| CPC G06F 21/6227 (2013.01) [G06F 16/2379 (2019.01); G06Q 20/382 (2013.01); G06Q 20/401 (2013.01); G06Q 40/02 (2013.01); G06F 2221/2107 (2013.01); G06Q 2220/00 (2013.01)] | 13 Claims |
|
1. A method of authenticating data with a data container host comprising:
generating the data at a point of sale system;
capturing, by the data container host communicating with the point of sale system across a network, the data;
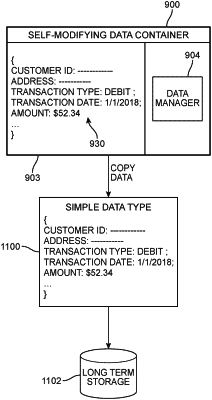
generating, by the data container host, a self-modifying data container, the self-modifying data container including a data storage structure and a data manager stored as executable code within the self-modifying data container, wherein access to the data storage structure is controlled through the data manager;
populating, by the data container host, one or more fields in the data storage structure with the data including authenticating information;
setting, by the data container host, instructions in the data manager for a modification trigger, the instructions configured to cause the data manager running on a processor to check for the modification trigger, and upon encountering the modification trigger access the data storage structure and modify the data in the data storage structure, thereby securing the data;
receiving, by the data container host from a processor across the network, a request for the authenticating information of the data;
authenticating the data in the data storage structure by running the data manager on the data container host to access the data storage structure and the authenticating information, and providing, by the data container host to the processor across the network, the authenticating information of the data;
encountering, by the data manager running on the data container host, the modification trigger upon completion of the authentication of the data in the data storage structure;
accessing, using the data manager running on the data container host, the data storage structure in response to encountering the modification trigger; and
deleting, using the data manager running on the data container host, at least a portion of the authenticating information in the data storage structure, thereby securing the portion of the authenticating information in response to encountering the modification trigger.
|