| CPC G06F 16/9024 (2019.01) [G06F 21/577 (2013.01); G06F 21/6218 (2013.01)] | 20 Claims |
|
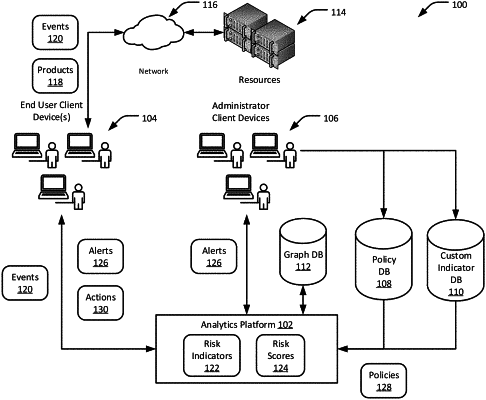
1. A method comprising:
retrieving, from a graph database, first data representing a first entity in a computing environment, a second entity in the computing environment, and an event representing data exchanged between the first entity and the second entity, wherein the first entity and the second entity are stored in the graph database as properties of a first vertex and a second vertex, respectively, and wherein the event is stored in the graph database as a property of an edge between the first vertex and the second vertex;
predicting, according to a risk indicator model and responsive to an occurrence of the event, a risk associated with the first entity based at least in part on the event;
adding or modifying, responsive to the predicting of the risk, a third vertex to the graph database; and
updating the graph database to include second data representing the risk and a risk indicator, wherein the risk indicator is stored in the graph database as a property of the third vertex, and wherein the risk is stored in the graph database as a property of an edge between the first vertex and the third vertex.
|