| CPC H04L 63/10 (2013.01) [H04W 12/63 (2021.01)] | 21 Claims |
|
1. A method comprising:
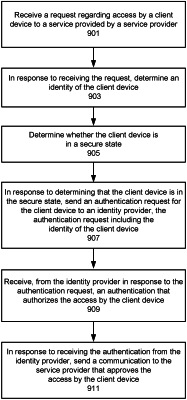
receiving, via a processor from an identity broker, a request regarding access by a client device to a service provided by a service provider;
in response to receiving the request, determining a first security state of the client device representing a risk of compromise associated with the client device;
determining that the first security state of the client device is a secure state representing a risk level below a threshold risk;
in response to determining that the first security state of the client device is the secure state, sending to the identity broker an indication that the client device is in the secure state indicating to the identity broker permission to authorize direct access by the client device to the service provider, wherein the identity broker is configured to, in response to receiving the permission, send a communication to the service provider that approves the direct access by the client device;
determining that the client device has changed to a new security state; and
in response to determining that the client device has changed to the new security state, replacing a component of an application in the client device corresponding to the new security state.
|