| CPC H04L 9/0869 (2013.01) [H04L 9/0631 (2013.01); H04L 9/0825 (2013.01); H04L 9/3066 (2013.01)] | 9 Claims |
|
1. A system comprising the following components:
a client device with a processor, an input device, a memory containing a client device application and optional external storage device;
a crypto package containing at least each of an Advanced Encryption Standard (AES, Secure Hash Algorithm 256-bit (Sha256), Pseudorandom Number Generator (PRNG) and elliptic curve function on both the server and the client; and
a server with a processor and a memory containing one or more databases, such database(s) containing encrypted secret data and the crypto package;
generating, via the processor of the server, a symmetric key to decrypt data stored on a server and perform work on the server;
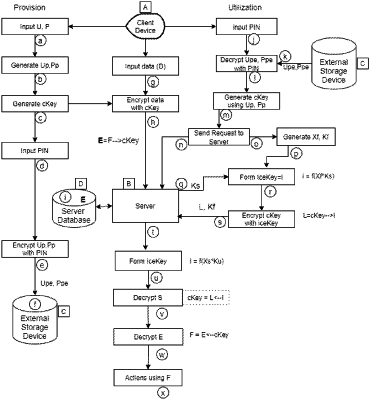
such system components executing the following steps (lower case letters are in reference to FIG. 2):
1. Provisioning the system, which provisioning includes the following sub steps:
a. Inputting, via the processor of the client device, a first set of credentials, such first set of credentials embodied as a username and password into the client device application;
b. Generating, via the processor of the client device, phantom credentials embodied as a phantom username and phantom password, wherein the phantom credentials are pseudo random regenerative credentials using the first set of credentials as seed to the PRNG;
c. Generating, via the processor of the client device, a first symmetric encryption key, such first symmetric encryption key embodied as a random string from the phantom credentials, such that the first symmetric encryption key is regenerative, using the phantom credentials to seed the PRNG process;
d. Inputting, via the input device of the client device, a personal identification number (PIN);
e. Encrypting, via the processor of the client device, the phantom credentials using the PIN to create a second symmetric encryption key;
f. Storing, via the processor of the client device, the encrypted phantom credentials on the client external storage device;
g. Inputting, via the input device of the client device, user secret data;
h. Initiating, via the processor of the client device, the AES engine to use the first symmetric encryption key to encrypt the secret data from the client device and send the encrypted secret data to the server memory;
i. Storing, via the processor of the server, the encrypted secret data on the server database;
2. Utilizing the system, which utilizing includes the following sub steps:
j. Inputting, via the input device of the client device, the PIN;
k. Retrieving, via the processor of the client device, the encrypted phantom credentials from the client external storage device into the client device processor;
l. Decrypting, via the processor of the client device, the phantom credentials using the PIN to create the second symmetric decryption key;
m. Generating, via the processor of the client device, the first symmetric encryption key from the phantom credentials;
n. Sending, via the processor of the client device, a request from the client device to the server processor for an elliptic public key;
o. Generating, via the processor of the client device, a fake client elliptic private key embodied as a random string;
p. Generating, via the processor of the client device, a fake client elliptic public key from the fake client elliptic private key;
q. Sending, via the processor of the server, a server temporary elliptic public key from the server processor to the client device processor;
r. Generating, via the processor of the client device, a third symmetrical encryption key via the client device from the fake client elliptic private key and server temporary elliptic public key;
s. Encrypting, via the processor of the client device, the first symmetric encryption key using the third symmetric encryption key and sending the encrypted first symmetric encryption key and the fake client elliptic public key from the client device processor to the server memory;
t. Extracting, via the processor of the server, the encrypted secret data from the server database and sending the encrypted first symmetric encryption key and the fake client elliptic public key from the client device memory to the server memory;
u. Generating, via the processor of the server, a fourth symmetric encryption key using the server temporary elliptic private key and the fake client elliptic public key;
v. Decrypting, via the processor of the server, the encrypted first symmetric encryption key using the fourth symmetric encryption key as a decryption key and thereby recovering the first symmetric encryption key;
w. Decrypting, via the processor of the server, the encrypted secret data stored on the server database using the first symmetric encryption key as an AES decryption key and thereby recovering the previously input secret data; and
x. Performing, via the processor of the server, work using the decrypted secret data.
|