| CPC G06Q 40/03 (2023.01) [G06F 9/445 (2013.01); G06F 21/305 (2013.01); G06F 21/6263 (2013.01); H04L 9/0819 (2013.01); H04L 41/147 (2013.01); H04L 63/0876 (2013.01); H04L 63/0884 (2013.01); H04L 63/126 (2013.01); H04L 67/535 (2022.05)] | 17 Claims |
|
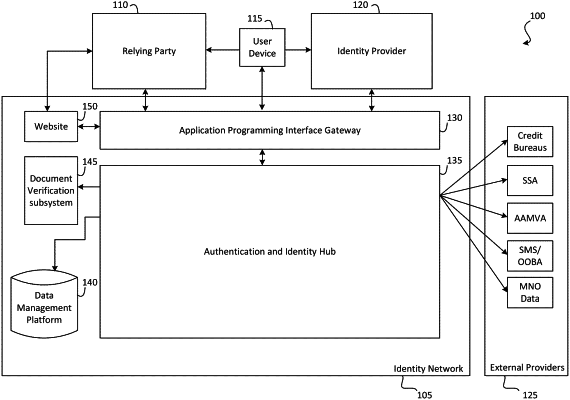
1. A method for using an authenticated, universal digital identity for a user, the method comprising:
receiving, by a relying party, a first request from a user to sign up for access to the relying party using a digital identity of the user;
providing, by the relying party, one or more identity providers for the user to select from;
receiving, by the relying party, a selection from the user of a specific identity provider from the one or more identity providers;
submitting, by the relying party, a second request to an identity network to retrieve identity attributes from the specific identity provider;
receiving, by the relying party, the identity attributes from the identity network, the identity attributes originating from the specific identity provider, wherein the identity attributes are encrypted using a first encryption key;
receiving a second encryption key from the specific identity provider that is used to decrypt the identity attributes; and
providing the second encryption key to the identity network prior to receiving the identity attributes.
|