| CPC H04L 63/1433 (2013.01) | 15 Claims |
|
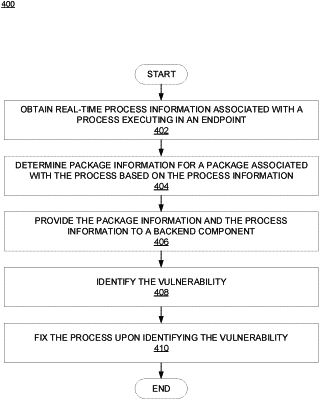
1. A method comprising:
obtaining, at a network controller and from one or more sensors running on one or more endpoints, real-time process information associated with at least one process executing on at least one of the one or more endpoints, wherein the network controller is communicatively connected to the one or more endpoints over a communication network;
determining, at the network controller, package information for a corresponding package associated with the at least one process based on the real-time process information; and
identifying, at the network controller and during runtime of the at least one process on the at least one of the one or more endpoints, at least one vulnerability associated with the package information using a database of vulnerabilities available only to the network controller.
|