| CPC H04L 63/1416 (2013.01) [H04L 63/0876 (2013.01); H04L 63/1425 (2013.01); H04L 63/1466 (2013.01)] | 12 Claims |
|
1. A system for detecting and mitigating golden Security Assertion Markup Language (SAML) attacks against federated services, comprising:
a computing device comprising a memory and a processor;
an authentication object inspector comprising a first plurality of programming instructions stored in the memory which, when operating on the processor, causes the computing device to:
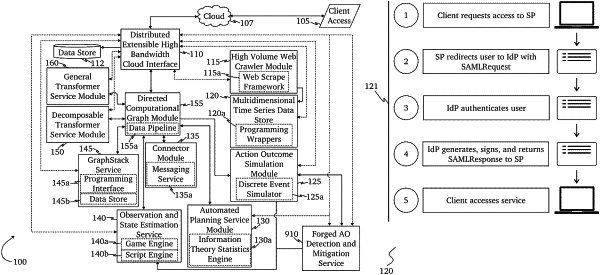
receive network traffic comprising a plurality of network packets, the plurality of network packets comprising a first authentication object for a user of a federated service, the first authentication object comprising a first identification string known to be generated by an identity provider associated with the federated service;
store a record of the first authentication object, with attached metadata comprising a timestamp of when the first authentication object was received, in a time-series database;
generate a security cookie for the first authentication object;
provide the security cookie to the identity provider from which the first authentication object was generated for inclusion in additional authentication objects issued to the user;
receive a request for access to the federated service by the user accompanied by a second authentication object comprising a second identification string and the security cookie;
compare a value of the second identification string of the second authentication object against a value of the second identification string of the stored record of the first authentication object;
check the second authentication object for the security cookie; and
generate an authentication failure if the security cookie is missing or invalid.
|