| CPC H04L 63/1425 (2013.01) [G06F 40/226 (2020.01); G06F 40/242 (2020.01); G06F 40/289 (2020.01); G06F 40/30 (2020.01); G06N 20/00 (2019.01); H04L 63/1408 (2013.01); G06F 40/247 (2020.01); G06F 40/253 (2020.01); G06F 40/284 (2020.01); G06F 40/40 (2020.01)] | 18 Claims |
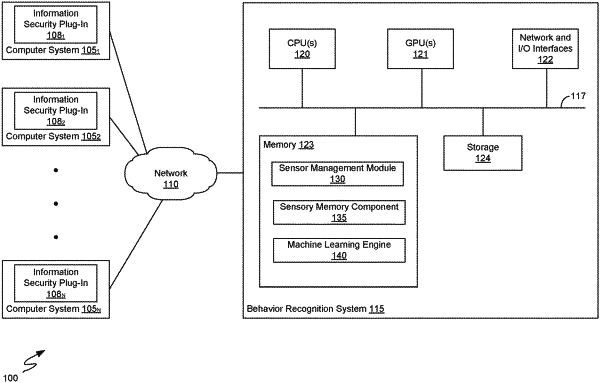
|
1. A method, comprising:
receiving, at a processor, a first ordered stream of normalized values associated with information security data for a computer network;
generating a stable neuro-linguistic model by:
clustering the first ordered stream of normalized values to form a plurality of clusters,
outputting an ordered sequence of letters based on the plurality of clusters,
building a dictionary of words based on the ordered sequence of letters, each word from the dictionary of words having a length from a plurality of lengths, each length from the plurality of lengths being less than or equal to a specified maximum letter length,
outputting an ordered stream of words based on the ordered sequence of letters, and
generating a plurality of phrases based on the ordered stream of words;
detecting, using a codelet template, a pattern in a linguistic representation of the information security data, the linguistic representation of the information security data including at least one of the ordered sequence of letters, the ordered stream of words, or the plurality of phrases;
receiving a second ordered stream of normalized values associated with the information security data for the computer network; and
issuing an alert based on the stable neuro-linguistic model, the pattern, and the second ordered stream of normalized values.
|