| CPC H04L 63/1441 (2013.01) [G06N 3/044 (2023.01); G06N 3/084 (2013.01); G06N 5/02 (2013.01); G06N 5/043 (2013.01); G06N 20/00 (2019.01); G10L 15/26 (2013.01); H04L 63/10 (2013.01); H04L 63/1408 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1483 (2013.01); H04L 67/306 (2013.01); H04W 12/08 (2013.01); H04W 12/12 (2013.01); H04W 4/21 (2018.02); H04W 12/67 (2021.01)] | 20 Claims |
|
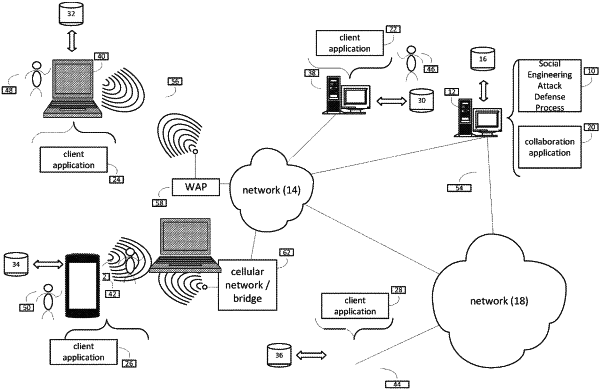
1. A computer-implemented method comprising:
identifying, by a computing device, a first characteristic of a first communication received on a first communication channel, wherein the first characteristic is determined based upon, at least in part, a first set of text in the first communication and sent on the first communication channel;
identifying a second characteristic of a second communication received on a second communication channel, wherein the second characteristic is determined based upon, at least in part, a second set of text in the second communication and sent on the second communication channel, wherein both the first communication channel and the second communication channel are different communication platforms;
comparing, with a rule, both the first characteristic of the first communication received on the first communication channel and the second characteristic of the second communication received on the second communication channel;
determining that both the first characteristic of the first communication received on the first communication channel and the second characteristic of the second communication received on the second communication channel correlates to the rule by performing an assessment of the first set of text in the first communication and the second set of text in the second communication compared to at least one of malicious or non-malicious communications; and
identifying activity that is potentially social engineering activity associated with at least one of the first communication or the second communication based upon, at least in part, correlating both the first characteristic of the first communication received on the first communication channel and the second characteristic of the second communication received on the second communication channel to the rule.
|