.g. detecting normal or anomalous behaviour; comparing behaviour; offline analysis using data mining, network security audit); non-real detection for deferred analysis.
This place covers:
Active probing of the network looking for vulnerable points, e.g. performing port scans, sending malformed packets and checking if they are detected.
This place covers:
Countering attacks or malicious traffic.
This place does not cover:
Countermeasures against attacks on cryptographic mechanisms |
This place covers:
Mitigation of denial of service attacks (also referred to as flooding, overload or congestion attacks) are classified here. Some techniques involve identification of the path followed by the attack. Some other techniques include rate limitation (throttling) or QoS (separation in different class of service). Some documents relate to black-hole attacks, wherein a malicious node discards all or part of the traffic (black-hole, gray-hole, worm-hole).
Attention is drawn to the following places, which may be of interest for search:
For QoS may be also relevant | |
Ad-hoc environments |
This place covers:
Protection against active wire tapping in which the attacker attempts to seize control of a communication association, e.g. packet injection or modifying, hijacking sessions, TCP sequence number attacks, piggyback attacks, man-in-the-middle attacks, spoofing etc.
This place covers:
Passively monitoring an existing session without the session participants noticing; e.g. eavesdropping or listening without modification of the traffic monitored.
Detection of rogue access point |
This place covers:
Security solution is specific to a certain layer.
Attention is drawn to the following places, which may be of interest for search:
Particular aspects of OSI layers in general |
This entries provides additional information. The documents classified here will also have a subgroup in further appropriate network security subgroup or subgroups.
This place covers:
Network traffic is secured by transmitting information through different channels of networks.
Two examples are:
- placing an order over the internet and using a telephone to communicate credit card information,
- or using a password received via SMS to obtain access to a remote computer.
This place does not cover:
Cryptographic mechanisms or cryptographic arrangements for key distribution involving distinctive intermediate devices or communication paths | |
Cryptographic mechanisms or cryptographic arrangements for authentication using a plurality of channels |
This place covers:
Management of network security or network security policies, e.g. managed services, deciding where to put firewalls, which data to encrypt, which authentication method to use, etc.
This place does not cover:
Filtering policies |
Attention is drawn to the following places, which may be of interest for search:
Restricting access to network management systems or functions, e.g. using authorization function to access network configuration | |
Negotiation of communication capabilities |
Packet filtering policies H04L 63/0227 and subgroups.
The classification in combination with H04L 63/08, H04L 63/04, H04L 63/10 is given to documents involving the selection of a particular authentication or confidentiality methods or access privileges by negotiation, according to capabilities or policies.
This place covers:
Negotiation or determination between networking entities of the one or more network security algorithms to be used.
This place does not cover:
Negotiation of communication capabilities in general |
This place covers:
Lawful interception; monitoring or retaining of communications or commnication related information
This place does not cover:
Call tracing; Detection or prevention of malicious calls |
In this place, the following terms or expressions are used with the meaning indicated:
handover interface | lawful interception handover interface HI1, HI2 and HI3 to hand over warrant, intercept related information and communication content between service provider and lawful authorities |
This place covers:
Gathering intelligence information for situation awareness or reconnaissance, tactical control or intelligence concepts.
This place does not cover:
Lawful interception of wireless communication including protecting privacy or anonymity, e.g. protecting personally identifiable information [PII] |
Attention is drawn to the following places, which may be of interest for search:
Arrangements enabling lawful interception [LI] |
This place covers:
Communication arrangements or protocols which fulfil the following two conditions:
- They are based on packet data
- There is real-time or pseudo-real-time temporal association between source and destination, or source and network, or destination and network
- Provided that the above two conditions are met, this group covers arrangements relating to:
- Transmission of the multimedia data itself
- User-to-user, user-to-network, inter-network or intra-network signalling support
- Establishment of a session for the subsequent transmission of the multimedia data
- Maintenance of the session
- Application services available to the user during the session
Generally, H04L 65/00 has relationships with the following general areas: H04L 67/00, H04L 69/00, H04N 21/00, H04N 7/00, H04N 5/00, H04L 12/18, H04L 51/00, H04L 41/00, H04L 41/06, H04M, H04Q 11/00.
As already mentioned, Real Time Multimedia Communications within the context of main group H04L 65/00 cover communications which have the following two characteristics:
- Data Packet based;
- Real-time or pseudo-real-time temporal association between source and destination, or source and network or destination and network.
The above definition covers both the arrangements or protocols related to the transmission of the multimedia data itself, as well as the user-to-user or user-to-network signalling supporting the establishment of a session for the subsequent transmission of the multimedia data, the maintenance of the session and the application services available to the user during the session (unless explicitly excluded in certain cases). The above definition/limitation of the scope of main group H04L 65/00 must always be borne in mind in interpreting the relationship of main group H04L 65/00 with all other fields.
Excluded from the scope of main group H04L 65/00 are arrangements for multimodal data communications which do not have the above two characteristics.
Examples of what is excluded are (if not in combination with a communication arrangement covered by the above definition, as in e.g. combinational or collaboration systems):
- Non-real-time multimedia file transfer (group H04L 67/06);
- Multimedia Store and Forward Messaging as in e-mail, MMS, etc. (main group H04L 51/00);
- Analogue multimedia streaming, e.g. in analogue television (main groups H04N 5/00, H04N 7/00, H04N 21/00).
Relationship between main group H04L 65/00 and legacy telephony (subclass H04M):
- Legacy telephonic communication is classified in subclass H04M, whilst real-time packet-based multimedia telephony (i.e. interactive voice and video communications over a network) is classified in main group H04L 65/00. Specifically: Systems and arrangements in which the legacy non-packet-based core telephony network (circuit switched PSTN or ISDN) represents a major part, are classified in subclass H04M.
- Systems and arrangements in which the legacy non-packet-based core telephony network (circuit switched PSTN or ISDN) represents a trivial or insignificant part or is totally absent, and the packet-based network (e.g. Internet, IMS) represents the only or the major and the most significant part are classified in main group H04L 65/00;
- Signalling adaptation-interworking between SIP and SS7 is classified in main group H04M 7/00.
- A CPE gateway or Terminal Adapter allowing a legacy user telephone device to connect to the packet-based network is classified in main group H04L 65/00;
- A signalling gateway interfacing two core networks, one legacy and one packet-based (e.g. SIP-SS7 gateway) is classified in subclass H04M;
- A transparent IP pipe interconnecting two legacy circuit switched networks, with no details on the IP pipe itself, is normally classified in subclass H04M;
- A transparent dial-up or leased circuit-switched line interconnecting two packet-based networks, with no details on the dial-up circuit-switched line itself, is normally classified in main group H04L 65/00;
- An IP-gateway allowing a call to be selectively branched off to either a legacy network or a packet-based network is normally classified in subclass H04M. However, if no significant details of the legacy network aspects are discussed apart from it being mentioned as an alternative, the IP-gateway may be classified in main group H04L 65/00.
Further comments and explanations regarding main group H04L 65/00 and its relationships with other related fields:
In order to avoid confusion with groups of other neighbouring fields, whose definitions use wording similar to that used in this main group, references to these fields will be mentioned with specific disclaimers if possible. In case a reference is unintentionally omitted, the above defined limitations in the scope of H04L 65/00 subgroup entries must always be borne in mind.
This place does not cover:
Real-time or near real-time messaging, e.g. instant messaging [IM] | |
Selective content distribution, e.g. interactive television or video on demand [VOD] |
Attention is drawn to the following places, which may be of interest for search:
Network security protocols | |
Data switching systems for broadcast or conference | |
Arrangements for connecting between networks having differing types of switching systems | |
Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks | |
Data network testing or monitoring | |
Arrangements for monitoring or testing data switching networks | |
Flow control or congestion control in data switching networks | |
User-to-user messaging in packet-switching networks, transmitted according to store-and-forward or real-time protocols, e.g. e-mail | |
Instant messaging | |
Network arrangements, protocols or services for addressing or naming in data networks | |
Arrangements for network security | |
Network arrangements or protocols for supporting network services or applications | |
WEB based applications | |
Adaptation for terminals and/or networks with limited resources or for terminal portability | |
Non-real-time multimedia file transfer | |
Terminal emulation | |
Arrangements to access one among a plurality of replicated servers, e.g. load balancing | |
Arrangements for peer-to-peer networking in network applications | |
Telewriting, virtual reality or network gaming | |
Non-real-time session management in network applications | |
Terminal profiles | |
Network application being adapted for the location of the user terminal | |
Arrangements for push based network services | |
Intermediate processing in the network with arrangements for data reduction or adaptation | |
Arrangements for scheduling or organising the servicing of requests whereby quality of service or priority requirements are taken into account | |
Network protocols for data compression | |
Protocols for interworking or protocol conversion | |
Multichannel or multilink protocols independent of the application payload | |
Header parsing or analysis independent of the application payload | |
Negotiation of communication capabilities independent of the application payload | |
Arrangements for broadcast or distribution combined with broadcast | |
Arrangements for broadcast applications with a direct linkage of broadcast information | |
Telephonic substation equipment, e.g. for use by subscribers | |
Automatic or semi-automatic telephonic exchanges | |
Systems providing special services to telephonic subscribers | |
Circuit switched PBXs | |
Arrangements for screening incoming telephone calls | |
Information services comprising voice | |
Contact centre services | |
Telephonic conference systems | |
Services and arrangements where telephone services are combined with data services | |
PBX networks | |
Interconnection arrangements between switching centres for working between exchanges having different types of switching equipment where the types of switching equipment comprise PSTN/ISDN equipment and equipment of networks other than PSTN/ISDN | |
Decomposed PSTN/ISDN-IP gateways | |
Television systems in general | |
Television conferencing systems | |
Television systems using two way working | |
Transmission of television signals using pulse code modulation | |
Selecting arrangements in telephonic networks | |
Selecting arrangements for time-division multiplexing | |
Wireless communication networks | |
Wireless location based services | |
Push-to-Talk services in wireless networks |
In patent documents, the following abbreviations are often used:
AS | Application server |
ATA | Analog telephone adapter |
BW | Bandwidth |
FTP | File transfer protocol |
H.323 | International telecommunication union recommendation no. 323, series H, entitled "Packet-based multimedia communications systems" |
IP | Internet protocol |
IMS | IP multimedia subsystem |
ISDN | Integrated services digital network |
MEGACO | Protocol used between elements of a physically decomposed multimedia gateway (i.e. Media Gateway and media Gateway Controller) as defined in RFC3525 (MEdia GAteway COntrol) |
MGC | Media gateway control/controller |
MGCP | Media gateway control protocol |
MMS | Multimedia messaging service |
PBX | Private branch exchange |
PSTN | Public switched telephone network |
QoS | Quality of service |
RTP | Real time protocol |
RTCP | Real time control protocol |
RTSP | Real time streaming protocol |
SIP | Session initiation protocol |
Attention is drawn to the following places, which may be of interest for search:
Data network management | |
Data network testing or monitoring | |
Admission control or resource reservation in packet switching networks | |
Control signalling related to video distribution | |
Selecting or control in telephonic networks |
This place covers:
Architectures and all entities, whether in the network or near and at the customer premises, identified at present as being part of packet-based multimedia systems and networks. Functionalities and services provided by these entities may also be classified in H04L 65/40 - H04L 65/4061 and H04L 65/60 - H04L 65/65.
This parent class is only used if the document cannot be classified in any of its dependent subclasses.
Attention is drawn to the following places, which may be of interest for search:
One-way network streaming services and controlling of the source by the destination | |
Streaming protocols, e.g. RTP or RTCP |
This place covers:
Repository of all IMS documents. Depending on its content an IMS related document which also describes an important entity service or functionality may also be classified in one of the other classes.
Attention is drawn to the following places, which may be of interest for search:
Wireless communication networks |
This place covers:
Gateway is an inter-working entity providing some degree of adaptation between otherwise incompatible entities or networks. An entity providing pure media manipulation (e.g. multiplexing of packets, media resolution optimisation, etc.) does not normally fall within this definition of a gateway. Such functionality is normally covered by H04L 65/60 - H04L 65/65. This parent class is only used if the document cannot be classified in any of its dependent subclasses.
This place does not cover:
Arrangements for connecting between networks having differing types of switching systems |
This place covers:
Gateways specifically providing media adaptation (e.g. codec incompatibility, analogue to packet voice or video, etc. If the document specifically identifies the position of the gateway within the network, then one of the following dependent classes must be given.
This place covers:
The media gateway is near or at the customer premises, e.g. a document describing the media adaptation functionalities of an ATA or a Residential Gateway.
This place covers:
The media gateway is within the network.
This place covers:
Gateways specifically providing signalling adaptation (e.g. SIP to H.323). Note: any adaptation to and from SS7 is covered by H04M 7/00. If the document specifically identifies the position of the gateway within the network, then one of the following dependent classes must be given.
This place covers:
The signalling gateway is near or at the customer premises, e.g. a document describing the signalling adaptation functionalities of an ATA or a Residential Gateway.
This place covers:
The signalling gateway is within the network.
This place covers:
MGCs using MCGP, Megaco, H.248, etc. The full MGCP-H.248-MEGACO family of protocols is covered by this class.
Attention is drawn to the following places, which may be of interest for search:
Decomposed PSTN/ISDN-IP gateways |
This place covers:
Details of entities acting on behalf of the user agent, e.g. SIP proxies, P-CSCF in IMS etc.
This place covers:
All different Call Controlling entities providing e.g. resource reservation. Note that MGCs in particular are covered by the previous class.
This place covers:
Entities providing IP PBX or Software-defined PBX functionality. However, the particular cases of IP PBX arrangements which may be distributed and provide effective local PBX service to users dispersed over multiple remotely located sites are covered by the following group.
This place does not cover:
Arrangements providing PBX functionality, e.g. IP PBX (circuit switched PBXs |
Attention is drawn to the following places, which may be of interest for search:
PBX networks |
This place covers:
Entities providing IP PBX or Software-defined PBX functionality related to the specific architecture of single-site PBX infrastructure.
This place covers:
IP PBX arrangements which may be distributed and provide effective local PBX service to users dispersed over multiple remotely located sites, e.g. corporate PBXs.
This place covers:
Functionalities of the user terminal associated with the signalling and control of the multimedia session and the handling of the media.
Constructional details and general features of a user terminal are normally covered by H04M 1/00.
Attention is drawn to the following places, which may be of interest for search:
Adaptation for terminals with limited resources or for terminal portability | |
Terminal emulation | |
Terminal profiles | |
Substation equipment for use by subscribers | |
Management of video client characteristics | |
Management of video client characteristics |
This place covers:
Application server (AS) entities in the network, providing services to the end users. A document describing details of an application server as well as the services it provides, may also need to be classified in one of the subentries of H04L 65/40 - H04L 65/613 or in the subentry for FEATURES H04L 65/1096.
This place does not cover:
systems providing special services to telephonic subscribers |
This place covers:
All the signalling and procedures required for a multimedia session of any type (VoIP call, video call, streaming session, conference, etc.) to be prepared, set up, maintained and serviced.
Attention is drawn to the following places, which may be of interest for search:
Conducting a computer conference, e.g. admission, detection, selection or grouping of participants, correlating users to one or more conference session or prioritising transmission | |
Admission control/resource reservation in packet switching networks |
This place covers:
The function of setting up a multimedia session irrespective of the type of the session, i.e. two-party multimedia telephony call, N-way multimedia telephony call, Conference call, etc.; e.g. a document describing a multiparty session setup should be assigned this entry and also at least one of the entries under H04L 65/403 - H04L 65/4053.
Attention is drawn to the following places, which may be of interest for search:
Computer conference organisation arrangements, e.g. handling schedules, setting up parameters needed by nodes to attend a conference, booking network resources or notifying involved parties | |
Admission control or resource reservation in packet switching networks | |
Arrangements for peer-to-peer networking in network applications | |
Session management in network applications | |
Negotiation of communication capabilities |
This place covers:
The procedure of a user registering in a network. The registration includes all aspects of the end user, i.e. addresses, aliases, capabilities, permissions, etc.
Re-registration, de-registration, maintaining or refreshing registrations, etc.
Details of the registrar directories and the procedures for consulting these directories are covered by H04L 61/00. A document describing both the registration procedure itself and the structure of the directory should be classified both in H04L 65/1073 and in the appropriate H04L 61/00 group.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for addressing or naming in data networks |
This place covers:
The procedure of admitting or rejecting a call or session setup request, either by the network or the destination.
Security-related call admission control is normally covered by H04L 63/00, with the exception of SPIT covered by H04L 65/1079. Also, billing-related call admission control is normally covered by H04L 12/14 and H04M 9/00.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for network security | |
Arrangements for screening incoming telephone calls |
This place covers:
Call control specifically associated with the identification of SPAM VoIP calls.
Attention is drawn to the following places, which may be of interest for search:
Message switching systems, e.g. electronic mail systems, with filtering and selective blocking capabilities |
This place covers:
Procedures that take place during the session either with in-band or out-of-band signalling. Procedures related to "Session scope modification" are covered by the explicit subentries that follow. All the other procedures are covered by this entry, including aspects of session (or voice or service) continuity (VCC) and session recording. Session continuity within this scope of this entry covers aspects associated with the signalling at session layer level (SIP, IMS). Lower level session continuity, handoff or handover (including mobile IP level) is covered by H04W 36/0011 .
Attention is drawn to the following places, which may be of interest for search:
Computer conferences, network arrangements for conference optimisation or adaptation | |
Reactions to resource unavailability in packet switching networks | |
Reallocation or renegotiation of resources in packet switching networks |
This place covers:
Procedures that expand or contract the scope or some aspect of the session. If the expansion or contraction is related to adding or removing media or participants, the following explicit subentries apply. Other aspects (e.g. expanding the BW of the call) are covered by this subentry.
This place covers:
Adding or removing a real time medium during the call; e.g. adding video to a voice only session.
This place covers:
Adding or removing a participant during the call; e.g. adding a 3rd participant to a 2-way call by using the SIP REFER method.
This place covers:
Session transfer or sharing between multiple UEs.
This place covers:
Features are certain session-related services provided by the network operator that can be (pre)programmed by a subscriber. Examples of legacy features offered by legacy telephony network operators are: Call forwarding, Call hold, Follow-me, etc. Depending on the scope of the features and the network over which they are provided, these features may be covered by this entry or the H04M 3/00 classes. The following table clarifies the distinction between the two classes:
Legacy features provided over legacy type circuit switched networks | |
Legacy features provided over packet-based networks, but the document describes mainly the "user experience" of the legacy features with insignificant to no details of the signalling involved in the packet-based network. | |
Legacy features provided over packet-based networks and the document describes details of the "user experience" of the legacy features as well as details of the signalling involved in the packet-based network | |
Legacy features provided over packet-based networks and the document only concentrates on the details of the signalling involved in the packet-based network without any details of the "user-experience" | |
New non-legacy features which could not be provided by legacy type networks and can only be offered by new packet-based networks |
This place does not cover:
systems providing special services to telephonic subscribers |
This place covers:
All packet-based signalling protocols for packet-based networks, current and future, although only SIP and H.323 families of protocols are explicitly identified at present. The SIP and H.323 families of protocols are classified in their specific dependent subgroups. All non-SIP and non-H.323 protocols for signalling and session management are classified in this parent class. SIP and H.323 are classified in their dedicated dependent subgroups.
This place covers:
IETF SIP family of protocols, including SDP, etc.
This place covers:
H.323 ITU family of protocols.
This place covers:
The use of WebRTC in real-time or near real-time communications.
Telephony services provided over legacy circuit switched networks are covered by H04M 3/00. Documents relating to telephony services provided over VoIP networks are only covered by this entry if they relate to the VoIP signalling and protocols required for the provision of the services. Documents relating mainly to the "user experience" provided by the services, with little to no information on the VoIP signalling and protocols, are only covered by H04M 3/00. The following table clarifies the distinction between the two places:
Services provided over legacy type circuit switched networks | |
Services provided over VoIP packet-based networks, but the document describes mainly the "user experience" of the information services with insignificant to no details of the signalling involved in the VoIP packet-based network | |
Information services provided over VoIP packet-based networks and the document describes details of the "user experience" of the information services as well as details of the signalling involved in the VoIP packet-based network | |
Services provided over VoIP packet-based networks and the document only concentrates on the details of the signalling involved in the packet-based network without any details of the "user experience" |
Note: Aspects of WEB related information services are also covered by H04L 67/02 (e.g. click-to-dial from within a WEB a page).
Attention is drawn to the following places, which may be of interest for search:
Network service management for ensuring proper service fulfilment | |
Systems providing special services to telephonic subscribers | |
Information services comprising voice | |
Contact centre services |
This place covers:
During an existing interactive real-time session, another parallel session is initiated and/or maintained. This entry covers the signalling for the initiation and the maintenance for this additional session. Note: adding a medium in an existing session is not considered a parallel session.
Attention is drawn to the following places, which may be of interest for search:
Real time messaging, e.g. instant messaging, interacting with other applications or services | |
Multichannel or multilink protocols | |
Services and arrangements where telephone services are combined with data services |
This place covers:
This entry involves an additional parallel session which is time sensitive, e.g. the initiation of a parallel session for the streaming of a video clip or for a shared white board for distant learning, etc. Also the spawning of a sub-conference by a participant is also covered by this entry.
Note: The addition of a participant in an existing session is not considered a parallel session, if this new participant becomes a full member of the existing session.
Aspects of Tele-writing, Virtual Reality and Network Gaming are also covered by H04L 67/131.
Attention is drawn to the following places, which may be of interest for search:
Telewriting, virtual reality or network gaming |
This place covers:
This entry involves an additional parallel session which is not time sensitive, e.g. the initiation of a parallel session for a file transfer using FTP, the sending of an e-mail message, etc.
Attention is drawn to the following places, which may be of interest for search:
Message switching systems | |
Instant messaging | |
WEB based applications | |
File transfer |
This place covers:
This entry involves an additional parallel session which is not time sensitive, e.g. the initiation of a parallel session for a file transfer using FTP, the sending of an e-mail message, etc.
Attention is drawn to the following places, which may be of interest for search:
Message switching systems | |
Instant messaging | |
WEB based applications | |
File transfer |
This place covers:
The control and the signalling of a multi-party session. Multi-party sessions, in the context of this entry can be Conferences and N-way calls. The subentries of this class distinguish multiparty communication by the type of floor control used in the session.
It is noted that floor control is defined as the ability of an entity to control when participants are allowed to transmit and receive multimedia data. The ability of a participant to simply mute its own output or input does not by itself constitute floor control.
The following table clarifies the definitions of the different types of floor control in the context of this group:
Floor control | Type of multiparty session |
None e.g. everyone can talk to everyone simultaneously or at will | Without floor control |
By central entity e.g. Conference bridge or MCU | With central floor control |
Always by the same end user terminal | With central floor control |
Exchanged between end user terminals e.g. using a token | With distributed floor control |
This place does not cover:
Data switching systems for computer conference | |
Telephonic conference systems | |
Television conferencing systems |
A document describing both a multiparty session as well as details of services and applications covered by other entries, should be classified in the other entries also. For example, a document describing setting up a multi party call using SIP, originally between 3 parties, the floor control being exercised by the originating participant with a 4th participant being added during the session, should be assigned the following groups: H04L 65/1104 (SIP), H04L 65/1069 (setup), H04L 65/4038 (conference centrally controlled) and H04L 65/1093 (adding a participant).
Note: The Conference entries of H04L 65/403 relate mainly to the signalling for the setting up, maintenance and the floor control of the Conference session. Other general aspects of the Conference, e.g. handling group membership, etc. are normally covered by the H04L 12/18 group.
This place covers:
When the document explicitly describes a system/method with central floor control.
Attention is drawn to the following places, which may be of interest for search:
Data switching systems for conducting a computer conference, e.g. admission, detection, selection or grouping of participants |
This place covers:
When the document explicitly describes a system/method with distributed floor control as defined above.
This place covers:
When the document explicitly describes a system/method which has no floor control as defined above.
This place covers:
Signalling involved to prepare and setup a "Push-To" half duplex one-to-one or one-to-many call. It covers all "Push-to" services like Push-to-Talk (PtT), Push-to-Video (PtV) etc. A document describing a PtT over IMS service should normally be assigned this symbol and H04L 65/1016.
Attention is drawn to the following places, which may be of interest for search:
Push-to-talk services in wireless networks | |
Connection management, e.g. connection set-up, manipulation or release for push-to-talk or push-on-call services in wireless communication networks |
This place covers:
The manipulation, the handling and the transmission of the media content itself as opposed to the signalling associated with it. Note: the creation of the media content (e.g. converting the image information into digitalised MPEG frames, etc.) is covered by the H04N 7/00, H04N 21/00 and H04N 5/00 classes. This entry deals with encapsulation of the digitalised content into network packets, the network transport protocols governing the transmission of these content-carrying packets, and the processes involving the interaction of the content itself and the packets carrying this content with the network.
This parent class is only used if none of the explicit children subclasses below is suitable.
This place covers:
This entry covers services involving streaming of data from a source to a destination (downstream) and not vice-versa (upstream). It is noted that the notion of one-way streaming is not related to the actual ability of a terminal to also stream in the other direction, but only to the nature of the particular service. A document describing the broadcast streaming of media to terminals is normally covered by a H04L 65/61 – H04L 65/613 entry, even though the terminals may be capable to also stream media themselves to other destinations.
This place covers:
Media is streamed in the downstream direction from a source to multiple destinations (e.g. from a head-end server to subscriber terminals). Applications that may be covered include DVB-IP, some aspects of WEBcasting, etc. Aspects that are covered by this entry involve the packet streaming protocols, the packet-based signalling, the gatewaying etc. General aspects of TV broadcast are normally covered by H04N 7/00. The general aspects of data multicasting and broadcasting are normally covered by H04L 12/18.
This place does not cover:
Data switching systems for broadcast or conference | |
Arrangements for broadcast or distribution combined with broadcast | |
Arrangements for broadcast applications with a direct linkage of broadcast information | |
Selective distribution of broadcast services, e.g. multimedia broadcast multicast service [MBMS] |
Attention is drawn to the following places, which may be of interest for search:
Arrangements for push based network services | |
Analog television systems in general | |
Creating video channels for a dedicated end-user group |
This place covers:
Media is streamed in the downstream direction from a source to selected destinations which requested the media (e.g. from a head-end server to subscriber terminals). Applications that may be covered include on demand video streaming, etc. Aspects that are covered by this entry involve the packet streaming protocols, the packet-based signalling, the gatewaying, the possible session setup etc. General aspects of TV are normally covered by H04N 7/00.
Attention is drawn to the following places, which may be of interest for search:
Analog television systems using two way working | |
End-user applications for requesting content, additional data or services |
This place covers:
The subscriber terminal can control the way media is streamed by the source (e.g. streaming rate, pause, stop etc.). Applications that may be covered include VCR-like control of the source, etc. Aspects that are covered by this entry involve the packet protocols (e.g. RTSP), the packet-based signalling, the gatewaying, the possible session setup etc. General aspects of TV are normally covered by H04N 7/00.
This place does not cover:
Control signals to video servers issued by video clients |
Attention is drawn to the following places, which may be of interest for search:
End-to-end flow control in packet switching networks | |
Explicit feedback from the destination to the source to modify data rate for flow control or congestion control in packet switching networks, e.g. choke packet | |
Analog television systems using two way working |
This place covers:
All the protocols dedicated to the transmission and the control of the transmission of real time streaming content, including the full IETF RTP family of protocols (RTP, RTCP, RTSP).
Note: an RTP packet header extension, with details of the encoding of the header, may be classified both in H04L 65/70 and H04L 65/65.
This place covers:
Details of the encoding of the packet streams; e.g. the encapsulation of MPEG transports into RTP packets, multiplexing of RTP/UDP packets, RTP packet header compression (may also be covered by H04L 69/04), RTP header extensions, piggy-bagging executable code in the content carrying packets, etc. Note that the encoding of the media data itself (i.e. voice coding or image coding in MPEG) is not covered by H04L 65/00 but by H04N 7/00, H04N 21/00, H04N 5/00.
Attention is drawn to the following places, which may be of interest for search:
Protocols for data compression | |
Header parsing or analysis |
This place covers:
Manipulating, converting and adapting the content, in support of its transition through the network. For example, selecting a different codec for BW saving or for matching to the capabilities of the terminal, dropping a medium for BW saving or for matching to the capabilities of the terminal, selecting or switching to a lower resolution version of the content for BW saving, etc.
Attention is drawn to the following places, which may be of interest for search:
Computer conferences, network arrangements for conference optimisation or adaptation | |
Flow control or congestion control in packet switching networks | |
Message switching systems, e.g. electronic mail systems, with message adaptation based on network or terminal capabilities | |
Adaptation for terminals or networks with limited resources or for terminal portability | |
Network application being adapted for the location of the user terminal | |
Involving intermediate processing or storage in the network | |
Transmission of television signals using pulse code modulation |
This place covers:
The content handling takes place at the source.
This place does not cover:
Reformatting of additional data in video distribution servers |
Attention is drawn to the following places, which may be of interest for search:
Reformatting of video signals in video distribution servers |
This place covers:
The content handling takes place at the destination.
This place does not cover:
Reformatting of additional data in video clients |
Attention is drawn to the following places, which may be of interest for search:
Reformatting of video signals in video clients |
This place covers:
The content handling takes place at an intermediate node in the network.
This place covers:
Quality of Service, QoS, aspects related to real time Multimedia Communication in the context of H04L 65/00.
Documents classified into this group relate to specific QoS issues, irrespective as to whether these issues apply to a service, signalling, an entity, an application, etc. or to techniques which intend to support an improved user experience. The group is meant to be assigned as a qualifier to documents which may or may not have been assigned one of the other entries under H04L 65/00. As an example, a document describing the setting up of an audio and video call, and where during the call the available BW is continuously monitored and at a critical moment the video medium is dropped in order to preserve bandwidth, should be assigned the following entries:
H04L 65/1069 (Call setup), H04L 65/1089 (removing a medium) and H04L 65/80 (QoS).
The following aspects in real-time communication are considered examples falling under QoS:
Note that some of these techniques are known from other fields (e.g. monitoring (H04L 41/06), load balancing (H04L 67/1001), etc.) and are often also classified there. However if the technique is specifically adapted to real-time multimedia communication it is also classified here. Where applicable, the other fields are indicated below and are useful when searching for particular techniques.
- Content support streams
QoS technique whereby one or more additional and separate support streams to a content stream is/are transmitted in parallel, providing for an improved user experience.
- Buffering techniques (see also flow control H04L 47/10)
Techniques relating to buffer management in sender, receiver or intermediate node used in order to compensate for network deficiencies such as delay, jitter, etc.
- Alternate path routing (see also H04L 45/22 )
Techniques whereby during the streaming of content the stream is rerouted via an alternate path through the network when network problems such as congestion appear.
- Server arrangements
Arrangements and techniques at the server side for improving the QoS in real-time or near real-time services.
- Network infrastructure
Arrangements and techniques in the network, in terms of special network infrastructure entities, for improving the QoS in real-time or near real-time services.
- Redundant media transmission
Transmission of a redundant separate content stream in parallel, possibly using a different codec over a possibly alternate route in order to improve the reliability of the content delivery to the client; the redundant content streams cannot be added together.
- Multiple stream components
Content is streamed to a client using different sub-streams (sub layers) whereby one (bas layer) - or each separate sub-stream (sub-layer) on its own allows for playback of the content and whereby multiple sub-streams (sub-layers) can be added together and provide for an improved quality of the playback.
- Load balancing arrangements (see also H04L 67/1001)
Arrangements for load balancing in order to offload a server or a part of the network.
- Multiple Channel transmission (also in H04W)
Content stream is spread (dynamically) over multiple channels in a usually wireless access.
- Adaptive coding (see also H04L 47/38 )
The coding of the content stream is adjusted in real-time depending on the conditions of the network, the bandwidth availability or the client/server device.
- Alternate coding
Switching between different versions of the content depending on the conditions of the network, the bandwidth availability or the client/server device; whereby the different versions exist prior to the content transmission
- Content provider selection
Near real-time content provider selection for allowing optimal QoS experience.
- Adaptive rate selection
Dynamic transmission rate selection depending on the conditions of the network, the bandwidth availability or the client/server device, covers for example subsampling and upsampling.
- Scheduling
Near real-time techniques for timing the start of the transmission or playout of a stream depending on the conditions of the network, the bandwidth availability or the client/server device.
- Server resource optimisation
Improvements and techniques allowing for increased server side performance.
- Reducing required client resources
Improvements and techniques allowing for increased client side performance.
- Network bandwidth reduction
Improvements and techniques allowing for reduced network demand in terms of bandwidth.
- Measurement techniques (see also H04L 41/06)
Specific real-time measurement techniques supportive of QoS arrangements for multimedia communications.
- Timing and synchronisation techniques
Techniques for synchronization between different streams relating to a unique content experience and between different playback entities. Covers also solutions where timing issues are important.
- De-jittering (see also H04L 47/283 )
QoS aspects tackling jitter in particular.
Attention is drawn to the following places, which may be of interest for search:
Network service management, ensuring proper service fulfilment according to an agreement or contract between two parties, e.g. between an IT-provider and a customer | |
Monitoring arrangements, testing arrangements, with monitoring of QoS metrics | |
Traffic-type related flow control in packet switching networks, e.g. priorities or QoS | |
Admission control/resource reservation in packet switching networks based on QoS or priority awareness | |
Adaptation for terminals or networks with limited resources, or for terminal portability | |
Network application adapted for the location of the user terminal | |
Reducing the amount or size of exchanged application data | |
Arrangements for scheduling or organising the servicing of requests whereby quality of service or priority requirements are taken into account | |
Monitoring of the downstream path of a video distribution network |
This place covers:
- User-applications and protocols facilitating their access to the underlying network. Networking involves delays in the transmission of information between a sender and a receiver, which are normally physically/geographically at a distance from each other.
- Data presentation, preparation and transfer (e.g. via established sessions or transactions).
This place does not cover:
User-to-user messaging in packet-switching networks, transmitted according to store-and-forward or real-time protocols, e.g. e-mail | |
Network arrangements, protocols or services for supporting real-time applications in data packet communications networks |
Attention is drawn to the following places, which may be of interest for search:
Data switching networks | |
Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks | |
Routing or path finding of packets in data switching networks | |
Interprocessor communication | |
Information retrieval; Database structures therefor; File system structures therefor | |
Automatic or semi-automatic exchanges for telephonic communication providing special services or facilities to subscribers | |
Network structure or processes for video distribution between server and client or between remote clients | |
Services or facilities specially adapted for wireless communication networks |
This place covers:
Protocols for supporting directly end-user applications and processes (helping implement a network communication component by interacting with software applications; establishing a communication through the cooperating communication partners). Application layer services establish an interface to the network. "Protocols" provide the rules and formats that govern how data is treated.
This place covers:
Web applications that are accessed over a network and processed by a remote server.
This place covers:
Solutions supporting acquiring application data and processing or analysing the application data by the remote entity.
Attention is drawn to the following places, which may be of interest for search:
Network management using Internet technology | |
Network monitoring | |
Management of end-device applications over a special purpose or proprietor network |
This place covers:
Solutions specially adapted for terminals with restricted capabilities or functions (bandwidth, display, etc.).
Attention is drawn to the following places, which may be of interest for search:
Services or facilities specially adapted for wireless communication networks |
This place covers:
Aspects relating to data transfers/sharing using specific protocols therefor.
This place covers:
Solutions enabling a user to connect to a remote host or device by establishing a network connection.
Attention is drawn to the following places, which may be of interest for search:
Protocols for telewriting or protocols for networked simulations, virtual reality or games | |
Emulation or software simulation | |
Terminal emulation (relates to peripheral devices) |
This place covers:
The distribution of computing activities (distributed computing) in a network, when the networking aspects are relevant.
Sending active messages (i.e. e-mail messages that contain not only data or text, but also active components like executables, sometimes being those executables the ones that take responsibility for routing the message in the network, i.e. finding the nodes in which to execute).
Distributing the execution of an algorithm between nodes in the network, i.e. executing one version of the algorithm in a server, another in a light-weight client, and comparing/sharing the results.
Attention is drawn to the following places, which may be of interest for search:
Routing aspects of active messages, active routing, active networks | |
Routing of messages based on application data | |
Task transfer, task migration, mobile agents | |
Intertask communication | |
Remote procedure calls | |
Provisions for intelligent networking |
This place covers:
Documents involving a client-server (or peer-to-peer) communication in which, based on specific criteria, a decision is taken, either in the network or in the client, for selecting one of a plurality of replicated servers (or peers acting as servers) to provide a specific resource. The plurality of replicated servers are characterised by being able to provide basically the same content or service.
This definition is not limited to an interpretation of the term "server" as "content server", but also comprises the load balancing to other types of network elements such as caches or firewalls, under the condition that these elements can be seen as end points of a client connection (this excludes routers, gateways, switches, wireless switches, etc.).
Documents in this group are consequently characterised by two main aspects: Firstly, a plurality of replicated servers and secondly, a selection among the plurality of replicated servers.
Attention is drawn to the following places, which may be of interest for search:
Selection among a plurality of network devices that are routing or forwarding devices and not end points for the communication (this includes AP-Access Points, gateways, LNS-L2TP Network servers, Home Agents, MAP-Mobile Anchor Points) | |
Link or network selection, i.e. routing, based on load balancing in core network without involving a selection of a server among a plurality of replicated servers | |
Load balancing between the outbound interfaces (NICs) in a network device | |
DNS resolutions when a plurality of DNS servers are involved but these are not replicated servers | |
Authentication processes when a plurality of authentication servers are involved but these are not replicated servers | |
Arrangements for mirroring or replication of data | |
Redirection of requests when the plurality of servers are not replicated servers, and are therefore not meant to provide the same content or service | |
Routing according to the context/content of the requests when, if there is a plurality of servers, these are not replicated servers | |
QoS and priority requirements taken into account in the scheduling (or organisation or prioritisation) of requests prior to the forwarding or routing of the request to a server | |
Multichannel or multilink protocols; Load balancing between the outbound interfaces (NICs) in a network device | |
Selection of a printer among a plurality | |
Allocation of resources to service a request, the resource being a machine, e.g. a server | |
Allocation of resources, i.e. techniques for rebalancing the load in a distributed system |
The architectural aspects of applications related to selection of a server among a plurality of replicated servers are classified in the architectural subgroups of the intermediate processing group H04L 67/56.
Documents with the following additional aspects should be classified not only with their specific "selection among a plurality of servers" aspects but also in the following other groups:
- Monitoring and management of servers or networks: H04L 41/00, H04L 41/06
- Selection of an ISP through which a selected server among a plurality can be reached: H04L 12/2856
- Selection of network access among a plurality of available networks (PSTN, WLAN, ADSL, etc.) when a server among a plurality is also selected: H04L 12/5691
- Load balancing of DNS requests to a plurality of DNS servers when the load balancing is the main aspect of the application: H04L 61/50
- Load balancing of requests between a plurality of security devices such as firewalls, IDSs, SSL offload devices, etc.: H04L 63/00
- Load balancing of requests between a plurality of peers in a peer-to-peer network: H04L 67/104
- Load balancing of requests to servers that are part of a SAN: H04L 67/1097
- Session management: H04L 67/14
- Architectural implementation aspects of the load balancing intermediate functionality: H04L 67/56
- Failure recovery or redundancy of servers, where a backup server is selected among a plurality in case of failure of another server: H04L 69/40
This place covers:
Documents where the invention is characterised by the criteria for selection of a server out of multiple servers with replicated content.
Attention is drawn to the following places, which may be of interest for search:
Allocation of processing resources to service a request in a distributed system, the resource being a machine, e.g. a server |
This place covers:
Criteria for selection of a server are based on static selection. The same server is always selected for a specific client, independently of load changes (for example based on client's IP address).
Attention is drawn to the following places, which may be of interest for search:
Allocation of processing resources to service a request, considering data affinity |
This place covers:
Criteria for selection of a server are based on parameters of the plurality of servers (selection of server with least connections, more memory available, response time, least recently used, current workload, queue length, processing delay, power consumption, etc.).
This place does not cover:
Monitoring of computer activity |
Attention is drawn to the following places, which may be of interest for search:
Allocation of processing resources to service a request, considering the load |
This place covers:
Criteria for selection of a server are based on network conditions (access network load, bandwidth, network topology, least hops, round-trip delay, latency, etc.).
This place covers:
Criteria for selection of a server are based on compliance between predetermined requirements or conditions (either indicated in the client request or not, or in the form of thresholds) and the server's resources available (client's process requiring a percentage of memory, data rate, server capabilities, etc.).
This place covers:
Criteria for selection of a server are based on the content of a request (URL, client selects criteria and sends a request, host information).
This place covers:
Criteria for selection of a server are based on round-robin (circular or rotational) distribution of requests.
This place covers:
Criteria for selection of a server are based on random or heuristic selection.
This place covers:
Criteria for selection of a server are based on the location of the client or the server or the distance between client and server. It does not include the case of mathematical algorithms being used to calculate a number of hops (this belongs to network conditions).
Attention is drawn to the following places, which may be of interest for search:
Server selection based on network conditions |
This place covers:
Criteria for selection of a server are other criteria, e.g. hash applied to IP address, specific algorithms, cost, etc.
This place covers:
Dynamic adaptation of the selection criteria in load balancers. In order to adapt to changes in the network / server conditions, the criteria for selection of a server among the plurality of servers are changed for other criteria (e.g. from static selection to a load-based criteria) or the criteria's algorithm is modified.
This place covers:
Persistence means how to ensure that subsequent packets of a session or subsequent sessions established between a client and a server are forwarded to the same server as was the initial request (based on cookies, address affinity, etc.). This ensures consistency of information in the server, utility of client state information in the server, etc.
This place covers:
Collection and organisation of information related to the states of the plurality of servers by the load balancer wherein the information can be used in a later stage for selection of a server among the plurality.
Attention is drawn to the following places, which may be of interest for search:
Server selection based on server parameters | |
Performance measurement for load balancing | |
Information retrieval in structured data stores |
This place covers:
Management of replicated servers. By controlling operations of servers, e.g. adding or removing servers from the plurality of servers available for answering requests, the resources available to the clients can be controlled and a better performance can be achieved.
This place covers:
Continuity of service. Active monitoring of servers to react in case of failure of a server by balancing current requests and forwarding new requests to another available servers.
Attention is drawn to the following places, which may be of interest for search:
Network fault restoration | |
Departure and maintenance mechanisms in Peer-to-Peer networks | |
Intermediate processing of operational support to end devices when they are unavailable | |
Intermediate processing providing operational support to end devices by emulation or by off-loading in the network | |
Techniques for recovering from a failure of a protocol instance or entity | |
Error detection or correction of the data by redundancy in hardware | |
Failing over workload from one server to another one |
This place covers:
Load balancing of requests to replicated services for services different from user content provisioning, e.g. replicated DNS servers, replicated AAA servers, load balancing of firewalls, etc.
Attention is drawn to the following places, which may be of interest for search:
Ingress point selection, Internet Service Provider [ISP] selection | |
Domain Name Service DNS arrangements | |
Firewalls |
This place covers:
Arrangements to avoid the use of a single path through an intermediate load balancer for requests and/or replies between a client and a server, e.g., the load balancer selects a server among a plurality and communicates the selection to the client that can use this information to contact the server directly, or the load balancer provides a list of servers to the client that will then select one.
This place covers:
Documents describing specific functionalities, architectural details or applications of Peer to Peer (P2P) networks.
P2P networks are those which exhibit the following two characteristics:
- Symmetric Communication: Peer nodes act both as clients and as servers ("Servents"). Peer nodes are considered equals; they both request and offer resources, rather than being confined to either client or server roles.
- Self-Organization: The peer nodes automatically organize themselves into an application layer overlay network and adapt to the arrival, departure and failure of nodes.
Note: The academic definition feature "distributed control" is not considered because of the existence of P2P networks which make use of a node /some nodes which centralize certain functions in the p2p network (e.g. the central server of Napster; the "tracker nodes" of BitTorrent - on a "file per file" basis).
In relation with the note to the definition above, some degree of distributed arrangement of data is required by the hierarchy of the class under H04L 67/10.
Moreover its hierarchy under H04L 67/00 requires that it must involve the higher application layers (i.e. layers 5-7 of the OSI model).
Attention is drawn to the following places, which may be of interest for search:
Applications for Multicasting | |
Route fault recovery in network routing | |
Applications for Instant Messaging | |
Addressing aspects | |
Applications for distributed directory services | |
Security, e.g. countermeasures to security attacks, access control, authentication mechanisms | |
Applications for Streaming Media | |
Real-time terminal functionality | |
Real-time session setup | |
Real-time session control registration | |
SIP | |
One way streaming on demand | |
QoS aspects of Multimedia | |
Applications/Protocols for File Transmission | |
Applications for Distributed processing | |
Mechanisms to access one among a plurality of peers with the same content (i.e. selection) in a peer-to-peer network | |
Reactions to failures of replicated servers by a load balancer | |
Permanent content data storage at distributed nodes, e.g. replication, mirroring or in a storage area network | |
Applications for sensor networks | |
Presence management | |
Push based mechanisms | |
Temporary content data storage at intermediate nodes | |
Intermediate processing of operational support to end devices when they are unavailable | |
Scheduling (e.g. ordering) of responses to requests from different peers according to prioritising criteria | |
Techniques for recovering from a failure of a protocol instance or entity, e.g. failover routines, service redundancy protocols, protocol state redundancy, protocol service redirection in case of a failure, disaster recovery | |
Peer-to-peer connections between video game machines | |
Applications for games | |
Distribution of tasks among a plurality of processors inside a multiprocessor computer | |
Data backup, redundancy and recovery functionalities | |
Information search/organisation/retrieval where the proposal relates mainly to managed objects as cognitive information units rather than as physical peer nodes (e.g. keywords based search, contents oriented indexing instead of peers oriented indexing) | |
Applications for IP Telephony | |
Applications for wireless peers | |
Small Scale hierarchical wireless network topologies | |
Wireless Ad-hoc Networks involving group organisation only at OSI Layer 3 or lower (i.e. network routing) | |
Wireless interfaces between video clients |
In this place, the following terms or expressions are used with the meaning indicated:
BitTorrent | P2P protocol for file distribution. Defined by The BitTorrent Protocol Specification (http://www.bittorrent.org/beps/bep_0003.html). |
Distributed hash table (DHT) | Decentralized distributed system that provides a lookup service similar to a hash table; (key, value) pairs are stored in a DHT, and any participating node can efficiently retrieve the value associated with a given key. Responsibility for maintaining the mapping from keys to values is distributed among the nodes, in such a way that a change in the set of participants causes a minimal amount of disruption. |
Chunk | Fragments or pieces of information which are downloaded or managed by P2P programs. |
Leech | Primarily leech (or leeches) refer to a peer (or peers) who has a negative effect on the swarm by having a very poor share ratio (downloading much more than they upload, creating a ratio less than 1.0). Most leeches are users on asymmetric internet connections and do not leave their BitTorrent client open to seed the file after their download has completed. The often used second meaning of leech is synonymous with downloader: used simply to describe a peer or any client that does not have 100% of the data. This alternative meaning was mainly introduced by most BitTorrent tracker sites. |
Overlay network | Computer network built on top of another network. Nodes in the overlay can be thought of as being connected by virtual or logical links, each of which corresponds to a path, perhaps through many physical links, in the underlying network. |
P2P | Peer to Peer. |
Peer | A participant of a peer to peer network, in which participants act as both client and server. In BitTorrent, a peer is one instance of a BitTorrent client running on a computer on the Internet to which other clients connect and transfer data. Usually a peer does not have the complete file, but only parts of it. However, in the colloquial definition, "peer" can be used to refer to any participant in a swarm (in this case, it's synonymous with "client"). |
Peer to Peer network | Those networks which exhibit the following two characteristics: 1.- Symmetric Communication: Peer nodes act both as clients and as servers ("Servents"). Peer nodes are considered equals; they both request and offer resources, rather than being confined to either client or server roles. 2.- Self-Organization: The peer nodes automatically organize themselves into an application layer overlay network and adapt to the arrival, departure and failure of nodes. |
Seed / Seeder: | Peer that offers a piece of content for upload. In BitTorrent, a Seed is used to refer to a peer who has 100% of the data. When a leech obtains 100% of the data, that peer automatically becomes a Seed. |
Seeding: | Uploading content to other peers. In BitTorrent, Seeding refers to leaving a peer's connection available for other peers, i.e. leechers, to download from. Normally, a peer should seed more data than leech. However, whether to seed or not, or how much to seed, is dependent on the availability of leeches and the choice of the peer at the seeding end. |
Swarm | Group of peers downloading file pieces, in parallel, from several distinct sources or uploaders of the file. In BitTorrent, together, all peers (including seeders) sharing a torrent are called a swarm. For example, six ordinary peers and two seeders make a swarm of eight. |
Torrent | A torrent can mean either a .torrent metadata file (see next) or all files described by it, depending on context. Torrents work by dividing the target file into small information chunks, found on an unlimited number of different hosts. Through this method, torrents are able to download large files quickly. When a client (the recipient of a target file) has initiated a torrent download, the chunks of target file that are needed can be found easily, based on the data from the torrent itself. Once all the chunks are downloaded the client can assemble them into a usable form. |
Torrent file | A BitTorrent tracker is a server that assists in the communication between peers using the BitTorrent protocol. Clients that have already begun downloading also communicate with the tracker periodically to negotiate with newer peers and provide statistics; however, after the initial reception of peer data, peer communication can continue without a tracker. A tracker should be differentiated from a BitTorrent index by the fact that it does not necessarily list files that are being tracked. A BitTorrent index is a list of .torrent files, usually including descriptions and other information. Trackers merely coordinate communication between peers attempting to download the payload of the torrents. Many BitTorrent websites act as both tracker and index. Sites such as these publicize the tracker's URL and allow users to upload torrents to the index with the tracker's URL embedded in them, providing all the features necessary to initiate a download. |
This place covers:
Documents dealing with organisational aspects among peers that normally are established independently (although as a base) to the operations of specific resource search, selection and delivery covered in the other main groups.
This place covers:
Documents dealing with group formation and internal organisation mechanisms/rules.
This place does not cover:
management of multicast group membership | |
reconfiguring of node membership in a computing system to eliminate errors |
Attention is drawn to the following places, which may be of interest for search:
User group management in wireless communication networks |
This place covers:
Documents where a new peer wants to join an existing group. Includes Admission Control.
Attention is drawn to the following places, which may be of interest for search:
Network architectures or network communication protocols for network security, for controlling e.g. access |
This place covers:
Departure and maintenance mechanisms: Planned node departure (graceful disconnection); Due to node failure ("un"graceful disconnection); Responsiveness to node departures. Churn.
Attention is drawn to the following places, which may be of interest for search:
Reaction to server failures by a load balancer | |
Arrangements for providing operational support to end devices when they are unavailable | |
Techniques for recovering from a failure of a protocol instance or entity, e.g. failover routines, service redundancy protocols, protocol state redundancy, protocol service redirection in case of a failure, disaster recovery | |
Error detection or correction of the data by redundancy in operations |
This place covers:
Selection mechanisms of group master/leader/head for peer groups.
This place covers:
Pre-configuration of logical or physical "connections" (i.e. relationships) with a determined number of other peers (e.g. connection limits in a system of automatic message relay peers or preestablishment of trust relationships among peers).
This place covers:
Documents of H04L 67/1053 involving connection limits.
This place does not cover:
involving dynamic management of active down- or uploading connections |
For dynamically managing active "downloading" connections then use H04L 67/1085.
This place covers:
Documents of H04L 67/1053 involving pre-establishment or assessment of levels of trust among peers.
Attention is drawn to the following places, which may be of interest for search:
Cryptographic mechanisms or cryptographic arrangements for entity authentication | |
Supporting authentication of entities communicating through a packet data network |
For mere trust reinforcement techniques when exchanging contents like authentication with certificates then use H04L 63/08 and Indexing Code under H04L 67/1078.
This place covers:
Group splitting, groups merging, interconnection of groups.
This place covers:
Function of finding peer nodes able to provide a specific resource (thus not just for relaying purposes, which should be classified under Resource Distribution).
This place does not cover:
for accessing one among a plurality of replicated servers | |
Service discovery or service management |
Attention is drawn to the following places, which may be of interest for search:
Topology update or discovery | |
File systems | |
Information retrieval in structured data stores |
For selection mechanisms only this main entry to be given, as the selection details are meant to be classified under H04L 67/1006.The node discovery mechanisms are quite specific in the context of P2P and therefore they should not be classified under H04L 67/51 but with the subentries H04L 67/1063 - H04L 67/1065. Topology discovery for routing H04L 45/02.
This place covers:
Discovery through centralizing entities (e.g. NAPSTER and Trackers in BitTorrent).
This place covers:
Discovery involving distributed (in a structured way) pre-establishment of resource based relationships among peers; generally in so called structured P2P networks (e.g. based on Distributed Hash Tables).
This place does not cover:
pre-configuration of logical or physical connections |
This place covers:
Discovery involving direct consultation/announcement mechanisms among (potential) requesting and (potential) source peers and/or involving local (at the requesting peer) compilation of content source node(s) information; generally in so called unstructured P2P networks (e.g. Broadcast/flooding mechanism, and spontaneous advertising of new contents by a potential source node).
Aspects involving measurements of the response times of the query hits are to be classified also under H04L 67/1001 (generally under the network condition criteria subgroup of H04L 67/101).
This place covers:
Documents of H04L 67/1068 involving limitation/expansion of the discovery scope (Max number of hops or TTL of the queries/announcements).
This place covers:
Discovery involving (ranked) list compilation of candidate peers.
This place covers:
Resource dissemination/placing/storage, as well as resource delivery mechanisms. This group relates to the phase of actual exchange (and associated storage mechanisms) of resources.
This place does not cover:
File transfer arrangements or protocols |
Attention is drawn to the following places, which may be of interest for search:
Routing over an overlay routing layer |
This place covers:
Resource dissemination mechanisms and data keeping policies (not user request based or user subscription based mechanisms) for optimal resource availability in the overlay network (e.g. mechanisms to guarantee persistence of resources in a group; seeding mechanisms).
This place covers:
Documents characterized by the resource request/response delivery.
This place covers:
Documents characterized by the resource being split in blocks or fragments (e.g. sequence order for requesting missing blocks and performing integrity checks).
This place covers:
Documents involving incentive/rewarding/punishment schemes. Free riding avoidance. Tit for Tat.
Attention is drawn to the following places, which may be of interest for search:
Marketing, e.g. market research and analysis. |
This place covers:
Documents involving dynamic management of active (downloading/uploading) connections (e.g. traffic engineering).
This place covers:
Some other aspects that are not exclusively (i.e. mainly) under one of the main functional groups, are to be classified with entries under this header.
This place covers:
Topology showing a clear Hierarchy (i.e. tree structure).
This place covers:
Interfacing with client/server systems and between different P2P systems (e.g. some contents to be retrieved from a dedicated "external" server).
This place covers:
Limited number of peer nodes performing special functions.
This place covers:
Replication or mirroring arrangements between servers, or between user terminals (e.g. arrangements for synchronization of data between user terminals).
Attention is drawn to the following places, which may be of interest for search:
Caching arrangements in the network. | |
Backing up, restoring or mirroring files or drives. | |
Synchronization between mobile agents and networked agents. | |
Mass storage redundancy by mirroring for error detection or correction of data | |
Synchronisation in information retrieval in file systems | |
Synchronisation in structured data stores |
This place covers:
A Storage Area Network (SAN) is a sub-network of shared storage devices such as disk and tape. SANs provide high-speed, fault-tolerant access to data for client, server and host computing devices ("host computers").
Traditionally, computers were directly connected to storage devices, such that only the computer that was physically connected to those storage devices could retrieve data stored therein.
A SAN allows any computer connected to the SAN to access any storage device included within the SAN. As more storage devices are added to a SAN, they become accessible to any computer connected to the SAN. This access takes place at "block level" (as opposite to file level in NAS, Network Attached Storage).
Network Attached Storage, NAS, storage devices that provide access to storage at "file level".
Examples of protocols: iSCSI (internet Small Computer System Interface), RDMA (Remote Direct Memory Access).
Attention is drawn to the following places, which may be of interest for search:
Fibre Channel switches. | |
Temporary storage of data at an intermediate stage | |
Fibre Channel identifiers | |
Dedicated interfaces to storage systems | |
Storage system details, disk controllers, digital I/O to/from direct storage devices. | |
Resource allocation, load balancing | |
Error detection/correction, fault tolerance, RAID levels. | |
Addressing issues in Fibre Channel (computers) | |
DMA, Direct Memory Access | |
Fibre Channel bus (in computers) | |
Network Attached Storage, File Systems, File Servers. |
This place covers:
- Networks that are specially adapted for a specific application or networking environment, like vehicles, aircraft, medical, process control, factory control, mining, well drilling, patient monitoring, etc...
- Networks in which control information is transmitted, as opposed to plain data.
- Sensor networks or sensor/actuator networks, i.e. networks of devices that detect physical or measured values and convert them to data; and/or networks of devices that take data and convert it to physical control actions (e.g. activating an actuator).
- Networks for a particular technical environment, like vehicles or aircrafts.
- "Internet-of-things" or machine-to-machine communication M2M, i.e. networks for ubiquitous computing and networking of objects that communicate with each other.
Aircraft: B64; Vehicles: B60; Medical science: A61; Computers: G06F; Measuring, sensors: G01; Controlling, regulating: G05; Signalling: G08.
Wireless sensor networks (WSN), wireless ad-hoc networks whereby the invention lies in the special adaption of WSNs to wireless networks are classified in H04W 84/18.
Topology and routing aspects are classified in H04L 45/00.
Attention is drawn to the following places, which may be of interest for search:
Attention is drawn to the following places, which may be of interest for search, and where documents might have to be classified too (or exclusively):
Home automation networks | |
Peer-to-peer networks | |
Location based services | |
Medical science, diagnosis, transmitting measured data | |
(Computer or video) games interconnected with networks | |
Vehicles. Transmission of signals between vehicle parts or subsystems | |
Vehicles. Conjoint control of vehicle subunits | |
Aircraft. Control systems and transmission networks for actuating flight control surfaces, fly by wire | |
Aircraft. Arrangements for entertainment or communication in passenger or crew accommodation | |
Aircraft. Remote control and communication of/with unmanned aircraft, i.e. drones | |
Earth drilling. Transmitting measured signals | |
Seismology. Seismic prospecting. Transmitting seismic signals | |
Total factory control characterized by the network communication, i.e. interconnections of machines or factory elements by means of specialized networks | |
Aircraft. Flight control systems, i.e. automatic pilot | |
Digital data processing | |
Networks used to signal the maintenance condition of a vehicle; fleet management | |
Alarm systems, reporting the alarm via a telecom network | |
Traffic control systems for aircraft | |
Remote control of audio/video equipment (HiFi equipment) | |
Aircraft. Communications with or from aircraft; aeronautical mobile service | |
Telephonic communication in combination with telemetry, remote control systems, or alarm systems | |
Wireless sensor networks, self-organizing, ad-hoc |
Special networks as defined above should be classified both in H04L 67/12 and the application subgroups of H04L 67/00 they support.
Sensor networks in general are classified in H04L 67/12. Here the classification code is applied if the invention lies in a communications protocol specially adapted for the sensor network, e.g. particular leader/follower node hierarchy negotiations, messaging for dynamic network configuration, mutual power management.
This place covers:
Application layer functionality of controlling or monitoring end-devices over a network, in particular with special purposes or proprietary protocols.
Attention is drawn to the following places, which may be of interest for search:
Network management of network elements | |
Device control and monitoring using web-based technology | |
Network management of network elements |
This place covers:
Protocols for telewriting, networked virtual reality, and networked games.
Telewriting: the (remote) reproduction by means of a telecommunication system of the movements of a pointing device (for example a pen writing "electronic ink" into a digitizer tablet or a touch screen) in a remote display, in such a way as to transmit the handwriting of a user to a remote user. The information to be transmitted consists of the coordinates of the position of the pointing device and the movement vector, or similar representations of position and movement.
Networked virtual reality, networked simulation, networked games: transmitting to (remote) user device(s) the movements and interactions (i.e. shooting weapons in an aircraft combat simulation) of a 2D/3D representation of an entity (person, animal, vehicle, aircraft, avatar, etc...) in such a way that this entity can be represented in a display at the remote device, so as to enable the two (or more) users to interact with each other by means of the representation of the entity. The information to be transmitted here is more complex, and is dependent on the characteristics of the entity. It can include orientation, position, speed/velocity, rotation, acceleration, movement of sub-components of the entity (i.e. movement of an arm of a robot), interactions (i.e. shooting of weapons, change of colours, audio, voice, etc.).
The distinction between virtual reality, simulation or game is one of purpose of the interaction: in the networked simulation case the purpose is to teach the user in the control of an entity; in the networked games the purpose is entertainment. The devices used are classified in different places in the classification, see references below.
The protocols adapted to these kinds of applications are very specific, and contain a lot of application information in the protocol itself. For example, the transmission of packets to the participants in a simulation, which is of a multicast nature, is sometimes restricted to those objects for which the information is relevant: movements of a mobile out of sight of a participant (behind an obstacle or mountain, or very far away) are not relevant, and are thus not transmitted, to avoid congestion in the network.
Attention is drawn to the following places, which may be of interest for search:
Graphical user interfaces for network management | |
Games using an electronically generated display | |
Features of games characterised by details of network, like secure communication, wireless, internet, peer-to-peer, etc. | |
Digital output (from CPU) to display device | |
Digital output (from CPU) to display device, with simultaneous display of data in two or more (remote) display. | |
Remote windowing or X-Windows | |
Information retrieval from the internet (browsers), virtual worlds or virtual tours | |
Image processing, 2D image generation | |
Image processing: animation | |
Image processing: 3D image rendering | |
Image processing: 3D image modelling, i.e. data description of 3D objects | |
Coin-freed apparatus for playing games; Interconnected into groups; Casino-like gaming devices | |
Simulators for teaching or training purposes; For teaching control of vehicles; Aircraft (i.e. flight) simulators | |
Telephone sets including a gaming application |
This place covers:
Grouping messages in conversations. Forking conversations. Keeping track of conversations.
Attention is drawn to the following places, which may be of interest for search:
Remote procedure calls |
This place covers:
Monitoring/tracking a user's activity on a network.
Attention is drawn to the following places, which may be of interest for search:
Charging, metering or billing arrangements specially adapted for data communications | |
Network monitoring | |
Instant messaging | |
Creation/usage of user profiles | |
Presence management | |
Computers; monitoring of computer activity, of computer processes | |
Recording of computer activity | |
Databases; data mining | |
Synchronised browsing | |
Time management; calendars; reminders | |
Network management in voice network | |
Wireless; selective distribution; user group management |
This place covers:
Arrangements for dynamic session management between at least two endpoints in networks controlled for applications, whereby sessions are initiated (setup), identified, modified or ended (release) and involve a state of the session during the lifetime of the session.
A session is a sequence of interactions between two endpoints providing signalling and traffic processing control independent of the underlying network structure, and can have a beginning, and end and during its existence, a state. A session comprises at least one signalling message for beginning a session and, optionally, messages for modifying and/or ending the session. A session can be identified and a session state can be kept during the lifetime of sessions.
In general, this group does not cover sessions at OSI layers 2-4, e.g. fixed or wireless data network access, packet switching or routing, mobile IP provisions, wireless connections, telephonic connections. These are classified in H04L 12/28, H04L 12/56, H04L 12/46, H04W, H04L 69/163 and H04L 69/326.
This place does not cover:
Session management for real-time applications in data packet communications networks |
Attention is drawn to the following places, which may be of interest for search:
Data switching network | |
Arrangements and protocols for real-time communications | |
IP Multimedia Subsystem | |
In-session procedures in real-time communications | |
Session Initiation Protocol | |
Distributed applications | |
Access to replicated servers, e.g. loadbalancing | |
Push Services | |
Negotiation of communication capabilities | |
Intertask communication in multiprogramming arrangements for program control | |
Session management for telephonic communication and services | |
Services or facilities specially adapted for wireless communication networks | |
Control or signalling for completing the hand-off in wireless networks | |
Connection management in wireless networks, e.g. connection set-up, manipulation or release |
This group is a residual subgroup and covers session signalling at higher OSI layers to support networked applications.
Documents with the following additional aspects should get a second code in:
- Negotiation of communication capabilities: H04L 69/24
- Security aspects related to sessions, e.g. securing data, access control, exchange of credentials: subgroups of H04L 63/00
- OSI Layer 5, session layer, if the invention explicitly resides in Layer 5: H04L 69/327
- Services running on top of user sessions, service discovery: H04L 67/51
- Location based services in general: H04L 67/52
- Presence data management: H04L 67/54
- Push Services: H04L 67/55
- User profiles: H04L 67/306
- Distributed applications: H04L 67/10
- Location based services in wireless networks: H04W 4/02
This place covers:
Arrangements for the setup of a session which supports networked applications, e.g. using signalling messages.
This place does not cover:
Admission control or resource allocation in data switching networks |
Attention is drawn to the following places, which may be of interest for search:
Setup in session control in real-time multimedia communications |
This place covers:
Arrangements for managing the state of a session in stateless protocols, e.g. HTTP, by using cookies or dynamic URLs.
Attention is drawn to the following places, which may be of interest for search:
In-session procedures in real-time multimedia communications |
This place covers:
E.g. managing a session release.
Attention is drawn to the following places, which may be of interest for search:
ID based key exchange | |
Verifying the identity or authority of a user or a system, ID based authentication | |
IP multimedia subsystem | |
Assigning addresses to a networking function |
This place covers:
E.g. messages for inviting multiple participants to parallel sessions, the response messages indicating ability or non-ability for participation in parallel sessions.
Attention is drawn to the following places, which may be of interest for search:
In-session procedures in real-time communications | |
Control or signalling for completing the hand-off in wireless networks |
This place covers:
Architectural non-trivial arrangements characterised by the implementing details of the interprocessing function.
Examples are
- Implementation details of a single intermediate entity;
- Pairs of interprocessing entities at each side of the network, e.g. split proxies;
- Distributed intermediate devices, i.e. intermediate device interaction with other intermediate devices on the same level;
- Hierarchically arranged intermediate devices, e.g. hierarchical caching;
- Where the intermediate processing is functionally located closer to the data consumer application, e.g. in same machine, in same home or in same subnetwork;
- Where the intermediate processing is functionally located closer to the data provider application, e.g. reverse proxies; in same machine, in same cluster or subnetwork.
This place covers:
Intermediate entities with data processing functionalities (usually allowing light-weight implementations on communication endpoints).
This place covers:
Applications making use of the characteristics (attributes) of either a terminal or a user.
This place covers:
Applications related to characteristics of a terminal (e.g. processing or storage capabilities).
Attention is drawn to the following places, which may be of interest for search:
Allocation of resources considering hardware capabilities in multiprogramming arrangements | |
Client hardware characteristics in distribution of video content |
This place covers:
Applications related to characteristics of a user (e.g. past behaviour, preferences, demographics). Targeted advertisements based on user profiles are classified in G06Q 30/0269.
Attention is drawn to the following places, which may be of interest for search:
Targeted advertisement based on user profile or attribute |
This place covers:
The transmission of programs (i.e. pieces of executable software, as opposed to plain data), in the form of downloading or bootstrapping (i.e. transmitting the operating system and networking software from the network to a diskless workstation).
The transmission of components of a program like Java applets on request, i.e. when a certain function has to be executed at a workstation.
The customisation, parameterization or configuration of generic network elements, by downloading additional programs and/or data.
This place does not cover:
Remote booting |
Attention is drawn to the following places, which may be of interest for search:
Configuration of network and network elements. | |
Software download or update in routers. | |
Address allocation | |
Program loading or initiating. | |
Task transfer, task migration, mobile agents. | |
Cordless telephones; software upgrading or downloading. | |
Updating, downloading or transfer of parameters to mobile subscriber equipment. |
This place covers:
Network services (usually provided by a server component) that run on one or more computers (often a dedicated server computer offering multiple services) and are accessed via a network by client components running on other devices. However, the client and server components can both be run on the same machine.
This place covers:
Service management arrangements to discover, search and advertise network services (i.e. network resources as servers, printers, etc.).
That includes network arrangements and mechanisms to make clients aware of available network services or resources.
Attention is drawn to the following places, which may be of interest for search:
Service provisioning in data communication networks; Service Level Agreements, SLAs | |
Address allocation to terminals or nodes connected to a network | |
Selection of a specific server | |
Selection based on location | |
Selection based on QoS; on context, content | |
Mobile application services specially adapted for wireless communication networks | |
Wireless; Discovering of network services, e.g. terminals | |
Discovery of wireless access points |
This place covers:
Network applications in which the position of the user, either geographical position, or topological position in the network, is used as a parameter to activate a set of value added functions that generate position dependant information (for example, using the geographical position of the user to inform him of the restaurants or gas stations around him).
Attention is drawn to the following places, which may be of interest for search:
Navigation systems specially adapted for navigating in a road network (car navigation systems) | |
Position determining by GPS or similar systems, using radio waves | |
Geographical information databases | |
Location based Web retrieval | |
Telephonic communication terminals (i.e. phones) with means for adapting their capabilities according to geographical position | |
Location based services in a PBX (telephonic exchange) | |
Services making use of the location of users or terminals | |
Locating users or terminals in a mobile wireless (cellular) telecom network |
Attention is drawn to the following places, which may be of interest for search:
Charging, metering or billing arrangements specially adapted for data communications | |
Lawful interception | |
Tracking the activity of the user in network | |
E-commerce | |
Providing advertisement messages in voice networks | |
Charging for voice communications; Metering arrangements |
This place covers:
End user activity tracking/monitoring, e.g. behaviour (as opposite to monitoring of networks and network devices).
This place does not cover:
Network monitoring | |
Recording of computer activity |
Attention is drawn to the following places, which may be of interest for search:
Charging, metering or billing arrangements specially adapted for data communications | |
Multicast; management of group membership | |
Network management | |
Instant messaging | |
Monitoring a user's activity on a network | |
Creation/usage of user profiles | |
Presence management | |
Databases; data mining | |
Synchronised browsing | |
Time management; calendars; reminders | |
E-commerce | |
Network management in voice networks | |
Wireless; selective distribution; user group management |
This place covers:
Presence management, i.e. monitoring and registration of the log-on/connected status of users connected to data networks.
Attention is drawn to the following places, which may be of interest for search:
Use and manipulation of presence information in instant messaging | |
Tracking the activity of the user |
This place covers:
Push based network services.
Attention is drawn to the following places, which may be of interest for search:
Broadcast or multicast push services |
This place covers:
Arrangements involving intermediate processing and/or storage in the network, i.e. wherein additional processing of the application data is performed somewhere between the data provider and data consumer application.
Proxy servers.
Excluded from classification in H04L 67/56 are, in general, interprocessing provisions which, due to their specific use or purpose, are already covered by other groups:
- Interprocessing at OSI layers 1-4 (e.g. routing, addressing conversion, mobile IP provisions, etc.) is per definition out of the scope of H04L 67/56. This subject matter is classified in H04L 12/00, H04W.
- Third entities which are not involved during the active exchange of data between data provider and data consumer.
This place does not cover:
Store-and-forward switching systems |
Attention is drawn to the following places, which may be of interest for search:
Charging, metering or billing arrangements specially adapted for data communications | |
Network management | |
Monitoring provisions | |
Messaging system | |
Pure addressing functionalities | |
Security provisions | |
Proxies for network security | |
Multimedia call management network architectures | |
Media manipulation, adaptation or conversion in real-time communications | |
Mere presence of gateways performing its trivial functions, e.g. WAP gateways, WAP | |
Load balancing | |
Generic protocol conversion | |
Message passing systems or structures for intertask communication | |
Transcoding algorithms, e.g. MPEG conversions |
Documents with the following additional aspects should be classified not only with their specific interprocessing aspects but also in the following other groups:
- Data adaptation according to terminal reduced capabilities: H04L 67/04
- Permanent content data storage at intermediate nodes, e.g. replication, mirroring, in a storage area network: H04L 67/1095, H04L 67/1097
- Connection and session management: H04L 67/14
- Data adaptation according to location context: H04L 67/52
- Presence management: H04L 67/54
- Push services: H04L 67/55
- Data adaptation according to terminal profiles: H04L 67/303
- Data adaptation according to user profiles: H04L 67/306
- Routing according to the context/content of the requests: H04L 67/63
- Data backup, redundancy and recovery functionalities: H04L 69/40
This place covers:
Adding control or functional data, e.g. metadata. The intermediate processing consists in enhancing the functional value of the transmitted content; also in case of (partially) replacing the received content by content of more interest for the consumer application.
Attention is drawn to the following places, which may be of interest for search:
Protocols for client-server architecture | |
Negotiation of communication capabilities | |
E-commerce |
This place covers:
Providing redirection of requests for connection to a specified server or service, e.g. transparent proxying. A message that is initially sent by a first node and intended to a second node is redirected by said second node to a third node (either by resending the message by the second node or by providing the third node address to the first node).
Attention is drawn to the following places, which may be of interest for search:
Access network selection | |
Routing or path finding of packets | |
Addressing aspects | |
Load balancing requests | |
Context based routing |
When data redirection of data network streams involves service providers providing different services, in case of selecting the most efficient server to provide one specific service, then H04L 67/1001 should be used.
This place covers:
Evaluating intercepted data for data control, e.g. exploiting metadata for cache control, inferring and storing control or functional data, validation of requests.
This place covers:
Converting/adapting contents/formats according to the application format type, e.g. using an intermediate format, transcoding (transcoding proxy, transcoding cache proxy).
This place does not cover:
Arrangements for adding application control or application functional data |
Attention is drawn to the following places, which may be of interest for search:
Message adaptation based on network or terminal capabilities | |
Media manipulation, adaptation or conversion in real-time communications | |
Protocol conversion | |
Optimising visualisation of content for web browsing |
This place covers:
Intermediate processing aimed to reduce the exchanged application data, e.g. for distillation of contents for a small display terminal.
Attention is drawn to the following places, which may be of interest for search:
Protocols for data compression | |
Optimising visualisation of content | |
Digital video compression |
This place covers:
Grouping service requests for unified processing; a plurality of requests from consumer application(s) are correlated somehow and dealt together as intermediate processing, e.g. push/pull proxy (push proxy, push-pull proxy).
Attention is drawn to the following places, which may be of interest for search:
Networking arrangements or communication protocols for scheduling or organising the servicing of application requests |
This place covers:
Integrating various data provision/service applications to appear as one single front-end, e.g. web portals including servlets. Web portals are also classified in H04L 67/02. An intermediate application provides a multi-service or multi-provider experience to a consumer application by offering or integrating the provision of services from a plurality of background service providers.
Attention is drawn to the following places, which may be of interest for search:
Web portals | |
Redirecting requests to service providers | |
Web site content organisation and management |
This place covers:
Temporarily storing data at an intermediate stage, e.g. caching including:
- Caching involving pre-fetching or pre-delivering data;
- Managing the intermediate device storage space, e.g. policies for admission, Replacement, update, refresh, deletion;
- Caching involving storage of data provided by user terminals, i.e. reverse caching.
Attention is drawn to the following places, which may be of interest for search:
Distributed storage of data in a network | |
Addressing of a cache within a hierarchically structured memory system | |
Disk caching | |
Browsing optimisation of access to content by caching |
Attention is drawn to the following places, which may be of interest for search:
Cache prefetching within a hierarchical structured memory system |
Attention is drawn to the following places, which may be of interest for search:
Replacement control in memory systems |
This place covers:
The intermediate processing consists in taking over partially (i.e. off-loading) or temporally fully (i.e. when end terminal is unavailable) the tasks of an end node.
Attention is drawn to the following places, which may be of interest for search:
Terminal emulation | |
Reactions to server failures by a load balancer | |
Departure and maintenance mechanisms in Peer-to-Peer networks | |
Counter-measures to a fault | |
Emulation or software simulation | |
Input/output emulation function for peripheral devices | |
Disconnected operation in file systems |
This place covers:
The intermediate processing consists of failover where if the end device is unavailable, then tasks are off-loaded in the network.
Attention is drawn to the following places, which may be of interest for search:
Terminal emulation | |
Reactions to server failures by a load balancer | |
Departure and maintenance mechanisms in Peer-to-Peer networks | |
For recovering from a failure of a protocol instance or entity | |
Emulation or software simulation | |
Input/output emulation function for peripheral devices | |
Disconnected operation in file systems |
This place covers:
Management and scheduling of application requests.
This place does not cover:
Admission control or resource allocation |
Attention is drawn to the following places, which may be of interest for search:
Computer conference arrangements | |
Broadcast or conference with schedule organisation | |
Network service management, ensuring proper service fulfilment according to an agreement or contract between two parties | |
Intermediate grouping or aggregating of service requests |
This place covers:
Aspects of the user interface that have to do with networking, i.e. indicating to the user some network condition with a special user interface.
Cordless telephone, i.e. mobile user terminal.
Attention is drawn to the following places, which may be of interest for search:
Graphical user interfaces for network management | |
Terminal emulation, networking aspects | |
Pointing devices | |
Interaction techniques for user interfaces, menus, icons, windows | |
User interface programs, command shells, help systems, multi-language systems | |
Terminal emulation | |
Markup languages for text documents | |
Speech synthesis; text to speech conversion | |
Speech recognition | |
Cordless telephones for supporting an internet browser application | |
Interacting with a data network using a telephonic device, e.g. browsing the World Wide Web with a telephone |
This place covers:
Application independent communication protocols and their mechanisms, which are designed to operate over various link technologies with different characteristics.
Interconnection arrangements between CPUs, memories or peripherals within a single computer are classified in main group G06F 13/00.
Attention is drawn to the following places, which may be of interest for search:
Data switching networks | |
Broadcast or multicast | |
Network topologies, i.e. networks characterized by the path configuration, Media Access Control [MAC] | |
Hybrid switching systems | |
Gateways | |
Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks | |
Network monitoring or testing | |
Routing or path finding of packets in data switching networks | |
Flow control | |
Packet switches and switching fabrics | |
Intermediate storing or scheduling | |
User-to-user messaging in packet-switching networks, transmitted according to store-and-forward or real time protocols, e.g. e-mail | |
Interprocessor communication | |
Information retrieval; Database structures therefor; File system structures therefor | |
Transmission systems | |
Automatic or semi-automatic exchanges for telephonic communication providing special services or facilities to subscribers | |
Services or facilities specially adapted for wireless communication networks |
This place covers:
Protocol definition or specification, programming languages and methods specially adapted for the definition or specification of protocols.
This place does not cover:
Protocol definition or specification (protocol conformance testing) |
Attention is drawn to the following places, which may be of interest for search:
Protocol analysers | |
Program specification techniques | |
Specific high level programming languages |
This place covers:
Use of data compression to reduce the size of payload/header.
Attention is drawn to the following places, which may be of interest for search:
Reduction of the amount or size of exchanged application data at an intermediate network processing stage | |
Header parsing and analysis; compressing the header. | |
Data compression algorithms | |
Optimizing, e.g. header compression, information sizing in wireless communication networks |
This place covers:
Notations for structuring of protocol data.
Protocols and mechanisms like ASN.1 (Abstract Syntax Notation 1) which are used to convey meta information in a data stream, that is data about the syntactical and semantic structure of the data itself, self-describing constructs and so on, and the encoding mechanisms associated to them.
Computers, information retrieval: G06F 17/00.
Attention is drawn to the following places, which may be of interest for search:
Computers. Information retrieval of semi-structured data, like XML. | |
Conversion between different mark-up languages. | |
Markup languages for text documents |
This place covers:
Conversion between a protocol and another protocol.
Attention is drawn to the following places, which may be of interest for search:
Interconnection of networks | |
Inter-networking arrangements, interconnection of networks having different types of switching systems (i.e. connection oriented to connectionless), i.e. gateways | |
Network management protocols conversion | |
Addressing; mapping of addresses of different types; address resolution | |
Addressing; mapping of addresses of the same type; address translation | |
Multimedia communication; gateways | |
Multimedia communication. Media handling and conversion | |
Computers. Information retrieval. File format conversion. | |
Computers. Information retrieval. Conversion between semi structured data, i.e. between different mark-up languages |
This place covers:
Streamlined, light-weight or high-speed protocols, e.g. express transfer protocol [XTP], byte stream.
This place covers:
Specialized CPUs or hardware devices with an instruction set adapted for those operations that occur more in the implementation of protocols, like bit masking, shifting, comparisons, but no floating point operations.
Architectures involving multiple CPUs (multiple processor engines or processor cores), when these are used for data communication, i.e. for protocol processing.
This place covers:
Documents in which there exist multiple parallel channels or links between a sender and a receiver, to increase the bandwidth available or to increase the reliability of the communication.
Attention is drawn to the following places, which may be of interest for search:
Charging, metering or billing arrangements specially adapted for data communications | |
When a node is attached to two different networks (i.e. attached to the internet (packet switched), and to the PSTN (circuit switched)), and the information is sent to either one according to the nature of the information; network selection according to the information sent. | |
Routing; multiple paths in the network. | |
When the network or path selection is made according to the security characteristics of the information (i.e. sending credit card info through the PSTN, and the rest of the transaction through the internet). | |
Wireless; selecting a network. | |
Wireless; selecting an access point. | |
Wireless; mobile (cordless) phones (terminals) with two or more interfaces to different networks (802.11/ Wi-Fi® and GSM/GPRS/UMTS, or 802.11/ Wi-Fi® and Bluetooth®, for example); terminal devices adapted for operation in multiple networks; multi-mode terminals. |
This place covers:
Adaptations to the standard protocols of the TCP/IP or UDP/IP Internet protocol suite.
The standards for TCP/IP are published in a series of documents called Requests for Comments (RFCs). RFCs are an evolving series of reports, proposals for protocols, and protocol standards that describe the internal workings of TCP/IP and the Internet.
Layer 3 - Network
The Internetwork Protocol (IP) as the network layer interface is responsible for routing, directing datagrams from one network to another. The network layer may have to break large datagrams, larger than MTU, into smaller packets and host receiving the packet will have to reassemble the fragmented datagram.
Layer 4 - Transport
Transport layer subdivides user-buffer into network-buffer sized datagrams and enforces desired transmission control. Two transport protocols, Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), sits at the transport layer. Reliability and speed are the primary difference between these two protocols.
TCP establishes connections between two hosts on the network through 'sockets' which are determined by the IP address and port number. TCP keeps track of the packet delivery order and the packets that must be resent. Maintaining this information for each connection makes TCP a stateful protocol.
UDP on the other hand provides a low overhead transmission service, but with less error checking.
Attention is drawn to the following places, which may be of interest for search:
Flow control in data switching networks in general | |
Special adaptations of TCP, UDP or IP for interworking of IP based networks with other networks | |
Transport layer addressing aspects | |
Adapting video multiplex streams to a specific network | |
Network layer protocol adaptations for supporting mobility, e.g. mobile IP |
The mere use of the TCP/IP, UDP protocol suite for implementing communication based applications/services is not classified under this subgroup.
This group is a protocol-centric classification entry for a broadly used protocol in packet data networks. Some of the functions carried out by said protocol are classified generically somewhere else. In these cases, double classification is performed according to the function and to the specific protocol.
In this place, the following terms or expressions are used with the meaning indicated:
TCP | Transmission Control Protocol; RFC 793 – Transmission Control Protocol |
IP | Internet Protocol ; RFC 791 – Internet Protocol ; RFC 2460 – Internet Protocol, Version 6 (IPv6) Specification |
UDP | User Datagram Protocol; RFC 768 – User Datagram Protocol; RFC 4113 – Management Information Base for the UDP; RFC 5405 – Unicast UDP Usage Guidelines for Application Designers |
OSI | Open System Interconnection; standard model for networking protocols and distributed applications; ISO standard for worldwide communications that defines a networking framework for implementing protocols in seven layers. Control is passed from one layer to the next, starting at the application layer in one station, proceeding to the bottom layer, over the channel to the next station and back up the hierarchy. |
This place covers:
Arrangements to implement the TCP, UDP or IP protocols at network nodes (mainly at end terminals) and proposed modifications of the TCP, UDP or IP protocol headers to enhance or improve the protocol functionalities.
Attention is drawn to the following places, which may be of interest for search:
Protocol engines in general | |
Protocol header analysis in general | |
OSI stack based layering aspects | |
Specification of modified or new header fields protocols engines in general |
TCP, UDP and IP protocol implementation aspects are classified in this subgroup and in H04L 69/12. TCP, UDP and IP headers aspects are classified in this group and in H04L 69/22.
This place does not cover:
Secure socket layer |
Attention is drawn to the following places, which may be of interest for search:
Application session management for sessions established over TCP/UDP sockets |
This place covers:
Control procedures for all functions performed by the TCP transport protocol, e.g. flow control and error control. Only TCP specific mechanisms.
Attention is drawn to the following places, which may be of interest for search:
Error control procedures in general | |
TCP or UDP flow control procedures | |
Generic OSI layer 4 protocols (if not classified somewhere else), e.g. SCTP |
TCP specific flow control mechanisms are classified in this subgroup and in H04L 47/19 . TCP specific error control mechanisms are classified in this group and in H04L 1/18.
This place covers:
UDP related aspects and non-trivial use of the UDP protocol.
Attention is drawn to the following places, which may be of interest for search:
Combined or selective use of TCP and UDP |
This place covers:
Simultaneous use of the two protocols or selective use of one of them according to some criteria.
Attention is drawn to the following places, which may be of interest for search:
Multilink protocols in general | |
Multi-protocol arrangements in general |
This place covers:
Special arrangements involving IP fragmentation or TCP segmentation.
Attention is drawn to the following places, which may be of interest for search:
Evaluation of maximum transfer unit (MTU) | |
Assembly or disassembly of packets in wireless networks |
This place covers:
Arrangements to allow transitional interoperability between IPv4 and IPv6 protocols.
This place does not cover:
Translation of internet protocol [IP] address |
Attention is drawn to the following places, which may be of interest for search:
Involvement of different protocol versions in wireless network layer protocols, e.g. MIPv4 and MIPv6 |
In patent documents, the following abbreviations are often used:
IPng | alternative designation for IPv6 |
This place covers:
Provisions to improve interrelation between TCP, UDP or IP and the lower layer protocols carrying them. Provisions being either at the TCP, UDP, IP or at the carrier protocol.
Attention is drawn to the following places, which may be of interest for search:
IP fragmentation and TCP segmentation | |
OSI Layer 2 protocol provisions in general | |
IP over ATM | |
Special adaptation of TCP protocol for wireless media |
This place covers:
Interworking arrangements to allow/enhance interoperability between TCP, UDP or IP protocols and other network protocols, e.g. SS7.
It does not cover mere inter-networking scenarios without special protocol adaptations (i.e. standard gateway provisions).
This place does not cover:
Protocols for interworking , protocol conversion |
Interworking/conversion between TCP,UDP or IP protocols and other network protocols is classified in this subgroup and in H04L 69/08.
This place covers:
Network nodes, Network Interface Cards (NIC) capable of handling more than one protocol; or where the protocol can be dynamically adapted.
Attention is drawn to the following places, which may be of interest for search:
Charging, metering or billing arrangements specially adapted for data communications | |
When a node is attached to two different networks (i.e. attached to the internet (packet switched), and to the PSTN (circuit switched)), and the information is sent to either one according to the nature of the information; network selection according to the information sent | |
Routing; multiple paths in the network | |
Multilayer or multiprotocol switches | |
When the network or path selection is made according to the security characteristics of the information (i.e. sending credit card info through the PSTN, and the rest of the transaction through the internet) | |
Downloading of software, including protocol functionality | |
Wireless; selecting a network | |
Wireless; selecting an access point | |
Wireless; mobile (cordless) phones (terminals) with two or more interfaces to different networks (802.11/ Wi-Fi® and GSM/GPRS/UMTS, or 802.11/ Wi-Fi® and Bluetooth®, for example); terminal devices adapted for operation in multiple networks; multi-mode terminals |
This place covers:
- Parsing and analysis of the of the information contained in the packet headers, within the network adapter (NIC), but also within the routers;
- Prediction of the contents of the header within the same stream;
- Header compression;
- Simplified header processing;
- Packet classification;
- Separating the header from the rest of the packet, for more efficient handling;
- High speed memories to place the header.
Attention is drawn to the following places, which may be of interest for search:
Traffic monitoring by flow aggregation or filtering | |
Separate storage for different parts of the packet, e.g. header and payload | |
Protocols for data compression; header compression | |
Wireless; optimizing, header compression |
This place covers:
Negotiation of communication capabilities, like communication bandwidth, speed, common protocol or protocol version, etc..., at call set-up or during the communication.
Attention is drawn to the following places, which may be of interest for search:
Multimedia communications. Session control; session set-up; in-session procedures | |
Multimedia communications. Signalling or session protocols | |
Arrangements for connection and session management, call setup | |
Arrangements for service discovery |
This place covers:
Special purpose or proprietary protocols or architectures.
This place does not cover:
Network applications for proprietary or special purpose networking environments |
This place covers:
Timer mechanisms used in protocols.
This place covers:
Definitions, standards or architectural aspects of layered protocol stacks.
Interfaces between layers (i.e. vertical interfaces across the protocol stack, between layer n and layer n+/-1).
Offloading or shifting processing that belongs to one layer to another layer, or from the host processor to the network adapter, network interface card.
Interfaces between the protocol stack and the operating system software (i.e. device drives for networking).
General documents about layering.
General documents about OSI standards.
Multiplexing/demultiplexing of several layer n connections into one layer (n-1) connection.
Attention is drawn to the following places, which may be of interest for search:
Data storage and handling aspects for data "in transit" between the network and the host. The functions classified here are normally physically located in what is known as network adapter, network interface unit, or network card. This group contains functions like buffering of data in the network adapter, data descriptors, input and output queues, priority queues, signalling between the network adapter and the host (like interrupt generation and handling when a packet is received, early warning interrupts, and so on) | |
The TCP/IP protocol stack | |
Computers. Operating Systems. Inter-task communication | |
Computers. Interconnection or transfer of information between memories, I/O devices, and CPUs | |
Program control for peripheral devices, i.e. device drivers | |
Direct Memory Access (DMA); burst mode transfer | |
Inter-processor communication in combinations of two or more computers, using an interconnection network | |
Multiplexing in general |
This place covers:
High level architectural aspects of 7-layer Open Systems Interconnection (OSI) type protocol stacks.
This place covers:
Aspects of inter-layer communication protocols or Service Data Unit (SDU) definitions in 7-layer Open Systems Interconnection (OSI) type protocol stacks; Interfaces between layers.
This place covers:
Aspects of intra-layer communication protocols among peer entities or Protocol Data Unit (PDU) definitions in 7-layer Open Systems Interconnection (OSI) type protocol stacks.
This place covers:
The protocols of the 1st layer of the ISO-OSI model, that is, the Physical Layer.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for detecting or preventing errors in the information received | |
Baseband systems | |
Modulated carrier systems |
This place covers:
The protocols of the 2nd layer of the ISO-OSI model, that is, the Link Layer.
The framing of packets (delimiting of the start and the end of the packet).
Generation and checking of CRCs.
Segmenting and reassembling of (variable length) packets in shorter (either fixed or variable length) cells or transmission units.
Sequencing the packets (i.e. generating identifiers like sequence numbers at the sender, and ordering them in a particular sequence at the receiver).
Checking for missing packets, acknowledging received packets, resending packets after a time interval when no acknowledge is received.
Attention is drawn to the following places, which may be of interest for search:
Arrangements for detecting or preventing errors in the information received | |
Bus networks | |
Loop networks | |
Star networks | |
Flow control | |
Wireless networks |
This place covers:
The protocols of the 3rd layer of the ISO-OSI model, that is, the Network Layer.
This place does not cover:
Transmission Control Protocol/Internet Protocol, TCP/IP |
Attention is drawn to the following places, which may be of interest for search:
Packet switching systems, packet routing |
This place covers:
The protocols of the 4th layer of the ISO-OSI model, that is, the Link Layer.
Generation and checking of CRCs.
Segmenting and reassembling of (variable length) packets in shorter (either fixed or variable length) cells or transmission units.
Sequencing the packets (i.e. generating identifiers like sequence numbers at the sender, and ordering them in a particular sequence at the receiver).
Checking for missing packets, acknowledging received packets, resending packets after a time interval when no acknowledge is received.
This place does not cover:
Transmission Control Protocol/Internet Protocol, TCP/IP |
Attention is drawn to the following places, which may be of interest for search:
Streaming protocols, e.g. RTP |
This place covers:
The protocols of the 5th layer of the ISO-OSI model, that is, the Session Layer.
Attention is drawn to the following places, which may be of interest for search:
Session control in real time communications | |
Session Initiation Protocol [SIP] | |
Arrangements for session management |
This place covers:
The protocols of the 6th layer of the ISO-OSI model, that is, the Presentation Layer.
Attention is drawn to the following places, which may be of interest for search:
Terminal emulation, e.g. Telnet | |
Graphical user interface |
This place covers:
This entry has been created for completeness. Documents about the 7th layer of the ISO-OSI model are classified in H04L 67/00
Networked applications: H04L 67/00
Digital data processing: G06F
Data processing systems and methods specially adapted for administrative, commercial, financial or managerial purposes G06Q
Attention is drawn to the following places, which may be of interest for search:
Network arrangements or network communication protocols for networked applications | |
Data processing systems and methods specially adapted for administrative, commercial, financial or managerial purposes |
This place covers:
Techniques for recovering from failure of a protocol instance or entity, e.g. failover routines, service redundancy protocols, protocol state redundancy, protocol service redirection in case of failure, disaster recovery.
This place does not cover:
Network fault management |
Attention is drawn to the following places, which may be of interest for search:
Route fault recovery in network routing | |
Fault recovery in packet switches | |
Reactions to failures of replicated servers by a load balancer | |
Departure or maintenance mechanisms in Peer-to Peer networks | |
Intermediate processing of operational support to end device when they are unavailable |
This place covers:
Details of addressing and naming in data networks, such as aspects relating to different types or formats of addresses and names.
H04L 2101/00 is an indexing scheme associated with main group H04L 61/00. Accordingly, documents classified in H04L 61/00 should also have the relevant indexing codes of H04L 2101/00 applied to identify the types of network names or network addresses disclosed.
Attention is drawn to the following places, which may be of interest for search:
Network architectures or network communication protocols using hop-by-hop encryption |
Attention is drawn to the following places, which may be of interest for search:
Security arrangements; Authentication; Protecting privacy or anonymity |
Attention is drawn to the following places, which may be of interest for search:
Generation of secret information including derivation or calculation of cryptographic keys or passwords |
Attention is drawn to the following places, which may be of interest for search:
Key transport or distribution using key encryption key |
Attention is drawn to the following places, which may be of interest for search:
Generation of secret information including derivation or calculation of cryptographic keys or passwords |
Attention is drawn to the following places, which may be of interest for search:
Arrangements for secret or secure communications including means for verifying the identity or authority of a user of the system |
Attention is drawn to the following places, which may be of interest for search:
Data processing systems specially adapted for commerce |
Attention is drawn to the following places, which may be of interest for search:
Data processing systems specially adapted for commerce |
Attention is drawn to the following places, which may be of interest for search:
Protecting distributed programs or content, e.g. vending or licensing of copyrighted material | |
Payment architectures, schemes or protocols | |
Analogue secrecy systems; Analogue subscription systems |
Attention is drawn to the following places, which may be of interest for search:
Cryptographic arrangements including means for verifying the identity or authority of a user of the system involving time stamps |