| CPC G06F 21/64 (2013.01) [G06F 21/52 (2013.01); G06F 21/57 (2013.01)] | 20 Claims |
|
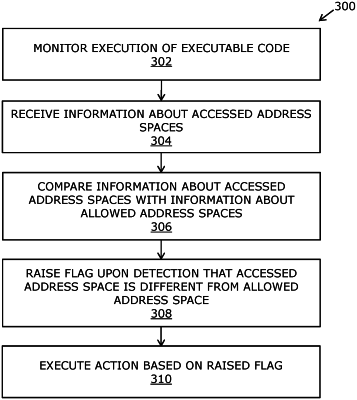
1. A method for detection of tampering in an executable code, the executable code comprising a gaming application and one or more code blocks, the method comprising:
monitoring execution of the executable code with a call stack data structure associated therewith, the execution involving accessing one or more address spaces, wherein an address space is associated with respective ones of the one or more code blocks;
receiving information about the accessed one or more address spaces, the received information about the accessed one or more address spaces further comprising a record of previous tampering by unauthorized users of code blocks associated with the one or more address spaces;
comparing the received information about the accessed one or more address spaces with information about one or more allowed address spaces defined in the call stack data structure of the executable code;
raising a flag upon detection that the received information about the accessed one or more address spaces are different from the information about the one or more allowed address spaces, based on the comparison; and
executing an action based on the raised flag, wherein the received information about the accessed one or more address spaces indicates that one or more address spaces are directed to outside the executable code.
|