| CPC G06F 21/121 (2013.01) [G06F 8/61 (2013.01); G06F 21/44 (2013.01); G06Q 20/20 (2013.01); G06F 2221/0724 (2013.01)] | 17 Claims |
|
1. A system to install and run an application for a terminal, said system comprising:
a terminal management server (TMS), wherein:
said TMS and said terminal are coupled to each other via a network,
an application store and said terminal are coupled to each other via said network,
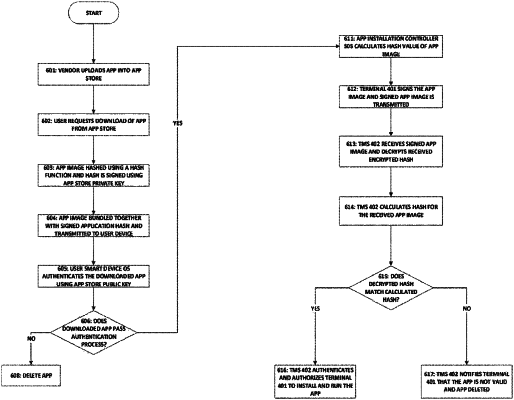
said TMS authorizes said terminal to install and run said application after said terminal downloads said application from said application store, wherein
said application is uploaded to said application store by a vendor, wherein prior to uploading, one or more portions of said application that handle sensitive information are encrypted by said vendor,
said terminal uses a public key of the application store to authenticate the downloaded application, and in response to the authentication, sends the TMS an image of the downloaded application and a signature generated from the image, wherein the signature comprise an encryption of a hash value computed by the terminal of the downloaded application,
said authorization comprises determining that the generated hash value matches the received hash value, and in response to said authorization, said TMS provides a decryption key of the vendor to said terminal to decrypt the one or more portions of said application to enable the application to handle the sensitive information.
|