| CPC G06F 21/57 (2013.01) [H04L 9/0869 (2013.01); G06F 2221/034 (2013.01)] | 19 Claims |
|
1. A system, comprising:
one or more processors; and
one or more computer-readable non-transitory storage media, the one or more computer-readable non-transitory storage media comprising instructions that, when executed by the one or more processors, cause one or more components of the system to perform operations comprising:
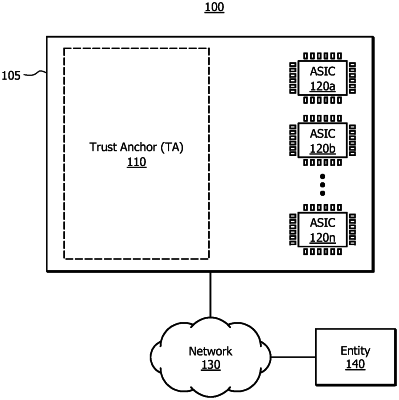
performing a posture assessment at a trust anchor to determine whether a hardware component is authorized to run on a product at a boot time of the product, wherein performing the posture assessment comprises:
determining a random value (K) associated with the product for a specific boot session;
obtaining a long-term key associated with the hardware component, the long-term key being provided by the hardware component or the product;
encrypting the random value (K) with the long-term key associated with the hardware component in order to yield an encrypted value, wherein:
the hardware component decrypts the encrypted value to confirm the random value (k); and
in response to determining that the long-term key is the long-term key associated with the hardware component, the hardware component confirms that the trust anchor is authorized to run on the product;
communicating the encrypted value to the hardware component; and
determining whether the hardware component is authorized to run on the product based at least in part on whether the trust anchor receives a response encrypted using the random value (K) from the hardware component; and
performing an action that depends on whether the hardware component is authorized to run on the product.
|