| CPC G06F 21/565 (2013.01) [G06F 21/577 (2013.01); G06F 9/45558 (2013.01); G06F 2009/45587 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
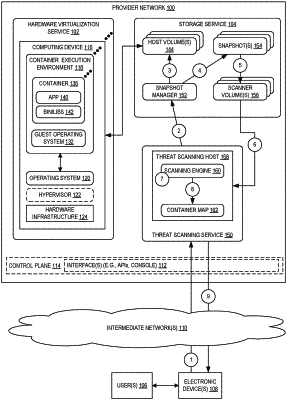
1. A computer-implemented method comprising:
obtaining a snapshot of at least one block storage volume associated with a host;
generating a scanner volume of the at least one block storage volume;
mounting the scanner volume based on the snapshot to a scanning instance of a threat scanning service;
generating a container map that maps storage locations in a file system of the scanner volume to one or more containers running in a container execution environment;
scanning, by a scanning engine of the scanning instance, the file system of the scanner volume;
identifying, by the scanning engine, at least one threat on the scanner volume;
identifying, by the scanning engine using the container map, at least one container of the one or more containers associated with the at least one threat; and
sending, by the scanning engine to a customer associated with the host, a detection report indicating the at least one container associated with the at least one threat.
|