| CPC H04L 63/1466 (2013.01) [H04L 9/0643 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01)] | 8 Claims |
|
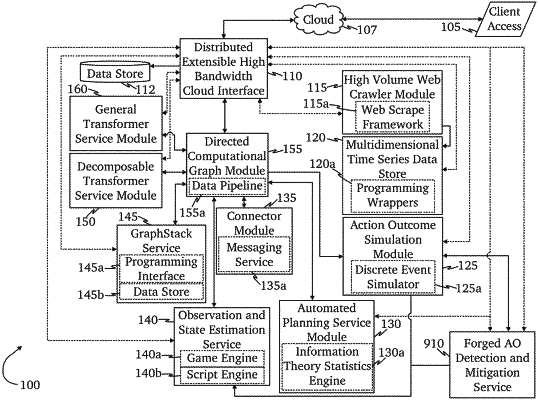
1. A system for detecting and mitigating attacks using forged authentication objects within a domain, comprising:
a computing device comprising a memory and a processor;
an authentication object inspector comprising a plurality of programming instructions stored in the memory which, when operating on the processor, causes the computing device to:
receive a plurality of first authentication objects known to be generated by an identity provider associated with an authentication domain;
store a record of each received first authentication object, with attached metadata comprising a timestamp of when each first authentication object was received, in a time-series database;
calculate an authentication object identifier for each first authentication object;
store the authentication object identifier of each first authentication object in a database of authentication object identifiers for the identity provider;
receive a request for access to a network resource associated with the authentication domain accompanied by a second authentication object;
calculate an authentication object identifier of the second authentication object;
compare the authentication object identifier of the second authentication object with the authentication object identifiers of the first authentication objects stored in the database of authentication object identifiers to determine whether the authentication object identifier of the second authentication object already exists in the database of authentication object identifiers;
where the authentication object identifier of the second authentication object does not exist in the database of authentication object identifiers, generate a notification that the identity provider may be compromised.
|