| CPC H04W 12/122 (2021.01) [G16Y 30/10 (2020.01); H04L 43/0829 (2013.01); H04L 43/16 (2013.01); H04L 63/1416 (2013.01); H04W 4/70 (2018.02); H04W 24/08 (2013.01); H04W 64/00 (2013.01); H04L 2463/143 (2013.01); H04W 84/18 (2013.01)] | 18 Claims |
|
1. A device comprising:
one or more processors; and
one or more non-transitory computer-readable media storing instructions that, when executed by the one or more processors, cause the one or more processors to perform operations comprising:
assigning a first rating to a plurality of nodes within a mesh network;
determining a number of drops of a plurality of messages sent to a first node of the plurality of nodes;
determining that the number of drops of the plurality of messages exceeds a threshold number of drops for a time period;
based at least in part on the number of drops of the plurality of messages exceeding the threshold number of drops for the time period, decrementing the first rating assigned to the first node to a second rating assigned to the first node;
determining that the second rating assigned to the first node is below a rating threshold;
based at least in part on the second rating being below the rating threshold, determining that the first node is a potentially malicious node;
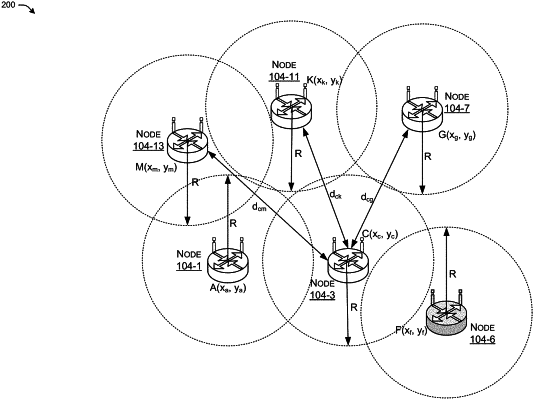
receiving first location information indicating a first location of the first node;
receiving second location information indicating a second location of a second node;
determining a distance threshold based at least in part on a second distance determined using the second location information;
determining, using the first location information, that a first distance to the first node is greater than or equal to the distance threshold; and
based at least in part on the first distance to the first node being larger than the distance threshold, identifying that the first node is a malicious node.
|