| CPC H04L 63/1441 (2013.01) [G06F 18/213 (2023.01); G06F 18/217 (2023.01); G06F 18/2148 (2023.01); G06F 18/2415 (2023.01); G06N 5/04 (2013.01); G06N 20/00 (2019.01)] | 20 Claims |
|
1. A method, comprising:
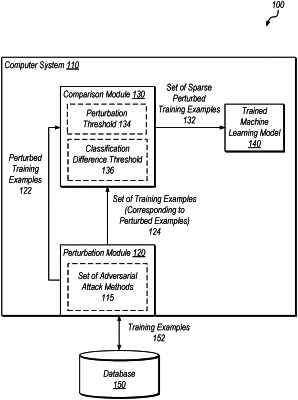
perturbing, by a computer system using a set of adversarial attack methods, a set of training examples used to train a machine learning model;
identifying, by the computer system from among the perturbed set of training examples, a set of sparse perturbed training examples that are usable to train machine learning models to identify adversarial attacks, wherein the set of sparse perturbed training examples includes examples whose perturbations are below a perturbation threshold and whose classifications satisfy a classification difference threshold; and
retraining, by the computer system using the set of sparse perturbed training examples, the machine learning model.
|