| CPC H04L 63/0209 (2013.01) [G05B 9/02 (2013.01); G06N 3/08 (2013.01)] | 20 Claims |
|
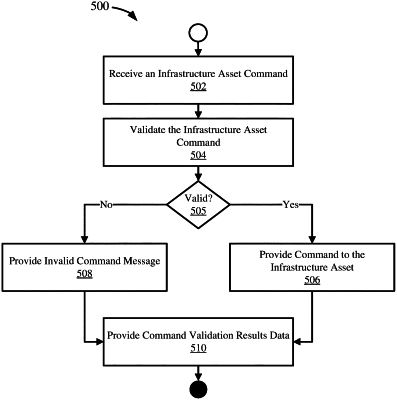
1. A method, implemented by one or more computing devices comprising at least one hardware processor and one or more tangible memories coupled to the at least one hardware processor, of protecting a set of controlled infrastructure assets in an infrastructure system, the method comprising:
receiving a first command for one of the set of controlled infrastructure assets;
validating the first command, wherein the first command is validated according to a command validation model, the command validation model having been generated based on data representing at least part of the infrastructure system;
responsive to a successful validation, providing the first command to the one of the set of controlled infrastructure assets;
adapting the command validation model to account for change in usage of the set of controlled infrastructure assets over time and for variance of components of the set of controlled infrastructure assets, including updating the command validation model based on results data of the command validation, the results data including the first command and a validity determination for the first command, wherein the updated command validation model is a process for analyzing and determining validity of one or more subsequent commands for the set of controlled infrastructure assets;
receiving a second command, among the one or more subsequent commands, for another one of the set of controlled infrastructure assets; and
responsive to an unsuccessful validation of the second command, rejecting the second command and preventing the second command from being executed by the other one of the set of controlled infrastructure assets, wherein the second command is malformed or the second command is determined to result in incorrect behavior of the other one of the set of controlled infrastructure assets.
|