| CPC G06F 21/554 (2013.01) [G06F 2221/034 (2013.01)] | 16 Claims |
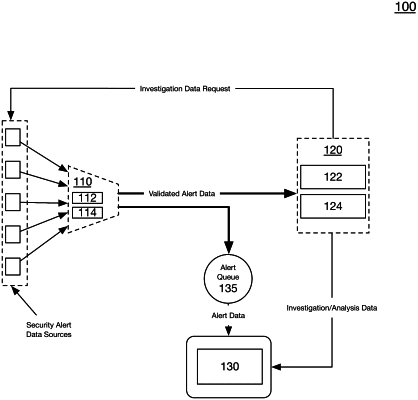
|
1. A method for verification-informed handling of cybersecurity activity, the method comprising:
at a cybersecurity event detection and response service:
attributing, by one or more computers, a service-computed threat severity level to a target cybersecurity event;
constructing, by the one or more computers, a cybersecurity threat verification communication based at least on the service-computed threat severity level, wherein the cybersecurity threat verification communication includes:
(a) one or more pieces of threat-informative content based on data associated with the target cybersecurity event;
(b) a first selectable interface object that, when selected, provides an indication that the target cybersecurity event relates to a cybersecurity incident; and
(c) a second selectable interface object that, when selected, provides an indication that the target cybersecurity event relates to a valid cybersecurity event;
selectively identifying a communication transmission destination for the cybersecurity threat verification communication from a plurality of distinct communication transmission destinations based on a subscriber-defined cybersecurity policy and the threat severity level, wherein the subscriber-defined cybersecurity policy defines a distinct communication transmission destination of the plurality of distinct transmission destinations for each of distinct threat severity level of a plurality of distinct service-computed threat severity levels;
transmitting, by the one or more computers, the cybersecurity threat verification communication based on the construction of the cybersecurity threat verification communication and the identification of the communication transmission destination;
updating, by the one or more computers, a threat severity level of the target cybersecurity event based on identifying an input selecting the first selectable interface object or the second selectable interface object of the cybersecurity threat verification communication; and
routing the target cybersecurity event to one of:
a cybersecurity threat escalation route of the cybersecurity event detection and response service based on identifying the input selecting the first selectable interface object, the cybersecurity threat escalation route comprising a cybersecurity incident queue; and
a cybersecurity threat de-escalation route of the cybersecurity event detection and response service based on identifying the input selecting the second selectable interface object, the cybersecurity threat de-escalation route comprising a cybersecurity event disposal queue.
|