| CPC G06F 21/52 (2013.01) [G06F 9/3005 (2013.01); G06F 9/30181 (2013.01)] | 11 Claims |
|
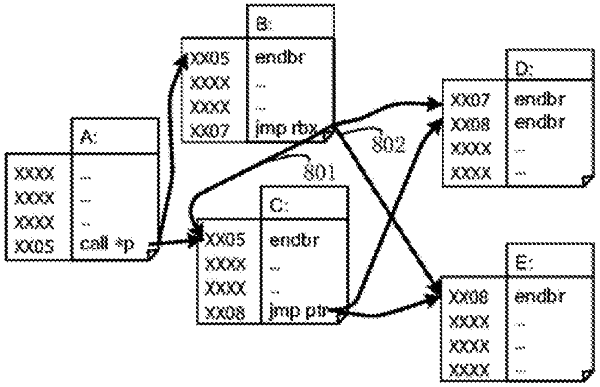
1. A method for control-flow integrity protection, comprising:
changing preset bits of all legal target addresses of a current indirect branch instruction in a control flow of a program to be protected, to make the preset bits of any legal target address of the current indirect branch instruction be same as the preset bits of other legal target addresses of the current indirect branch instruction; and
rewriting preset bits of a current target address of the current indirect branch instruction to be same as a label of the current indirect branch instruction, so that a current indirect branch cannot jump to the legal target addresses and the program to be protected terminates, when the current target address is tampered with; wherein the label is the changed preset bits of the legal target addresses of the current indirect branch instruction, and
wherein the changing preset bits of all legal target addresses of a current indirect branch instruction in a control flow of a program to be protected, to make the preset bits of any legal target address of the current indirect branch instruction be same as the preset bits of other legal target addresses of the current indirect branch instruction, comprises:
performing a null instruction fitting operation on each of the legal target addresses, so that the preset bits of each of the legal target addresses increase, until the preset bits of each of the legal target addresses are equal to the label of the current indirect branch instruction, wherein the label of the current indirect branch instruction is preset at random, and the label of the current indirect branch instruction is different from labels of other indirect branch instructions in the program to be protected.
|