| CPC H04L 9/3066 (2013.01) [G06F 21/606 (2013.01); H04L 9/0872 (2013.01); H04L 9/3263 (2013.01); H04W 12/02 (2013.01); G06F 2221/2107 (2013.01); G06F 2221/2111 (2013.01); H04L 63/0442 (2013.01); H04L 63/107 (2013.01); H04W 4/40 (2018.02); H04W 4/46 (2018.02); H04W 12/63 (2021.01)] | 20 Claims |
|
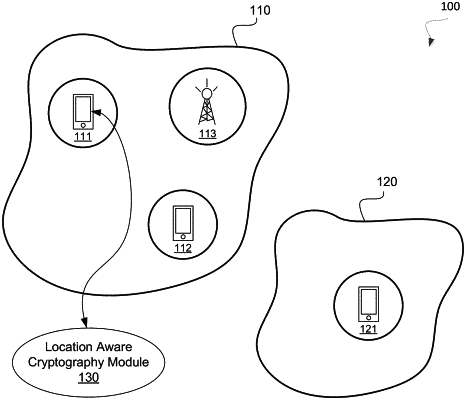
1. A method of operating a first device, the method comprising:
initiating a communication session with a second device;
generating first location information associated with the first device;
retrieving a public key and a private key associated with the first device;
generating a location-based private key based on the first location information and the private key;
transmitting a public key and a certificate to the second device;
receiving, from the second device, a session key encrypted based on the public key and second location information associated with the second device; and
communicating encrypted data with the second device in the communication session, wherein the encrypted data is encrypted with the session key.
|