| CPC H04L 63/1416 (2013.01) [G06N 5/025 (2013.01); G06N 5/04 (2013.01); H04L 63/1433 (2013.01); H04L 63/1466 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A method for protecting computing assets in a protected computing environment, the method comprising:
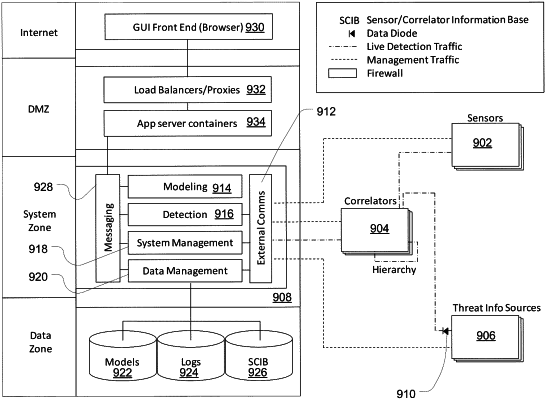
detecting a set of events associated with an originator using a set of event sensors, wherein the originator is a monitored resource in the protected computing environment;
comparing, using an inference server in communication with the set of event sensors, the detected set of events to a detection model, the detection model including an event lattice, the event lattice including a set of event nodes and a set of nodes linked to event nodes of the set of event nodes, each node having a node position corresponding to events sensed by the event sensors;
determining a pattern of behavior indicative of an attack on the computing assets based on the comparing; and
communicating, using the inference server, an identifier associated with the originator.
|