| CPC G06F 21/6263 (2013.01) [G06F 21/602 (2013.01); H04L 9/3073 (2013.01); H04L 63/0428 (2013.01)] | 20 Claims |
|
1. A method for protecting data input to a web-based application, the method comprising:
executing, within a web browser being executed by a computer system, a web-based application, wherein the web-based application is accessed through the web browser and executing the web-based application comprises:
automatically differentiating, in code downloaded as part of accessing the web-based application, one or more data fields as sensitive from one or more other data fields as not sensitive;
tagging the one or more data fields as sensitive; and
fetching a public key from a remote server system;
identifying, by the web-based application being executed within the web browser, a keystroke entry being input to the one or more data fields tagged as sensitive within the web-based application;
prior to storing the keystroke entry in memory mapped to the web browser, encrypting, by the web-based application being executed within the web browser, the keystroke entry using the fetched public key to generate an encrypted entry;
storing, by the web browser, the encrypted entry to memory, wherein the keystroke entry is never stored to memory of the computer system in an unencrypted form;
presenting, by the web browser, a representation of the keystroke entry in the data field tagged as sensitive;
transmitting, by the web-based application being executed within the web browser, the encrypted entry to the remote server system; and
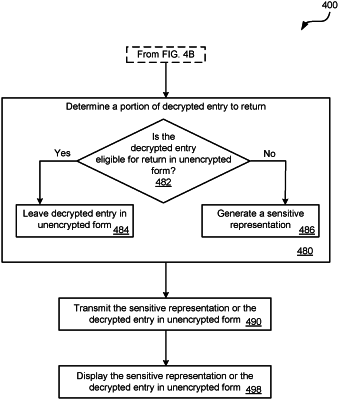
receiving, by the web-based application being executed within the web browser, a portion of the encrypted entry that has been decrypted and determined eligible for return to the web-based application in unencrypted form by the remote server system, wherein the determination that the portion of the encrypted entry is eligible for return in unencrypted form is based on a type of data entered into the one or more data fields.
|