| CPC H04L 63/08 (2013.01) [H04L 9/008 (2013.01); H04L 9/0643 (2013.01); H04L 43/0864 (2013.01); H04L 43/0876 (2013.01); H04L 2463/082 (2013.01); H04W 64/00 (2013.01)] | 20 Claims |
|
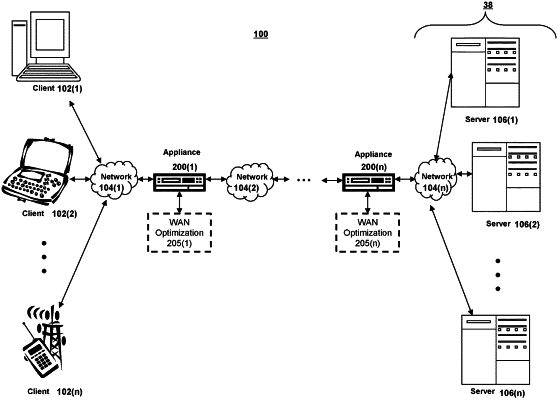
1. A method comprising:
receiving, by a computing device, a request from a client, the request being to perform an action to access at least one file and including a first computed value indicative of one or more previous actions on files;
comparing, by the computing device, the first computed value to a second computed value maintained by the computing device independently from the first computed value, the second computed value indicative of the one or more previous actions on the files; and
performing, by the computing device, secondary authentication in addition to primary authentication for the client, responsive to an indication of trustworthiness of the client or the at least one file according to the comparison of the first computed value to the second computed value.
|