| CPC H04L 63/1433 (2013.01) [G06F 8/65 (2013.01); H04L 41/22 (2013.01); H04L 63/20 (2013.01)] | 16 Claims |
|
1. A system, comprising:
one or more hardware processors; and
a non-transitory memory storing instructions that, when executed by the one or more hardware processors, causes the one or more hardware processors to perform actions comprising:
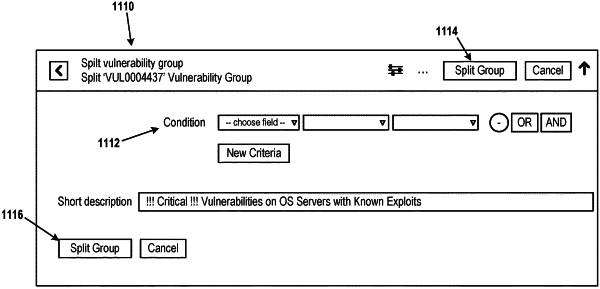
storing an indication of a vulnerability group of a managed network, wherein the vulnerability group comprises one or more hardware or software components of the managed network, and wherein the vulnerability group identifies one or more vulnerabilities of the one or more hardware or software components;
receiving a command to split the vulnerability group into a first vulnerability group and a second vulnerability group based on a filter expression, wherein the first vulnerability group comprises a first subset of the one or more hardware or software components that match the filter expression, wherein the second vulnerability group comprises a second subset of the one or more hardware or software components that do not match filter expression;
receiving one or more inputs defining a first change request related to only the first vulnerability group and a second change request related to only the second vulnerability group;
generating the first change request and the second change request based on the received one or more inputs;
storing a first association of the first change request with the first vulnerability group; and
storing a second association of the second change request with the second vulnerability group.
|