| CPC G06F 21/566 (2013.01) [G06F 9/45545 (2013.01); G06F 9/45558 (2013.01); G06F 21/54 (2013.01); G06F 21/554 (2013.01); G06F 2009/45583 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45591 (2013.01); G06F 2221/034 (2013.01)] | 21 Claims |
|
1. A method in a virtualized computing environment to protect operating system (OS) kernel objects against modification by malicious code, the method comprising:
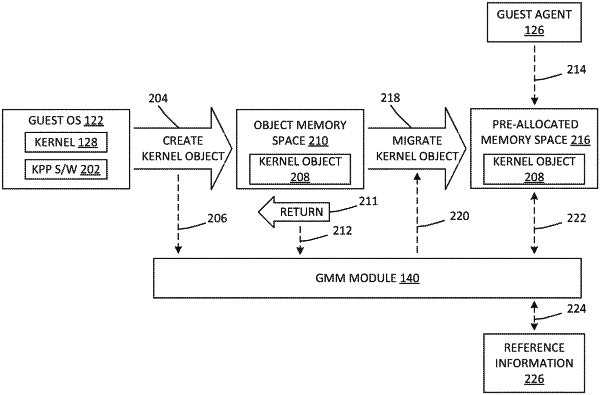
allocating, by a guest agent in a guest virtualized computing instance supported by a host in the virtualized computing environment, a memory space to store the OS kernel objects;
detecting, by a guest monitoring mode (GMM) module at the host, creation of an OS kernel object by a guest OS of the virtualized computing instance;
in response to detecting the creation of the OS kernel object, migrating, by the GMM module, the created OS kernel object to one or more memory addresses of the allocated memory space;
monitoring, by the GMM module, for at least one attempt to modify the OS kernel object in the one or more memory addresses of the allocated memory space;
in response to the monitoring having detected a first attempt to modify the OS kernel object, checking, by the GMM module, reference information to determine whether the first attempt is authorized; and
in response to a determination that the first attempt is unauthorized, initiating, by the GMM module, a remedial action to respond to the first attempt.
|