| CPC G06F 21/52 (2013.01) [G06F 21/566 (2013.01); G06N 20/00 (2019.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
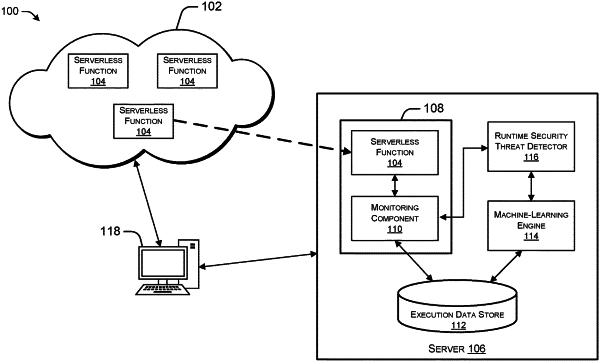
1. A method comprising:
receiving, by a computer system, a serverless function configured to execute in a cloud computing environment;
executing, by the computer system, the serverless function within a container-based application environment;
determining by the computer system, a first execution parameter associated with the execution of the serverless function, using a monitoring component executing within the container-based application environment;
determining a threshold value associated with the first execution parameter, wherein the threshold value is based at least in part on a runtime security threat associated with the serverless function;
comparing, by the computer system, the first execution parameter to the threshold value associated with the first execution parameter; and
determining, by the computer system, that the serverless function is associated with the runtime security threat, based on comparing the first execution parameter to the threshold value.
|