| CPC G06F 21/575 (2013.01) [G06F 21/572 (2013.01); H04L 9/0825 (2013.01); H04L 9/3073 (2013.01); H04L 9/3247 (2013.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
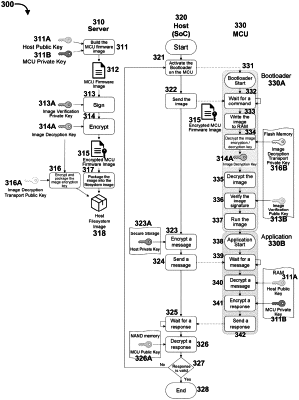
13. A non-transitory processor-readable medium storing code representing processor-executable instructions to cause the one or more processors to:
receive, at a bootloader of a system on chip (SoC), an encrypted symmetric encryption key and an encrypted signed firmware image,
the encrypted symmetric encryption key being a symmetric encryption key,
the encrypted signed firmware image (1) being a signed firmware image encrypted with the symmetric encryption key and (2) including a first encryption public key and a first encryption private key;
the signed firmware image being a firmware image digitally signed with a second encryption private key;
decrypt the encrypted symmetric encryption key to produce the symmetric encryption key using a third encryption private key that is included in an asymmetric key pair that includes the second encryption public key;
decrypt the encrypted signed firmware image to produce the signed firmware image using the symmetric encryption key;
verify a digital signature of the signed firmware image using a third encryption public key that is included in an asymmetric key pair that includes the second encryption private key; and
execute, after verifying the signed firmware image, the firmware image.
|