| CPC G06F 21/54 (2013.01) [G06F 21/554 (2013.01); G06F 21/572 (2013.01)] | 11 Claims |
|
1. An electronic device comprising:
a memory configured to store a kernel and at least one application; and
a processor configured to, based on a system call generated by a process executed by the application being transmitted to the kernel, execute the application to cause the application to perform an operation corresponding to a request generated by the kernel based on the system call,
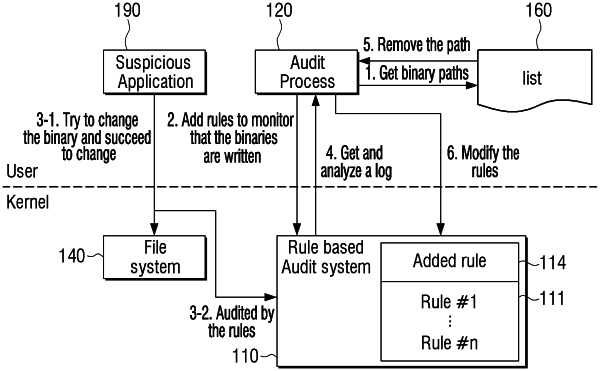
wherein the kernel is configured to perform an audit for the system call based on a plurality of predefined rules,
wherein the processor is further configured to:
generate a first rule to identify a point in time of a system call generated by the application to perform the process,
identify whether the application corresponds to a security-verified application based on the first rule,
based on the application corresponding to the security-verified application, generate a second rule to skip the audit based on the plurality of predefined rules,
perform security verification for at least one application stored in the memory,
generate a list including information about the at least one security-verified application, among the at least one application,
store the list in the memory,
generate a third rule to monitor modulation for at least one security-verified application stored in the list, and
based on modulation for the application being identified according to the third rule, delete information about the application of which modulation is identified from the list, and
wherein the modulation of the application is a modulation of binary code of the file associated with execution of the application is changed by an unauthorized user or system.
|