| CPC H04L 63/1425 (2013.01) [H04L 61/4511 (2022.05); H04L 63/0236 (2013.01); H04L 63/0281 (2013.01); H04L 63/101 (2013.01); H04L 63/105 (2013.01)] | 26 Claims |
|
1. A system to support Internet traffic inspection, comprising:
a networking component; and
an inspection component communicatively coupled to the networking component,
wherein the inspection component is configured to
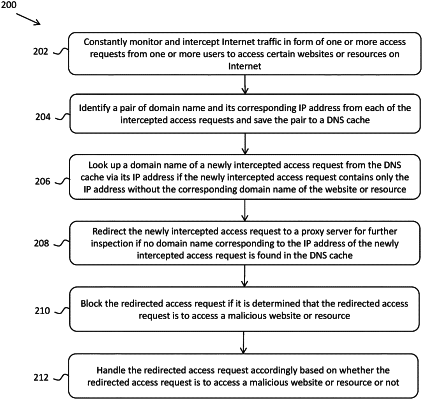
constantly monitor and intercept Internet traffic in form of one or more access requests from one or more users to access certain websites or resources hosted on a server on Internet;
identify a pair of domain name and its corresponding IP address from each of the intercepted one or more access requests and save the pair to a Domain Name System (DNS) cache;
look up a domain name of a newly intercepted access request from the DNS cache via an IP address of the newly intercepted access request if the newly intercepted access request contains only the IP address without corresponding domain name;
redirect the newly intercepted access request to a proxy server for further inspection if no domain name corresponding to the IP address of the newly intercepted access request is found in the DNS cache;
said proxy server configured to
determine whether the redirected newly intercepted access request into access a malicious website or resource or not;
handle the redirected newly intercepted access request accordingly based on whether the redirected newly intercepted access request is to access the malicious website or resource or not.
|