| CPC G06F 21/62 (2013.01) [G06F 21/604 (2013.01)] | 14 Claims |
|
1. A computer-implemented method for controlling access to data by computer systems, the method comprising:
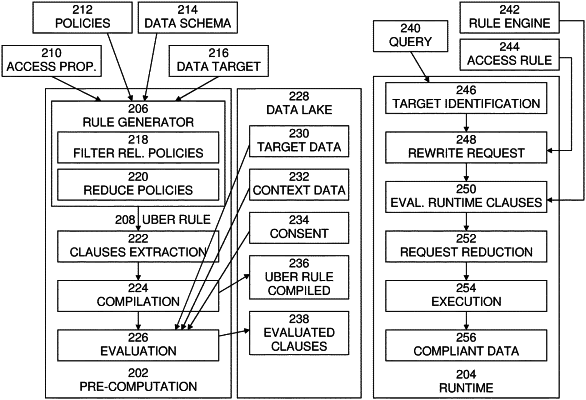
generating at least one rule governing access to the data by grouping a plurality of data access policies by related data access attributes, and combining and reducing the grouped plurality of data access policies to form a single logical expression;
generating an intermediate representation by integrating a combination of clauses extracted from the single logical expression comprising variables and rules that govern data attributes, the data attributes including attributes per data subject, and the data itself to form the intermediate representation;
extracting at least one logical clause from the generated at least one rule governing access to the data wherein the at least one logical clause contains data access attributes only from a group of properties that are known in a pre-computation phase;
compiling and evaluating the at least one logical clause into at least one selected clause comprising at least one data-source specific expression;
receiving a request for access to the data;
rewriting the request for access to the data into a new request for access by evaluating the variables and the at least one selected clause to concrete values, substituting the evaluated variables and the at least one selected clause into the new request for access, and reducing the new request for access based on the substitution, so as to provide access only to data allowed by the grouped plurality of data access policies integrated into the intermediate representation;
storing the at least one selected clause in a compressed form; and
executing the new request for access and providing only data allowed by the grouped plurality of data access policies integrated into the intermediate representation.
|