| CPC H04L 63/1433 (2013.01) [G05B 15/02 (2013.01)] | 18 Claims |
|
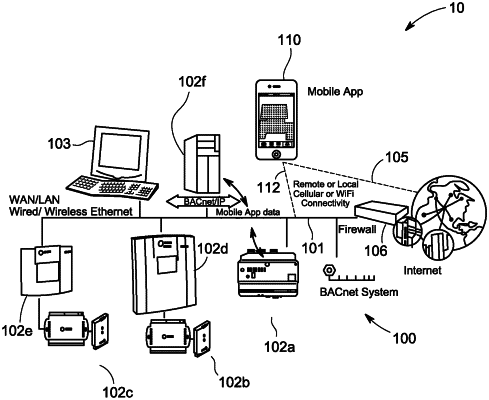
1. A computer-implemented method for performing an electronic security self-assessment of a controller in a building automation system, the building automation system including a network of electronic devices connected in electronic communication, the method comprising:
initiating an electronic security scan of the controller;
electronically self-assessing, by the controller, security vulnerabilities of the controller, the self-assessing including:
identifying one or more of a validation of whether the controller is protected by a firewall or other network security device,
identifying which communication ports are open,
identifying and verifying an Ethernet and Wi-Fi configuration of the controller,
determining whether any routers communicating with the controller are protected by the firewall or other network security device,
determining whether the controller is running an up-to-date software or firmware version,
determining a listing of software applications and versions installed on the controller, and
instructing an application on a remote computer to attempt to gain improper access to the controller, the attempt including:
conducting analysis of password strength for accessing the network of electronic devices as part of a controller instructed attack to gain access to the controller; and
determining a listing of recommendations for resolving security vulnerabilities of the controller based on the electronically self-assessed security vulnerabilities of the controller,
wherein the recommendations are based on at least one of industry standards or company guidelines.
|