| CPC H04L 63/1433 (2013.01) [H04L 43/08 (2013.01); H04L 63/205 (2013.01)] | 20 Claims |
|
1. A computer-implemented method comprising:
determining, for a selected device in a network, at least one user of the selected device;
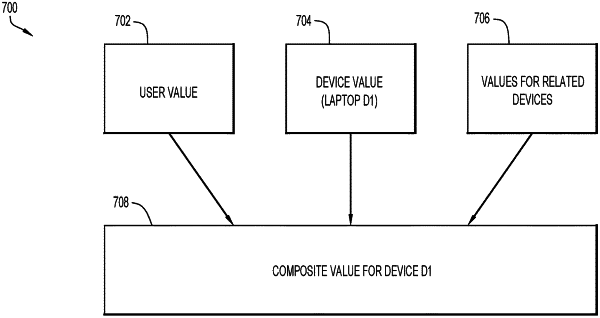
assigning a user value to the at least one user, wherein the user value is based on an identity of the at least one user;
obtaining behavior information of the at least one user, the behavior information including a list of other devices in the network used by the at least one user;
determining one or more related devices on the network associated with the at least one user by evaluating the behavior information of the at least one user and identifying devices in the network that are in communication with the selected device;
calculating a composite device value for the selected device by combining contributions from: (i) a value of the selected device that is based on direct or indirect relationships to the devices in the network that are in communication with the selected device, (ii) the user value, and (iii) values of the one or more related devices;
determining, for the selected device, a probability factor associated with potential security vulnerabilities affecting the selected device;
calculating a risk score for the selected device based on the composite device value and the probability factor; and
implementing security measures in the network based on a comparison of the risk score for the selected device with a plurality of risk scores for other devices in the network.
|