| CPC G06F 21/577 (2013.01) [G02B 27/0172 (2013.01); G02C 11/10 (2013.01); G06F 1/163 (2013.01); G06N 5/04 (2013.01); G06N 20/00 (2019.01); H04W 76/10 (2018.02); G02B 2027/014 (2013.01); G02B 2027/0138 (2013.01); G02B 2027/0178 (2013.01); G06F 2221/033 (2013.01); H04W 4/80 (2018.02); H04W 84/12 (2013.01)] | 20 Claims |
|
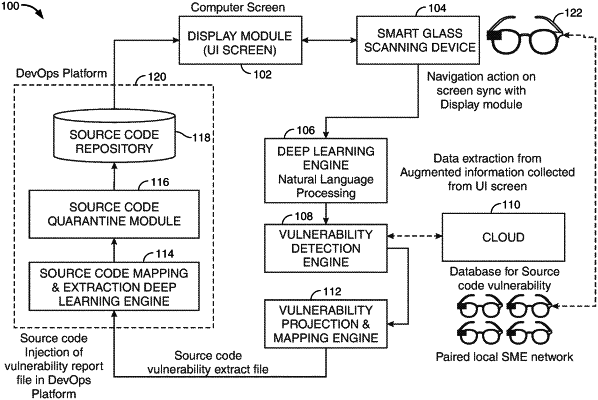
1. A method for leveraging smart glasses for capturing application source code associated with an application and further identifying vulnerabilities within the application source code, the capturing being independent from accessing an internal development platform associated with the application, the method comprising:
scanning, using a scanning device embedded on the smart glasses, application source code displayed on a user interface (“UI”);
projecting the scanned application source code on an augmented virtual screen on the smart glasses;
identifying one or more vulnerabilities within the scanned application source code using machine-learning (“ML”), the identifying including searching the application source code for one or more features stored in a ML database, each feature being associated with at least one of the vulnerabilities;
linking a vulnerability classification code for each identified vulnerability, the vulnerability classification code retrieved from a cloud repository, the cloud repository residing on a cloud independent from the internal development platform;
generating a vulnerability report file including the scanned application source code, each identified vulnerability and its linked vulnerability classification code;
transferring the vulnerability report file to a source code repository within the internal development platform;
extracting from the vulnerability report file, the scanned application source code, each identified vulnerability and the linked vulnerability classification code associated with each identified vulnerability;
matching the scanned application source code to an original application source code within the source code repository; and
separating, pending completion of revisions to the code based off of the vulnerability report file, the original application source code from the application within the source code repository.
|