| CPC H04L 9/0894 (2013.01) [G06F 21/604 (2013.01); H04L 9/085 (2013.01); H04L 9/14 (2013.01); H04L 9/3218 (2013.01)] | 18 Claims |
|
1. A system, comprising:
a first client device comprising a processor and a memory; and
machine readable instructions stored in the memory that, when executed by the processor, cause the first client device to at least:
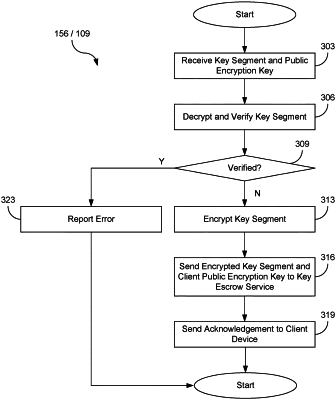
receive a first version of an encrypted key segment from a second client device, the first version of the encrypted key segment being a key segment of the second client device encrypted with a first public key associated with the first client device;
decrypt the first version of the encrypted key segment using a first private key associated with the first public key to generate the key segment;
verify the key segment using a second public key associated with the second client device;
encrypt the key segment with the first public key to regenerate the first version of the encrypted key segment in response to verification of the key segment; and
send a regenerated first version of the encrypted key segment to a key escrow service.
|