| CPC H04L 63/145 (2013.01) [G06F 21/56 (2013.01); G06N 20/00 (2019.01); H04L 63/1416 (2013.01)] | 20 Claims |
|
1. A computer program product comprising computer executable code embodied in a non-transitory computer readable medium that, when executing on one or more computing devices, performs the steps of:
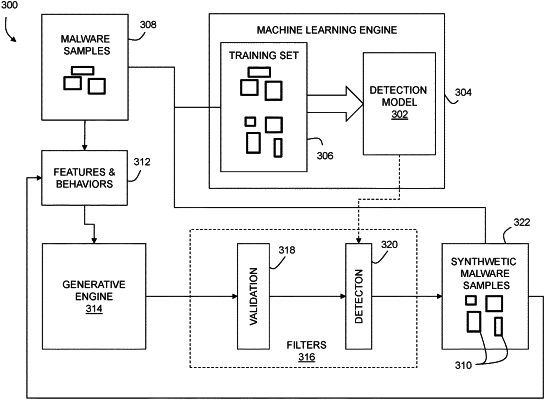
providing a first training set including a plurality of malware samples;
configuring a first antimalware system to detect the malware samples;
characterizing one or more functional blocks of the malware samples by extracting abstracted features, functions, or behaviors of the malware samples to provide characterizations of the one or more functional blocks;
generating a first number of synthetic malware samples including modifications of the one or more functional blocks of the malware samples based on the characterizations;
validating the first number of synthetic malware samples to provide a validated sample set containing one or more of the first number of synthetic malware samples that execute and perform an unwanted task in a target computing context;
filtering the validated sample set to provide a filtered sample set containing one or more of the first number of synthetic malware samples in the validated sample set that are not detected by the first antimalware system;
creating a second antimalware system by training a machine learning malware detection engine to detect malicious code including the one or more of the first number of synthetic malware samples in the filtered sample set;
repeating one or more of generating, validating, filtering, or training until a predetermined threshold for positive detection by the second antimalware system is reached; and
deploying the second antimalware system on an endpoint.
|