| CPC H04N 21/43615 (2013.01) [G06F 3/167 (2013.01); H04N 21/4415 (2013.01); H04N 21/4825 (2013.01); H04N 21/8113 (2013.01)] | 20 Claims |
|
1. A playback device comprising:
one or more amplifiers configured to drive one or more speakers;
one or more network communications interfaces;
at least one processor;
a housing carrying the one or more amplifiers, the one or more network communications interfaces; and the at least one processor; and
at least one non-transitory computer-readable medium comprising program instructions that are executable by the at least one processor such that the playback device is configured to:
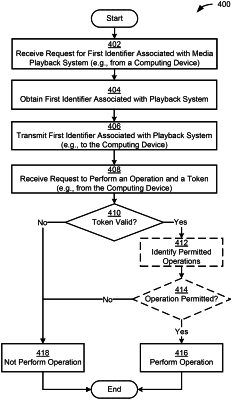
receive, via the one or more network communications interfaces from a computing device, a request for a first identifier;
obtain the first identifier;
transmit, via the one or more network communications interfaces to the computing device in response to the received request, the first identifier;
receive, via the one or more network communications interfaces from the computing device, (1) a request to perform an operation and (2) a token, wherein the token is generated by a computing system when one or more credentials received by the computing system from the computing device are determined to be valid based on the one or more credentials including the first identifier;
determine that the token is valid;
responsive to the determination that the token is valid, identify a set of permitted operations associated with the token;
determine that the operation is within a set of permitted operations associated with the token; and
responsive to the determination that the operation is within the set of permitted operations associated with the token, perform the operation.
|