| CPC H04W 12/30 (2021.01) [G06F 21/31 (2013.01); G06F 21/554 (2013.01); H04W 12/122 (2021.01); G06F 2221/034 (2013.01)] | 18 Claims |
|
1. A computer-implemented method for utilizing user identity notifications to protect against potential privacy attacks on mobile devices, at least a portion of the method being performed by a mobile computing device comprising at least one processor, the method comprising:
monitoring the mobile computing device to detect one or more user interactions by a current user;
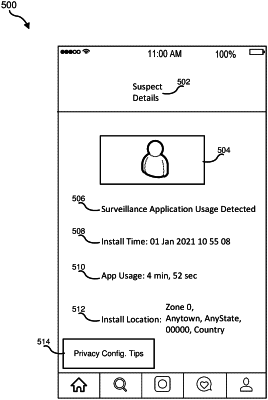
identifying the current user of the mobile computing device by capturing and applying a facial recognition algorithm to a self-portrait image of the current user;
determining that the current user is a potentially malicious user associated with one or more privacy-invasive applications installed on the mobile computing device; and
performing a security action that protects a benign user of the mobile computing device against an attack initiated by the potentially malicious user associated with the privacy-invasive applications, wherein performing the security action comprises generating a notification comprising an identification of the potentially malicious user and an identification of the privacy-invasive applications installed on the mobile computing device for delivery to the benign user, wherein the identification of the potentially malicious user is determined by applying the facial recognition algorithm to the captured self-portrait image of the current user, wherein the notification is generated after the potentially malicious user is determined to no longer be the current user based on a low likelihood that an additional mobile computing device associated with the potentially malicious user is near the mobile computing device.
|