| US 11,816,672 B1 | ||
| Flexible authentication | ||
| Priyamvada Singh, San Francisco, CA (US); Jeff Cornman, San Francisco, CA (US); and Melody Kao, San Francisco, CA (US) | ||
| Assigned to Wells Fargo Bank, N.A., San Francisco, CA (US) | ||
| Filed by Wells Fargo Bank, N.A., Charlotte, NC (US) | ||
| Filed on Jan. 29, 2016, as Appl. No. 15/009,917. | ||
| Claims priority of provisional application 62/221,970, filed on Sep. 22, 2015. | ||
| Int. Cl. G06Q 20/40 (2012.01); H04L 9/40 (2022.01); G06Q 20/38 (2012.01) | ||
| CPC G06Q 20/405 (2013.01) [G06Q 20/382 (2013.01); G06Q 20/40145 (2013.01); H04L 63/08 (2013.01); H04L 63/0807 (2013.01); H04L 63/0861 (2013.01); H04L 63/20 (2013.01)] | 14 Claims |
|
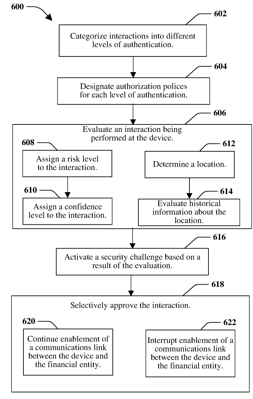
1. A method, comprising:
categorizing, by a system comprising a processor, a set of financial interactions into different levels of authentication; designating, by the system, an authentication policy for each level of authentication, wherein each level of authentication is designated with a different authentication policy; evaluating, by the system, an interaction of the set of financial interactions being performed at a device, wherein the interaction is performed over a communication link enabled between a financial entity and the device, and wherein evaluating the interaction includes:
assigning a risk level to the interaction, wherein the risk level is based on whether the interaction indicates an anomaly relative to a historical pattern of interactions previously performed by the device,
assigning a confidence level to the interaction, wherein the confidence level is based on a characteristic of the device or an indicator of an identity of a user of the device, and
assigning, for the interaction, a level of authentication based on the assigned risk level and confidence level, wherein assigning the level of authentication includes: (i) identifying a set of rules associated with the interaction, the set of rules being defined by a matrix; (ii) selecting, from the matrix, a rule of the set of rules based on the assigned risk level and confidence level; and (iii) applying the rule to the interaction to determine at least one type of authentication required to authenticate the device before approving the interaction;
as a result of the evaluating, causing a security challenge to be output at the device, wherein the security challenge comprises a prompt to perform a set of passive and active actions, wherein the set of passive and active actions are determined based on the at least one type of authentication identified by the level of authentication, wherein a passive action of the set of passive and active actions identifies an action to be performed by the device without user input, and wherein an active action of the set of passive and active actions identifies an action to beperformed by the user of the device; receiving, from the device, a response to the security challenge, wherein the response includes results indicative of whether the set of passive and active actions have been successfully performed; authenticating the user of the device based on the results of the set of passive and active actions meeting a predetermined threshold for the level of authentication; and approving, by the system, performance of the interaction at the device based on authenticating the user. |