| CPC H04L 63/0442 (2013.01) [H04L 9/0631 (2013.01); H04L 9/14 (2013.01); H04L 9/0894 (2013.01)] | 10 Claims |
|
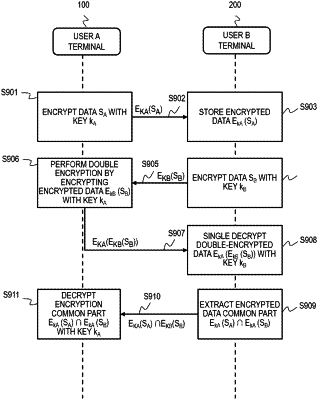
1. An information processing system comprising:
a first terminal; and
a second terminal, wherein
the first terminal holds first encrypted data encrypted, by the first terminal by encrypting values of first data, using a first key by a first encryption scheme,
the second terminal holds second encrypted data encrypted, by the second terminal by encrypting values of second data, using a second key by the first encryption scheme,
the first encryption scheme satisfies deterministic that a same encrypted data is generated when a same plaintext is encrypted with the same key and commutativity that same encrypted data is generated even if encryption using each of a plurality of keys is performed in an arbitrary order in a case where the same plaintext is multiplexed and encrypted with the plurality of keys,
wherein the first terminal and the second terminal are configured to sequentially perform following steps in order:
the first terminal transmits the first encrypted data to the second terminal,
the second terminal stores the encrypted first data in a data storage area of the second terminal,
the second terminal transmits the second encrypted data to the first terminal,
the first terminal:
generates third encrypted data by encrypting the second encrypted data using the first key by the first encryption scheme; and
transmits the third encrypted data to the second terminal,
the second terminal:
decrypts the third encrypted data with the second key;
calculates a common part between the first encrypted data and the decrypted third encrypted data; and
transmits the common part to the first terminal; and
the first terminal decrypts the common part with the first key.
|