| CPC H04L 63/1433 (2013.01) [G06N 20/00 (2019.01); H04L 63/1425 (2013.01)] | 25 Claims |
|
1. A computer-implemented method, comprising:
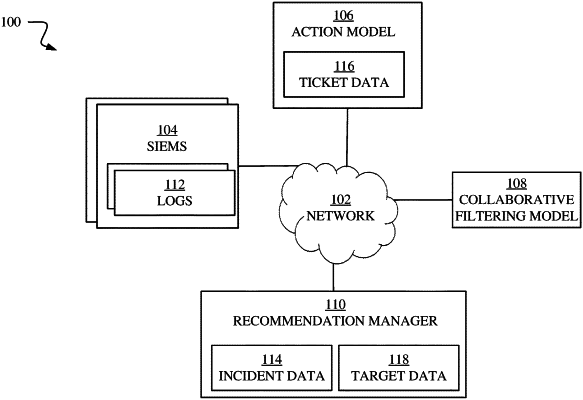
determining a plurality of recommended actions based on a security incident identified by a security information and event management (SIEM) system using an action model trained to make recommendations by:
determining a plurality of similar targets to a potential target of the security incident, wherein the similar targets and the potential target comprise a computer communication networking infrastructure, using a collaborative filtering model trained to assign a confidence value of similarity between an organization having a first networking infrastructure and the potential target, wherein the confidence value of similarity indicates a similarity in one or more shared characteristics, wherein similar targets can be determined based upon organizational factors of the similar targets and the potential target;
generating a plurality of actions taken by the similar targets using the action model;
assigning a plurality of weights to the actions based on:
one or more actions taken by the similar targets and the confidence value; and
a success or failure of the recommended actions; and
generating a prioritized list of the recommended actions that is sorted based on the assigned weights.
|