| CPC H04L 9/0869 (2013.01) [G06F 21/602 (2013.01); G09C 1/00 (2013.01); H04L 9/088 (2013.01); H04L 9/0861 (2013.01); H04L 9/0891 (2013.01); H04L 9/14 (2013.01); H04L 9/3213 (2013.01); H04L 63/0435 (2013.01); H04L 63/10 (2013.01); H04L 9/0618 (2013.01); H04L 2209/04 (2013.01)] | 20 Claims |
|
1. A one-to-many symmetric cryptographic system, comprising:
a central location being in communication with at least one remote location;
the central location having a memory having computer executable instructions stored thereon for execution by a processor, causing the processor to:
receive a document from said at least one remote location; and
provide the document to a cryptographic module for encryption, comprising:
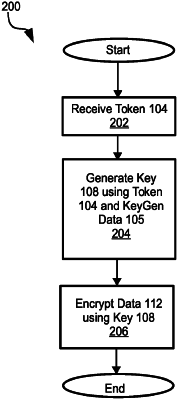
receiving a token;
performing a walk through an entropy space, which is a large set of random bits, to fetch a string of bits, the walk through and the fetched string of bits depending on the token;
generating a secret key for encrypting the document based on the fetched string of bits, thereby generating an encrypted document; and
destroying the secret key upon encrypting the document;
the computer executable instructions further causing the processor to provide the encrypted document to the cryptographic module for decryption, comprising:
receiving the token;
performing the walk through the entropy space to fetch the string of bits; and
generating the secret key for decrypting the encrypted document based on the fetched string of bits;
thereby avoiding storing or communicating the secret key.
|