| CPC H04L 63/104 (2013.01) [G06V 40/173 (2022.01); H04L 63/20 (2013.01)] | 20 Claims |
|
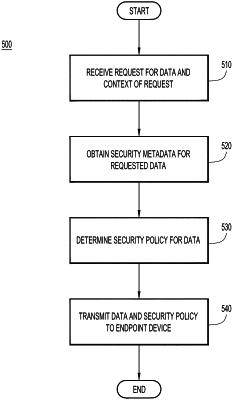
1. A computer-implemented method for secure data access comprising:
receiving, at a server, a request from an endpoint device for requested data, wherein the request includes one or more contextual attributes of the endpoint device including an identity of a user of the endpoint device;
processing the one or more contextual attributes and authenticating the identity of the user to determine that the endpoint device is authorized to receive the requested data;
determining a security policy for the requested data based on the one or more contextual attributes; and
transmitting, by the server, the requested data including the determined security policy to the endpoint device, wherein responsive to receiving the requested data to obtain received data, the endpoint device enforces the security policy associated with the authenticated user to selectively permit access to the received data by (i) preventing the endpoint device from displaying the received data to an unauthorized individual and (ii) locally caching the received data on the endpoint device.
|