| CPC G06F 21/562 (2013.01) [G06F 9/45558 (2013.01); G06F 21/51 (2013.01); G06F 21/53 (2013.01); G06N 3/02 (2013.01); G06F 2009/45587 (2013.01)] | 19 Claims |
|
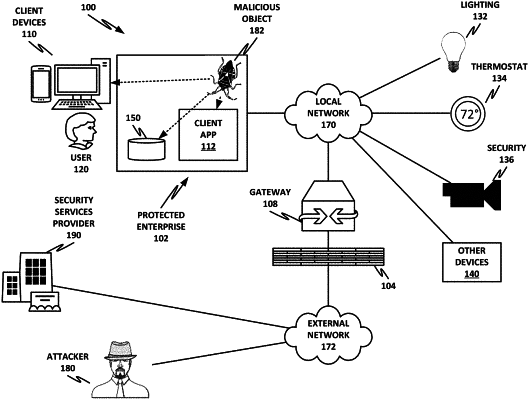
1. A method of detecting computer malware, comprising:
receiving a compressed binary object for analysis;
allocating the compressed binary object to a sandbox;
within the sandbox, unpacking the compressed binary object into an unpacked binary object and loading the unpacked binary object into an executable memory region;
performing a core dump of the executable memory region; and
performing a computer vision analysis of the core dump to determine malware characteristics.
|